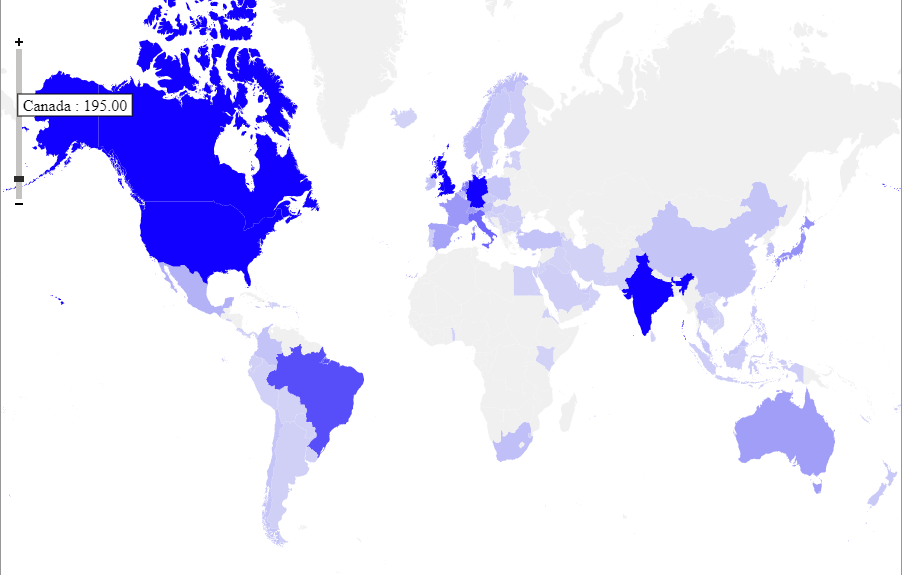
This week, SonicWall Capture Labs Threat Research team observed a huge spike in the hits targeting the Microsoft SharePoint server flaw. These HTTP requests are made to command and control the hosts that are infected with the exploits of CVE-2019-0604. It is seen to hit almost 100 countries, but most observed only in the United States.
CVE-2019-0604 | Microsoft SharePoint Remote Code Execution Vulnerability:
A remote code execution vulnerability exists in Microsoft SharePoint when the software fails to check the source markup of an application package. An attacker can exploit these vulnerabilities by sending malicious crafted requests to a vulnerable SharePoint server or enticing a SharePoint user to upload a specially crafted SharePoint application package to a vulnerable server. An attacker who successfully exploited the vulnerability could run arbitrary code in the context of the SharePoint application pool and the SharePoint server farm account.
Exploit:
Earlier this month, Canadian Center for Cyber Security and Saudi National Cyber Security Center have reported evidences of active exploitation of Microsoft SharePoint Remote Code Execution Vulnerability ( CVE-2019-0604). The Threat actors exploited this vulnerability in order to deploy the China Chopper web shell. After establishing the initial foothold, threat actors utilized the web shell to run PowerShell scripts to download other malicious files including backdoor. The threat actors then installed HTTP backdoor to handle any requests to “hxxp://localhost:80/TEMPORARY_LISTEN_ADDRESSES/WSMAN”, or other folders such as WSMAN3 and SMSSERVICE. Through HTTP requests, malware receives commands encrypted by AES. The malware on the infected hosts has the ability to execute commands, download and upload files. The result is encoded and sent back to C&C server.
The majority of requests come from the IP address ‘188.166.64.99‘ trying to command & control the SharePoint servers that have been exploited already. The scan is so massive that around 30,000 SonicWall firewalls have observed these malicious HTTP requests and blocked them successfully.
