BadBoy ransomware, variant of Spartacus charges $1000 for decryption
The SonicWall Capture Labs threat research team have observed reports of ransomware that encrypts files and appends a “.BadBoy” extension to their names. This variant of the malware is new but is based on Spartacus ransomware which was first seen in early 2018. Like Spartacus, it is written in .NET and uses a ransom page that is similar in appearance. However, in this variant, the code is not obfuscated.
Infection Cycle:
Upon execution, files are encrypted and the following message is displayed on the desktop:
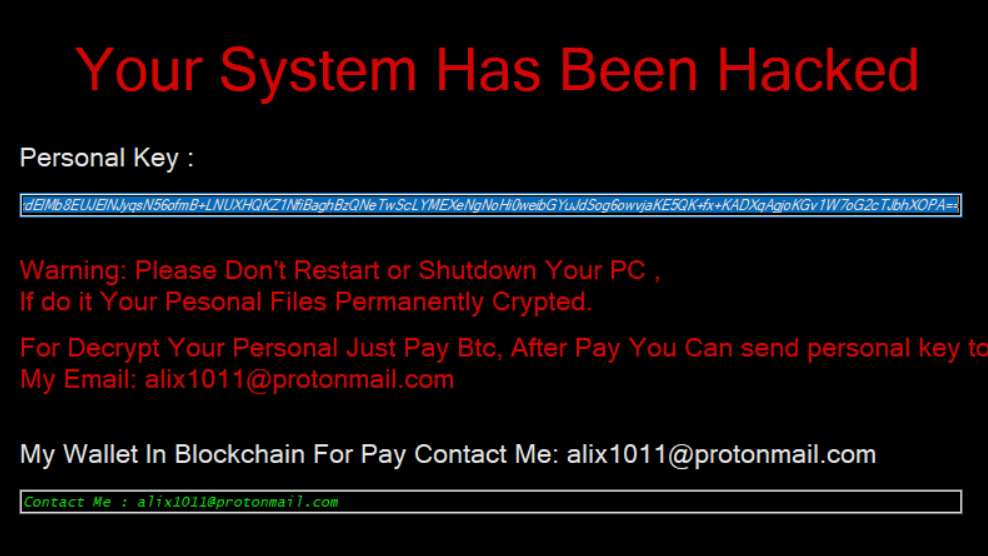
Files encrypted by the malware are given a .BadBoy extension.
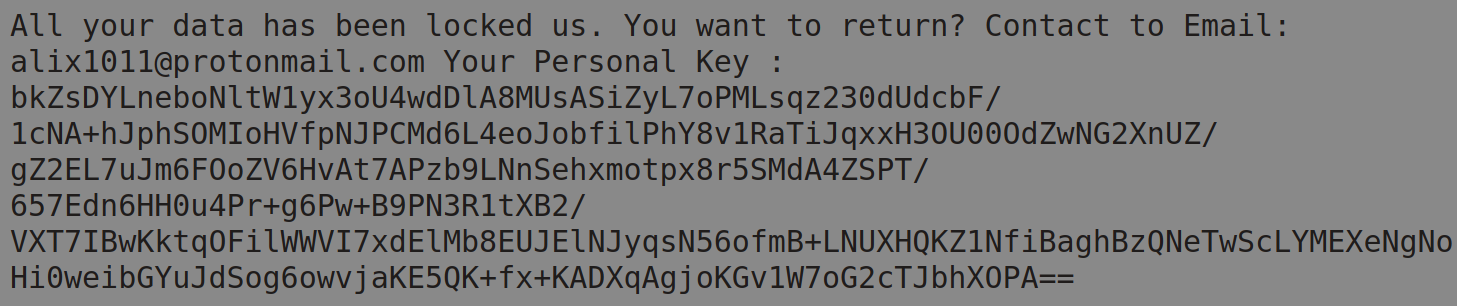
The malware drops ReadME-BadboyEncryption.txt on to the desktop. It contains the following message:
