VirLocker Generation 8
Overview:
SonicWall Capture Labs Threat Research Team, recently found, “VirLocker Generation 8” also known as “VirLock”, and “VirRansom”. This variation, has been updated with many new techniques and anti-debugging routines that make it even harder for the “Security Researcher” to see the actual core code behind many layers of xor decryption routines, metamorphic and polymorphic code.
Ransomware variants such as this one and others are making security vendors, “stop and think”, about how next to generate different kinds of techniques to stop, detect and track this type of malware. Many are offering solutions such as artificial intelligence but no matter how much time we invest into new techniques and tools. The attackers are always ahead, creating new ways to slow down the anti-virus detection and removal process.
The protection methods added to Virlocker are making any clean-up attempt challenging. Just like past infections of Virlocker, the disinfection process for this virus involves locating the keys inside the malware then unwrapping the core ransomware like an onion, layer by layer until you reach the file that has been infected. Once the file is located you can strip the original file out.
Payment:

How to pay a fine:
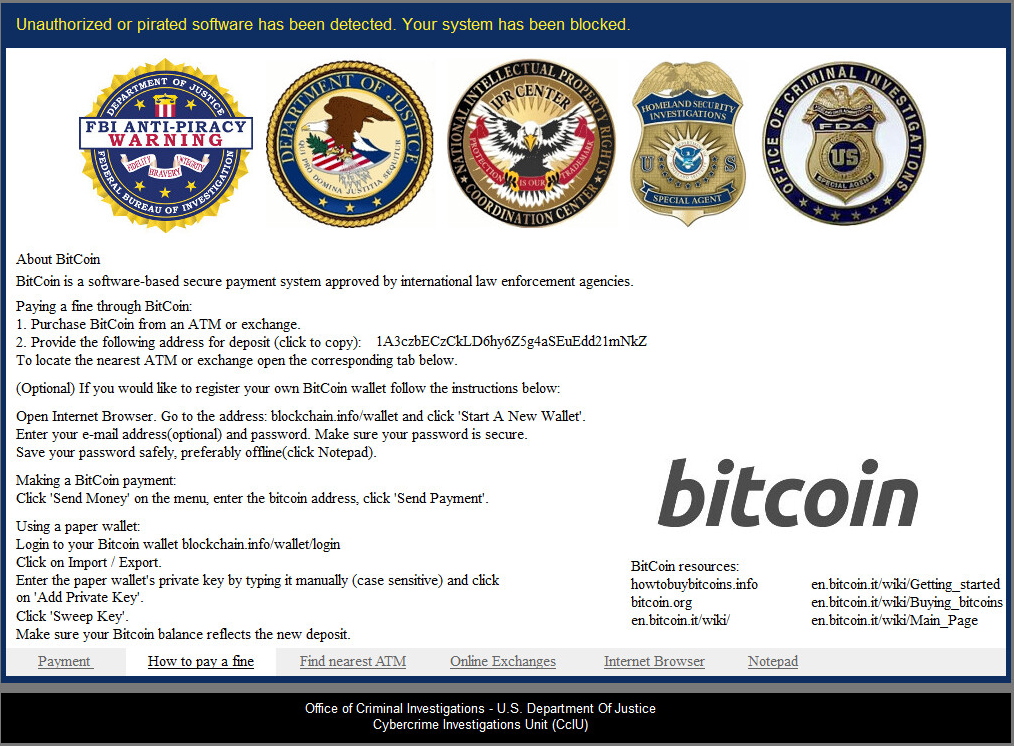
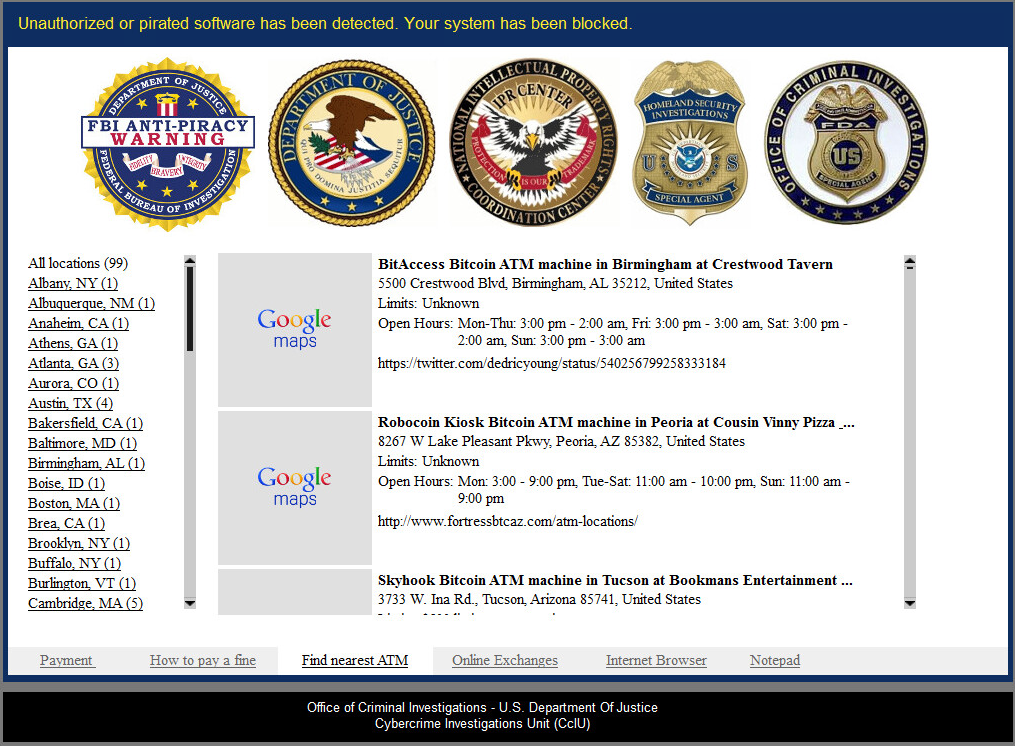
Find nearest ATM:
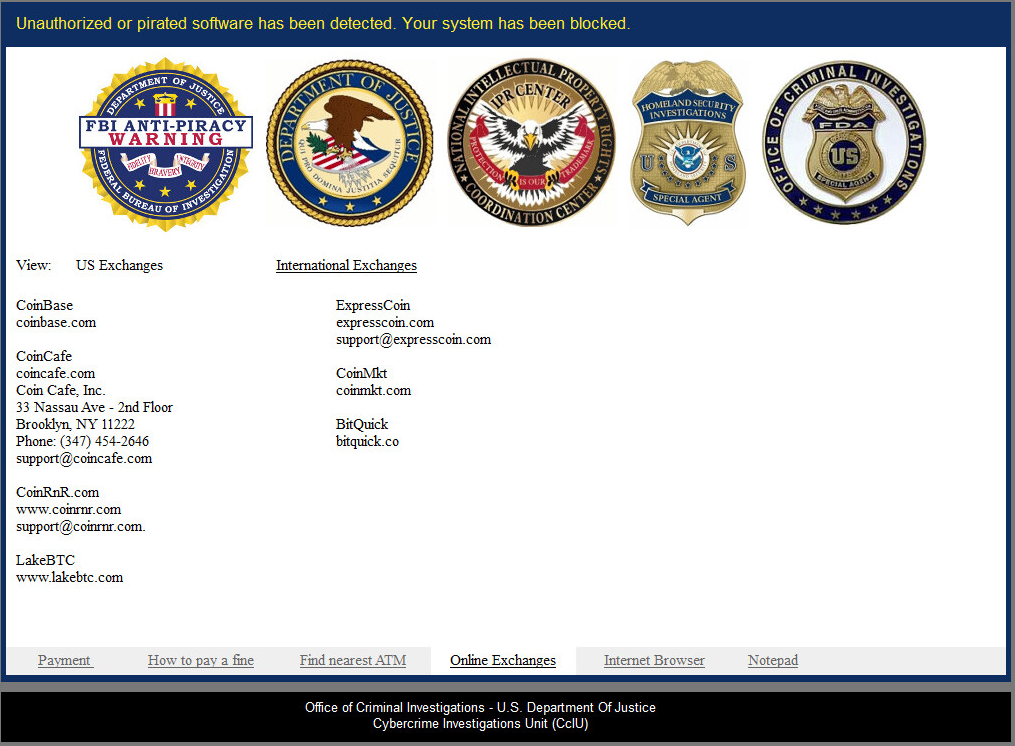
Online Exchanges:
Internet Browser:
Notepad:
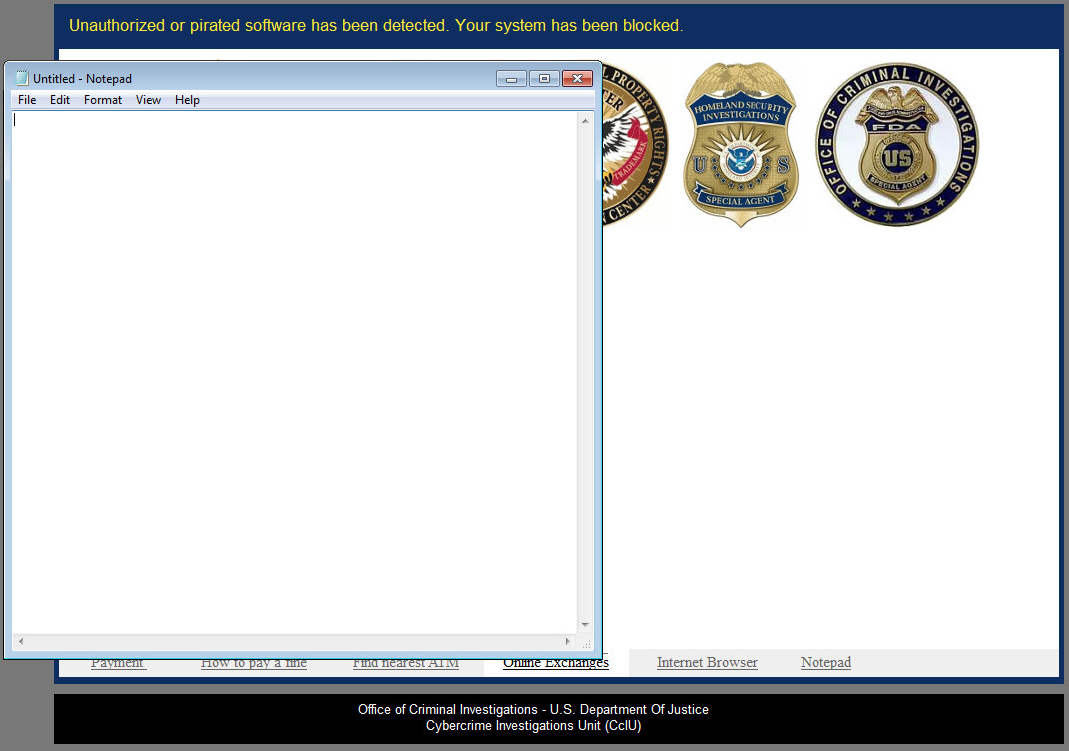
Control-Alt-Delete No Longer Works:
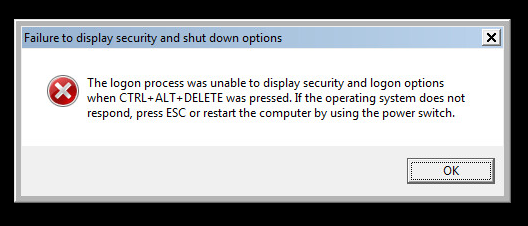
Sample Static Information:
Hash Information:
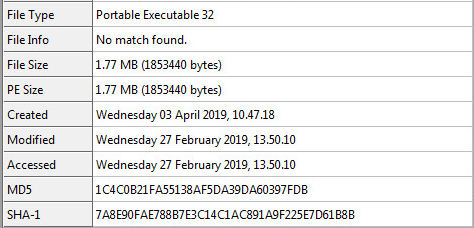
