As the world manages voluntary quarantines, mandated isolations, social distancing and “shelter-at-home” edicts, cybercriminals are busy creating malware and other cyberattacks that prey on the fear surrounding the novel coronavirus epidemic (COVID-19).
“More than ever, the public needs to be hyper-aware of the interactions they have online, particularly involving the links and emails they open,” SonicWall Vice President Terry Greer-King told The Sun. “Cybercriminals do their utmost to take advantage of trying times by tricking users into opening dangerous files, through what they consider to be trusted sources.”
While SonicWall Capture Labs threat researchers are constantly investigating and analyzing all threats, the team has flagged the top cyberattacks that leverage coronavirus and COVID-19 to take advantage of human behavior. Here are some of the earliest:
Malicious Archive File: February 5, 2020
In early February, SonicWall Capture Labs used patent-pending Real-Time Deep Memory Inspection (RTDMI) to detect an archive file containing an executable file named CoronaVirus_Safety_Measures.exe. The archive is delivered to the victim’s machine as an email attachment.
After analyzing the executable file, SonicWall found that the file belongs to the GOZ InfoStealer family, which was first detected by SonicWall RTDMI in November 2019.
The GOZ InfoStealer is known for stealing user data from installed applications, along with victims’ system information, which is then sent to the threat actor over Simple Mail Transfer Protocol (SMTP).
The malware author is continuously updating the malware code and changing its infection chain. Details of this analysis are available in this SonicAlert: “Threat Actors Are Misusing Coronavirus Scare To Spread Malicious Executable.”
Coronavirus-Themed Android RAT: February 26, 2020
SonicWall Capture Labs observed a coronavirus scare tactic being used in the Android ecosystem in the form of a Remote Access Trojan (RAT), which is an Android apk that simply goes by the name coronavirus.
After installation and execution, this sample requests that the victim re-enter the pin/pattern on the device and steals it while repeatedly requesting ‘accessibility service’ capabilities.
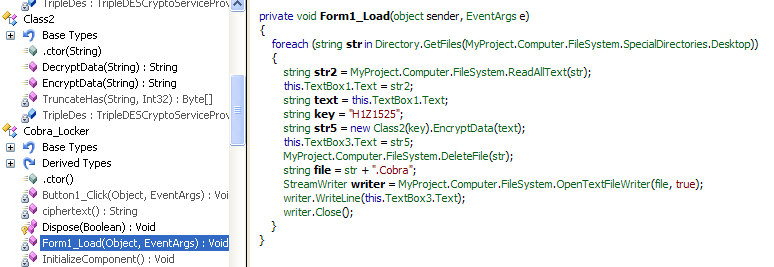
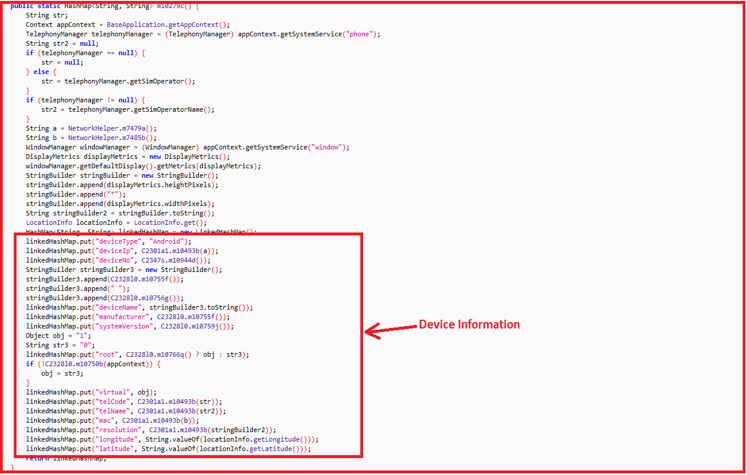
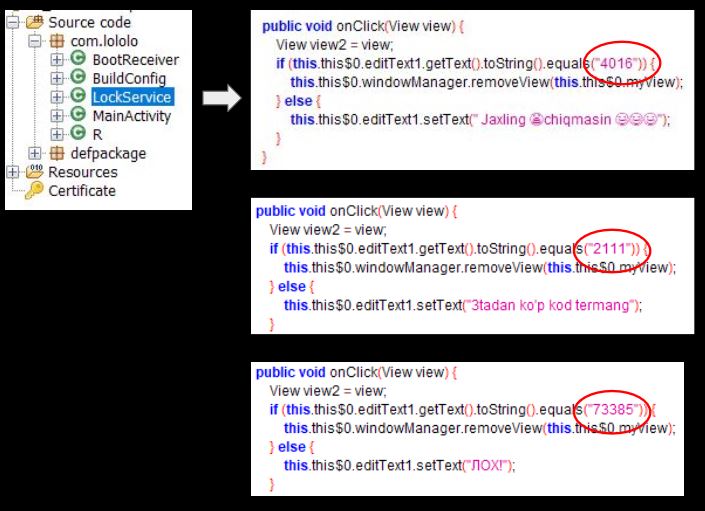
Upon viewing the code structure (below), it becomes apparent that some form of packing/encoding is being used in this sample. The class names appear random, but have a structure in themselves; most class names are of similar length and equally random.
