Valak Initial Infection
Overview:
SonicWall Capture Labs Threat Research Team recently observed new activity for Valak. The Valak malware campaign is usually found lurking inside your email inbox or spam folder. The distribution of Valak is attached to an email with a password-protected zip attachment containing a Microsoft related document. Over the last six months or so, Valak has switched from password-protected zip files to HTTP hyperlinks instead.
An example of the HTTP hyperlink:
http://centruldeinfoliere.ro/_qRlDMkyWtPIbz7M5.php?x=MDAwMyBNY5KWcZGMy8k0oIxYUVH2_-u1yUh7ZePvmuNyclVUgcLADWz6g4R0fHir0QUTpjr0UBdTZZveY32hmH7Fx_mkyU3ULfkkoyPTm1HAbKKfvdiUO6QsABHKdzpaK9i6kwgErffcRV6BvyQKLhcSJA~~&y=Ry5fTWljaGFlbCdzX0Jpc3Ryb18mX0Jhci56aXA=
Files returned from the URL above listed as SHA256 hash and file size:
– 691e4c75b51448ffb1cb031dea5950ce18fdc843a75a4775f82276c4838d071a File-size: 112,611 bytes
– d3486e1ed6f486f1ca391d9a7b03def818bc977dce3902436d176fa9f7e93289 File-size: 113,635 bytes
– 19cba4e01f15b628ebd46ac48c4b4a28c515c3bb1fd65572970e8b8701ebd874 File-size: 111,587 bytes
Example filename: G._Michael’s_Bistro_&_Bar.zip
SHA256 hashes and document names… (Macro Inside Sample Is For Valak):
– 84a07333851ed300b34b34a026a58636844861e2d5265f2faabddddf05815f21 direct.07.20.doc
– deb7d8bd4c03fac7e23dcbd1e77d9b9d70939072bb13ee884fe6c12ac2f95b99 docs,07.01.2020.doc
– 3eea8f8774723f76413ae73643e0da254837edca2dcefddc8981e2f1f0d871db document_07.20.doc
– 41fdd6d39d225d97db624d1cf2edb76cedaf051b909cdfd100be3e473dcad1f8 file 07.20.doc
– cadc90fa3cf275745d9f925b1cc0d85e5ae44c03b7e904212cb3c91656d0c021 instruct.07.20.doc
– ddf5af999b9ce2eb55e056a84a0185f199f56786986599f02586943d6615ce39 legal agreement-07.20.doc
– 16e28494025fa62cfc22e7d22ff11c47aee04ebff4e7d76f9393499d4f7c72f1 question,07.20.doc
– 8a71f3e2f7bd40f2c98bbe0257e925408cc1c2a56d5a0b70961304609d6e0a72 question_07.01.2020.doc
Today we are going to peek inside the initial Valak DLL retrieved by a Microsoft related document macro. This DLL is provided inside many other hyperlinks listed below:
URLs that supply Valak DLL from documents:http://407.cd.gov.mn/_W54sEoZKl-m2w6RZ.php/?x=MDAwMSDquFjnnQfNskuQwXSFpyH0Z9_qXomuRTk0GI_JRu_fKoAz7nCHxvKoT8dz8tAtY6hCXcf7As15lmDc9hy783iLCvBjCDIJbjSKoo-yMGxsQeXacHaexrHhGtmbv6dHXB6EcntdaN8Mkiq-pA_sQw~~
https://bangrajan.org/wp-content/uploads/_m8CVdv47q2JCqgaq.php?x=MDAwMSD_acsCi6_1dic7V-Dk5gCE0DDV3NvQOyIDSnpYLVbLeUSOtixzS9j5_-xegs4j_zu5Lm49dFEVSaWhi1PlZnUr0Pw2gDPaJKfcHs2rPGyw94m8hYSKaHfJSB6c2WK5JcwPXSZMKLoHTbP2UWuljg~~
http://centruldeinfoliere.ro/_qRlDMkyWtPIbz7M5.php?x=MDAwMSDKSoJE5lV1GKwb4Ub-pzqjnaQZjzWFvlOnWNYSs9gYKoCD5q1mXjEObRFguTFtWGu6AKCDSBglzHJ-vYeohvLg55dXJ5Zue890q8jHP2jdoP1Tww5YIL58J7-m0i2BPW9hrbOVFEUAgh9TOtEJzQ~~
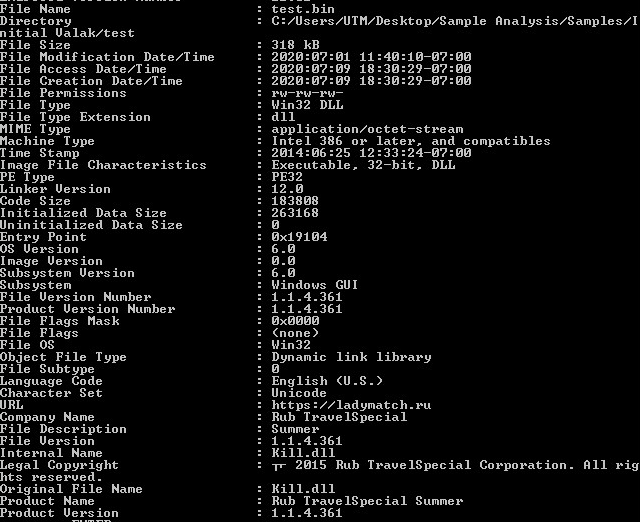
DLL Sample Layer, Static Information:
Looking at the first layer in CFF Explorer, checking for corruption. The first layer is a Native Windows DLL binary.
