Cybersecurity News & Trends – 09-14-2023
Fall is in the air, and the leaves will soon be changing colors, which is fitting because today is National Coloring Day. SonicWall may not have any crayons, but we’ve been adding some color to the media this week with SonicWall EMEA Vice President Spencer Starkey talking to SC Media about threat geomigration and Security Boulevard citing data from our Mid-Year Cyber Threat Report.
In industry news, Bleeping Computer had the lowdown on the latest Lazarus gang cryptojacking attack as well as the massive cyberattack at MGM Resorts. Tech Crunch covered the near-parallel attack at Caesars Entertainment. Dark Reading reported on a brand-new malware variant with a late-night theme.
Remember to keep your passwords close and your eyes peeled – cybersecurity is everyone’s responsibility.
SonicWall News
How to promote online student safety
Security Boulevard, SonicWall News: Worse yet, cybercriminals are upping the ante with a host of sophisticated new attack vectors. SonicWall identified over 270,000 never-before-seen malware variants in just the first half of 2022 — a 45% year-over-year increase. For perspective, that’s the equivalent of 1,500 new malware strains daily.
UK military data possibly compromised in LockBit attack against third party
SC Media, SonicWall News: “Such an attack shows the persistent risk of cyberattacks faced by governments amid threat geomigration,” according to SonicWall Vice President of EMEA Spencer Starkey. “These cyberattacks raise concerns about a country’s own national security, critical national infrastructure as well as the safety of sensitive information,” Starkey added.
Stealthier Means of Malicious Cyber-Attacks and What It Means for IT Departments
Nasdaq, SonicWall News: Bob VanKirk, CEO, SonicWall, joins Jill Malandrino on Nasdaq TradeTalks to discuss stealthier means of malicious cyber-attacks and what it means for IT departments.
SonicWall: ‘Complacency is the enemy in the cybersecurity game’
Unleash, SonicWall News: SonicWall’s VP of EMEA Spencer Starkey’s topline message to organizations is: “Don’t let the overall data fool you.” Yes, the first quarter of 2023 saw the lowest number of attacks since the fourth quarter of 2019 (51.2 million). However, the second quarter of this year saw the number of attacks rocket to 74% higher than Q1 at 88.9 million. Indeed, SonicWall predicts that ransomware attacks are “poised for a rebound” later this year.
Liongard Expands SonicWall Relationship to Enhance Configuration Change Detection and Response with Capture Client Platform to Mitigate Cybersecurity Risk
Business Wire, SonicWall News: “Extending Liongard’s relationship with SonicWall gives us the ability to inspect and assess across the SonicWall solution portfolio,” said Michelle Accardi, CEO of Liongard, “Our integrated solution will proactively monitor SonicWall Capture Client policy configurations, guarding against human errors and changes, both on and off network. With this comprehensive protection in place, our partners gain effective threat protection, increased visibility and protection, and centralized management.”
SonicWall Promotes Michelle Ragusa-McBain To Global Channel Chief
CRN, SonicWall News: SonicWall has promoted Michelle Ragusa-McBain to head its sizable global partner organization, just months after hiring the channel veteran as its North America channel chief. Looking ahead, SonicWall is planning to roll out a “soft launch” of its revamped SecureFirst Partner Program in September, with a full global launch of the new program planned for February 2024, Ragusa-McBain told CRN.
SonicWall Promotes Cisco Vet to Global Channel Leader
Channel Futures, SonicWall News: SonicWall has promoted Michelle Ragusa-McBain to vice president and global channel leader. She joined SonicWall as vice president and North America channel leader in May. A key theme for SonicWall’s channel strategy is embracing an outside-in approach to crafting its strategy and executing with partners. What that means is we’re listening to our partners and customers more than ever before, rather than operating in a vacuum and telling you what you need.
Ransomware Attacks Skyrocket in Q2 2023
Infosecurity Magazine, SonicWall News: “Ransomware attacks surged by 74% in Q2 2023 compared to the first three months of the year, a new report has found.
The 2023 SonicWall Mid-Year Cyber Threat Report observed two “very unbalanced quarters” regarding the volume of ransomware attacks so far this year. SonicWall Capture Labs Threat Researchers recorded 51.2 million attacks in Q1 2023, representing the smallest number of attacks since Q4 2019.”
How Bitcoin Swings Helped Drive an Almost Nin-fold Surge in Cryptojacking attacks in Europe
DL News, SonicWall News: Cryptojacking attacks skyrocketed when Bitcoin prices fell, and could be the overture to something worse, according to SonicWall researchers. These attacks turn victims’ computers into unknowing crypto mining rigs. Bitcoin reached a $68,000 high in November 2021 before crashing down to as low as just above $16,000 in 2022. It currently hovers around $30,000.
