Cybersecurity News & Trends – 04-29-22
Cybersecurity News & Trends
This week, SonicWall is on a winning streak with another strong showing in general news and industry press. There were continued mentions of the 2022 SonicWall Cyber Threat Report, new product reviews, and partner news. In industry news, the Tenet healthcare network suffered a cyberattack that disrupted operations at two hospitals in Palm Beach, FL. While cyberattacks rage in Ukraine, US Intel warns of fresh attacks on US targets by state-sponsored cyber gangs from China, Russia, and North Korea. Krebs is following a developing situation where hackers are using fake Emergency Data Requests (EDRs) to gain fraudulent law enforcement actions that can compromise companies and agencies. Meanwhile, JPMorgan is getting sued for a hack, the US State Department antes $10M for information about Russian hackers, the malware loader Bumblebee is loose, and experts examine predictive analytics for cybersecurity.
SonicWall News
Cyberwar Zone: Biden, Experts Warn Business Attacks are Coming
Virginia Business, News: But many cybercrimes go unreported, and private sector numbers paint a far worse picture. Cybersecurity firm SonicWall reports that its researchers recorded 623.3 million ransomware attacks worldwide in 2021 — a 105% increase from 2020.
What Should You Do If Your Brand is the Target of a Data Breach?
TFL, Threat Report Mention: The same is true in the U.S., with ransomware attacks, alone, rising by almost 100 percent in 2021 according to SonicWall’s 2022 Cyber Threat Report.
SonicWall Virtual Firewall Tested and Certified in AWS Public Cloud – Ideal for Distributed Networks
Markets Insider, News: SonicWall today announced a new report by The Tolly Group, which detailed the testing and analysis of the performance of the SonicWall NSv 470 virtual firewall. Using Keysight’s CyPerf cloud-native testing solution to provide the test infrastructure for standardized, repeatable performance tests, Tolly benchmarked the throughput and connection performance of the virtual firewall in Amazon Web Services (AWS).
For Over 30 Years, Jeff Dann Has Had the People, Process, And Technology To Ensure Their Customers Are Protected
MSP Success, Threat Report Mention: SonicWall reports there were 304.7 million ransomware attacks, 51.1 million crypto-jacking attacks, and 32.2 million IoT malware attacks in 2021. The report states that attackers targeted web applications with financial and personal information for a big payday.
The Industry Takes Stock of Cyberattacks In Hawaii
Pacific Inno, News: Each year, the SonicWall Cyber Threat Report uncovers insights extracted from global cyberthreat data collected and analyzed by expert researchers. SonicWall calls its report “the world’s most quoted ransomware threat intelligence,” and it is an annual snapshot of the threat landscape, helping business and government leaders make informed decisions about cybersecurity.
Learn how NLP Can Help to Understand the Cyber-Exposure And The Silent Cyber
Intelligent Insurer, Threat Report Mention: Corporate IT teams handled 623 million ransomware attacks in 2021, up 105% year on year, according to security vendor SonicWall. The firm reports an 1,885 percent increase in attacks on government targets, healthcare (755 percent), education (152 percent) and retail (21 percent).
Cyber Threats to Media Companies Are on The Rise
E&P, Threat Report Mention: Reporter Amiah Taylor explained ransomware research by SonicWall, an internet cybersecurity company, and its 2022 Cyber Threat Report, which offers some alarming statistics about ransomware attacks, in particular governments worldwide saw a 1,885% increase in ransomware attacks, and the health care industry faced a 755% increase in those attacks in 2021.
How To Choose the Best VPN For Security and Privacy
CSO Magazine, Product Mention: For example, SonicWall’s Mobile Connect supports Ping, Okta and OneLogin identity providers.
Privacy Coin Monero’s Use in Ransomware Fuels Growing Security Concerns
PYMNTS.com, Threat Report Mention: That comes as ransomware is exploding, with attacks up 105% last year, according to the 2022 Cyber Threat Report released in February by cybersecurity company SonicWall.