On inspecting the Manifest.xml files, most of the activities listed are unavailable in the decompiled code. This indicates that the ‘real’ class files will be decrypted during runtime. This is a mechanism that makes it difficult for automated tools to analyze the code and give a verdict.
Details of this analysis are available in this SonicAlert: “Coronavirus-themed Android RAT on the Prowl.”
SonicWall Capture Labs provides protection against these threats with the following signatures:
- AndroidOS.Spyware.RT (Trojan)
- AndroidOS.Spyware.DE (Trojan)
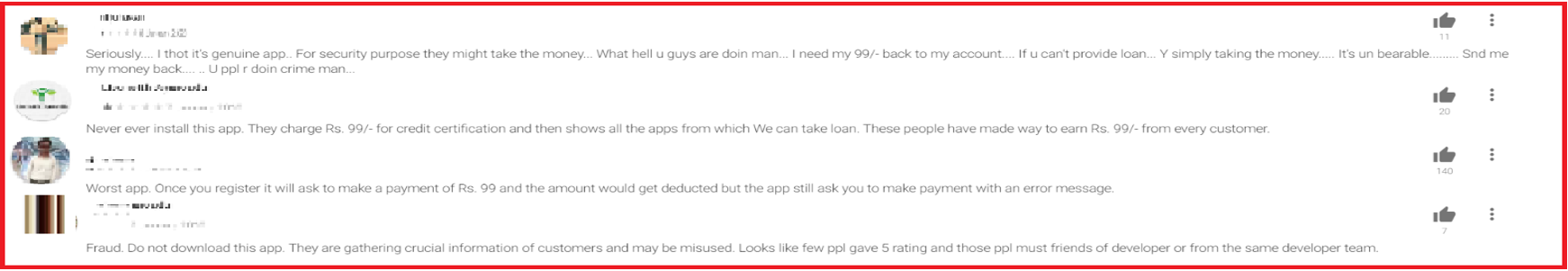
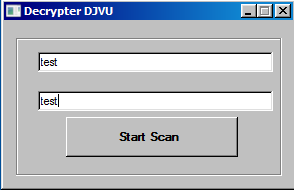
COVID-19 Hoax Scareware: March 13, 2020
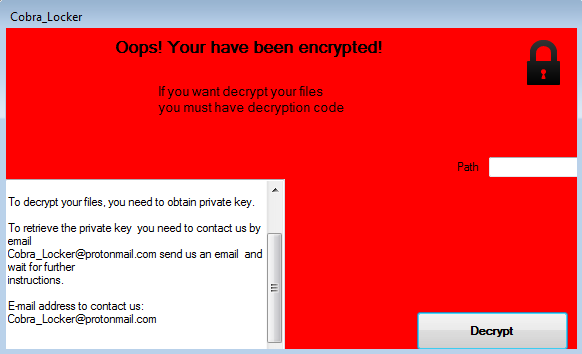
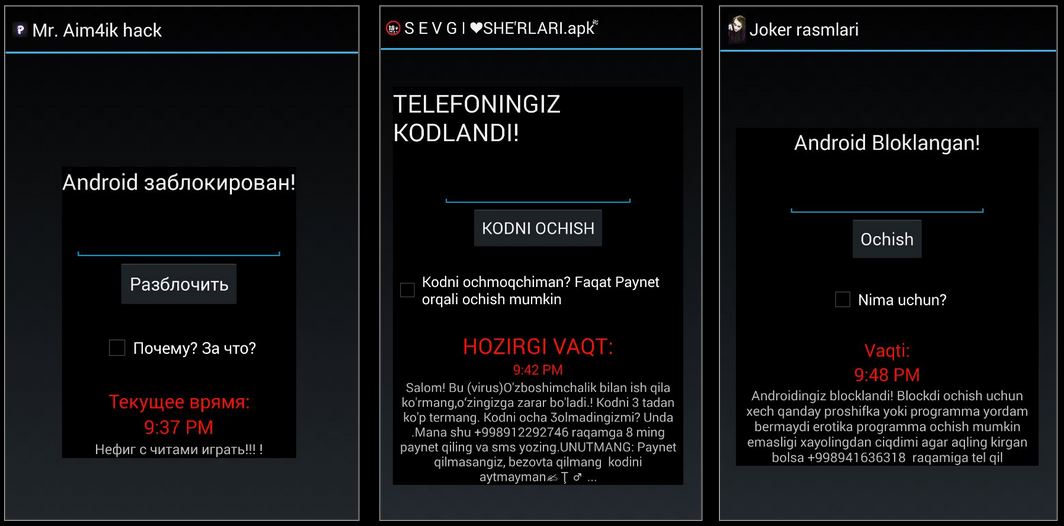
SonicWall Capture Labs threat researchers observed a malware taking advantage of the coronavirus (COVID-19) fears, also known as ‘scareware.’ The sample pretends to be a ransomware by displaying a ransom note (shown below). In reality, however, it does not encrypt any files.
To scare the victim, a number of security warning messages are displayed:
In the end, the malware is benign and hopes fear and human behavior will force victims into paying the ransom. Details of this analysis are available in this SonicAlert: “COVID-19 Hoax Scareware.”
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: Scareware.CoVid_A (Trojan)
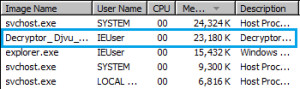
Malicious “Marketing Campaign” Propagates Android RAT: March 14, 2020
SonicWall Capture Labs threat researchers discovered and analyzed malicious campaign websites that currently serve (at the time of publication) Android Remote Access Trojan (RAT) belonging to the same family discovered in February 2020 (see below).
Cyberattackers are creating websites that spread misinformation about coronavirus (COVID-19), falsely claiming ways to “get rid of” the novel virus. Instead, the sites attract new victims via download links.
SonicWall found two main variants of this strategy, one in English and another in Turkish. Both serve the apk named corona.apk when the victim clicks on Google Play image.
Upon downloading the apk file and examining the code, SonicWall found a similar structure to the variant outlined in February. This sample is an Android Remote Access Trojan (RAT) and can perform a number of malicious operations, including:
- Get information about the device
- Get a list of apps installed
- Allow remote control of the device via TeamViewer
- Steal Gmail password and/or lock pattern
- Keylogger
- Upload files
- Steal SMS messages, contacts
- Disable Play Protect
There is a lot of misinformation and panic surrounding coronavirus (COVID-19). SonicWall Capture Labs reiterates that there are no mobile apps that can track coronavirus infections or point to a vaccine. Please exercise extreme caution.
Details of this analysis are available in this SonicAlert: “Misinformation Related to Coronavirus Being Used to Propagate Malicious Android RAT.”
