Cybersecurity News & Trends – 05-27-21
This week, healthcare was under attack in the U.S. and abroad, as facilities reported outages and blackmail demands.
SonicWall in the News
Discord is now the young hacker’s weapon of choice — here’s why — tom’s guide
“Discord is the potential future of the dark net,” said Brook Chelmo, a senior strategist for SonicWall, during his recent RSA session.
Fish out the Phishing attacks — Security Middle East & Africa
“The best defense against most credential harvesting attacks is the use of a password manager,” SonicWall’s Mohamed Abdallah said. “Most are free, and none can be fooled into entering a password into a malicious site, no matter how authentic it seems.”
Industry News
As Chips Shrink, Rowhammer Attacks Get Harder to Stop — Ars Technica
A full fix for the “Half-Double” technique will require rethinking how memory semiconductors are designed.
Rise in Opportunistic Hacks and Info-Sharing Imperil Industrial Networks — Dark Reading
Security researchers have seen an increasing wave of relatively simplistic attacks involving ICS systems (and attackers sharing their finds with one another) since 2020.
Alleged North Korean hackers scouted crypto exchange employees before stealing currency — Cyberscoop
Suspected North Korean hackers have breached cryptocurrency exchanges in Japan, Europe, the U.S. and Israel in an effort to steal millions of dollars from the platforms in the last three years.
Ransomware: Two-thirds of organisations say they’ll take action to boost their defences — ZDNet
The impact of the Colonial Pipeline ransomware attack is leading companies to re-examine their cybersecurity strategies.
New Zealand Hospitals Under Prolonged IT Outage From Ransom Hack — Bloomberg