As the malware is written in .NET, it is easy to decompile and analyse. Initial inspection of the decompiled output paints a clear picture of the malware’s intentions:
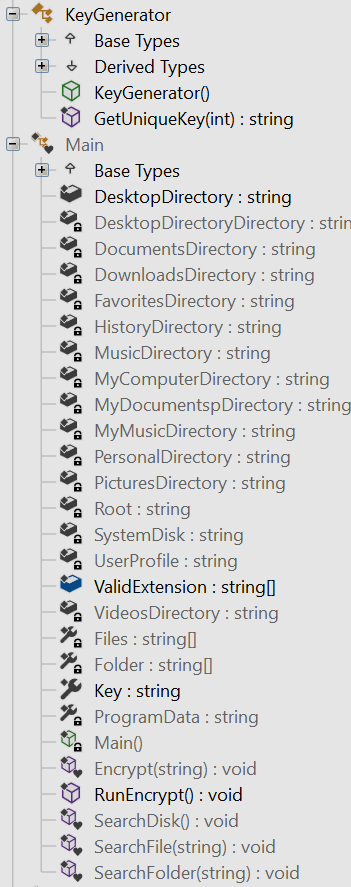
BadBoy code layout
The code layout of the BadBoy variant is simple compared to Spartacus’ layout which is obfuscated:
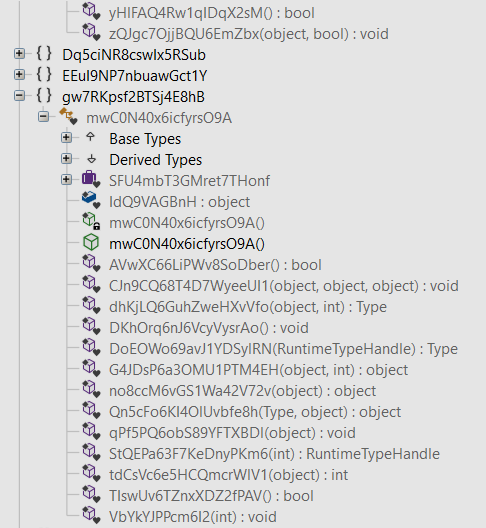
Spartacus obfuscated code layout
Further inspection shows the directories and file extensions that are targeted for encryption:
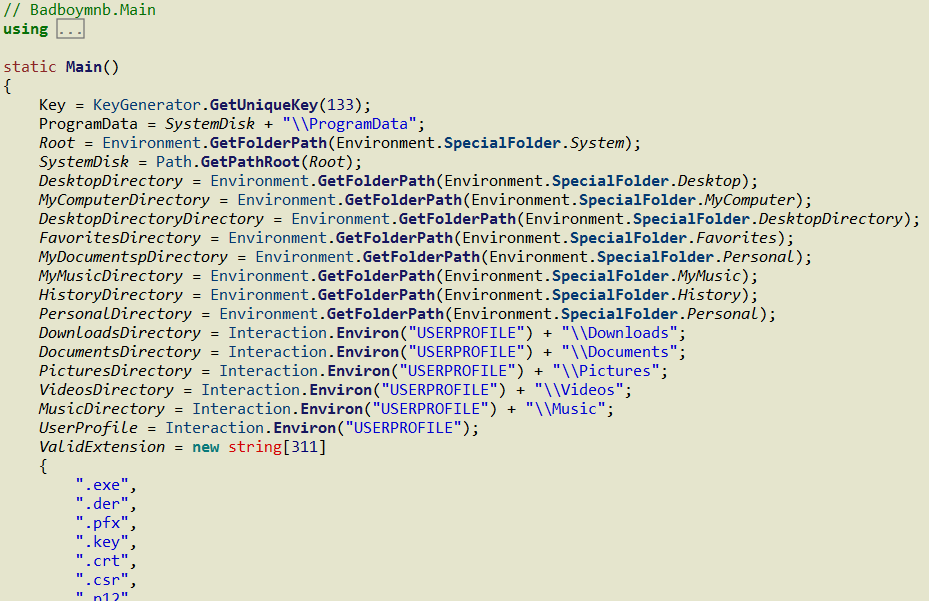
Files of the following filetypes are sought out and encrypted:
.exe, .der, .pfx, .key, .crt, .csr, .p12, .pem, .odt, .sxw, .stw, .3ds, .max, .3dm, .ods, .sxc, .stc, .dif, .slk, .wb2, .odp, .sxd, .std, .sxm, .sqlite3, .sqlitedb, .sql, .accdb, .mdb, .dbf, .odb, .mdf, .ldf, .cpp, .pas, .asm, .cmd, .bat, .vbs, .sch, .jsp, .php, .asp, .java, .jar, .class, .mp3, .wav, .swf, .fla, .wmv, .mpg, .vob, .mpeg, .asf, .avi, .mov, .mp4, .mkv, .flv, .wma, .mid, .m3u, .m4u, .svg, .psd, .tiff, .tif, .raw, .gif, .png, .bmp, .jpg, .jpeg, .iso, .backup, .zip, .rar, .tgz, .tar, .bak, .ARC, .vmdk, .vdi, .sldm, .sldx, .sti, .sxi, .dwg, .pdf, .wk1, .wks, .rtf, .csv, .txt, .msg, .pst, .ppsx, .ppsm, .pps, .pot, .pptm, .pptx, .ppt, .xltm, .xltx, .xlc, .xlm, .xlt, .xlw, .xls b, .xlsm, .xlsx, .xls, .dotm, .dot, .docm, .docx, .doc, .ndf, .pdf, .ib, .ibk, .bkp, .dll, pdb, .dat, .File, .ini, .bin, .PC, loli, .sys, .log, .xml, .vir, .prx, .ds, .mui, .amx, .aep, .csproj, .sln, .cs, .ico, .license, .vb, .resx, .vbproj, .settings, .asset, .json, .db, .md, .ios, .app, .xaml, .snk, .appxmanifest, .asax, .html, .index, .config, .cshtml, .js, .map, .ttf, .css, .aspx, .Master, .nff, .save, .vdproj, .info, .nfo, .flp, .suo, .rec, .studioonemacro, mid, .nvram, .vmsd, .vmx, .vmxf, .wav, .bbc, .cat, .daa, .cue, .nrg, .img, .mds, .ashdisc, .bwi, .b5i, .gi, .cdi, .pdi, .p01, .pxi, .ncd, .c2d, .cif, .lcd, .fcd, .vcd, .dmg, .bif, .uif, .isz, .wim, .ima, .package, .langpack, .cfg, .data, .PNF, .inf, .xsd, .cab, .dmp, .theme, .jnt, .msc, .cd, .user, .manifest, .application, .deploy, .c, .h, .filters, .vcxproj, .sqlproj, .cache, .dacpac, .pdb, .pub, .mpp, .ssk, .wtv, .SFX, .chm, .lst, .ion, .Targets, .lng, .ulf, .xsl, .tmp, .lock, .inc.php, .lib, .pm, .frm, .hlp, .it, .inc, .b4a, .bas, .scss, .nsi, .cgi, .var, .ax, .pck, .bik, .qtr, .vfs0, .vfx, .webm, .webcam, .rpkg, .xpi, .rc, .spr, .res, .tga, .video, .mdl, .lmp, .sc, .lua, .md5, .vst, .awk, .nki, .reg, .7z, .ace, .arj, .bz2, .cab, .gz, .jar, .lz, .lzh, .tar, .uue, .xz, .db, .dbs, .dll, .z, .ogg, .apk, .md, .dewar, .rst, .plist, .tmSnippetz
