Cybersecurity news and trends curated from major news outlets, trade pubs and infosec bloggers.
SonicWall had an excellent news week. The highlight was a report by BBC on over-qualified workers struggling to find jobs, with a quote from Terry Greer-King, SonicWall vice-president for EMEA operations. There were also articles quoting Bill Conner, bylined articles by Immanuel Chavoya, articles citing the 2022 Cyber Threat Report, plus US Representative Elissa Slotkin, from Michigan, who mentioned SonicWall threat data.
Industry news was also very busy. We found a report from ZDNet about crooks using deepfakes to apply for remote work tech jobs. From Bleeping Computer, an alert about the PwnKit exploit on Linux. There was a fascinating report from New York Times about how North Korea used stolen cryptocurrency to keep the country afloat. We have a consolidated report from Dark Reading, WAFB News and Health IT Security on cyberattacks on US healthcare organizations. ZDNet (again) reported on the UK government warning businesses that paying ransoms will not keep their data safe. From HackerNews, Google blocks dozens of malicious domains operated by hack-for-hire groups. And finally, from The Star, the massive AMD breach was aided by “terrible passwords” used by employees.
Remember, cybersecurity is everyone’s business. Be safe out there!
SonicWall News
The Register, Threat Report Mention: “According to SonicWall, there were 304.7 million ransomware attacks in 2021, an increase of 151 percent. In healthcare, the percentage increase was 594 percent.”
BBC, Terry Greer-King Quoted: “They move towards the peak of a pyramid,” explains Terry Greer-King, vice-president of EMEA at cybersecurity firm SonicWall. “As employees gain greater experience, there’s less breadth in terms of opportunities: trying something different would require scaling back down the pyramid.”
Information Age, Immanuel Chavoya Byline: “Immanuel Chavoya, emerging threat detection expert at SonicWall, discusses how businesses can stay protected against customizable ransomware and the wider cyber weapons arms race.”
TechMonitor, Terry Greer-King Quoted: “The toolkits from big RaaS gangs such as REvil are becoming much cheaper and easier to use, agrees Terry Greer-King, vice president for EMEA at SonicWall. “Only a few years ago, they needed to write their own malicious code. Now, anyone with bad intentions can buy a ransomware kit for as little as $50 on the dark web,” he says.”
The Independent, Bill Conner Quoted: ““Organizations and government entities carry a responsibility to consumers and civilians alike to guard their most valuable information at all costs,” Bill Conner, CEO of cybersecurity firm SonicWall and adviser to GCHQ and Interpol, told The Independent. Personal information that does not change as easily as a credit card or bank account number drives a high price on the dark web. This kind of personally identifiable information is highly sought after by cybercriminals for monetary gain. Companies should be implementing security best practices such as a layered approach to protection, as well as proactively updating any out-of-date security devices, as a matter of course.”
Security Boulevard, Threat Report Mention: “According to research from SonicWall, cyber threats of nearly all types are increasing at breakneck speed. Ransomware, for example, has increased 232% since 2019. With the rate of attack accelerating, it’s only logical that school districts close their data protection gap and identify an adequate cloud platform.”
Silicon Republic, Bill Conner Quoted: “Speaking about the latest cyberattacks on Lithuania, Bill Conner, CEO of cybersecurity firm SonicWall, said threat actors have gotten more efficient in their attacks. He added that these groups are leveraging cloud tools to reduce costs and expand their scope in targeting additional attack vectors. “We are dealing with an escalating arms race,” Conner said. “It’s a cyber arms race that will likely never slow, so we can never slow in our efforts to protect organizations. The good news is that the cybersecurity industry has gotten more sophisticated in identifying and stopping new ransomware strains and protecting organizations. There’s better cooperation between the public and private sectors, and greater transparency in many areas.”
SC Magazine, US Representative cites threat report: “Rep. Elissa Slotkin, D-Mich., chair of the Homeland Subcommittee on Intelligence and Counterterrorism, cited research from private cybersecurity company SonicWall claiming a 98% increase in observed ransomware attacks over the past year, while she also noted “we heard from [Michigan] state officials …that ransomware attacks have doubled since last year.”
iNews, Bill Conner Quoted: “Bill Conner, who has advised GCHQ, Interpol and Nato on cyber security and is president and CEO of SonicWall, told: “When you look at what’s happened here in the States, like Colonial Pipeline, our water system, our electrical grids – even though our electrical grids are very different than the UK – they’re still very vulnerable. Our healthcare systems are vulnerable.”
CXOtoday (India), SonicWall Byline: Security teams and the organizations they support live in difficult times: they increasingly are the targets of sophisticated threats developed by a shadowy and very well financed cybercrime industry that has demonstrated it can often outsmart even the most robust security defenses.
CRN (Australia), SonicWall News: “SonicWall has awarded Australian partners Dicker Data, Hitech Support, Next Telecom, Datacom System and Dell Australia for their work at its Asia-Pacific Partner Awards for the 2022 financial year.”
Industry News
ZDNet: According to the FBI, scammers and criminals use deepfakes to steal personally identifiable information when they apply for remote jobs. Deepfakes, synthetic audio, video and image content created using AI or machine-learning technology have been a concern for phishing threats for many years.