Entropy of Sample:
Folder & File Locations:
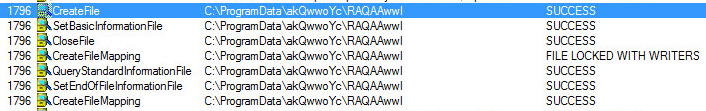
C:\Users\NAME\gKsQkYEI\SuEcwMMM:
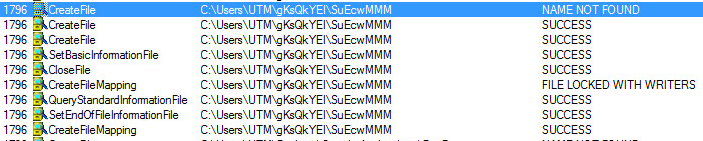
C:\ProgramData\akQwwoYc\RAQAAwwl:
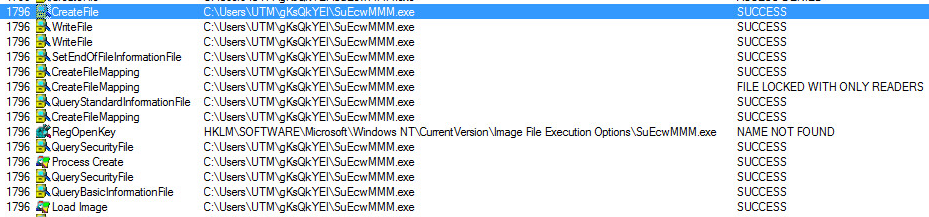
C:\Users\NAME\gKsQkYEI\SuEcwMMM.exe:
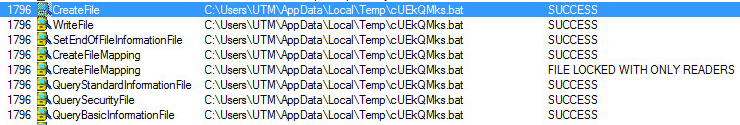
C:\Users\NAME\AppData\Local\Temp\cUEkQMks.bat:
Shim Database:
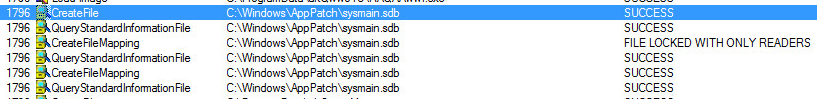
Unpacking The Sample:
Unpacking this sample is relatively harder than all of the other Virlocker generations. This is due to the added multiple layers of encryption used in the initial cryptor stub. The cryptor stub in this sample is very small. This gives the sample a higher entropy rating that can be seen above. The stub will start out with a smaller initial decryption routine which will lead into an intense anti-debugging loop that will trip up the “Security Researcher” for a few hours.