Industry News
Tenet Says, ‘Cybersecurity Incident’ Disrupted Hospital Operations
Healthcare Dive: Tenet is one of the largest US for-profit health systems. It reported that it suffered a cybersecurity incident last week, which disrupted some acute care operations. According to the statement issued Tuesday by the Texas-based operator, most critical functions have been restored, and affected facilities are beginning normal operations. Tenet did not disclose the nature or extent of the incident or the affected facilities. It also didn’t say whether hackers accessed any patient data.
SC Media and CBSNews affiliate WEPC offered additional details on the incident, reporting that the attack forced caregivers to chart patient care using paper because the network’s phone and computer systems were down. As a result, the company’s “acute care operations” at Good Samaritan Hospital in West Palm Beach and St. Mary’s Medical Center were temporarily interrupted.
Cyberattacks Rage in Ukraine, Support Military Operations
Threat Post: At most, five advanced persistent threats (APTs) are believed to be behind attacks tied to ground campaigns that aim to harm Ukraine’s digital infrastructure. Five state-sponsored APT groups are behind the attacks on Ukraine that started in February. The groups used the cyberattacks against Ukraine strategically to support the ground campaign. Microsoft published research on Wednesday that revealed that Russia had state-sponsored the APTs in the campaign.
Separate reports this week shed light on cyberattacks against Ukrainian digital assets carried out by APTs linked to Russia. Microsoft researchers have found that six distinct Russia-aligned threat agents carried out 237 cyber operations, resulting in threats to civilian welfare. They also attempted to launch dozens of cyber espionage attempts against Ukrainian targets.
US Intel, Google Warn of Cyberattacks from China, Russia, North Korea
Newsweek: In the past month, intelligence agencies, President Joe Biden and large companies such as Google all issued the same warning — sounding alarms about the growing threat of cyberattacks coming from foreign governments. Christopher Wray, Director of the Federal Bureau of Investigation, stated that the People’s Republic of China and the Chinese Communist Party are the biggest threats to the country’s counterintelligence. He said they target our innovation, trade secrets, and intellectual property at a scale never before seen in history. According to Google’s Threat Analysis Group (TAG), Iran, North Korea and Russia are the top cyberattacks on the US.
Fighting Fake EDRs with ‘Credit Ratings’ for Police
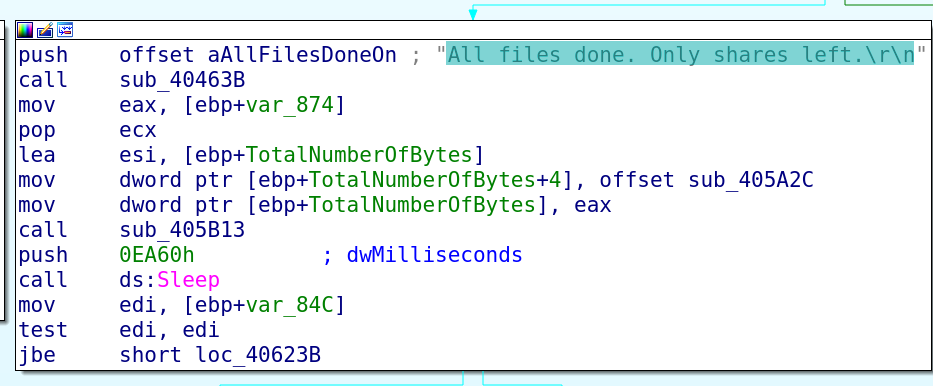
Krebs On Security: The Krebs security team recently examined how cybercriminals used hacked email accounts of police departments worldwide to obtain warrantless Emergency Data Requests from technology providers and social media companies. Many security experts called it an insurmountable problem. Matt Donahue is a former FBI agent who recently left the agency to start a startup to help tech companies screen out fraudulent law enforcement data requests. This includes assigning credit ratings or trustworthiness to law enforcement agencies worldwide.
