Fake Antivirus apps on Google Play flag themselves as risky
Google Play hosts a plethora of different types of apps. One such popular type of app is Antivirus (AV) for the device. Searching for ‘antivirus’ on Google Play gives upwards of 200 results:
But can all these apps be trusted with securing your device ?
A few months back there was an interesting find about fake Antivirus apps for Android. SonicWall Threats Research Team identified fresh apps that exist on Google Play (during the time of our analysis) that exhibit similar behavior.
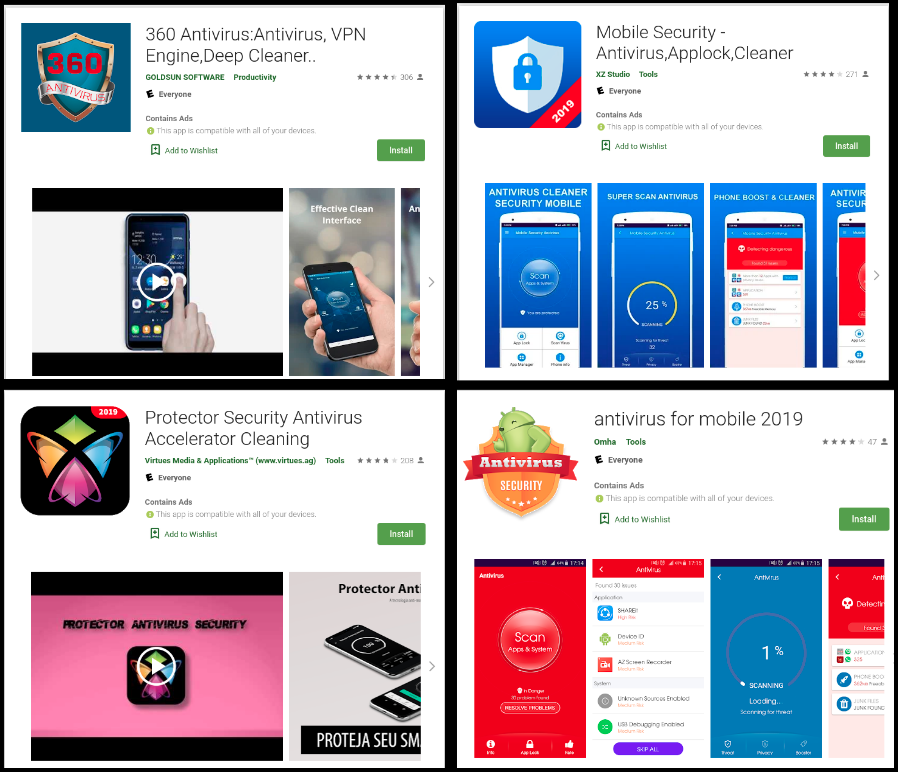
During our analysis we identified the following fake AV apps that are present on Google Play (at the time of writing this blog):
- 360 Antivirus:Antivirus, VPN Engine,Deep Cleaner
- Mobile Security – Antivirus,Applock,Cleaner
- Protector Security Antivirus Accelerator Cleaning
- antivirus for mobile 2019
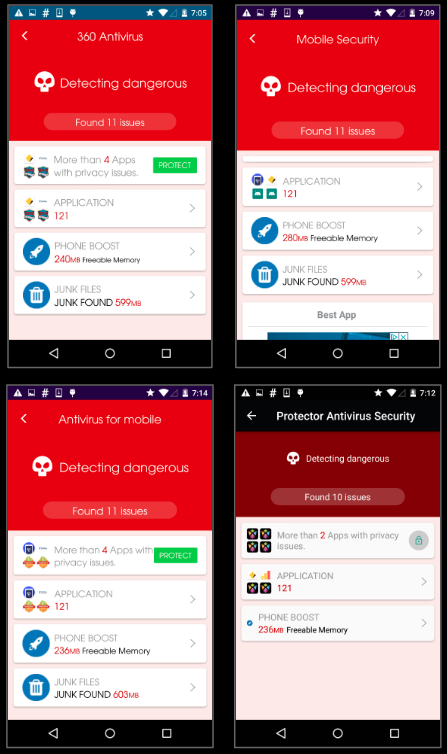
Fake Scans
As each of the above app claims to be an Antivirus app we ran a scan of our device via the apps above. Upon execution each one of the apps showed a scan result page that seems to have a common design pattern:
The apps find few similar security issues on the device, upon inspecting the code the reason for this similarity becomes clear.
