CoronaVirus Trojan overwriting the MBR
SonicWall Capture Labs Threat Research team recently found a new malware taking advantage of the CoViD19 pandemic which makes disks unusable by overwriting the MBR.
Infection cycle
Upon execution, a number of helper files are dropped inside a temporary folder:
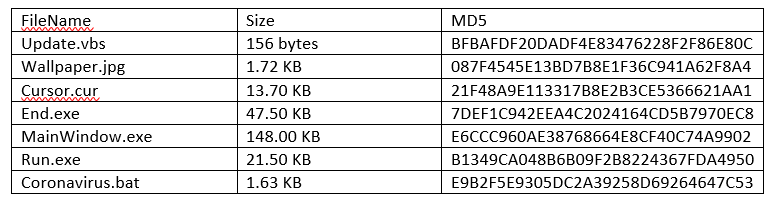
One of the helper files named “coronavirus.bat”, which identifies itself as “coronovirus Installer” performs most of the setup work. It creates a folder named “COVID-19” where all the previously dropped helper files are moved. In order to go unnoticed, “COVID-19” folder is hidden. It further goes on to disable Windows Task Manager, User Access Control (UAC), disables options to add/modify wallpaper after changing the user’s current wallpaper. It also adds entries in registry for persistence.

Coronavirus.bat
The victim is notified of installation and reboot before the system is finally restarted.
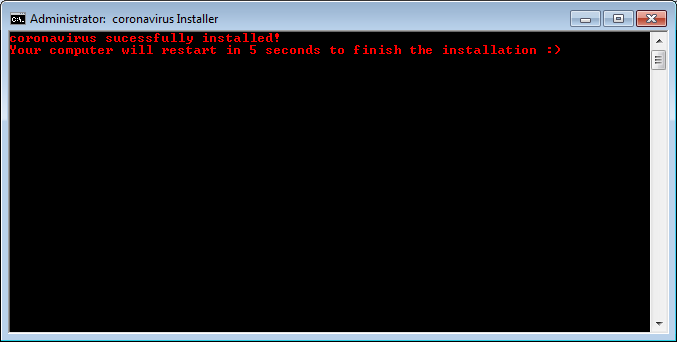
run.exe creates a batch file named run.bat to ensure the registry modifications done by “coronavirus.bat” are kept intact besides facilitating execution of “mainWindow.exe”.
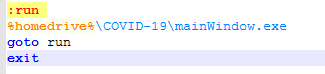
MainWindow.exe upon execution displays a window with two buttons showing structure of CoViD19 virus.
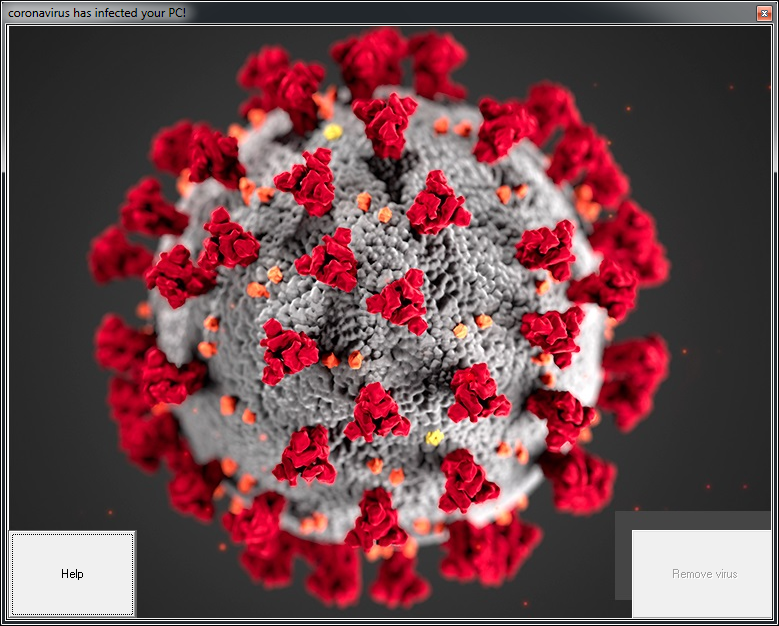
One of the button named “Remove virus” is non-functional. Upon clicking on the “Help” button it displays below image.
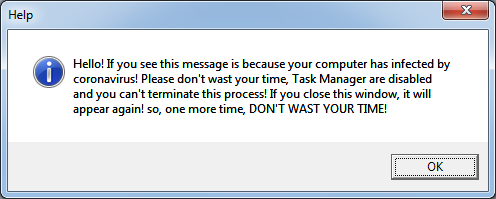
The sole functionality of the Update.VBS script file is to display below message window.
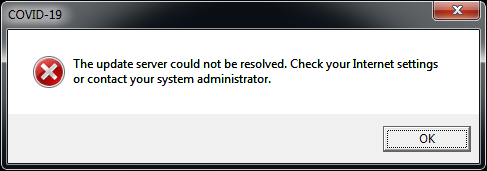
The other binary which starts execution after reboot is responsible for overwriting the MBR.
The original MBR is first backed up in the first sector before it is overwritten with new one.

MBR overwritten with the new code

Also on the sector 2 of the disk it copies below message

MBR and new code

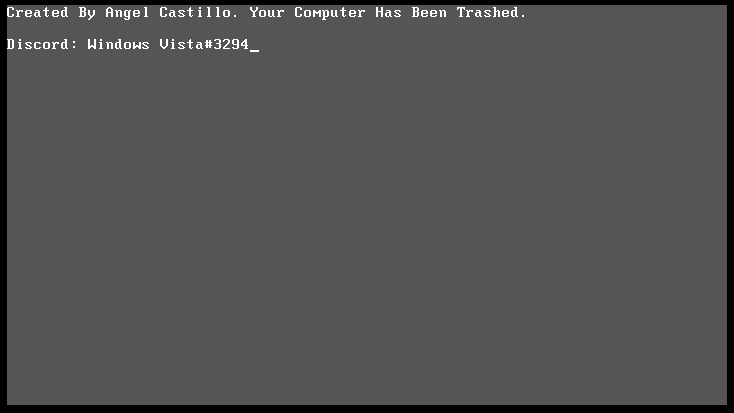
Henceforth, the victim is displayed below message by the bootstrap code.
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: KillMBR.Corn_A (Trojan)
Indicators Of Compromise (IOC):
- DFBCCE38214FDDE0B8C80771CFDEC499FC086735C8E7E25293E7292FC7993B4C
This threat is also detected by SonicWALL Capture ATP.






