TOTOLINK A3000RU Command Injection
Zioncom (Hong Kong) Technology Limited also know as TOTOLINK is a professional manufacturer for network communication products, including Wireless Router/AP (Indoor & Outdoor), Wireless USB Adapter, Wireless Module, Switch and Wired Router. ZIONCOM (HK) was established on 1999.
A3000RU is a wireless router complies with the latest IEEE 802.11ac wave2 Wi-Fi standard, with MU-MIMO technology offering continual high speed data transmission for multiple devices at the same time.
Command injection vulnerability exists in TOTOLINK A3000RU router.
Command Injection Vulnerability
The goal of command injection attack is the execution of arbitrary commands on the host operating system via a vulnerable application. Command injection attacks are possible when an application passes unsafe user-supplied data (forms, cookies, HTTP headers etc.) to a system shell. In this attack, the attacker-supplied operating system commands are usually executed with the privileges of the vulnerable application. Command injection attacks are possible largely due to insufficient input validation
TOTOLINK A3000RU Command Injection | CVE-2022-25075
TOTOLink A3000RU V5.9c.2280_B20180512 was discovered to contain a command injection vulnerability in the “Main” function. This vulnerability allows attackers to execute arbitrary commands via the QUERY_STRING parameter.
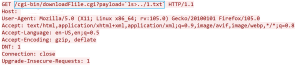
In the following exploit the attacker can pass commands like ‘wget’ via the query string . This command is used to download toto.sh script from the attacker controlled website. The attacker then changes the permissions of the script and executes the malicious script on the device.
SonicWall Capture Labs provides protection against this threat via following signature:
- IPS 15515:TOTOLINK A3000RU Command Injection
IoCs
179.43.142.11
36db973e85684633846a2cd9c46ca48896b5703b9aeb174b1f741633428f68c1
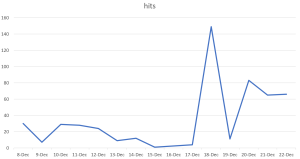
Threat Graph