Manufacturer Sues JPMorgan After Cybercriminals Stole $272m
Computer Weekly: Essilor Manufacturing sued JP Morgan, alleging that the bank failed to report suspicious activity, leading cybercriminals to steal $272 million. According to reports, Ray-Ban sunglasses’ French manufacturer claimed that the bank failed to notify them of suspicious activity in New York. As a result, the manufacturer claimed an increase in money transactions and money sent to offshore companies in high-risk countries in papers filed in Manhattan federal court.
State Dept Offering $10 Million For Information on Russian Cybercriminals
The Hill: The State Department has announced it is offering a reward of up to $10 million for information on a group of Russian cybercriminals. The department released a press release on Tuesday stating that its Rewards for Justice program (RFJ) is looking for information about six people who are allegedly involved in a criminal conspiracy involving malicious hacking activities that affect the critical infrastructure of the United States. According to the State Department, these individuals were part of a criminal conspiracy that infected computers with destructive malware in June 2017. The malware was called NotPetya.
Cybercriminals Using New Malware Loader’ Bumblebee’ in the Wild
Hacker News: The cybercriminals who were previously seen delivering IcedID and BazaLoader as part of their malware campaigns may have switched to a new loader called Bumblebee, which is currently actively being deployed. Researchers report that Bumblebee may be the new multifunctional tool of choice for spreading malware based on cybercriminals’ timing and early proliferation of the loader. The new loader was distributed in March 2022. There are overlaps between malicious activity and Conti ransomware deployments.
Predictive Analytics could be the Future of Cybersecurity
Analytics Insight: While it might not be possible to prevent every data breach, it is possible to minimize the risk. Even the most skilled cyber professionals admit that it is impossible to control all data breaches. It is impossible to stop determined hackers from getting into systems. This is not because they are too sophisticated; even the most experienced security professionals fall prey to human error. Nevertheless, it is possible to minimize the risk, which is good news. Organizational leaders must accept this fact as soon as possible. It is best to assume that data breaches will happen and set up cyber defenses to reduce the damage. A crisis checklist can help prepare for the worst.
In Case You Missed It
Five Times Flawless: SonicWall Earns Its Fifth Perfect Score from ICSA Labs – Amber Wolff
NSv Virtual Firewall: Tested and Certified in AWS Public Cloud – Ajay Uggirala
How SonicWall’s Supply-Chain Strategies Are Slicing Wait Times – Amber Wolff
SonicWall SMA 1000 Series Earns Best-Of Enterprise VPNs Award from Expert Insights – Bret Fitzgerald
World Backup Day: Because Real Life Can Have Save Points Too – Amber Wolff
CRN Honors SonicWall With 5-Star Rating in 2022 Partner Program Guide – Bret Fitzgerald
Cyberattacks on Government Skyrocketed in 2021 – Amber Wolff
Meeting the Cybersecurity Needs of the Hybrid Workforce – Ray Wyman
Third-Party ICSA Testing – Perfect Score Number 4 – Kayvon Sadeghi
Ransomware is Everywhere – Amber Wolff
Shields Up: Preparing for Cyberattacks During Ukraine Crisis – Aria Eslambolchizadeh
Capture Client 3.7: Rapid Threat Hunting with Deep Visibility and Storylines – Suroop Chandran
2021 Threat Intelligence Shows Attacks Rising Across the Board – Amber Wolff
Break Free with SonicWall Boundless 2022 – Terri O’Leary
SonicWall’s Bob VanKirk, HoJin Kim & David Bankemper Earn 2022 CRN Channel Chief Recognition – Bret Fitzgerald
Don’t Let Global Supply Chain Issues Impact Your Security – Kayvon Sadeghi
Unpacking the U.S. Cybersecurity Executive Order – Kayvon Sadeghi
Everything Old Is New Again: Remote Access Comes Full Circle – James Whewell