The FBI’s Internet Crime Complaint Center (IC3) says they have seen increased complaints about deepfakes and stolen personally identifiable information used to apply for remote roles in tech. Some offices are asking employees to return to work. Information technology is one job category that has seen a lot of remote work. Reports to IC3 primarily concern remote vacancies in information technology programming, database, or software-related job function functions.
The FBI highlights the dangers of an organization hiring fraudulent applicants by noting that some of the positions reported include access to financial data and customer PII.
Bleeping Computer: Cybersecurity and Infrastructure Security Agency has added PwnKit, a severe Linux vulnerability, to its bug list.
CVE-2021-4034 was identified as the security flaw in Polkit’s Polkit’s Pkexec component, which is used by all major distributions, including Ubuntu, Fedora and CentOS. PwnKit is a memory corruption bug that unprivileged people can exploit to gain full root rights on Linux systems with default configurations.
It was discovered by researchers at Qualys Information Security, who also found its source in the original commit of pkexec. This means that it affects all Polkit versions. It has been hidden in plain sight since May 2009, when pkexec was first released. The proof-of-concept (PoC) exploit code was posted online within three hours of Qualys publishing technical details about PwnKit.
New York Times: North Korea has suffered severe economic damage from the United Nations sanctions and coronavirus pandemic. The government warned of severe food shortages. Unidentified intestinal diseases began to spread among the population in June.
Yet, the country has conducted more missile tests than any other year. The government is providing luxury homes for party elites. North Korea’s leader Kim Jong-un has pledged to create advanced technology for its growing arsenal of weapons. The country will likely conduct a new nuclear test, its seventh, in the not-too-distant future.
Where did the money come from?
In April, the United States publicly accused North Korean hackers of stealing $620 million in cryptocurrency from Axie Infinity. This theft, the largest of its kind, is the most substantial evidence that North Korea’s use of cryptocurrency heists to raise money to support its regime during the pandemic and fund its weapon development and maintenance was highly profitable.
According to Chainalysis, North Korean hackers could have taken home nearly $400 million worth of cryptocurrency last year. North Korea’s total haul this year is just under $1 billion. These figures are to be viewed in context. According to South Korea’s statistical agency, $89 million was earned in official exports for the country in 2020.
Dark Reading: The FBI, US Cybersecurity and Infrastructure Security Agency and Treasury Department warned Wednesday about North Korean state-sponsored threat agents targeting US healthcare and public-health organizations. These attacks are using a new, unusually operated ransomware tool called Maui.
Multiple incidents have occurred since May 2021 in which threat actors using the malware have encrypted servers critical to healthcare services. They have also attacked digital diagnostic devices and electronic health records servers.
In a related story from WAFB News and Health IT Security, hospitals in Wisconsin, Georgia, and Louisiana reported separate healthcare cyberattacks. Reports of healthcare cyberattacks continue to roll in as threat actors advance their tactics and narrow in on widespread vulnerabilities in the sector. For example, at Baton Rouge General, LA, a Mayo Clinic care network member, reports of a cyberattack emerged on June 28. As of this report, the hospital has reverted to paper records. Other hospitals report various damage from system lockouts to compromised patient and employee records.
ZD Net: The number of businesses paying a ransom following a ransomware attack is increasing. The UK’s National Cyber Security Centre (NCSC) and Information Commissioner’s Office (ICO) are asking attorneys to remind their clients that paying up may not keep their data safe.
In a joint letter, The NCSC and ICO noted a rise in ransomware payments. Also, they reasoned that some attorneys may have advised clients to pay ransoms to keep their data safe or avoid a financial penalty from ICO. However, both agencies warn that not only are ransom payments not condoned; such payments only serve to encourage hackers to push on with more attacks.
The joint letter also reminds UK businesses and organizations that ransom payment offers no guarantee that hackers will return data or keep it safe. They note that even though hackers provided an encryption key, some do not work correctly. It is also possible that cyber criminals may not keep their word and delete data stolen in a ‘double-extortion’ attack to intimidate victims into paying.
The Hacker News: Google’s Threat Analysis Group (TAG), Thursday’s disclosure by the Hacker News, revealed that it had blocked as many as 36 malicious websites operated by hacker-for-hire groups from India, Russia, or the UAE.
Hack-for-hire companies allow their clients to launch targeted attacks against corporates, activists, journalists, and other high-risk users like the surveillance ware environment. These operators are known to carry out intrusions on behalf of clients anxious to hide their roles in the attack.
One hack-for-hire operator allegedly launched a recent attack on an IT company in Cyprus, a financial technology company in the Balkans, a Nigerian education institution, and an Israeli shopping company to demonstrate the breadth of the victims affected.
An identical set of credential theft attacks against journalists, European politicians and non-profits was linked to a Russian threat actor named Void Balaur.
The same group may have also been working for the past five years to target individual accounts at major webmail providers such as Gmail, Hotmail and Yahoo! plus regional webmail providers such as abv.bg, mail.ru, inbox.lv and UKR.
