Runouce Trojan with IRC bot spreads via .eml files (March 24, 2016)
The Dell Sonicwall Threats Research team has observed a Trojan that spreads via .eml files. The Trojan contains IRC functionality and also has the ability to infect pre-installed system executable files with malicious code:
Infection Cycle:
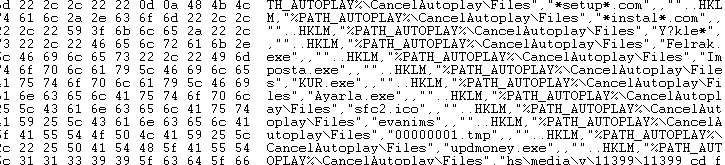
The Trojan makes the following DNS queries:
On our test system the following files were created:
- %USERPROFILE%kuelio.exe [Detected as GAV: Runouce.B2 (Trojan)]
- %SYSTEM32%runouce.exe (“runonce” with “n” changed to “u” (patched)) [Detected as GAV: Virut.U_6 (Trojan)]
- %SYSTEM32%runonce.exe (patched) [Detected as GAV: Virut.U_6 (Trojan)]
The following files were also created [all detected as GAV: Runouce.B2#email (Trojan)]:
- %APPDATA%GoogleChromeUser DataDefaultExtensionsaapocclcgogkmnckokdopfmhonfmgoek�.9_0readme.eml
- %APPDATA%GoogleChromeUser DataDefaultExtensionsaohghmighlieiainnegkcijnfilokake�.9_0readme.eml
- %APPDATA%GoogleChromeUser DataDefaultExtensionsenacoimjcgeinfnnnpajinjgmkahmfgb�.65.0_0readme.eml
- %APPDATA%GoogleChromeUser DataDefaultExtensionsenacoimjcgeinfnnnpajinjgmkahmfgb�.65.0_0tabsreadme.eml
- %APPDATA%GoogleChromeUser DataDefaultExtensionsfelcaaldnbdncclmgdcncolpebgiejap1.1_0readme.eml
- %APPDATA%GoogleChromeUser DataDefaultExtensionsfocgpgmpinbadijfcdimbdkgnpndjnkl�.54_0readme.eml
- %APPDATA%GoogleChromeUser DataDefaultExtensionsfocgpgmpinbadijfcdimbdkgnpndjnkl�.54_0changelogsreadme.eml
- %APPDATA%GoogleChromeUser DataDefaultExtensionsfocgpgmpinbadijfcdimbdkgnpndjnkl�.54_0tabsreadme.eml
- %APPDATA%GoogleChromeUser DataDefaultExtensionsnmmhkkegccagdldgiimedpiccmgmieda�.1.1.0_0htmlreadme.eml
- %USERPROFILE%Local SettingsTempreadme.eml
- %USERPROFILE%Local SettingsTemporary Internet FilesContent.IE5B4ZWX2C9readme.eml
- %USERPROFILE%Local SettingsTemporary Internet FilesContent.IE5FATM9A7Mreadme.eml
- %USERPROFILE%Local SettingsTemporary Internet FilesContent.IE5HE7GL0WOreadme.eml
- %USERPROFILE%Local SettingsTemporary Internet FilesContent.IE5MDJBB39Wreadme.eml
- %PROGRAMFILES%Common FilesMicrosoft SharedOFFICE121033readme.eml
- %PROGRAMFILES%Common FilesMicrosoft SharedOFFICE12HTMLreadme.eml
- %PROGRAMFILES%Common FilesMicrosoft SharedOFFICE12VS Runtime1033readme.eml
- %PROGRAMFILES%Common FilesMicrosoft SharedSmart Tag1033readme.eml
- %PROGRAMFILES%Common FilesMicrosoft SharedStationeryreadme.eml
- %PROGRAMFILES%Common FilesSystemadoreadme.eml
- %PROGRAMFILES%Microsoft OfficeOffice12readme.eml
- %PROGRAMFILES%Microsoft OfficeOffice121033readme.eml
- %PROGRAMFILES%Microsoft OfficeOffice12AccessWebreadme.eml
- %PROGRAMFILES%Microsoft OfficeOffice12GrooveToolDatagroove.netGrooveFormsreadme.eml
- %PROGRAMFILES%Microsoft OfficeOffice12GrooveToolDatagroove.netGrooveForms3readme.eml
- %PROGRAMFILES%Microsoft OfficeOffice12GrooveToolDatagroove.netGrooveForms4readme.eml
- %PROGRAMFILES%Microsoft OfficeOffice12GrooveToolDatagroove.netGrooveForms5readme.eml
- %PROGRAMFILES%Microsoft OfficeStationery1033readme.eml
- %PROGRAMFILES%Microsoft OfficeTemplates12MseNewFileItemsreadme.eml
- %PROGRAMFILES%NetMeetingreadme.eml
- %PROGRAMFILES%WinRARreadme.eml
- %PROGRAMFILES%Wiresharkreadme.eml
The Trojan writes the following keys to the registry to enable continued infection activity after reboot:
- HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun kuelio “%USERPROFILE%kuelio.exe /y”
- HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRun Runouce “%SYSTEM32%runouce.exe”
If there are shared folders or external drives attached the following file will be written to it:

The Trojan disables the ability to kill kuelio.exe.
NOTHING-6A527FE.eml and readme.eml are email files that contain an attachment called pp.exe [Detected as GAV: Runouce.B_3 (Worm)]:

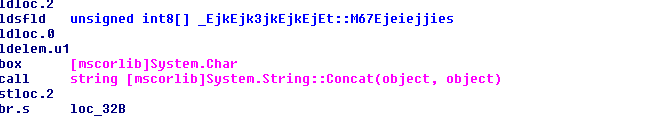
The Trojan infects %SYSTEM32%runonce.exe with additional malicious code. It modifies the PE section headers to extend the rsrc section and inject code. It then changes the OEP (entrypoint) so that the infected executable runs the malicious code first:

The Trojan joins an IRC server hosted at ircd.zief.pl and awaits further instructions:

SonicWALL Gateway AntiVirus provides protection against this threat via the following signatures:
- GAV: Sirefef.A_33 (Trojan)
- GAV: Runouce.B2 (Trojan)
- GAV: Runouce.B2#email (Trojan)
- GAV: Runouce.B_3 (Worm)
- GAV: Chir.B (Worm)
- GAV: Nimda_2 (Worm)
- GAV: Virut.U_6 (Trojan)