SonicWall Capture Labs provides protection against this threat with the following signatures:
- Spyware.RT (Trojan)
- Spyware.DE (Trojan)
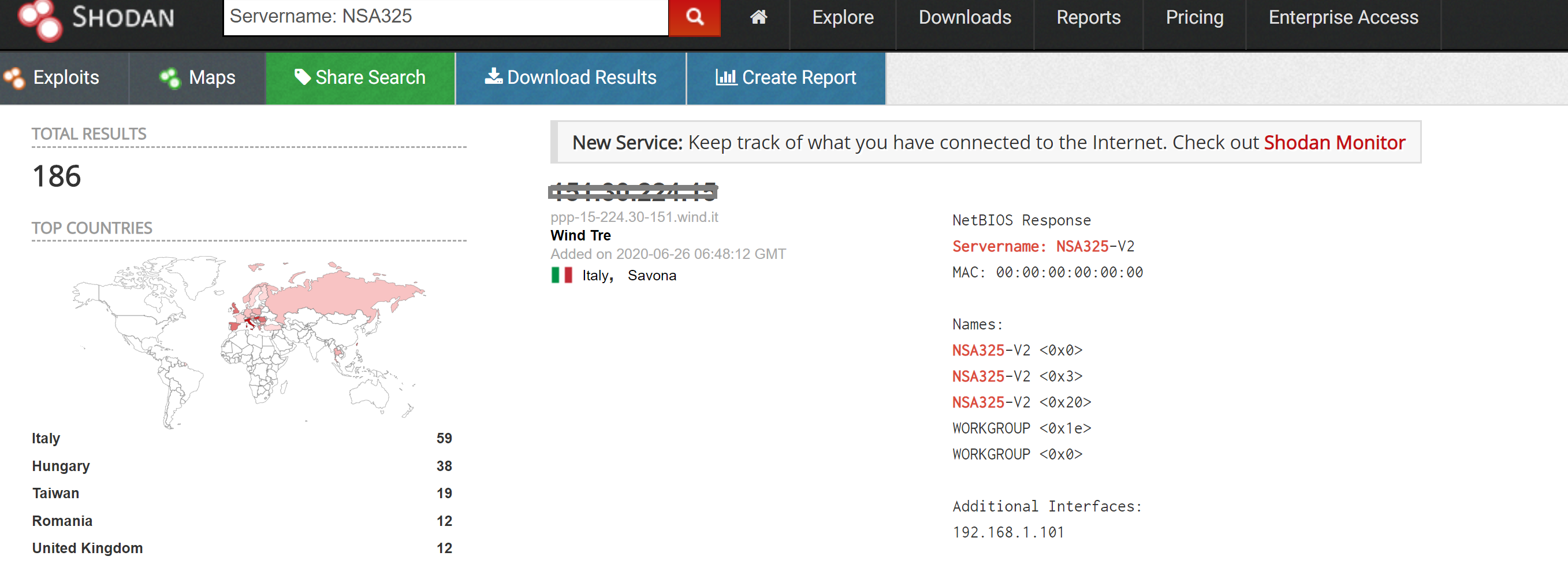
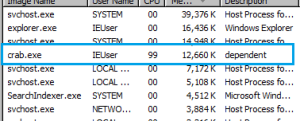
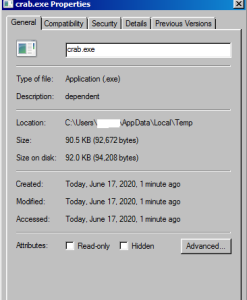
12-Layer Azorult.Rk: March 16, 2020
SonicWall Capture Labs threat researchers found a new sample and activity for the “coronavirus” binary Azorult.Rk. Malware authors have taken advantage of the public’s desire for information on the COVID-19 pandemic since it was first discovered in December 2019 — and it has only escalated since.
Azorult.Rk masquerades as an application providing diagnosis support, even including a screenshot of a popular interactive tool that maps COVID-19 cases and exposure. It includes 12 different layers of static and dynamic information, making it difficult for threat analysts to quickly investigate. This specific analysis serves as a strong primer on how malware authors mask their motives and tactics.
After sorting through the layers, SonicWall found the malware eventually attempted to transmit statistics and metrics of the physical machine hardware, as well usernames, hostnames and much more.
