Bot with possible Chinese origins and Taliban lure (July 27, 2012)
Dell SonicWALL Threats Research team came across a new Malware submission that looks like a bot with backdoor functionality. The Malware executable has Chinese origins based on the file resources and the Command & Control (C&C) domain involved but is using Taliban warfare image as a lure.
The original Malware executable named Talibanwarfare.exe uses an image file icon for disguise and drops the actual bot:
![]()
Upon execution, it drops the following files on the victim machine:
- c:lsass.exe [Malicious bot detected as GAV: Dapato.BNCB (Trojan)]
- c:Talibanwarfare.jpg
The malware displays the dropped image file Talibanwarfare.jpg in default Windows image viewer application to make the user believe that everything is normal while it runs the dropped malicious bot in the background.

It also ensures that the dropped malicious executable runs for the infected user upon system reboot by adding following registry key:
- HKU(USERID)SoftwareMicrosoftWindowsCurrentVersionRunworkstations: “C:lsass.exe”
A quick analysis of the dropped malicious executable shows that it connects to a remote server web(REMOVED)yourturbe.org being hosted in San Francisco, USA. The domain name however was supposedly registered last year by some su guang in China.
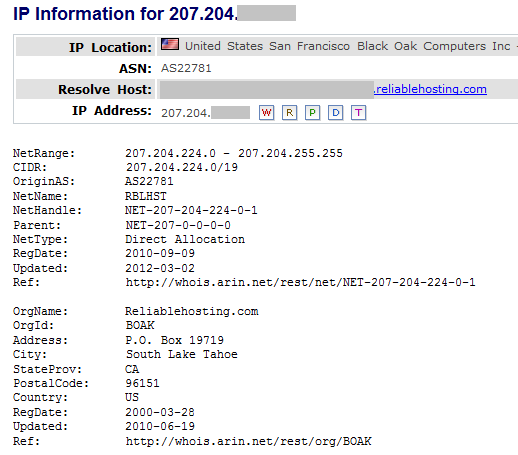

The physical server involved looks to be part of the VPN service provided by Reliablehosting ISP. We found few similar malware samples in our database that connected to this and other VPN servers hosted by Reliablehosting for C&C communication. Reliablehosting has been notified about this and we are working with them to take further action.
The C&C communication in case of this Malware is encrypted. It continuously sends and receives packets from the C&C server every 30 seconds which looks like PING/PONG messages to ensure connectivity:

It is interesting to note that the messages contain fake MSN messenger protocol headers. We also monitored commands to perform a network scan and some basic SMB/CIFS exploit attempts to propagate further inside the infected system’s network. We will update this Alert as we continue to analyze this attack further.
Dell SonicWALL Gateway AntiVirus provides protection against this threat via following signatures:
- GAV: Agent.TBW_2 (Trojan)
- GAV: Dapato.BNCB (Trojan)



