Microsoft Exchange Server HandleBackEndCalculationException Vulnerability
Overview:
Microsoft Exchange Server is an ASP.NET implementation of an email and calendaring server and is capable of handling most standard Internet protocols as well as numerous proprietary Microsoft protocols and formats. Microsoft Exchange Server provides web access for users to various components such as Outlook Web Access and Autodiscover. Autodiscover is a component that allows clients to automatically discover the Exchange settings for the client without requiring users to know specific server addresses.
A reflected cross-site scripting vulnerability has been reported in Microsoft Exchange Server. The vulnerability is due to insufficient sanitization of incoming request parameters reflected in exception messages returned by the
server.
A remote attacker can exploit this vulnerability by enticing a target user into clicking a malicious link. Successful exploitation could result in arbitrary script execution in the target user’s browser.
CVE Reference:
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2021-41349.
Common Vulnerability Scoring System (CVSS):
The overall CVSS score is 8.6 (CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H/E:P/RL:O/RC:C).
Base score is 9.6 (AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H), based on the following metrics:
• Attack vector is network.
• Attack complexity is low.
• Privileges required is none.
• User interaction is required.
• Scope is changed.
• Impact of this vulnerability on data confidentiality is high.
• Impact of this vulnerability on data integrity is high.
• Impact of this vulnerability on data availability is high.
Temporal score is 8.6 (E:P/RL:O/RC:C), based on the following metrics:
• The exploit code maturity level of this vulnerability is proof of concept.
• The remediation level of this vulnerability is official fix.
• The report confidence level of this vulnerability is confirmed.
Technical Overview:
When any Exchange module receives an HTTP request, it is eventually handled by the OnPostAuthorizeInternal() method of the ProxyModule class in Microsoft.Exchange.FrontEndHttpProxy.dll. In the case the request is not authenticated, the SelectHandlerForUnauthenticatedRequest() method is then called which checks the value of the HttpProxy.ProtocolType property to determine which module the request was received by and decide which specific ProxyRequestHandler class to instantiate in order to handle the request. In the case that the request is received by the Autodiscover module (i.e. the request-URI begins with “/autodiscover”) HttpProxy.ProtocolType is set to “Autodiscover” and as a result SelectHandlerForUnauthenticatedRequest() creates an AutodiscoverProxyRequestHandler object as the handler for the request.
Once the handler is chosen, the Run() method of the ProxyRequestHandler object is called which applies the handler to the HttpContext object for the request with the RemapHandler() method. The request is then processed with the BeginProcessRequest() method which queues a call to the BeginCalculateTargetBackEnd() method in the thread pool. BeginCalculateTargetBackEnd() calls InternalBeginCalculateTargetBackEnd() which attempts to resolve the anchor mailbox location for the request. The resolution is performed by first calling TryDirectTargetCalculation(), which returns null because this is the default method behaviour and the method is not overridden by AutodiscoverRequestHandler or any of its parent classes. InternalBeginCalculateTargetBackEnd() then calls ResolveAnchorMailbox() which is overridden in AutodiscoverRequestHandler and its parent classes EwsAutodiscoverProxyRequestHandler and BEServerCookieProxyRequestHandler.
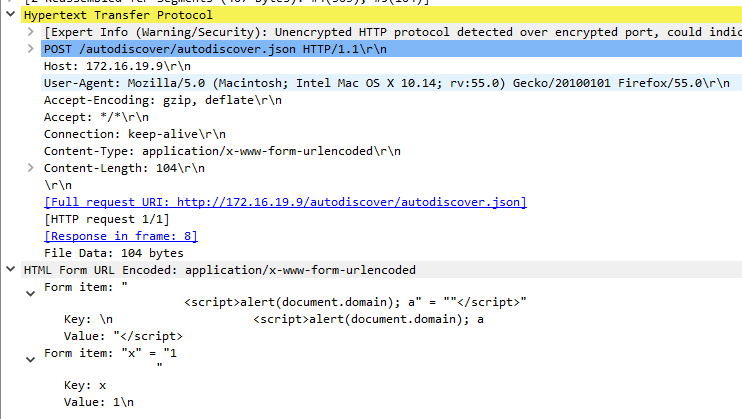
AutodiscoverRequestHandler.ResolveAnchorMailbox() only handles autodiscover requests with a request-URI containing “/wssecurity/x509cert” and otherwise calls EwsAutodiscoverProxyRequestHandler.ResolveAnchorMailbox(). This method inspects the request-URI to see if it corresponds to a specific type of autodiscover request. If the request path ends with “/autodiscover.json” it is considered an “autodiscover V2 preview request” and if this is the case, an explicit logon address is retrieved from the Email HTTP query, form field, or cookie value. When attempting to retrieve the value from HTML form fields, the ValidateHttpValueCollection() method is called to validate the form fields. In turn, this method calls ValidateString() on each form field.
Each field is checked by calling System.Web.Util.RequestValidator.IsValidRequestString(), which calls System.Web.CrossSiteScriptingValidation.IsDangerousString() with the form field value. This method considers the value dangerous if it contains either (1) ‘<' followed by a letter, '!', '/', or '?'; or (2) the sequence "&#". If the form field value is considered dangerous, the ValidateString() method returns an HttpRequestValidationException exception. This exception's message contains the form name and its truncated value.
If an HttpRequestValidationException exception is thrown, it is caught by the method BeginCalculateTargetBackEnd() and the exception is handled by HandleBackEndCalculationException(). This exception is eventually handled by the method HandleHttpException(), which returns the exception message as the HTTP response, without encoding the message contents.
Triggering the Problem:
• The target system must have the vulnerable product installed and running.
• The attacker must be able to deliver a malicious URL to the target user.
Triggering Conditions:
An attacker entices a user to open a page that redirects the user to a malicious URL. The vulnerability is triggered when the server parses the crafted request and returns a page containing injected JavaScript code to the target user’s browser.
Attack Delivery:
The following application protocols can be used to deliver an attack that exploits this vulnerability:
• HTTPS, over port 443/TCP
SonicWall’s, (IPS) Intrusion Prevention System, provides protection against this threat:
• IPS: 15711 Microsoft Exchange Server Spoofing Vulnerability (CVE-2021-41349)
Remediation Details:
The risks posed by this vulnerability can be mitigated or eliminated by:
• Applying the vendor supplied patch resolving the vulnerability.
• Upgrading to a version unaffected by the vulnerability.
• Detecting and filtering malicious traffic using the signature above.
The vendor has released the following advisory regarding this vulnerability:
Vendor Advisory