Systems are still down a week after a ransomware attack disrupted the IT network of five hospitals in the New Zealand district of Waikato, and concerns remain that private patient information may have been exposed.
Iranian hacking group targets Israel with wiper disguised as ransomware — Bleeping Computer
An Iranian hacking group has been observed camouflaging destructive attacks against Israeli targets as ransomware attacks. Meanwhile, they’re maintaining access to victims’ networks for months.
Gartner: Global Security Spending Will Reach $150 Billion in 2021 — Security Week
Gartner says nearly half (roughly $72 billion) will be spent on security services, including consulting, hardware support, and implementation and outsourced services.
Hear ye, DarkSide! This honorable ransomware court is now in session — Ars Technica
A crime forum is holding a quasi-judicial proceeding against the makers of DarkSide to hear claims from former affiliates who say the makers skipped town without paying.
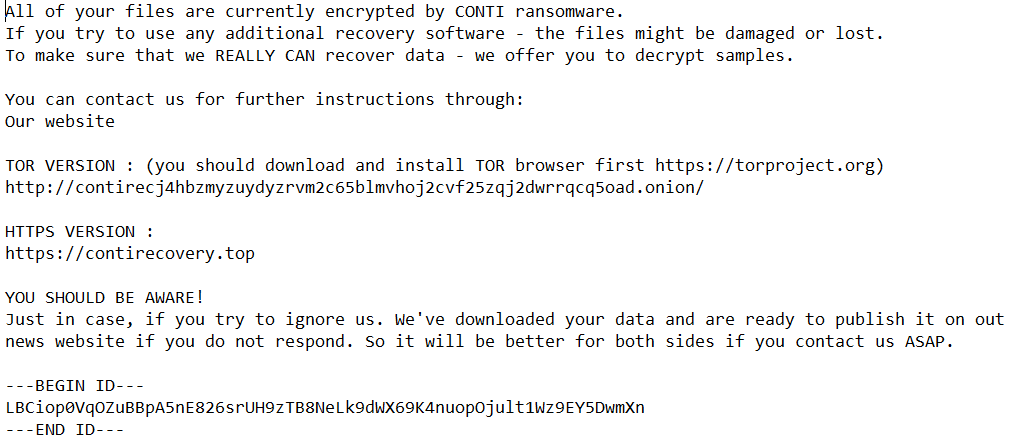
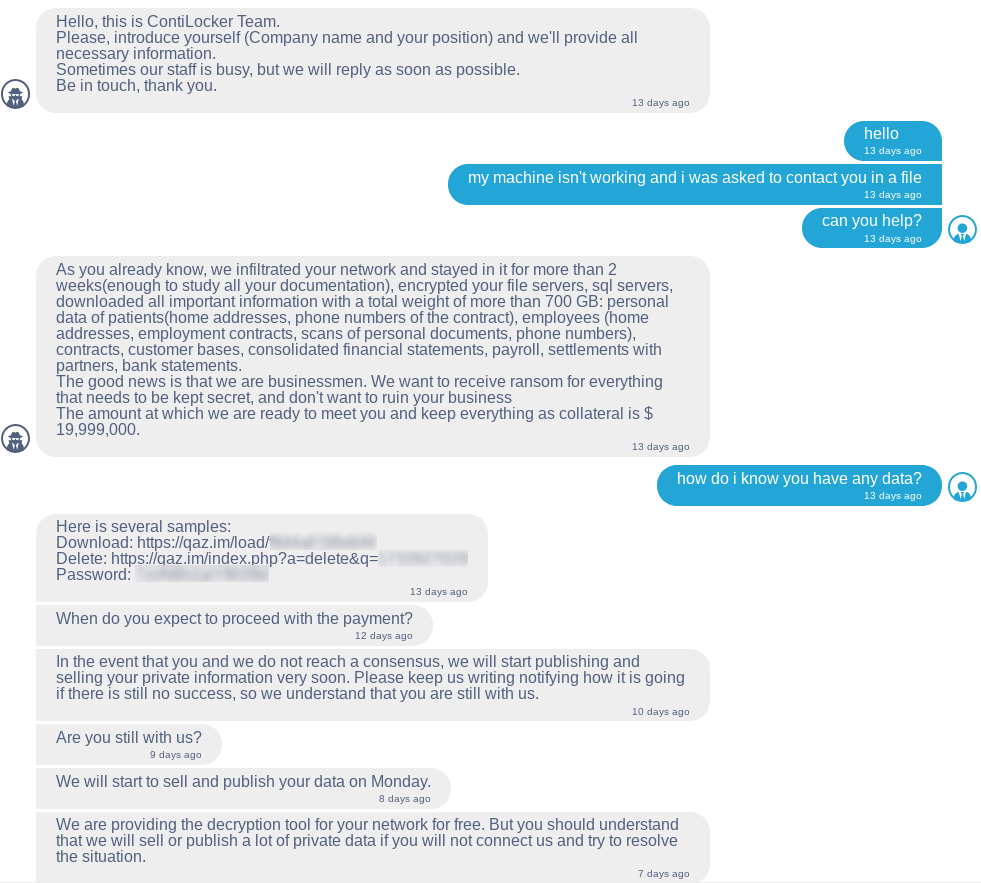
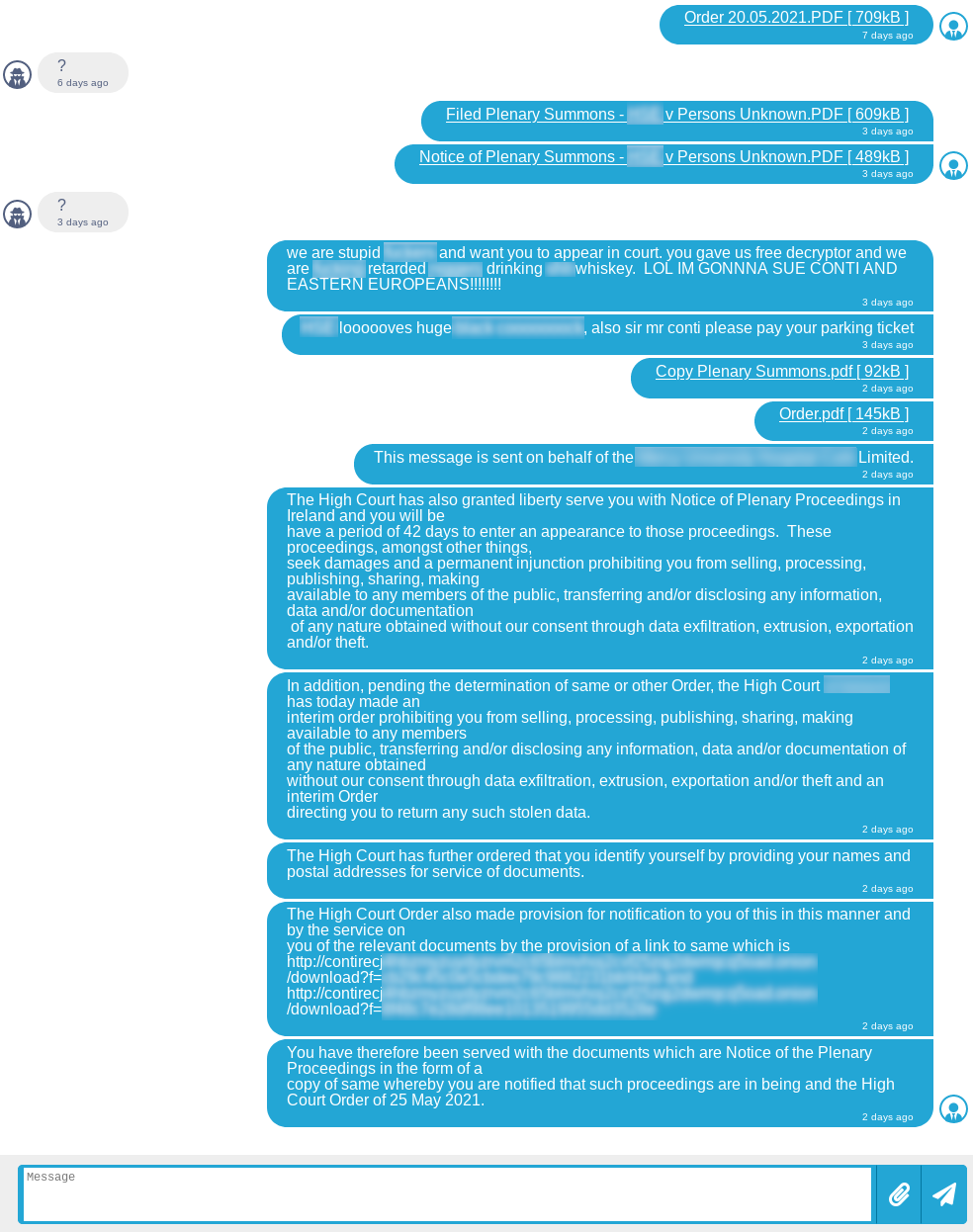
FBI identifies 16 Conti ransomware attacks striking US healthcare, first responders — ZDNet
The targets identified include 911 dispatch carriers, law enforcement agencies and emergency medical services — all of which have been attacked over the past year as medical services struggled to manage the pandemic.
Vulnerability in VMware product has severity rating of 9.8 out of 10 — Ars Technica
The security flaw, which VMware disclosed and patched on Tuesday, resides in the vCenter Server, one of the most popular virtualization solutions on the market.
Cyber insurance premiums, take-up rates surge, says GAO — ZDNet
