Zeus, also known as Zbot, WSNPoem and NTOS is a crimeware kit. It offers its own cryptor that obfuscates the Trojan, making it difficult to detect. The cryptor creates a new binary file each time it is used, and these files are radically different from each other. SonicWALL blocks over 3,500 different binary variants of the Zeus Trojan.
Zeus is built for hijacking E-banking sessions, although it can steal credentials for any online services. The kit costs about $700 to purchase.
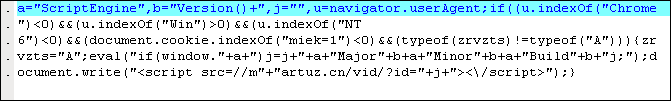
The Zeus Trojan is frequently installed through drive-by exploits or through spam mails that pretend to be invoices and contain a copy of the Trojan as an attachment.
Typically the Trojan is located on the system at:
- Variant A:
- C:WINDOWSsystem32ntos.exe
- C:WINDOWSsystem32wsnpoemaudio.dll
- C:WINDOWSsystem32wsnpoemvideo.dll
- Variant B:
- C:WINDOWSsystem32oembios.exe
- C:WINDOWSsystem32sysproc64sysproc86.sys
- C:WINDOWSsystem32sysproc64sysproc32.sys
- Variant C:
- C:WINDOWSsystem32twext.exe
- C:WINDOWSsystem32twain_32local.ds
- C:WINDOWSsystem32twain_32user.ds
Zeus consists of three parts:
- Control Panel, which is installed on the server
- Builder, an application for Windows, is used to specify the configuration for the infector bot.
- Bot, Trojan for for Windows, infects the victim, then connects to the dropzone.
Zeus host consists of three components as well:
- a config file (usually with file extension *.bin)
- a binary file which contains the newest version of the trojan
- a dropzone (usually a php file)
The config file is an encrypted binary file that contains information necessary for the Zeus bot to update itself and instructions where to submit stolen data. Also, it has a list of sites to target, to avoid, and what code to inject into web pages.
Decoding Zeus Config

Zeus uses HTTP for command and control. It is built on PHP, mySQL. The system normally installs with a password protection scheme using HTTP basic authentication to protect the botnet. The Zeus botnet uses HTTP to communicate to its controlling servers by sending a POST message to the server. The response contains an encoded command.
The Zeus is capable of logging all network information, stealing banking data or credit card numbers, controlling the system, sending spam, or stealing passwords from Protected Storage. The collected info is sent to the dropzone via HTTP requests. Zeus can be re-configured, malware retrieves current configuration file from the dropzone.
It is a very effective stealer of user private and confidential information (form grabber), it can inject arbitrary HTML code into any website (also encrypted websites), can steal certificates and use screenshots to defeat virtual keyboards commonly used by financial institutions. It can also act as a proxy server via Socks 4/4a/5, even if compromised device is behind a NAT.
Zeus kit is a complete package, complex professional software with a team of Russian programmers actively developing it. Zeus’s “features under development” include:
- Compatibility with Windows Vista and Windows 7
- Random generation of configuration files to avoid generic detection”
- Console-based builder
- Full IPv6 support
- Detailed statistics on antivirus software and firewalls installed on the infected machines
Zeus even has its own EULA (end-user license agreement), in Russian.

Which translates roughly as follows:
- The user may not distribute the product in a commercial way.
- The user may not reverse-engineer the bot builder.
- The user may not use the control panel to control other botnets.
- The user may not deliberately share any portion of the code to anti-virus companies.
- The user must pay for any future features or improvements..
According to Zeus Tracker, the countries where most Zeus sites are hosted are USA, Russia, China, Ukraine and Latvia. More than half of the dropzones are hosted on bullet-proof hosting (providers that do not honor takedown requests).
The individuals behind Zeus are allegedly based in Europe, and known as the Rock Phish group. It is a criminal collective that has been targeting banks and other financial institutions since 2004. According to RSA, they are responsible for half of the worldwide phishing attacks and have siphoned tens of millions of dollars from individuals’ bank accounts. The group got its name from an old feature where phishers used directory paths that contained the word “rock.”
Antivirus companies have different names for Zeus threat, most common being: Trojan.Wsnpoem (Symantec), W32/Zbot (F-Secure), Trojan.Spy.Zeus (Bitdefender), TSPY_ZBOT (TrendMicro), NTOS.
SonicWALL has many signatures protecting from variants of Zeus malware, including: GAV: Zbot.HNO (Trojan) , GAV: ZBot.gen (Trojan) , GAV: Zbot.AEZ (Trojan) , GAV: Zbot.ABC (Trojan) , GAV: Zbot.CMS (Trojan) , GAV: Zbot.RL (Trojan) , GAV: Zbot.IXC (Trojan).
Zeus builder

Zeus admin panel
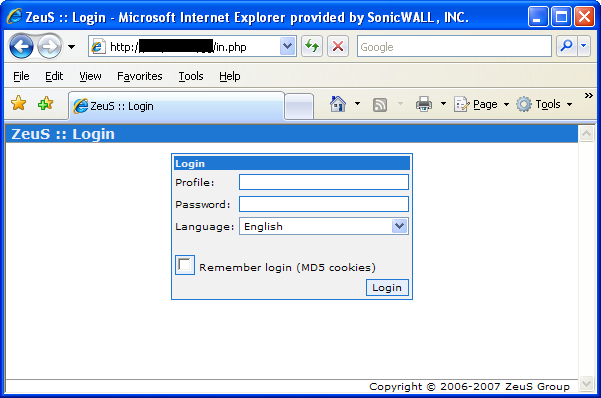
Some screenshots from www.abuse.ch:
Zeus admin panel

Zeus stats

Issuing a command

Online Bots

Browsing logs for stolen accounts

For more on ZEUS check out Zeus Tracker .