Static Command-Line Information:
Dynamic Information:
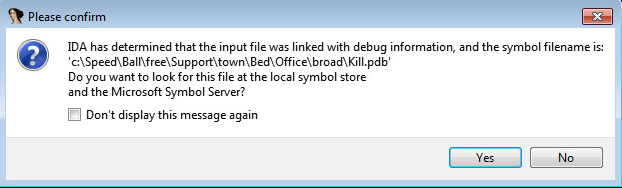
PDB Information:
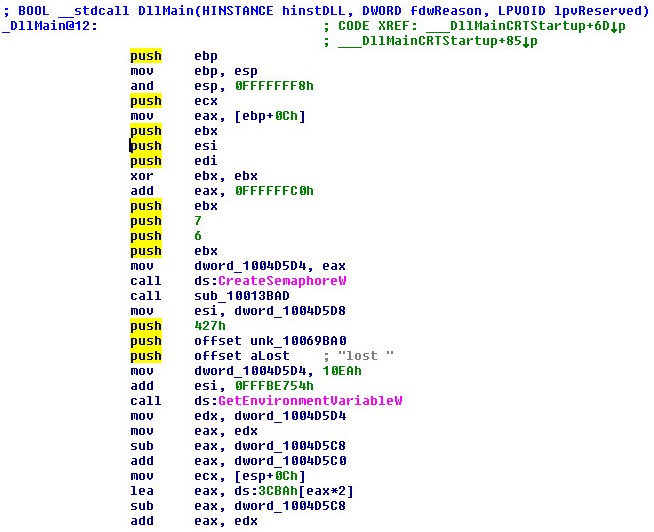
Dll Main:
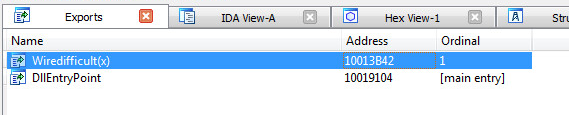
Exports:
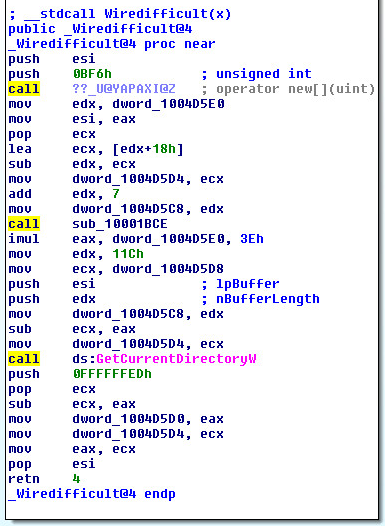
Inside Wiredifficult:
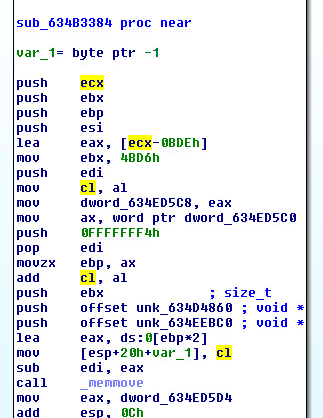
Obfuscated Buffer:
Call to decode buffer
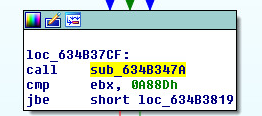
This is where the decrypted buffer will be called, Call ESI:
After stepping through the call to ESI, the shellcode will build out a small hidden call table as seen below:
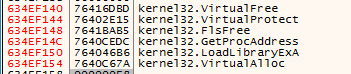
Through a variety of calls to VirtualAlloc and dumping modules, full binaries, regions, and custom partial memory regions. You will also have to jump the hurdle of bypassing INT3 calls to arrive at a full decrypted MZ Binary in memory below:
Fully Decrypted:
After the decryption, you will see a Import Address Table get assembled
(Take notice of CreateFileA, & WinExec, 3rd and 6th entry):
If you did everything correctly at this point. You should see a new native Dll binary:
