Realtek Jungle SDK remote code execution
Realtek currently manufactures and sells a variety of microchips globally. Realtek chipsets are found in many embedded devices in the IoT space. Realtek offers total HomeKit solutions with Ameba (RTL8711 series) and iCOM (RTL8196/8188 series) that can be easily implemented into various IoT platform designs, e.g. smart plug, smart home appliances, home security systems, and smart sensor/lighting devices.RTL8xxx SoCs provide wireless capabilities and the SDK exposes services over the network.
CVE-2021-35395
Realtek Jungle SDK version v2.x up to v3.4.14B provides an HTTP web server exposing a management interface that can be used to configure the access point.There are two versions of of this management interface namely one based on Go-Ahead named webs and another based on Boa named boa. Arbitrary command execution in formSysCmd via the sysCmd parameter exists in this SDK. Successful exploitation of this vulnerability allows remote attackers to gain arbitrary code execution on the device.
The HTTP web server ‘boa’ is also vulnerable to multiple buffer overflows due to unsafe copies of some overly long parameters submitted in the form, such as
- unsafe copy of ‘submit-url’ parameter in formRebootCheck/formWsc/formWlanMultipleAP
- unsafe copy of ‘peerPin’ parameter in formWsc

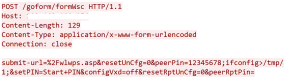
- unsafe copy of ‘ifname’ parameter in formWlSiteSurvey
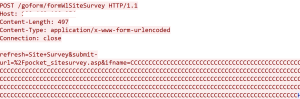
- unsafe copy of ‘hostname’ parameter in formStaticDHCP

The root cause of the above vulnerabilities is insufficient validation of the buffer size and unsafe calls to sprintf/strcpy. An attacker can exploit these vulnerabilities by crafting arguments in a specific request. Successful exploitation could lead server crash and denial of service.
Realtek has patched these vulnerabilities.
SonicWall Capture Labs provides protection against this threat via following IPS signatures:
- 18646:Realtek Jungle SDK Remote Code Execution 2
- 18645 Realtek Jungle SDK Remote Code Execution 1
- 18649 Realtek Jungle SDK HTTP Server Buffer Overflow 5
- 18648 Realtek Jungle SDK HTTP Server Buffer Overflow 4
- 18647 Realtek Jungle SDK HTTP Server Buffer Overflow 3
- 18644 Realtek Jungle SDK HTTP Server Command Injection
- 18643 Realtek Jungle SDK HTTP Server Buffer Overflow 2
- 18642 Realtek Jungle SDK HTTP Server Buffer Overflow
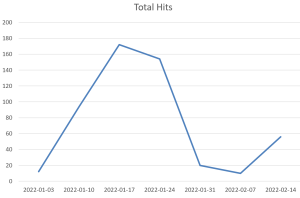
Threat Graph