The Star: The Silicon Valley tech giant AMD was hit by a data breach last week. But that’s no big news. According to this story, what’s utterly amazing is that the hackers had help from employees using terrible passwords such as “password” and “123456.
According to SF Gate, AMD, a microchip manufacturer, was attacked by RansomHouse hackers.
In a statement, the semiconductor giant confirmed that there was a digital breach. But the company had no answers asked why employees of multinational manufacturers aren’t subject to standard password protection rules such as regularly changing passwords and including numbers and symbols in passwords.
Lesson learned: breaches are increasing — time has long since passed to take the threat seriously.
In Case You Missed It
Enhance Security and Control Access to Critical Assets with Network Segmentation – Ajay Uggirala
Three Keys to Modern Cyberdefense: Affordability, Availability, Efficacy – Amber Wolff
BEC Attacks: Can You Stop the Imposters in Your Inbox? – Ken Dang
SonicWall CEO Bill Conner Selected as SC Media Excellence Award Finalist – Bret Fitzgerald
Cybersecurity in the Fifth Industrial Revolution – Ray Wyman
What is Cryptojacking, and how does it affect your Cybersecurity? – Ray Wyman
Why Healthcare Must Do More (and Do Better) to Ensure Patient Safety – Ken Dang
SonicWall Recognizes Partners, Distributors for Outstanding Performance in 2021 – Terry Greer-King
Anti-Ransomware Day: What Can We Do to Prevent the Next WannaCry? – Amber Wolff
CRN Recognizes Three SonicWall Employees on 2022 Women of the Channel List – Bret Fitzgerald
Enjoy the Speed and Safety of TLS 1.3 Support – Amber Wolff
Four Cybersecurity Actions to Lock it All Down – Ray Wyman
Understanding the MITRE ATT&CK Framework and Evaluations – Part 2 – Suroop Chandran
Five Times Flawless: SonicWall Earns Its Fifth Perfect Score from ICSA Labs – Amber Wolff
NSv Virtual Firewall: Tested and Certified in AWS Public Cloud – Ajay Uggirala
How SonicWall’s Supply-Chain Strategies Are Slicing Wait Times – Amber Wolff
SonicWall SMA 1000 Series Earns Best-Of Enterprise VPNs Award from Expert Insights – Bret Fitzgerald
World Backup Day: Because Real Life Can Have Save Points Too – Amber Wolff
CRN Honors SonicWall With 5-Star Rating in 2022 Partner Program Guide – Bret Fitzgerald
Cyberattacks on Government Skyrocketed in 2021 – Amber Wolff
Meeting the Cybersecurity Needs of the Hybrid Workforce – Ray Wyman
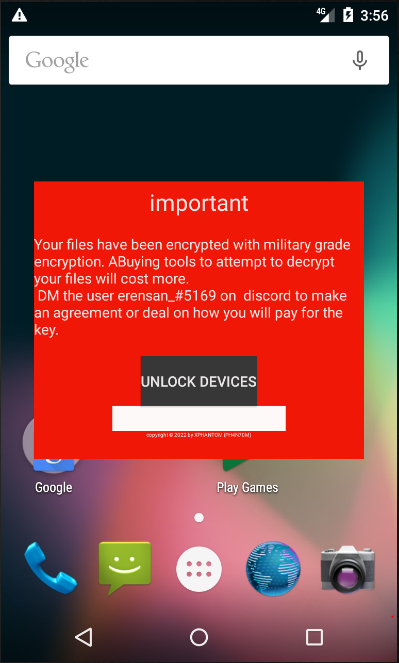
![]() Figure 1: Ransomware App Icons
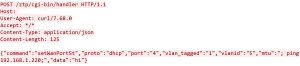
Figure 1: Ransomware App Icons Figure 2: VirusTotal submission history
Figure 2: VirusTotal submission history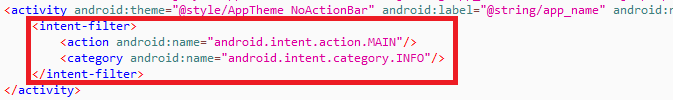 Figure 4: Main activity launcher missing
Figure 4: Main activity launcher missing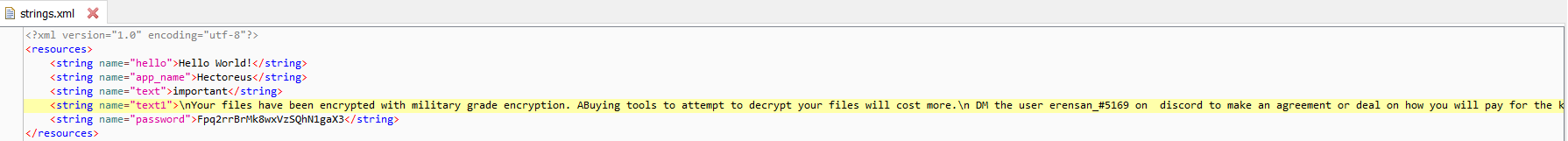 Figure 6: Password and Ransom note present in code
Figure 6: Password and Ransom note present in code