Excel 4.0 macro being used to deliver Malware
Sonicwall Capture Labs Threats Research team has been tracking a campaign from the last two months which involves Microsoft Office Excel for malware distribution. Microsoft Excel provides a feature to its user which allows one to hide worksheets. Worksheet state is “visible” by default which can be changed to “hidden” or “very hidden”. The malicious MS-Excel files are found to be leveraging this feature to hide worksheet carrying malicious excel 4.0 macro. Another interesting artifact in these malicious excel files is the use of excel 4.0 macro though Microsoft has been encouraging its users to use the latest version of Microsoft Visual Basic for Application (VBA).
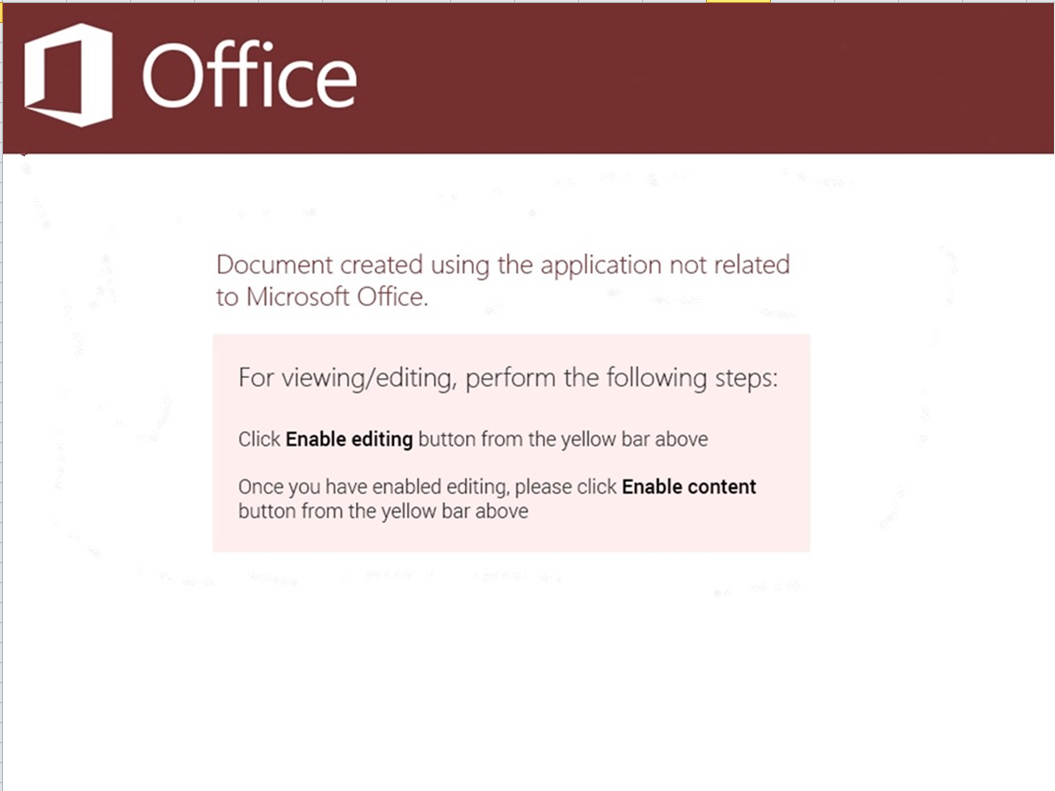
Upon opening the malicious excel file, user is displayed an image with a message educating the user on how to enable editing in order to view the document. As can be seen in the following image, the file appears to be just having one sheet.
