A wave of C++ based IRCBot discovered in the wild (June 21, 2013)
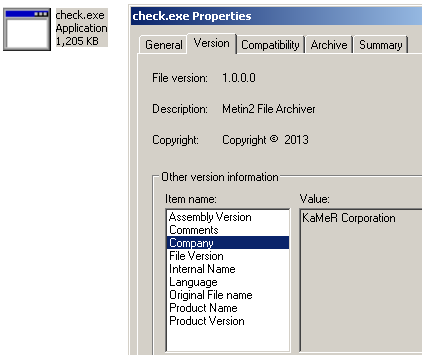
The Dell SonicWALL Threats Research team has observed a recent wave of a C++ based IRC bot which is very similar to a bot covered in a previous alert . This bot appears to be hosted on compromised legitimate websites that aim to infect unsuspecting web surfers visiting these infected websites. The bot installer may arrive in the computer with file names such as, quick.exe, wmplayer.exe or check.exe with the following file properties information:
Infection Cycle:
Upon execution the bot creates a copy of itself into the following folders:
- %windir%-(random digits)unsecapp.exe [Detected as GAV: Injector.AHXY (Trojan)]
- %temp%file.exe [Detected as GAV: Injector.AHXY (Trojan)]
In order to start after reboot the bot adds the following keys to the registry:
- HKCUsoftwaremicrosoftwindowscurrentversionrun [adobeupdate] “%temp%file.exe”
- HKCUsoftwaremicrosoftwindowscurrentversionrunonce [*-(random digits)] “%windir%-(random digits)unsecapp.exe”
- HKLMsoftwaremicrosoftwindowscurrentversionrunonce [*-(random digits)] “%windir%-(random digits)unsecapp.exe”
It also executes the following command to run itself with the highest privileges whenever a user logs on:
- %system%schtasks.exe [SCHTASKS /CREATE /SC ONLOGON /TN A-(*random folder name*) /TR %windir%-(random digits)unsecapp.exe /RL HIGHEST]
The bot modifies the values of the following registry keys to hide its presence within the system:
- HKCUSoftwareMicrosoftWindowsCurrentVersionPoliciesExplorerNoFolderOptions dword:00000001
- HKCUSoftwareMicrosoftWindowsCurrentVersionPoliciesExplorerAdvancedHidden dword:00000002
It also disables Windows Update by modifying the following registry key:
- HKCUSoftwareMicrosoftWindowsCurrentVersionPoliciesExplorerNoWindowsUpdate dword:00000001
It connects to an IRC server:
![]()
And then joins an IRC channel named #marketevo:

Upon successful connection to an IRC server, a bot will typically wait for commands from its operator. This allows an attacker to perform a number of actions such as the following commands which are present in the binary’s strings:
- decrypt
- download
- update
- arguments
- ftp.upload
- filesearch
- silent
- connect
- notice
- invite
- flood.channel
- kill.user
Within minutes of joining the #marketevo channel, we noticed an influx of users joining from presumably infected machines spanning from different parts of the world.

During our analysis, we also observed the bot sending private messages to the channel:

SonicWALL Gateway AntiVirus provides protection against this threat via the following signature:
- GAV: Injector.AHXY (Trojan)



