Microsoft Security Bulletin Coverage for December 2023
Overview
Microsoft’s December 2023 Patch Tuesday includes 33 vulnerabilities, 10 of which are Elevation of Privilege. The vulnerabilities can be classified into the following categories:
- 10 Elevation of Privilege Vulnerabilities
- 8 Remote Code Execution Vulnerabilities
- 5 Information Disclosure Vulnerabilities
- 5 Denial of Service Vulnerabilities
- 5 Spoofing Vulnerabilities
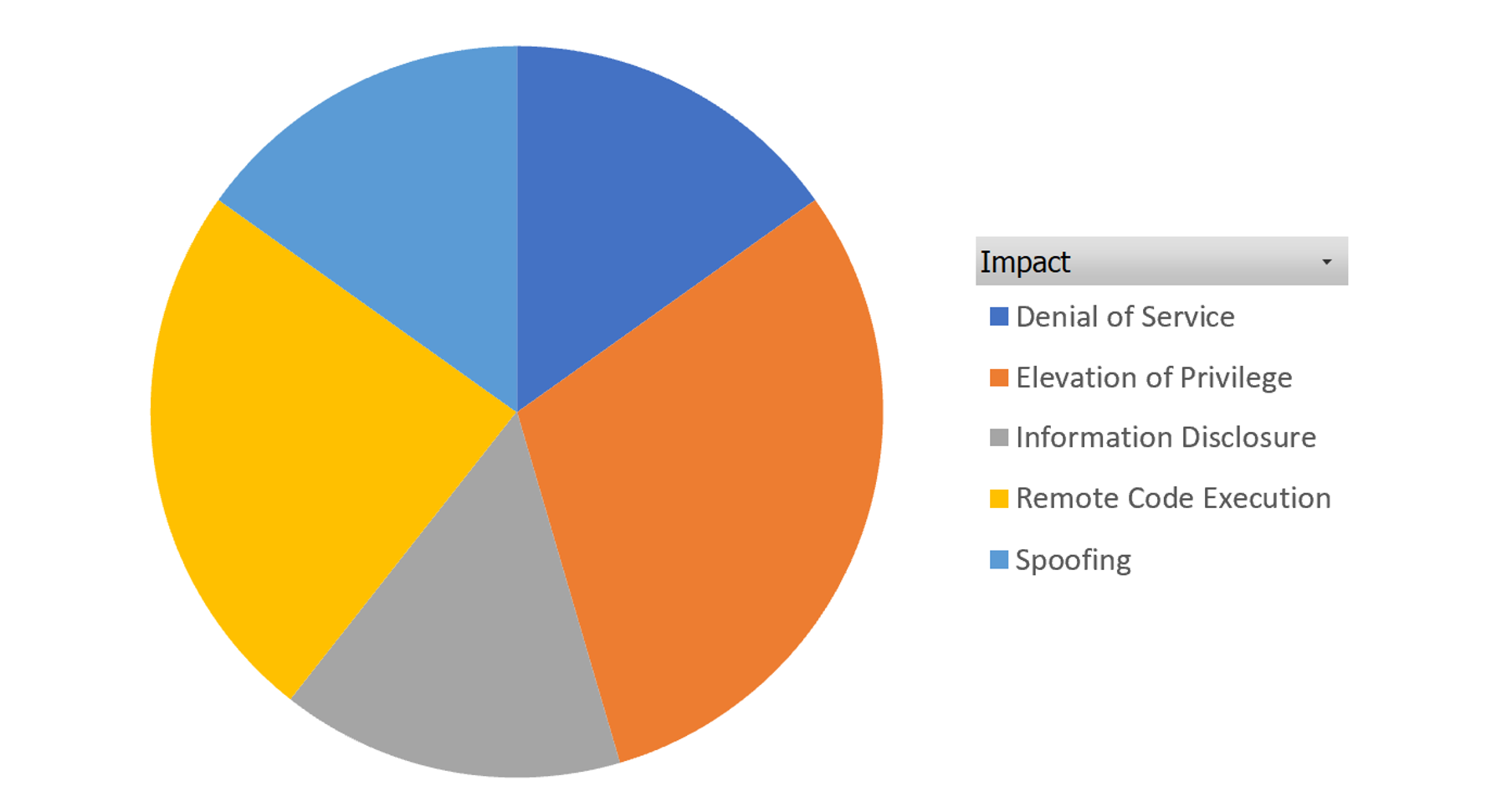
December Vulnerabilities by Impact
SonicWall Capture Labs threat research team has analyzed and addressed Microsoft’s security advisories for the month of December 2023 and has produced coverage for seven of the reported vulnerabilities.