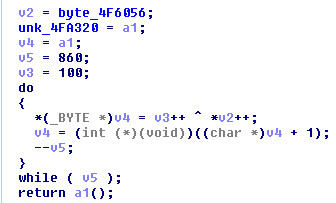
After the initial decryption, you will see the following anti-debugging loop.
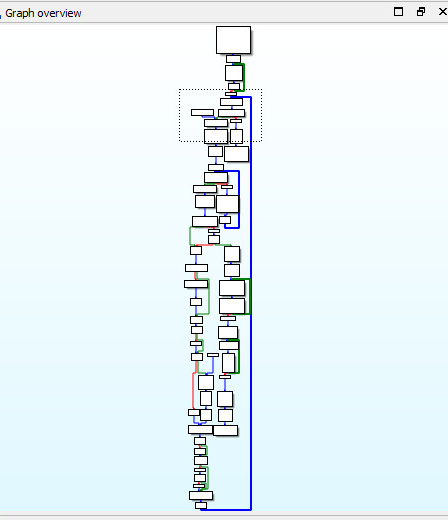
See the big “BLUE” line? This anti-debugging loop will only execute one line of the core malware code each iteration.
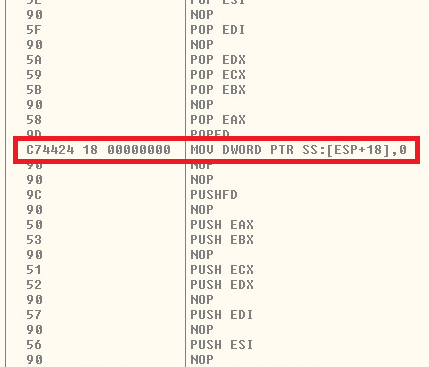
This one line of code will change and execute over a million times creating the next set of decryption stubs and metamorphic code to follow. Once you fight your way through the decryption and metamorphic stubs. You have the sample unpacked. If you have trouble, check our last Sonic Alert: “JPMORGAN CHASE NYSE: JPM, PAYMENTECH, BITCOIN RANSOMWARE” which covered an earlier version of Virlocker.
