New fake codec malware (May 15, 2009)
SonicWALL UTM Research team came across a new Fake codec malware drive-by site posing to contain nude Rihanna video.
The drive-by site was actively serving the malware at the time of posting this alert:
www.scribd.com/(REMOVED)/Rihanna-nude | --> http://tumler(REMOVED)/2.html | --> http://xtube-host.com/(REMOVED)Mediacodec_v3.7 | --> Mediacodec_v3.7.exe (1,984,538 bytes) detected as GAV: FakeAlert.BDP (Trojan)
The downloaded malware executable file looks like:

It performs the following activity on the victim machine:
- Creates multiple directories including (App Data)PCenter and (Program Files)PCenter.
- Drops multiple files including (Program Files)PCenteragent.exe and (Program Files)PCenterpc.exe.
- It adds registry keys to ensure that agent.exe and pc.exe starts every time on system reboot:
- HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionRunagent.exe = “(Program Files)PCenteragent.exe”
- HKEY_CURRENT_USERSoftwareMicrosoftWindows NTCurrentVersionWinlogonShell = “(Program Files)PCenterpc.exe”
- It creates following mutex objects to mark its presence on the system:
- AMResourceMutex2
- VideoRenderer
- It sends HTTP request to below URLs:
- http://194.165.4.(REMOVED)/software_response.php?uid=1235
- http://privacyupdate447.com/avail
The screenshots of the drive-by site and the Fake codec Trojan being downloaded are shown below.
Main site posing to host nude Rihanna video:

When user attempts to start the video, it opens a new page asking the user to download a certified ActiveX video codec (VAC codec) to protect content Copyrights. The page looks like below:
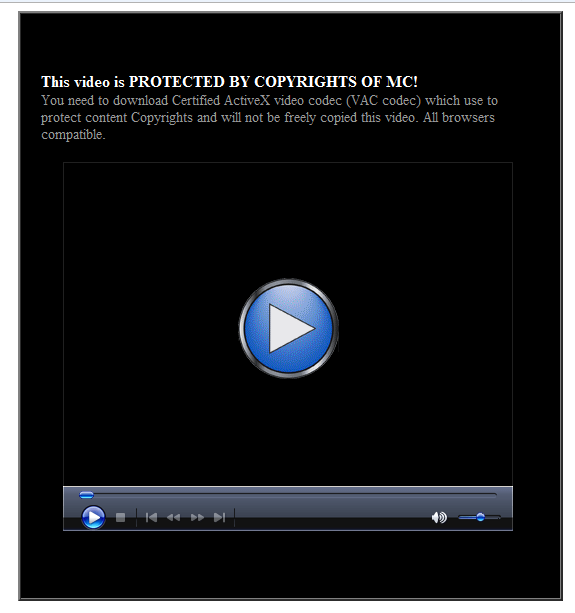
If the user clicks on the video frame again then it downloads the malware executable file as seen below:

The Trojan is also known as Win32/Adware.PrivacyComponents [ESET], Trojan.FakeAlert.BDP [BitDefender], and Cryp_FakeAV-12 [Trend Micro].
SonicWALL Gateway AntiVirus provides protection against this malware via GAV: FakeAlert.BDP (Trojan) signature.