A General Accountability Office report finds that cyber insurance premiums surged in 2020 based on more frequent cyberattacks. That trend is likely to continue.
Zeppelin ransomware comes back to life with updated versions — Bleeping Computer
The developers of Zeppelin ransomware have resumed activity after a period of relative silence that started last fall.
This massive phishing campaign delivers password-stealing malware disguised as ransomware — ZDNet
Java-based STRRAT malware creates a backdoor into infected machines — but distracts victims by acting like ransomware.
Bizarro banking malware targets 70 banks in Europe and South America — Bleeping Computer
A banking trojan named Bizarro that originates from Brazil has crossed the borders and started to target customers of 70 banks in Europe and South America.
E-commerce giant suffers major data breach in Codecov incident — Bleeping Computer
E-commerce platform Mercari has disclosed a major data breach incident that occurred due to exposure from the Codecov supply-chain attack.
QNAP confirms Qlocker ransomware used HBS backdoor account — Bleeping Computer
QNAP is advising customers to update the HBS 3 disaster recovery app. The goal: to block Qlocker ransomware attacks targeting their Internet-exposed Network Attached Storage (NAS) devices.
In Case You Missed It
Infiltrate, Adapt, Repeat: A Look at Tomorrow’s Malware Landscape — Brook Chelmo
Join us for the 2021 SonicWall Partner Virtual Roadshow — David Bankemper
Capture Client 3.6 Launch Brings Key Features — Brook Chelmo
Using Client VPN with Your Firewall for WFH: a Setup for Disaster? — Jean-Pier Talbot
Triple Threat: CRN’s 2021 Women of the Channel List Honors SonicWall Leaders — Lindsey Lockhart