Cryptojacking attacks surge 399% globally as threat actors diversify tactics
ITPro, SonicWall News: Security experts have issued a warning over a significant increase in cryptojacking attacks as threat actors seek to ‘diversify’ their tactics. The volume of cryptojacking attacks surged by 788% in Europe during the first half of the year, with attacks in North America also rising by 345%.
SonicWall: Ransomware Declines Further As Attackers ‘Pivot’ Their Tactics
CRN, SonicWall News: Ransomware continued to lose favor among malicious actors during the first half of 2023, but overall intrusions increased as some attackers switched focus to other types of threats, according to newly released SonicWall data. In the cybersecurity vendor’s report on the first six months of the year, ransomware attack volume dropped 41 percent from the same period a year earlier, the report released Wednesday shows.
Industry News
MGM Resorts Cyberattack Causes IT Shutdown
The main website, online reservation system, and some in-casino services of MGM Resorts International were shut down following a cyberattack this week. As of Thursday, systems have now been down for four full days. The company stated that it began an immediate investigation as soon as it noticed a cyberattack was underway. The systems appear to have been shut down by MGM Resorts itself as a protection measure – not shut down by the hackers. According to a local news outlet, some guests at the resort even reported that their room keys were no longer working. While it appears many systems have been affected, the type of cyber incident that led to this has not been released publicly. A hacking group known as ‘Scattered Spider’ has taken credit for the attack. Scattered Spider is believed to be made up of young adults and teenagers from the United States and United Kingdom. They’ve claimed the attack on MGM but denied involvement with a similar attack on Caesars Entertainment. Dark Reading believes they are responsible for both. This string of attacks on casinos has certainly shaken things up in Las Vegas. It’s unclear when MGM’s systems may come back online at this time. This isn’t MGM Resorts’ first rodeo with cybersecurity incidents. In 2019, hackers stole more than 10 million customer records from the company. Further information should become available as time goes on.
Caesars Entertainment Suffers Massive Data Breach
MGM isn’t the only casino getting hit with cyberattacks this week. On Thursday, Caesars Entertainment reported that hackers had stolen a significant amount of customer data in a cyberattack. The hackers allegedly stole a complete copy of Caesars’ customer loyalty database. The stolen data has loads of sensitive information including Social Security numbers, driver’s license numbers and more. The report from Caesars indicated that they may have paid a ransom to the hackers, stating, “We have taken steps to ensure that the stolen data is deleted by the unauthorized actor, although we cannot guarantee this result.” Some reports claimed Caesars had paid around $15 million to the hackers to stop the leak of its data. The attack was apparently the result of a social engineering attack on a third-party IT company that works with Caesars. Representatives of Caesars Entertainment haven’t responded to any requests for comments but have confirmed that they’ve reached out to relevant law enforcement agencies concerning the breach. The hacking group that has now taken credit for the attack on MGM, Scattered Spider, denies any involvement in the attack on Caesars, but Dark Reading states otherwise.
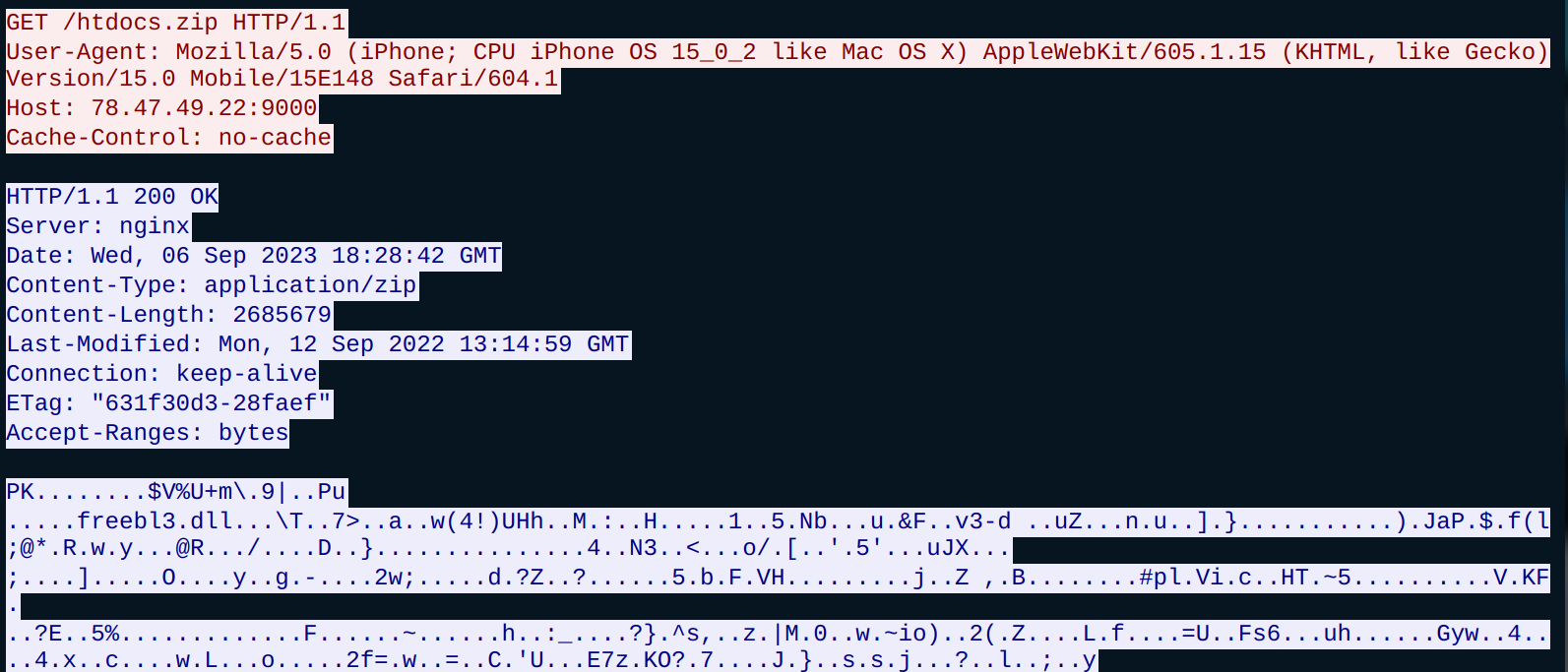
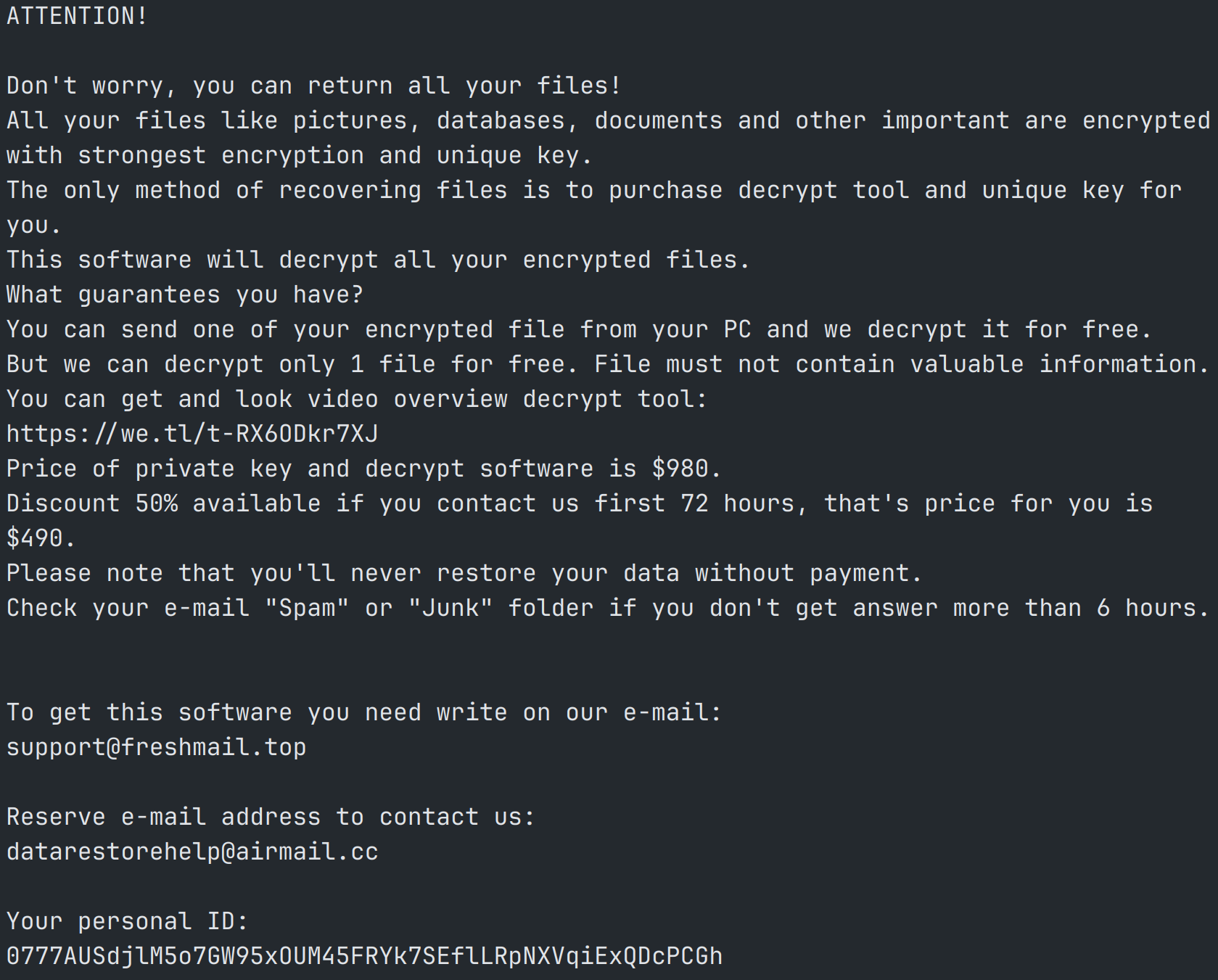
Hackers Unveil Never-before-seen ‘3AM’ Malware After LockBit Fails
Threat actors attacking a construction company using LockBit ransomware had a surprise trick up their sleeve. When the LockBit ransomware failed to infiltrate the network, they pulled out a never-before-seen malware variant called ‘3AM.’ According to Dark Reading, the new malware is nothing to write home about other than its cutesy name, but it did sneak through one computer on the system making the attack successful. After deploying 3AM, a thematic note appeared saying, “Hello, ‘3 am’ The time of mysticism, isn’t it? All your files are mysteriously encrypted, and the systems ‘show no signs of life’, the backups disappeared. But we can correct this very quickly and return all your files and operation of the systems to [sic] original state.” While the note reads like a bad attempt at creative writing, the ransomware was indeed successful. Researchers noted that organizations should expect hackers to have more than one method of attack. An attacker using multiple malware families isn’t unheard of. The best thing any organization can do is have robust cybersecurity capable of thwarting multiple malware variants in place.
