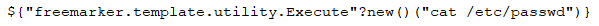VMware Workspace ONE Access & Identity Manager (vIDM) RCE Vulnerability
Overview:
VMware’s Workspace ONE Access, VMware Identity Manager (vIDM), vRealize Lifecycle Manager, vRealize Automation, and VMware Cloud Foundation products; contain a remote code execution vulnerability due to server-side template injection. A remote, unauthenticated attacker can exploit this vulnerability by sending crafted requests to the server. If the injection is successful, the attack (exploit) will result in a remote code execution (RCE) which could lead to information disclosure, addition or modification of data or denial-of-service conditions. VMware has confirmed that exploitation of CVE-2022-22954 has occurred in the wild.
CVE Reference:
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2022-22954.
Common Vulnerability Scoring System (CVSS):
The overall CVSS score is 9.8 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H).
Base score is 9.8 (AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H), based on the following metrics:
• Attack vector is network.
• Attack complexity is low.
• Privileges required is none.
• User interaction is none.
• Scope is unchanged.
• Impact of this vulnerability on data confidentiality is high.
• Impact of this vulnerability on data integrity is high.
• Impact of this vulnerability on data availability is high.
Temporal score is 9.8 (E:X/RL:X/RC:X), based on the following metrics:
• The exploit code maturity level of this vulnerability is not defined.
• The remediation level of this vulnerability is not defined.
• The report confidence level of this vulnerability is not defined.
Technical Overview:
SSTI(server-side template injection) attacks can occur whenever user input is concatenated directly into a template, rather than being passed in as data. Moreover, attackers can manipulate the template engine by injecting arbitrary template directives.
An attacker can execute commands and reverse shell payloads that could potentially result in Remote Code Execution; granting complete server control.
The URL encoded string given as a parameter to the “deviceUdid” argument is:
Triggering the Problem:
• The target must be running a vulnerable version of the software.
• The attacker must have network connectivity to the vulnerable server.
• The target must have network connectivity to the attacker controlled server.
Triggering Conditions:
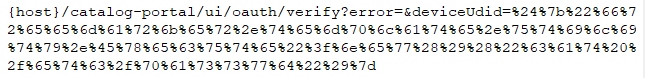
Using the maliciously crafted request; the vulnerability is triggered after the target receives the request below.
Vulnerable Versions:
VMware Workspace ONE Access Appliance – 21.08.0.1, 21.08.0.0, 20.10.0.1, 20.10.0.0
VMware Identity Manager Appliance – 3.3.6, 3.3.5, 3.3.4, 3.3.3
Attack Delivery:
The following application protocols can be used to deliver an attack that exploits this vulnerability:
• HTTP,
• SSL/TLS
Client GET Request Below:
SonicWall’s, (IPS) Intrusion Prevention System, provides protection against this threat:
• IPS: 2642 VMware Workspace ONE Access Server Side Template Injection 1
• IPS: 2649 VMware Workspace ONE Access Server Side Template Injection 2
• IPS: 2651 VMware Workspace ONE Access Server Side Template Injection 3
Remediation Details:
The risks posed by this vulnerability can be mitigated or eliminated by:
• Applying the vendor supplied patch.
• Detecting and blocking malicious traffic using the signatures above.
The vendor has released the following advisory regarding this vulnerability:
Vendor Advisory