The key used to encrypt files can be found in the decompiled output. However, this is not sufficient for decryption as the algorithm (RSA) is asymmetric and the private key (held only by the operators) is required to decrypt files:
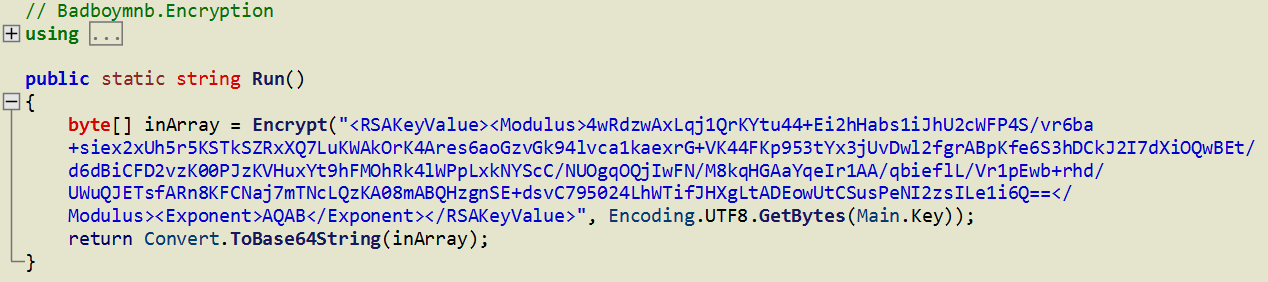
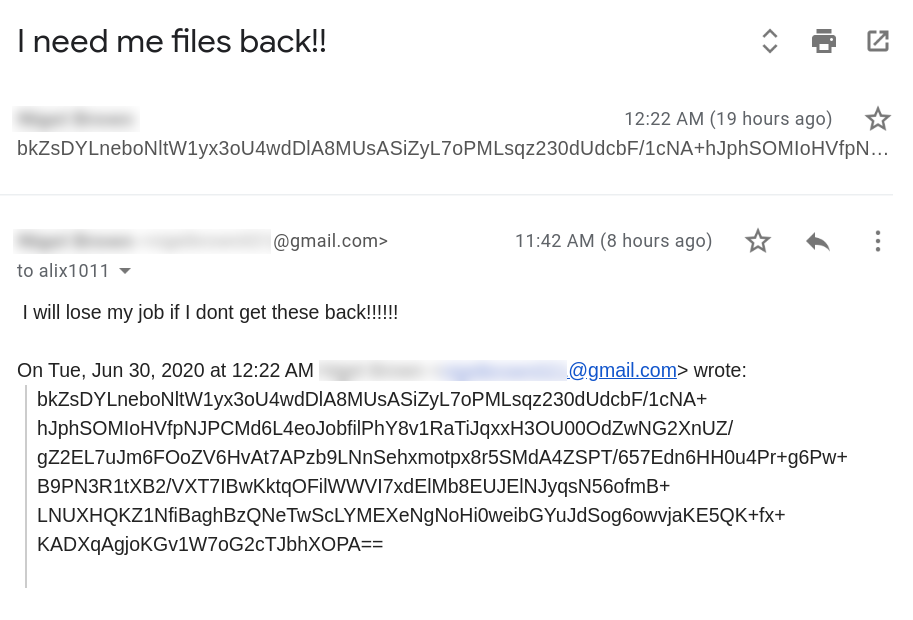
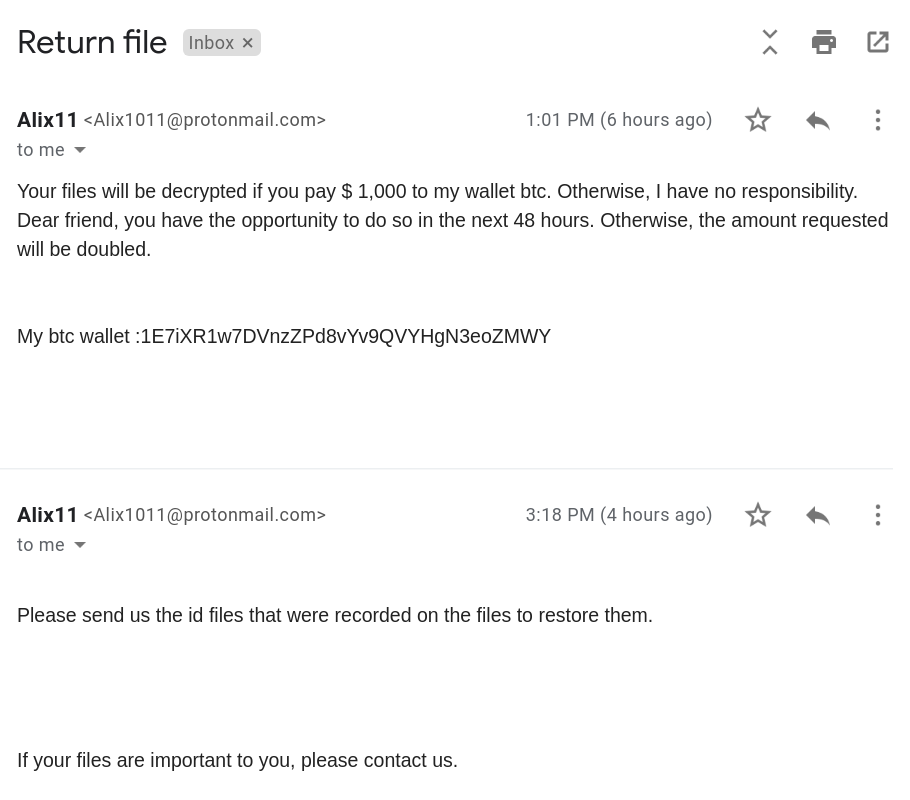
We contacted the operators via email as instructed in the ransom message and had the following conversation:
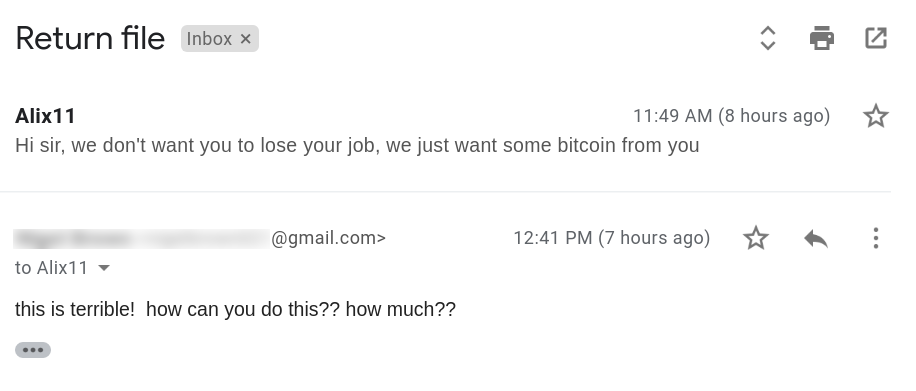 

$1000 in bitcoin to 1E7iXR1w7DVnzZPd8vYv9QVYHgN3eo
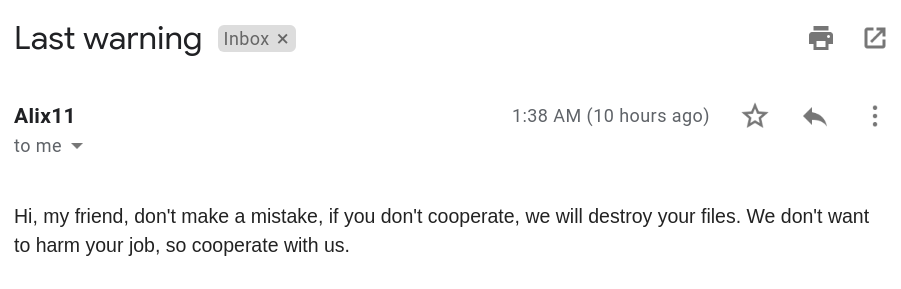
The next day we even received a final warning:
SonicWall Capture Labs provides protection against this threat via the following signatures:
- GAV: BadBoy.RSM (Trojan)
- GAV: Blackheart.RSM (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.






