SysAid Path Traversal Vulnerability
Overview
SonicWall Capture Labs Threat Research Team became aware of the SysAid path traversal vulnerability, assessed its impact and developed mitigation measures for the vulnerability. On November 8, 2023, SysAid, an IT service management company, disclosed CVE-2023-47426, which is a zero-day path traversal vulnerability carrying a CVSS 9.8 score and affecting on-premise SysAid servers running version < 23.3.36. According to Microsoft’s threat intelligence team and SysAid’s Advisory, it has been exploited in the wild by Lace Tempest (DEV-0950 / TA-505). SonicWall is also currently seeing an increasing number of active exploitation attempts. This is the same threat actor responsible for exploiting the MoveIT File Transfer Tool vulnerability, and the threat actor is associated with a ransomware group known as "CL0P". To mitigate this vulnerability, SysAid has released a patch which is present in version 23.3.36.
CVE Details
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2023-47246.
The overall CVSS score is 9.8 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H).
Base score is 9.8 (AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H), based on the following metrics:
- Attack vector is network.
- Attack complexity is low.
- Privileges required is none.
- User interaction is none.
- Scope is unchanged.
- Impact of this vulnerability on data confidentiality is high.
- Impact of this vulnerability on data integrity is high.
- Impact of this vulnerability on data availability is high.
Technical Overview
This path traversal vulnerability allows for threat actors to upload a malicious WAR archive that contains a web shell into the webroot of the SysAid Tomcat web service through a POST request. The attacker can then request the web shell by browsing to the URL where it now resides to gain access to the server.
Triggering the Vulnerability
The vulnerability exists within the SysAid com.ilient.server.UserEntry class in the doPost method. The accountID parameter within this request is suspectable to the path injection since it is directly passed to the File function. By decompiling the Java code, it is possible to see the accountID parameter being saved into a string variable named convertParamater as shown in Figure 1.
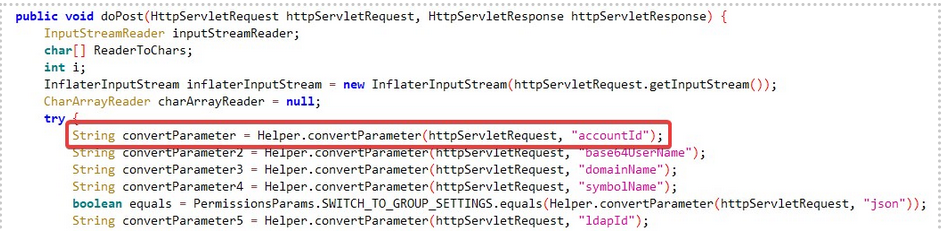
Figure 1: doPost Method parsing accoutnId
convertParameter is then stored in a variable which is passed to the file constructor as shown in Figure 2. For readability, the variable has been renamed accountIDParameter.
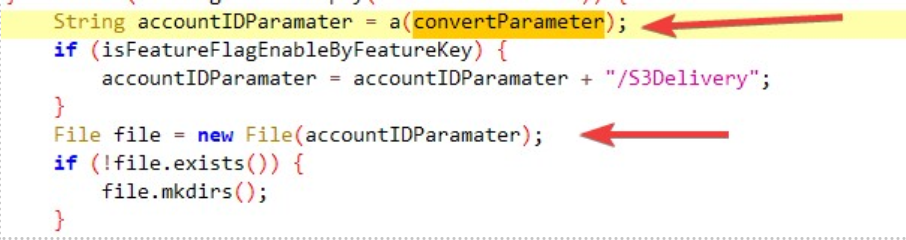
Figure 2: accountID being used to create a file
The path dictated in the accountID parameter is the location where the data in the body of the POST request will be written. Therefore, to trigger and leverage this vulnerability the attacker needs to send a POST request to the server with the accountID parameter set to where the data in the body of the post request should be written.
Exploitation
Threat actors have been seen successfully exploiting this vulnerability by uploading a WAR archive that contains a web shell into the webroot of the SysAid Tomcat web service. This is accomplished by sending a POST request with a zlib compressed WAR file containing the web shell as the request body and the accountID parameter are injected with the webroot directory. The threat actor then executes this web shell and gains access to the system by navigating to the location injected into the accountID parameter.
Post-Exploitation
After gaining a web shell through the SysAid vulnerability, threat actors were seen leveraging two PowerShell scripts to carry out post exploitation activities. The first is used to launch a malware loader named user.exe. This loads the GraceWire trojan and injects it into Windows processes such as spoolsv.ese. Following the first GraceWire trojan deployment, a second PowerShell script is used to erase evidence associated with the attacker’s actions including cleaning the SysAid on-prem server web logs. Figure 3 below shows the complete attack chain as presented by Zscaler.
