OpenEMR Reflected XSS Vulnerability
Overview:
SonicWall Capture Labs Threat Research Team has observed the following threat:
OpenEMR is a comprehensive open-source electronic health records (EHR) and medical practice management application. It provides an array of functionalities aimed at enhancing the efficiency of medical practice management. Among the critical features it provides are patient statistics, medical billing, electronic medical record (EMR) generation, and appointment scheduling. The listed capabilities empower medical practitioners, clinics, and hospitals to effectively manage and coordinate patient schedules, maintain detailed patient records, and streamline the billing process electronically. OpenEMR is designed with a flexible, user-friendly interface, making it an accessible solution for healthcare providers aiming to digitize and optimize their administrative and patient care processes. As an open-source platform, it also affords the flexibility of customization according to individual or institutional needs, further enhancing its applicability across a broad range of healthcare settings.
A reflected cross-site scripting vulnerability has been identified in OpenEMR. This vulnerability arises from inadequate input validation associated with the ‘list_id’ parameter in ‘share_template.php’.
A remote attacker could exploit this vulnerability by enticing a victim to open a crafted URL. Successfully exploiting this vulnerability could result in arbitrary code execution in the context of the victim’s browser.
CVE Reference:
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2023-2948.
Common Vulnerability Scoring System (CVSS):
The overall CVSS score is 8.6 (CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H/E:P/RL:O/RC:C).
Base score is 9.6 (AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H), based on the following metrics:
• Attack vector is network.
• Attack complexity is low.
• Privileges required is none.
• User interaction is required.
• Scope is changed.
• Impact of this vulnerability on data confidentiality is high.
• Impact of this vulnerability on data integrity is high.
• Impact of this vulnerability on data availability is high.
Temporal score is 8.6 (E:P/RL:O/RC:C), based on the following metrics:
• The exploit code maturity level of this vulnerability is proof of concept.
• The remediation level of this vulnerability is official fix.
• The report confidence level of this vulnerability is confirmed.
Technical Overview:
The vulnerability stems from inadequate validation of the “list_id” parameter in the “share_template.php” file. When a request is submitted to the RequestURI at “library/custom_template/share_template.php”, it leads to the generation of HTML content by “share_template.php”. This content also encompasses some JavaScript code. Within the context of this generated JavaScript code, the value of the “list_id” parameter is manifested in the definition of a function called “add_template()”, as illustrated below:
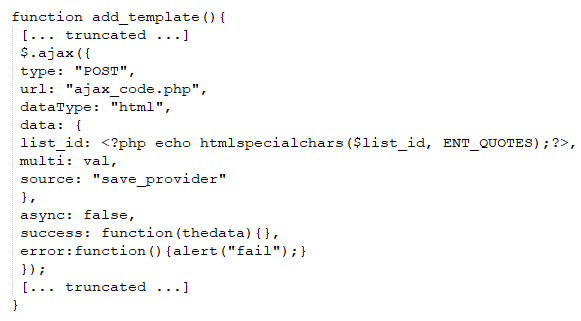
where $list_id is sanitized first by using PHP htmlspecialchars() function.
However, the use of htmlspecialchars() for XSS sanitization in this case is ineffective, as it only escapes the characters “<", ">“, and single and double quotes. An attacker can bypass this limitation by sending malicious JavaScript code that excludes these specific characters in the “list_id” request parameter and delivering the request to the “share_template.php” endpoint. With a specially tailored “list_id” value, the attacker can interfere with the original “add_template()” function definition and append their own JavaScript code immediately after it. For instance, consider a situation where the “list_id” parameter contains a skillfully crafted value like the one below:

Then “share_template.php” will generate the JavaScript code HTML format as below:
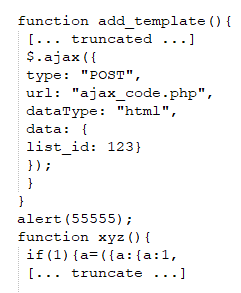
In this scenario, the crafted value allows the original “add_template()” function definition to be escaped and a script command – “alert(55555)” – to be inserted right after the function’s conclusion. Consequently, the “alert(55555)” will execute when the server-returned HTML content is loaded in the user’s browser. If the “alert(55555)” were to be swapped with a different malicious script, it would lead to the execution of this harmful code in the browser, potentially triggering XSS opportunities.
Triggering the Problem:
• The target system must have the vulnerable product installed and running.
• The target user must have network connectivity to the affected ports.
• The attacker must be able to deliver a malicious URL to a target user.
Triggering Conditions:
A user is lured by an attacker into opening a URL that contains a carefully designed list_id parameter. The vulnerability manifests itself when the user initiates the URL in a web browser.
Attack Delivery:
The following application protocols can be used to deliver an attack that exploits this vulnerability:
• HTTP
• HTTPS
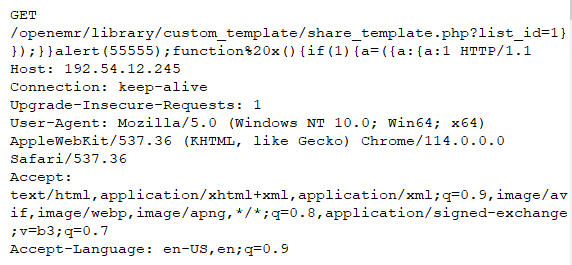
SonicWall’s, (IPS) Intrusion Prevention System, provides protection against this threat:
• IPS: 19216 OpenEMR Cross-Site Scripting
Remediation Details:
The risks posed by this vulnerability can be mitigated or eliminated by:
• Filtering traffic based on the signature above.
• Upgrading the product to a non-vulnerable version.
The vendor has released the following patch to address this issue:
Vendor Advisory
