Chinese ransomware spotted in the wild (Apr 7, 2017)
This week, SonicWALL Threats research team has received reports of a ransomware that appears to be targeting Chinese speaking users. The ransomware note has a translation in Mandarin and has recommended Bitcoin trading platforms in China. This ransomware variant comes from a group calling themselves Lambda Anti-Society team – Nuke Script team or LAST-NST.
Infection Cycle:
This Trojan uses the following icon:
![]()
Upon execution, it makes a copy of itself in the root directory:
- %HOMEDRIVE%reloader.exe [Detected as GAV: Lambda.RSM (Trojan)]
It appeands “.lambda.l0cked” to all the encrypted files.

It also creates a log file where it writes all the names of all files that were encrypted:
- %HOMEDRIVE%If.Lst

It then creates and opens the file READ_IT.html which shows the ransom note and instructions on how to pay. The note is written in English and also has the Mandarin translation on the same page as shown in the screenshots below:

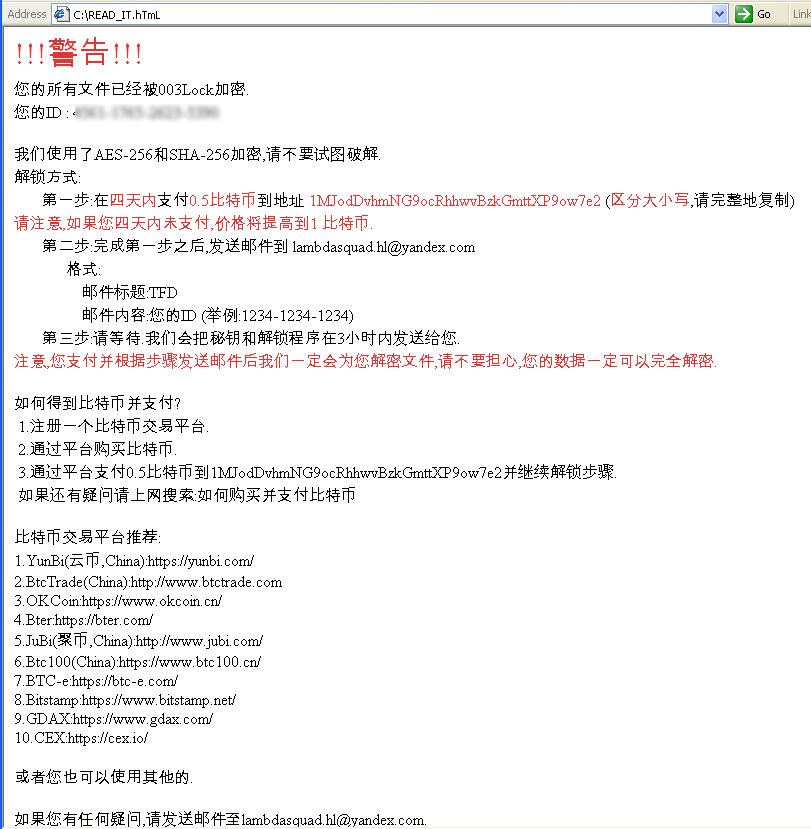
It also drops the following files:
- %HOMEDRIVE%#Cyb3rGh0st_S0c13tyF@ck3r – a config file
- %HOMEDRIVE%!A_NOTICE_FROM_LAST
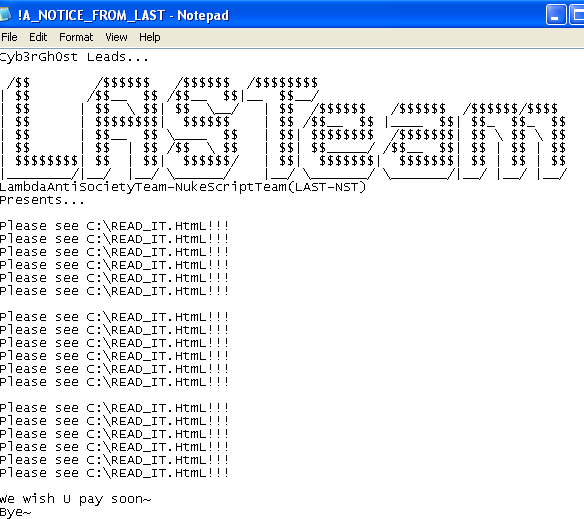
This ransomware does not encrypt any system executables therefore leaving the victim’s machine still adequately functional. During our analysis, it encrypted the files with the following file extensions:
asp, aspx, bak, bmp, c, class, conf, config, cpp, cs, dat, dbf, dmp, doc, doy, frm, gif, hta, htm, html, img, jar, jpg, mdb, mid, pdf, php, png, pot, ppt, rtf, sql, swf, tif, txt, txt, vbs, wav, wma, xls, xlt, zip
Checking the bitcoin address provided on the ransom note, it appears that this cybercriminal group has received a few Bitcoin transfers of what appears to be payment from victims based on the transactions shown below:

Because of the prevalence of these types of malware attacks, we urge our users to back up their files regularly.
SonicWALL Gateway AntiVirus provides protection against this threat with the following signature:
- GAV: Lambda.RSM (Trojan)