Details of this analysis are available in this SonicAlert: “Coronavirus, COVID-19 & Azorult.Rk.”
SonicWall Capture Labs provides protection against this threat with the following signature:
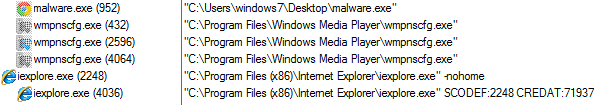
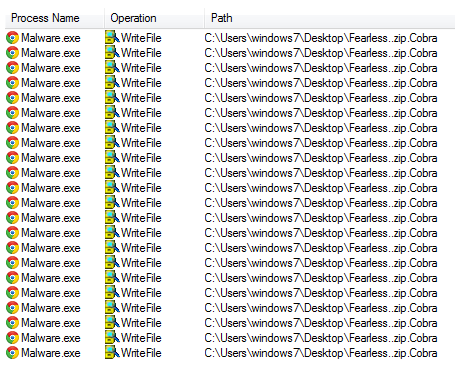
Coronavirus Ransomware: March 19, 2020
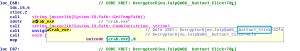
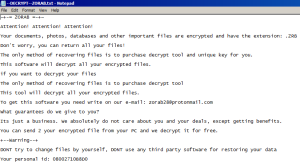
SonicWall Capture Labs threat researchers have observed a new ransomware threat leveraging coronavirus fear. This ransomware encrypts and zips the files and renames it ‘coronaVi2022@protonmail.ch__<filename>’. It then changes the drive name to coronavirus and drops coronavirus.txt in each and every folder of the infected system.
After modifying registration keys, it adds new keys and shows users the following ransom message:
After 20 minutes, it restarts the victim machine and displays yet another ransom note.
Additional details of this analysis are available in this SonicAlert: “Coronavirus Ransomware.”
SonicWall Capture Labs provides protection against this threat with the following signatures:
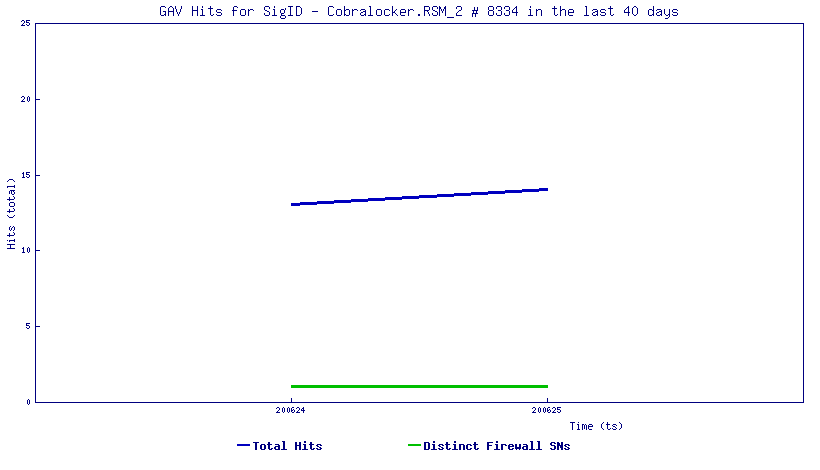
- GAV: CoronaVirus.RSM_2
- GAV : CoronaVirus.RSM
Work-from-Home VPN Solutions for Remote Workforces
To help organizations cost-effectively implement VPN technology for their rapidly expanding work-from-home employees, SonicWall is making its remote access products and services available to both new and existing customers at deeply discounted rates. We’re also bundling critical security solutions for new enterprise and SMB customers.
This special offer provides free Secure Mobile Access (SMA) virtual appliances sized for enterprises and SMBs, and also includes 50% discounts on Cloud App Security and Capture Client endpoint protection when paired with SMA.
These packages were bundled to include everything needed to protect employees outside the network:
To explore the new offers, please visit our special SonicWall promotions page. From there you can review offer details or chat with a SonicWall security expert who can answer questions on how best to quickly scale your remote workforce.