Microsoft IE 0-Day vulnerability (Dec 11,2008)
SonicWALL UTM Research team observed exploits circulating in the wild targeting the new zero-day vulnerability in Microsoft Internet Explorer from December 9th, 2008. It has been confirmed that some existing viruses such as IESlice.FO can be downloaded by the published exploits. The vulnerability is identified as CVE-2008-4844. The vendor also released an advisory 961051 for it.
The actual vulnerability exists in the Dynamic Link Library mshtml.dll of Microsoft Internet Explorer application. The flaw is due to an error in a module that is handling specially crafted XML data. A memory corruption will occur while Microsoft Internet Explorer handles the nested tags which contain identical XML reference in their datasrc attributes. For example, the nested XML reference can be like the following:
< span datasrc=#I datafld=B dataformatas=HTML> < span datasrc=#I datafld=B dataformatas=HTML>If the vulnerability is triggered, the attacker can change the execution flow of the application to the code injected into the heap memory, which may cause the virus download or even full compromise of the target machine.
SonicWALL UTM Research team has analyzed the published exploits, and the following network snippet is from one of the exploits:

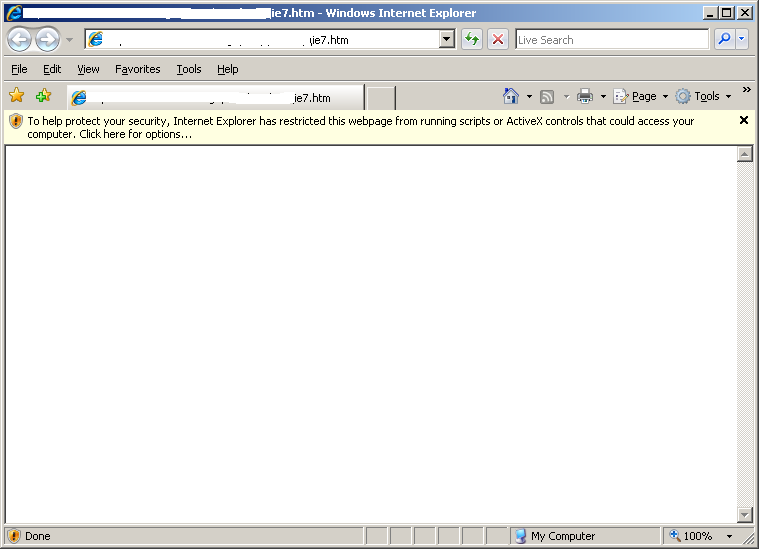
Note that Internet Explorer 7 by default restricts the malicious code from being executed as seen below, but it is a general warning message that is seen even while executing legitimate code:
SonicWALL UTM provided proactive protection against some of these vulnerability exploits with the following signatures:
- IPS: 4665 Javascript Code Injection Attempt (Win/Linux) 2
- GAV: IESlice.FO (Exploit)
Additional signatures specific for this vulnerability were added on December 10, 2008:
- IPS: 3670 MS IE XML SPAN Tag Heap Overflow Attempt
- IPS: 3671 MS IE XML SPAN Tag Heap Overflow Attempt 2
- GAV: XMLHttpd.U (Exploit)
- GAV: XMLHttp (Exploit)