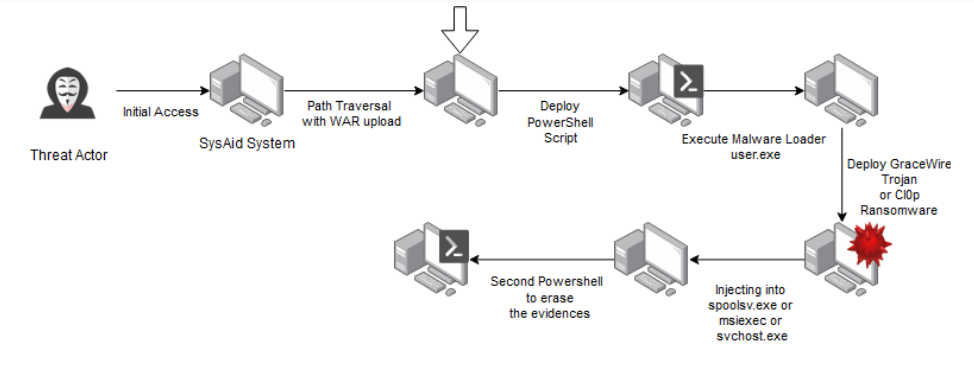
Figure 3: Zscaler’s suspected exploit chain
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signatures have been released:
- Attempted Exploitation – IPS:4172 SysAid On-Prem Software Directory Traversal
- Known Post Exploitation – SPY: 500 Malformed-ps1 ps1.OT_1
- Known Post Exploitation – SPY: 501 Malformed-ps1 ps1.OT_2
Threat Graph
SonicWall sensors have confirmed active exploitation of these vulnerabilities. The graph in Figure 4 indicates an increasing number of exploitation attempts and we expect exploitations to continue to increase.
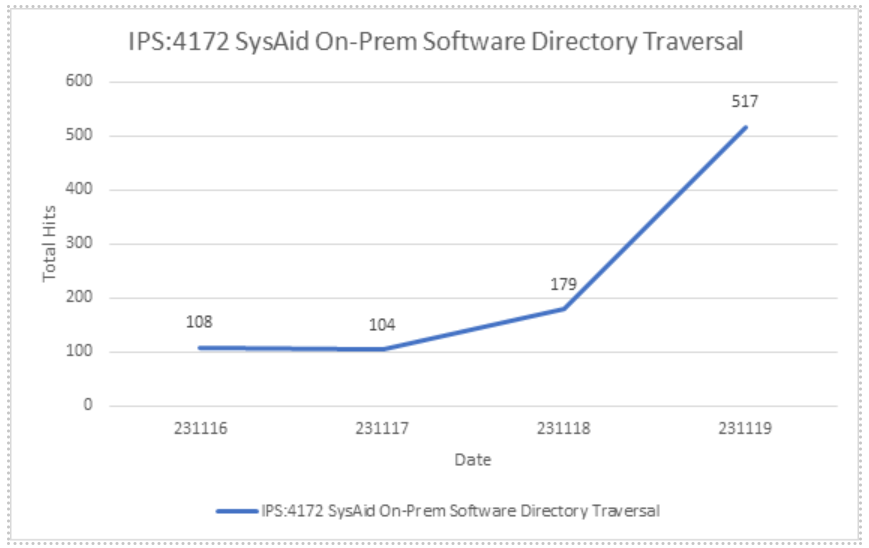
Figure 4: SonicWall IPS 4172 Threat Graph
Remediation Recommendations
SysAid has released an update to patch the vulnerability, and it is strongly recommended to update to version 23.3.36 if running a SysAid On-Prem server. The SysAid advisory has also published relevant IOCs and recommendations to identify any system compromise.
Relevant Links
- https://www.sysaid.com/blog/service-desk/on-premise-software-security-vulnerability-notification
- https://profero.io/posts/sysaidonpremvulnerability/
- https://www.zscaler.com/blogs/security-research/coverage-advisory-cve-2023-47246-sysaid-zero-day-vulnerability
- https://www.rapid7.com/blog/post/2023/11/09/etr-cve-2023-47246-sysaid-zero-day-vulnerability-exploited-by-lace-tempest/
- https://www.huntress.com/blog/critical-vulnerability-sysaid-cve-2023-47246