These AV apps consults a few .json files from the assets folder to determine the risk levels of applications on the device. The following json files are used:
- Permissions.json – This file saves a list of permissions and gives them a rating. Based on what permissions are used by an application a risk score is given:
- BlackListActivities.json – Contains a list of package names, if an application contains a subset of these package names in their activities it is deemed risky:
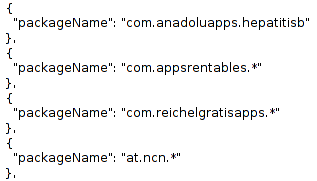
- BlackListPackages.json – If packages present in this file are present on the device, they are deemed risky:
- WhiteList.json – Contains a list of package names, if an application contains a subset of these package names it is automatically considered safe:
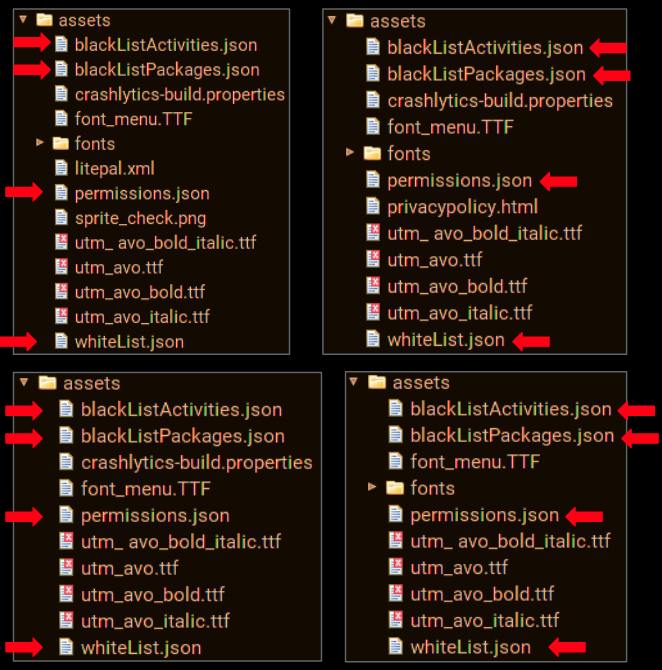
All the four apps mentioned in this blog contain the same json files listed above:
Suspicious Network Activity
During the analysis of these apps, few of them started showing fullscreen ads during their execution:
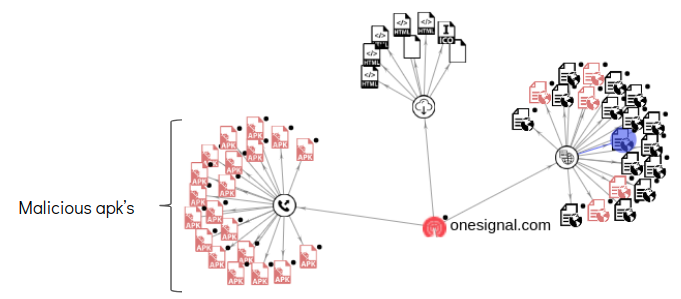
One of the apps communicated with a domain onesignal.com which has suspicious associations with apps that have detection on VirusTotal. Below VT graph further highlights this:
Flawed Approach
These apps follow a very simplistic approach towards security as most of the parameters considered to determine a risk score are not reliable:
- Package names can be easily changed. As a result, if a malicious app has a package name present in the whitelist.json file it will not be considered malicious
- Permissions alone cannot be used to decide if an application is malicious. Most of the permissions present in the permissions.json file are used by clean applications as well
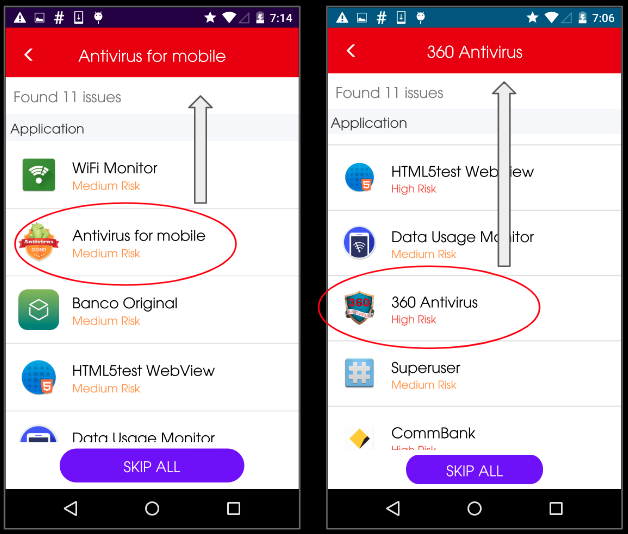
Probably the biggest irony of these antivirus apps is that they manage to flag themselves as ‘Medium Risk’/’High Risk’ apps as they do not have their own package name in the whitelist file:
Common Elements
Along with detection related assets, most of the .json files discussed in this blog are common among the fake AV apps that we saw. This makes one question if the app creators are reusing common code.
