Cisco ASA and FTD Directory Traversal Vulnerability
Cisco ASA is a security device that combines firewall, antivirus, intrusion prevention, and virtual private network (VPN) capabilities. Cisco Adaptive Security Appliance (ASA) software is the core operating system for the Cisco ASA family.
Directory Traversal Vulnerability
A directory traversal attack aims to access files and directories that are stored outside the web root folder. It does this by manipulating variables that reference files with dot-dot-slash sequences. A directory traversal vulnerability exists in Cisco’s Adaptive Security Appliance software and Firepower Threat Defense software web services. The vulnerability is due to improper validation of user input.
Cisco ASA and FTD Directory Traversal Vulnerability |CVE-2020-3452
The vulnerability is due to a lack of proper input validation of URLs in HTTP requests processed by a vulnerable device. An attacker could exploit this vulnerability by sending a crafted HTTP request containing directory traversal character sequences to an affected device.
Some examples of exploits:
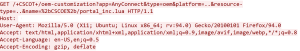
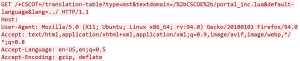
![]()
A successful exploit could allow the attacker to view arbitrary files within the web services file system on the targeted device. An attacker could impersonate another VPN user and establish a Clientless SSL VPN or AnyConnect VPN session to the device as that user. The attacker can view files within the web services file system.
SonicWall Capture Labs provides protection against this threat via following signatures:
- IPS 15716:Cisco ASA and FTD Directory Traversal 1
- IPS 15717:Cisco ASA and FTD Directory Traversal 2
This vulnerability is patched.
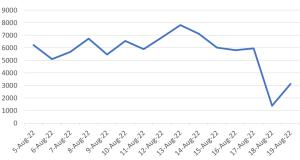
Threat Graph