CoinEx Loses $53 Million of Cryptocurrency in Cryptojacking Attack
CoinEx, a global cryptocurrency exchange platform, announced this week that cyber attackers had stolen more than $50 million worth of cryptocurrency from them. The stolen cryptocurrencies include Ethereum, Tron and Polygon. CoinEx did state that cryptocurrencies held by its users were not affected by this attack, and if it’s discovered that any have been, the affected parties will receive full compensation from CoinEx. According to Bleeping Computer, a blockchain investigator has linked the attack to North Korea’s Lazarus gang. Lazarus has been responsible for many high-profile cryptojacking attacks this year including attacks on Atomic Wallet, Alphapo and CoinsPaid. At this point, one would almost assume that any high-profile cryptojacking will be linked to Lazarus. Crypto exchanges seem to be the favorite target of the group as of late.
SonicWall Blog
Why Firewall Throughput Numbers Don’t Tell the Whole Story – Tiju Cherian
Elevate Your Network with The Ultimate 3 & Free Promotion – Michelle Ragusa-McBain
Why Education is the New Cybercrime Epicenter – Amber Wolff
How SonicWall Offers High Availability at the Lowest Price – Tiju Cherian
Cryptojacking Continues Crushing Records – Amber Wolff
Why Should You Choose SonicWall’s NSsp Firewalls? – Tiju Cherian
Utilize APIs to Scale Your MySonicWall Operation – Chandan Kumar Singh
First-Half 2023 Threat Intelligence: Tracking Cybercriminals Into the Shadows – Amber Wolff
If It’s Easy, It’s TZ – Tiju Cherian
Sonic Boom: Getting to Know the New SonicWall – Michelle Ragusa-McBain
SonicWall’s Traci McCulley Orr Honored as a Talent100 Leader – Bret Fitzgerald
3 & Free Promotion: How to Upgrade to a Gen 7 NSsp Firewall for Free – Michelle Ragusa-McBain
Monthly Firewall Services Option for Simplicity and Scalability – Sorosh Faqiri

 *Based on data publicly published by Vendor A, current as of 9/1/2023
*Based on data publicly published by Vendor A, current as of 9/1/2023 *Based on data publicly published by Vendor B, current as of 9/1/2023
*Based on data publicly published by Vendor B, current as of 9/1/2023