Vulnerabilities with detections
CVE-2023-35631 Win32k Elevation of Privilege Vulnerability
ASPY 512 Exploit-exe exe.MP_353
CVE-2023-35632 Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability
ASPY 518 Exploit-exe exe.MP_359
CVE-2023-35633 Windows Kernel Elevation of Privilege Vulnerability
ASPY 513 Exploit-exe exe.MP_354
CVE-2023-35644 Windows Sysmain Service Elevation of Privilege Vulnerability
ASPY 514 Exploit-exe exe.MP_355
CVE-2023-36005 Windows Telephony Server Elevation of Privilege Vulnerability
ASPY 515 Exploit-exe exe.MP_356
CVE-2023-36391 Local Security Authority Subsystem Service Elevation of Privilege Vulnerability
ASPY 516 Exploit-exe exe.MP_357
CVE-2023-36696 Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability
ASPY 517 Exploit-exe exe.MP_358
Remote Code Execution Vulnerabilities
CVE-2023-21740 Windows Media Remote Code Execution Vulnerability
CVE-2023-35628 Windows MSHTML Platform Remote Code Execution Vulnerability
CVE-2023-35629 Microsoft USBHUB 3.0 Device Driver Remote Code Execution Vulnerability
CVE-2023-35630 Internet Connection Sharing (ICS) Remote Code Execution Vulnerability
CVE-2023-35634 Windows Bluetooth Driver Remote Code Execution Vulnerability
CVE-2023-35639 Microsoft ODBC Driver Remote Code Execution Vulnerability
CVE-2023-35641 Internet Connection Sharing (ICS) Remote Code Execution Vulnerability
CVE-2023-36006 Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability
Elevation of Privilege Vulnerabilities
CVE-2023-35624 Azure Connected Machine Agent Elevation of Privilege Vulnerability
CVE-2023-35631 Win32k Elevation of Privilege Vulnerability
CVE-2023-35632 Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability
CVE-2023-35633 Windows Kernel Elevation of Privilege Vulnerability
CVE-2023-35644 Windows Sysmain Service Elevation of Privilege Vulnerability
CVE-2023-36003 XAML Diagnostics Elevation of Privilege Vulnerability
CVE-2023-36005 Windows Telephony Server Elevation of Privilege Vulnerability
CVE-2023-36011 Win32k Elevation of Privilege Vulnerability
CVE-2023-36391 Local Security Authority Subsystem Service Elevation of Privilege Vulnerability
CVE-2023-36696 Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability
Denial of Service Vulnerabilities
CVE-2023-35621 Microsoft Dynamics 365 Finance and Operations Denial of Service Vulnerability
CVE-2023-35635 Windows Kernel Denial of Service Vulnerability
CVE-2023-35638 DHCP Server Service Denial of Service Vulnerability
CVE-2023-35642 Internet Connection Sharing (ICS) Denial of Service Vulnerability
CVE-2023-36010 Microsoft Defender Denial of Service Vulnerability
Information Disclosure Vulnerabilities
CVE-2023-35625 Azure Machine Learning Compute Instance for SDK Users Information Disclosure Vulnerability
CVE-2023-35636 Microsoft Outlook Information Disclosure Vulnerability
CVE-2023-35643 DHCP Server Service Information Disclosure Vulnerability
CVE-2023-36009 Microsoft Word Information Disclosure Vulnerability
CVE-2023-36012 DHCP Server Service Information Disclosure Vulnerability
Spoofing Vulnerabilities
CVE-2023-35619 Microsoft Outlook for Mac Spoofing Vulnerability
CVE-2023-35622 Windows DNS Spoofing Vulnerability
CVE-2023-36004 Windows DPAPI (Data Protection Application Programming Interface) Spoofing Vulnerability
CVE-2023-36019 Microsoft Power Platform Connector Spoofing Vulnerability
CVE-2023-36020 Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability




