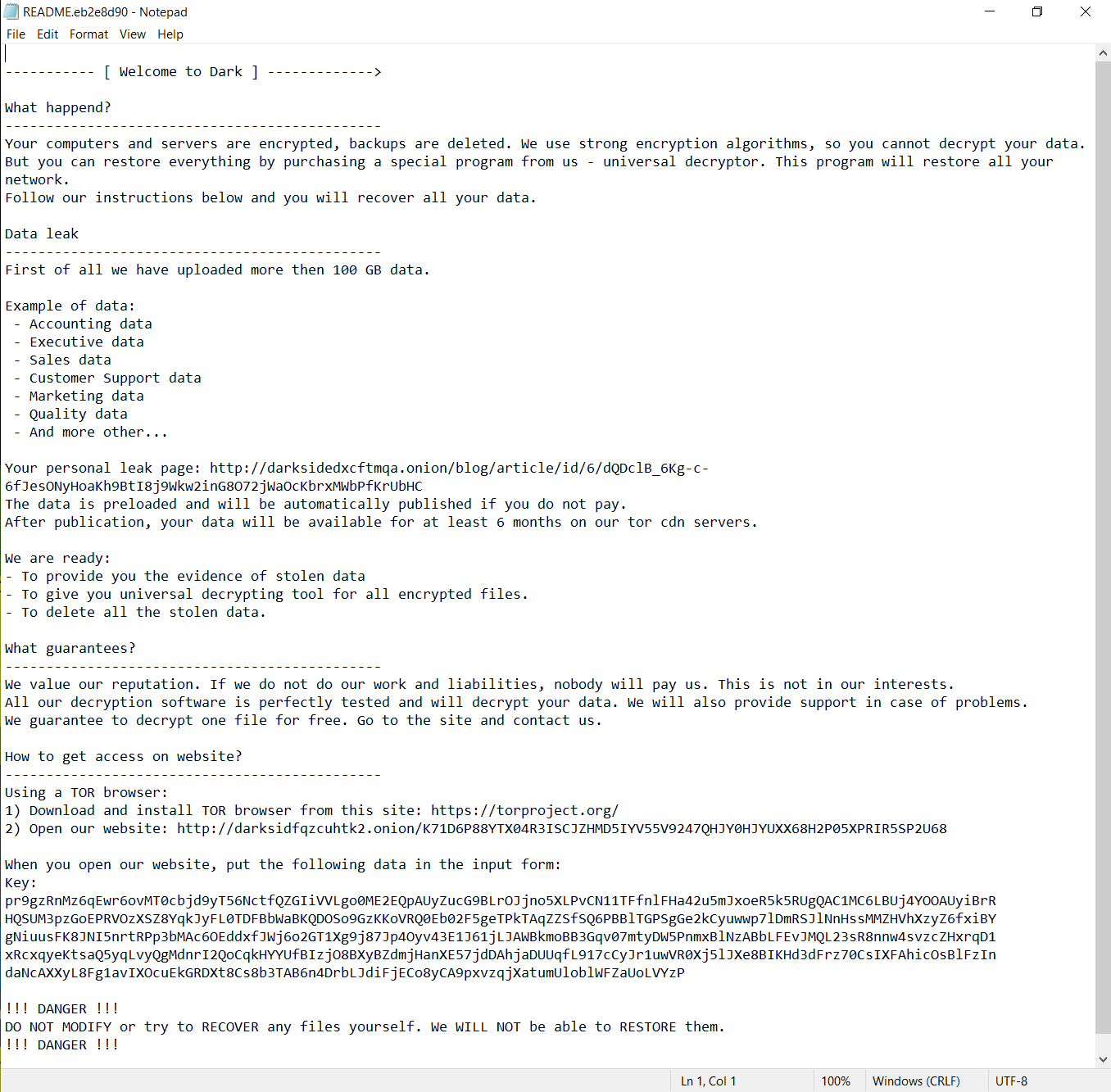
Windows Netlogon Elevation of Privilege Vulnerability CVE-2020-1472
An elevation of privilege vulnerability exists when an attacker establishes a vulnerable Netlogon secure channel connection to a domain controller, using the Netlogon Remote Protocol (MS-NRPC). An attacker who successfully exploited the vulnerability could run a specially crafted application on a network device.
This vulnerability also called Zerologon has a CVSS score of 10.
Netlogon Remote Protocol
The Netlogon Remote Protocol is used for secure communication between machines in a domain and domain controllers (DCs) The communication is secured by using a shared session key computed between the client and the DC that is engaged in the secure communication. The session key is computed by using a preconfigured shared secret that is known to the client and the DC. The Microsoft Windows Netlogon Remote Protocol (MS-NRPC) is a core authentication component of Active Directory that provides authentication for user and computer accounts.
Vulnerability (CVE-2020-1472)
The vulnerability arises from a flaw in the cryptographic implementation of the Netlogon protocol, specifically in its usage of AES-CFB8 encryption. MS-NRPC uses an initialization vector (IV) of 0 (zero) in AES-CFB8 mode when authenticating computer accounts.Due to incorrect use of an AES mode of operation it is possible to spoof the identity of any computer account (including that of the DC itself) and set an empty password for that account in the domain.
The successful exploitation of the vulnerability will allow an attacker to
- Impersonate any computer on the network,
- Disable security features that protect the Netlogon process
- Change a computer’s password associated with its Active Directory account.
Affected products
- Windows Server 2008 R2 for x64-based Systems Service Pack 1
- Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation)
- Windows Server 2012
- Windows Server 2012 (Server Core installation)
- Windows Server 2012 R2
- Windows Server 2012 R2 (Server Core installation)
- Windows Server 2016
- Windows Server 2016 (Server Core installation)
- Windows Server 2019
- Windows Server 2019 (Server Core installation)
- Windows Server, version 1903 (Server Core installation)
- Windows Server, version 1909 (Server Core installation)
- Windows Server, version 2004 (Server Core installation)
Microsoft has patched this vulnerability and is urging to prioritize patching Domain Controllers, as this is likely the primary target.
SonicWall Capture Labs provides protection against this threat via the following signatures:
- IPS 15143:Windows Netlogon Elevation of Privilege Vulnerability (CVE-2020-1472)1
- IPS 15156:Windows Netlogon Elevation of Privilege Vulnerability (CVE-2020-1472) 2
- IPS 15158:Windows Netlogon Elevation of Privilege Vulnerability (CVE-2020-1472) 3