Network Artifacts:
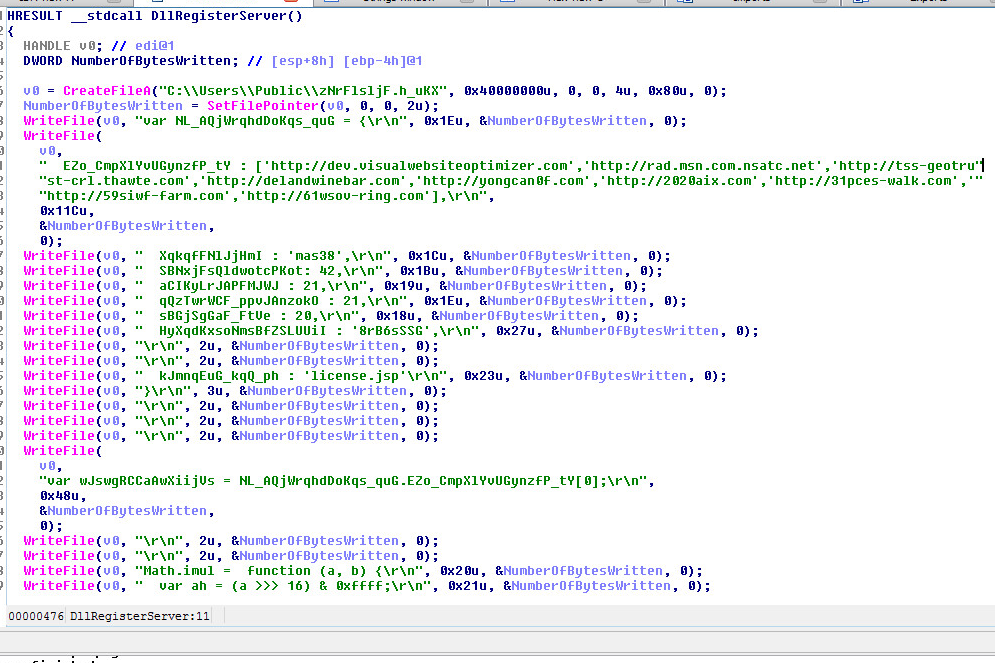
DECOY DOMAINS FOR VALAK C2:
– dev.visualwebsiteoptimizer.com
– rad.msn.com.nsatc.net
– tss-geotrust-crl.thawte.com
MALICIOUS DOMAINS FOR VALAK C2:
– 95.169.182.116 port 80 – delandwinebar.com
– 95.169.182.116 port 80 – yongcan0f.com
– 2020aix.com
– 31pces-walk.com
– 59siwf-farm.com
– 61wsov-ring.com
MALICIOUS DOMAINS FOR ICEDID:
– 165.227.64.184 port 443 – ldrhonda.casa
– 167.71.227.19 port 443 – sweeteator.best
– 167.71.227.19 port 443 – plutiasitop.top
Supported Systems:
- Windows 10
- Windows 8.1
- Windows 8.0
- Windows 7
- Windows Vista
SonicWall, (GAV) Gateway Anti-Virus, provides protection against this threat:
- GAV: Valak.AG
Appendix:
Sample SHA256 Hash: fd44086fe5fd433c14f4fc1e03f318353add50ac77dee6da3f64c4d2c5414c1c
File Location: http://detayworx.com/_vsnpNgyXp84Os8Xh.php?x=MDAwMSD7k0uWF2BKCkQGuSvAXqzhVD7pPpu-mirofSGC48QkKx26TywMByaP_nQjE_2EZXGfKy_H-gb2d-aDRgRbUwBi0XgbtTnVlugs38r3vI298UWyMzmQsvid4SyXJOUkCK4dpXj6mXuT7tTBXC3_-w~~