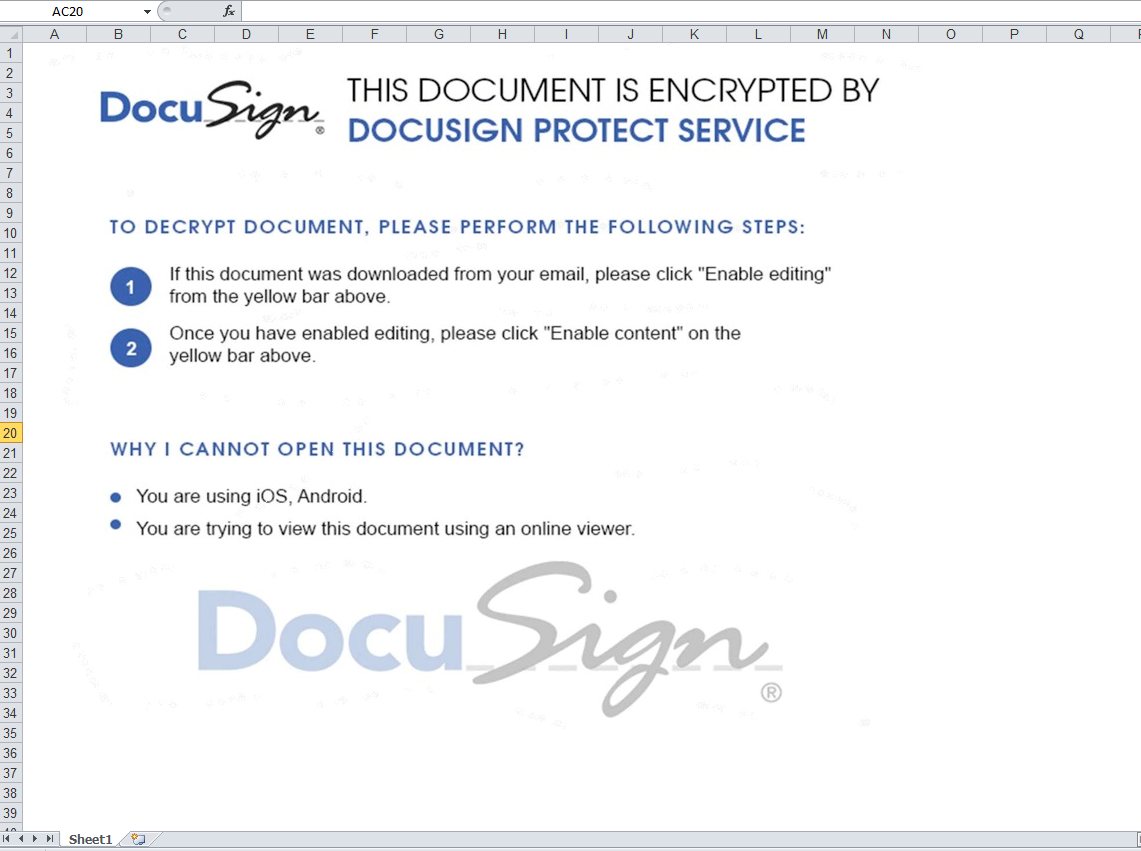
We have observed a few variants surrounding this campaign. In some of its appearances, the image varies as shown below:
Screen captured images of third party products or services are intended only to demonstrate the real-world application of the reported malware
Initial variants of this malware were found to be using data connection which could further be used to download payload. Later variants started using excel 4.0 macro for downloading payload. As of now, the samples analyzed either have domain names that are not registered or they redirect the victim to google.com or they download a DLL file from GitHub which further launches Microsoft Windows calculator application “calc.exe”.
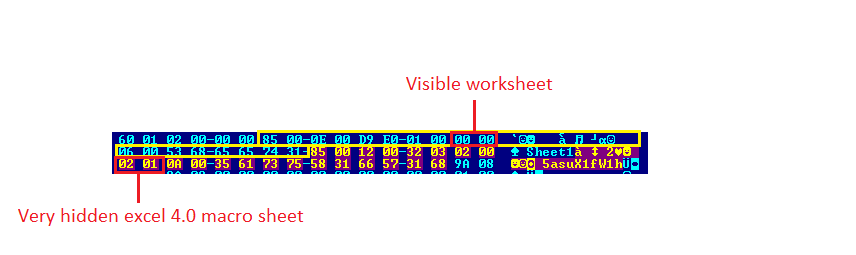
As highlighted in the following image, the malicious excel contains two sheets indicated by the two BOUNDSHEET records (85h). One sheet’s state is set to hidden thus the sheet is not visible. This sheet also contains excel 4.0 macro.
Sheet Record:
| 85 00 | Start of sheet record | 2 Bytes |
| 0E 00 | Size of record | 2 Bytes |
| D5 58 01 00 | Address of BOF | 4 Bytes |
| 00 | 00h = visible01h = hidden
02h = very hidden |
1 Byte |
| 00 | 00h = worksheet or dialog sheet
01h = Excel 4.0 macro sheet 02h = chart 06h = Visual Basic module |
1 Byte |
| 06 | Size of sheet name | 1 Byte |
| 53 68 65 65 74 31 | Sheet name |
The sheet can be made visible by altering the state byte to “0” which happens to be the 9th byte of the BOUNDSHEET record. Following VBA macro would also do the trick:
For Each ws in Sheets
ws.Visible = xlSheetVisible
Next ws
The early variants which surfaced had hidden sheet but with no macro code. The other variants differ how payload is downloaded. Payload execution through excel 4.0 macro has been the same.
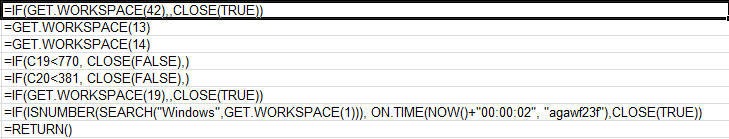
The macro begins by checking the workspace width (13), height (14), presence of mouse (19), whether the system can play sound and windows environment.
GET.WORKSPACE(42): Should be capability of playing sound.
GET.WORKSPACE(13): Usable workspace width should be less than 770.
GET.WORKSPACE(14): Usable workspace height should be less than 381.
GET.WORKSPACE(19): Mouse should be present and avoid execution in sandbox.
GET.WORKSPACE(1): Environment should be windows.
SonicWall Capture Labs Threat Research team provides protection against this threat with the following signature:
- GAV:Downloader.XL_8 ( Trojan )
Sonicwall RTDMI engine detects these Excel files.