New Botnet controlled via Twitter (Aug 18, 2009)
SonicWALL UTM Research team observed a new Botnet family that uses social networking services like Twitter, Jaiku, Tumblr as its Command & Control (C&C) server mechanism.
The status messages on the social blogging sites serve as the C&C commands that contain links to download malicious payload. The status messages are Base-64 encoded.
Example Base-64 encoded status message shown below:
aHR0cDovL2JpdC5seS9HaHVVdSBodHRwOi8vYml0Lmx5L1FqC
decodes to
http://bit.ly/GhuUu -> http://rifers.org/paste/content/paste/9506/body [Malware payload]
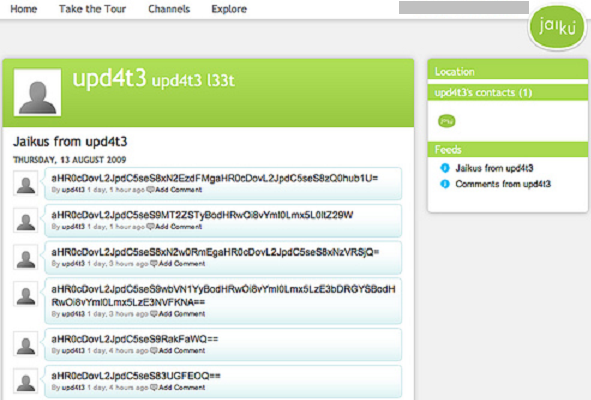
The name of one such account used for issuing C&C commands on these blogging sites – upd4t3. Twitter, Jaiku, and Tumblr have already suspended the account in question but there could be more such accounts.
This Bot is packed using MPRESS packer. It is also known as Trojan:Win32/Svelta.A [Microsoft], Trojan-Banker.Win32.Banker.alvx [Kaspersky], and W32/Bancos.MSB [Eset].
SonicWALL Gateway AntiVirus provides protection against this malware via GAV: Suspicious#mpress (Worm),GAV: Suspicious#mpress.2 (Worm), and GAV: Agent.CMCF (Trojan) signatures.
Screenshot of the Twitter C&C account –

Screenshot of the Jaiku C&C account –