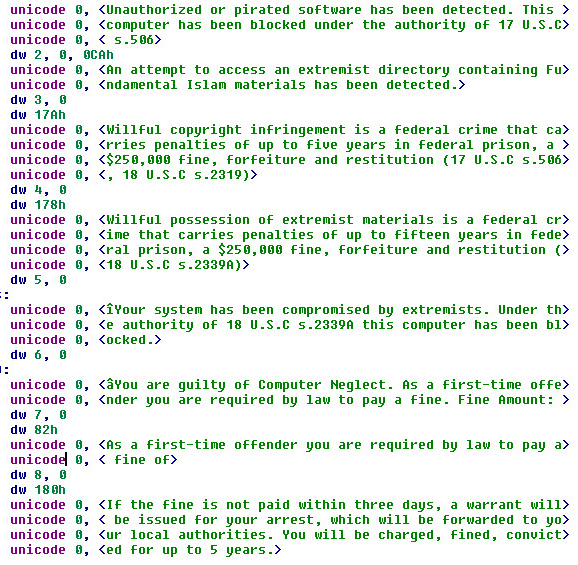
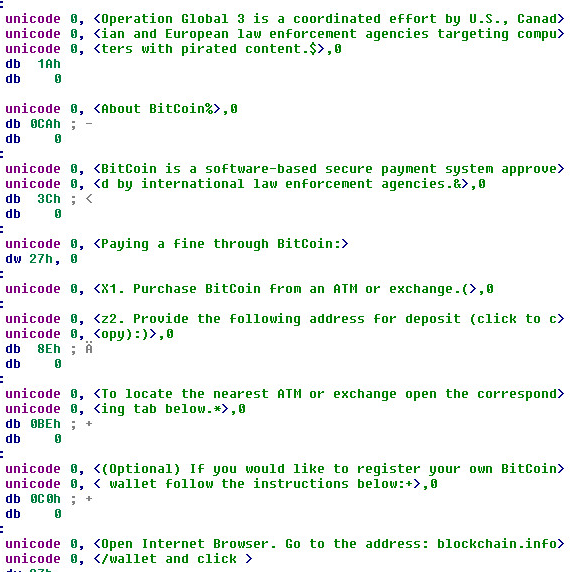
The unpacked binary will produce some interesting strings such as “Islam materials”, “extremist materials” and “Operation Global 3”. The Unicode strings are also translated in German, English and Spanish throughout Ida Pro.
Strings 1:
Strings 2:

Strings 3:
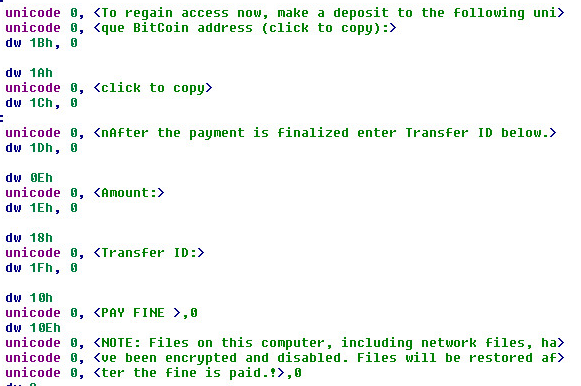
Strings 4:
Supported Systems:
The sample was tested and debugged on (x86) – 32 Bit, Windows 7 Professional.
Summary:
- Attaches the core malware code into the infected file.
- Has the ability to append, prepend, or save the core injection inside a random cavity
- Maintains persistence with: Run Registry Keys, Scheduled Tasks, Startup Folder, and Shim Database.
- Infected file is hard to restore. This involves peeling away the metamorphic code to gain access to the deeply embedded key.
- Holds your computer for ransom.
- Uses cryptocurrency, such as bitcoins for it’s payment model.
- Virlocker is a File Infector and Screen Locker.
- Uses a metamorphic engine with polymorphic routines and various xor encryption and decryption routines.
SonicWall, Signature Hit Graph:
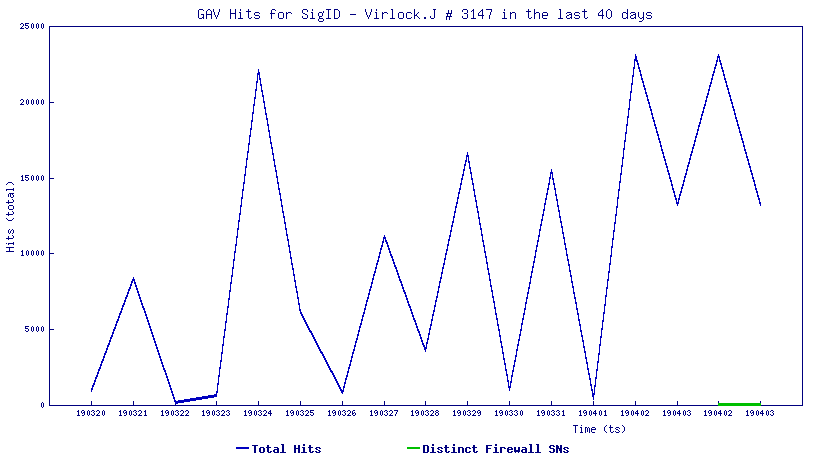
SonicWall, (GAV) Gateway Anti-Virus, provides protection against this threat:
- GAV: Virlock.J (Trojan)