We have observed the following malicious HTTP requests :
- hxxp://188.166.64.99/TEMPORARY_LISTEN_ADDRESSES/WSMAN
- hxxp://188.166.64.99/TEMPORARY_LISTEN_ADDRESSES/WSMAN3
- hxxp://188.166.64.99/TEMPORARY_LISTEN_ADDRESSES/SMSSERVICE
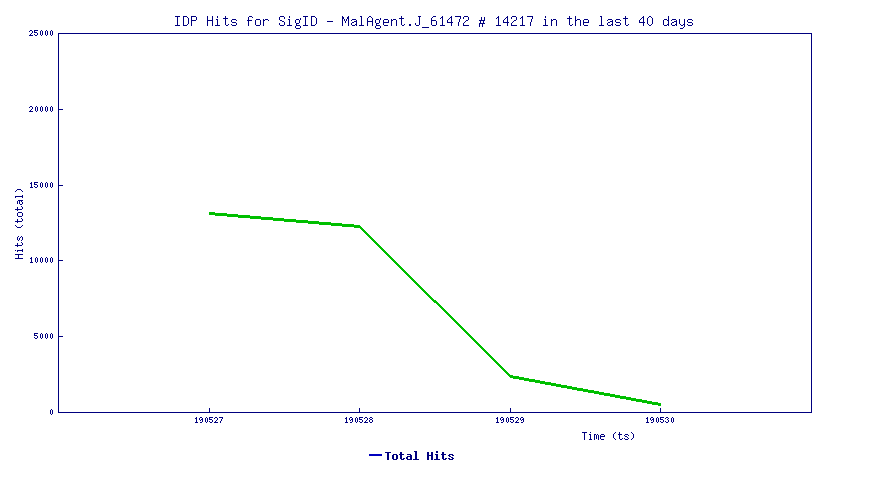
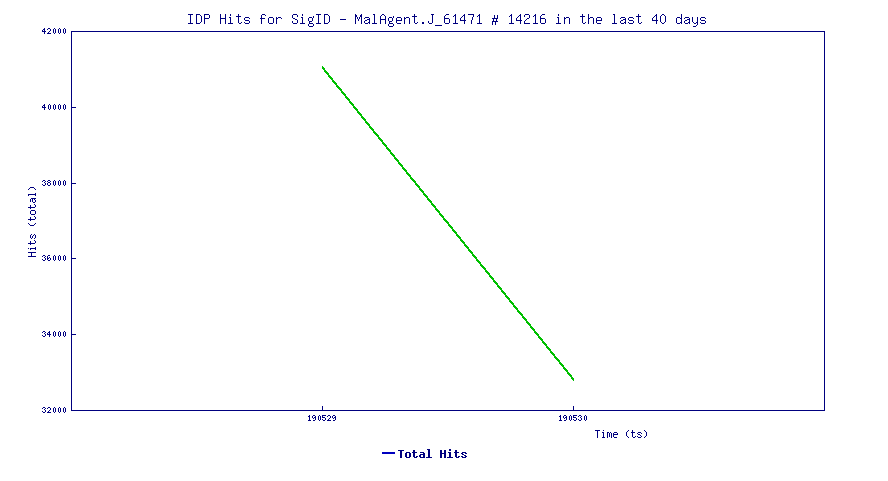
Trend Chart
The trend line below shows how this vulnerability in recent days has been actively exploited.
Heat Map:
Heat map is based on the no of unique firewalls geographically hit by this attack
The affected software versions are
-
Microsoft SharePoint Foundation 2010 Service Pack 2
-
Microsoft SharePoint Foundation 2013 Service Pack 1
-
Microsoft SharePoint Server 2010 Service Pack 2
-
Microsoft SharePoint Server 2013 Service Pack 1
-
Microsoft SharePoint Enterprise Server 2016
-
Microsoft SharePoint Server 2019
SonicWall Capture Labs Threat Research team provides protection against this exploit with the following signatures:
IPS 14201 Microsoft SharePoint Remote Code Execution 4
IPS 14216 WSMAN Inbound Access
IPS 14217 SMSSERVICE Inbound Access
IPS 14218 Microsoft SharePoint Remote Code Execution 5
IPS 14219 Microsoft SharePoint Remote Code Execution 6
IPS 14231 Microsoft SharePoint ActionRedirect.aspx Access
IPS 14232 Microsoft SharePoint downloadexternaldata.aspx Access
IPS 14233 Microsoft SharePoint profileredirect.aspx Access
WAF 1711 Microsoft Sharepoint Picker.aspx Remote Code Vulnerability
The SonicWall Capture Labs Threat Research Team gathers, analyzes and vets cross-vector threat information from the SonicWall Capture Threat network, consisting of global devices and resources, including more than 1 million security sensors in nearly 200 countries and territories. The research team identifies, analyzes, and mitigates critical vulnerabilities and malware daily through in-depth research, which drives protection for all SonicWall customers. In addition to safeguarding networks globally, the research team supports the larger threat intelligence community by releasing weekly deep technical analyses of the most critical threats to small businesses, providing critical knowledge that defenders need to protect their networks.