Metasploit is one of the most widely used Penetration Testing tool to test and improve defenses of internet facing services. It boasts of more than 1300 exploits and new ones are added at regular intervals thanks to the strong community that backs these efforts. Metasploit contains a number of different modules that cater to different requirements. For instance there are exploits that focus on a particular weakness whereas payloads consist of code that runs remotely.
Android has been relishing popularity among mobile phone users but at the same time there has been a lot of security concerns with regards to malware and other vulnerabilities, Metasploit developers saw this as a new avenue for research and introduced the support to generate Android specific payloads. Using these payloads an attacker can run myriad commands on a victims Android device, provided a modified APK (Android Package) with Metasploit modules is present on the target.
Dell SonicWALL Threats Research team recently observed a slew of Android malware that contain Metasploit specific components. This might be an indication of a new wave of Metasploit specific Android malware that will become commonplace in the near future.
Metasploit for Android
Using Metasploit it is possible to gain shell access on a target device which allows the attacker to perform a number of operations, additionally if the device is rooted the attacker can perform system level changes as well. The following high level steps are involved in creating a malicious Metasploit modified apk to compromise a victims device:
- msfvenom module is used to modify a clean APK and add a reverse TCP component into it
- Reverse TCP essentially makes the malicious apk initiate a connection back to the attacker who has a listener for incoming connections
- Once the device is infected with this modified APK, it connects back to the attacker with a shell which potentially gives him unlimited access
In the past few weeks we observed a number of malicious APK’s with Metasploit reverse TCP component present in them. Below image shows the code for three APK’s; first one is the code for a clean un-modified APK, second one is for a clean APK that we modified using the msfvenom module and the last one is for a malicious APK that we obtained:



We can see that the code for both the modified APK and malicious APK has striking similarity, this gives an indication that the attacker has been using the same Metasploit module for this modification.
A callback address needs to be specified in the case of Reverse TCP, following is a subset of few IP’s that we observed in malicious APK’s during our analysis:
- 10.0.2.15:443
- 10.20.4.28:4444
- 104.3.138.65:50106
- 75.133.215.49:4444
- 192.168.0.101:8888
- 192.168.1.2:4444
- 192.168.1.8:4443
- 192.168.43.225:4444
- 192.168.77.132:4444
- 192.168.254.66:4444
- 127.0.0.1:8888
Some of the IPs belong to 192.168 block, in such cases it is possible that an infected private server is present that forwards the data back to the attacker. Most of the malicious APK’s we observed were standalone APK’s with only the Metasploit modules, however we did see two cases where the Metasploit module was bundled with a separate completely working APK. In these cases the Metasploit module will run in the background while the original APK keeps running in the foreground. In this scenario the victim is oblivious to the fact that the attacker has gained an open shell to his device.
The following figure shows code for the malicious APK’s with bundled Metasploit modules:


As we can see both the APK’s have similar Metasploit components along with other class files that make up the APK. The callback addresses specified in these two APK’s are as below, at the moment Virustotal deems these links as clean:
- security-checks.de
- 92.97.176.17
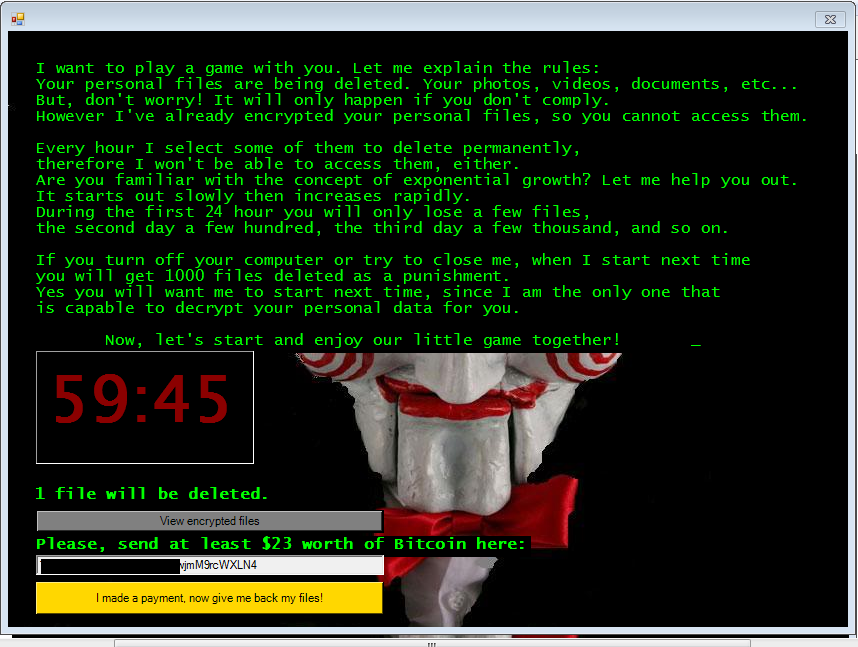
Using Metasploit as a component of a malicious APK might become more common as time passes but for now it still looks like this campaign is in its early stages. As mentioned before, this attack has tremendous impact on rooted devices as it would allow the attacker to perform system level changes. This further highlights the dangers of rooting an Android device.
Another good way to be cautious is to use security tools like OS Monitor and check for open connections on the device. A vigilant eye can catch connections opened by unknown apps as shown below:

Few MD5’s with package name com.metasploit.stage:
- 5781e46a33b1e680606aa1bc6de0f4b3
- e72f2256beb00995f75756fe6b1015ff
- 8be2a9c3deb2cb042f0d169f7aa1e09c
- 62ce4bfac9515391cf491202bde612d1
- b72e70d3354637a1789a42766fb02b85
- 98fa5306c6fa7a582f5cc20bee4199dd
- dca3e24d8a713b48509ec71f7f08393a
- 2fa4c90f4e18da57f35e20e2cfc94b36
- 54991e04f5dea9e6b889482dd32199a6
- babac94884531c8ded98a4a4631ec0aa
- 955404e259d848411c6b7663eae2efb5
- 9cfac5052012a36db9f68cad629f88bb
- 115a6624c31874fada0480c785a25490
- 6445745776b76f8740cd9dcbf1d819fd
- 7d250daa3247eb9fdce99d77a4244dba
- 52107f2cff13644cd376e3d896d4e774
- ef1f8d649e4aa63118973f198520557a
- 4fee3d7d944cbd16d4b43d9a45cc3ec7
- e206152242dc89565d824378a509dbc0
- c5951a883b738b19304ca0cda72b2ac9
- 148bb86e18af8d49b1e41e13c00f65d8
MD5’s with Metasploit component in a working APK:
- 3763b28338dff3f703a8192eff0f1c82 – com.thepapership.braingames.espanol
- f36704560abc8172433820ecabcef76a – com.piriform.ccleaner
Dell SonicWALL provides protection against multiple versions of this threat via the following signature:
- GAV: AndroidOS.Metasploit.PL (Trojan)