The Real Danger
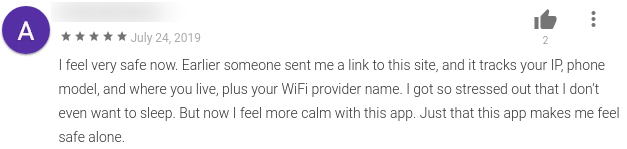
Even though the apps discussed in this blog are not malicious in nature they do something dangerous, they give the users a false sense of security. Users feel secure once they install these anti-virus apps but these apps don’t actively protect the users, they simply reply on a static .json file to identify potentially dangerous apps. This sentiment can be seen in a review for one of these apps:
Rather than downloading such dubious apps we urge readers to take some precautions when downloading security related apps:
- Install security related apps from reputed companies that have a presence in the field of security
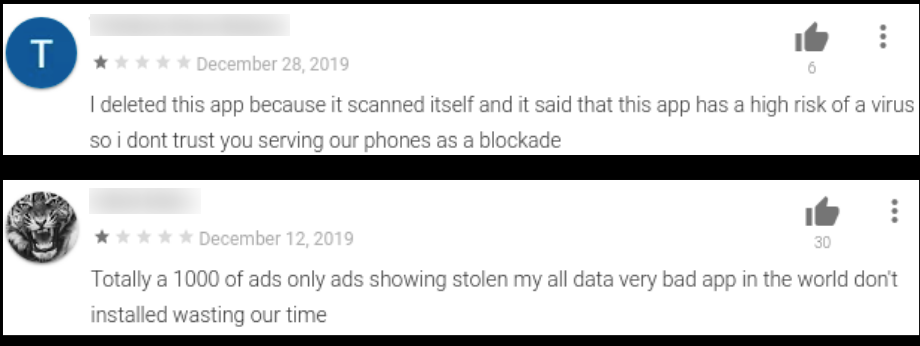
- Reading reviews of the app helps in identifying potentially harmful/fake apps. Few reviews of the apps listed above don’t inspire confidence:
But sadly based on the stats on Google Play, a large number of users have already downloaded these apps:
SonicWall Capture Labs provides protection against these threats with the following signature:
- GAV: AndroidOS.FakeAV.JS
Indicators of Compromise (IOC’s):
- fd6ae5a3d73d9f13c2a88934d4af9a90
- 73107da87705c19c7ca8873f04323c6b
- 816f496a67c9d00837ce5d7140abde4f
- 8476aa9e1887fadd03a1df0a608d5877
- 4b1728bb946863e1d2e916f5c6b90ab9
- 714d036cd152d84caeb975e7e49a2bc9
- 76dc8ad67c36650fd6da158ebf226567
- 69a9610d8a9bd569f6795090a2b9fbff
- ca1239ddc7a672919f606d770c07ab27
- 9f91b53fad1572cef861eb2fe8ce5dcf
- a04a913cd59833da915c2f44a05e5866
- 1378680364d963b3af9bae44d61a838c