F5 BIG-IP iControl remote command execution vulnerability
SonicWall Capture Labs threat research team observed attacks exploiting vulnerability in F5’s BIG-IP iControl API.
BIG-IP
F5’s BIG-IP is a product family consisting of software, hardware, and virtual appliances designed around application availability, access control, and security solutions. BIG-IP software products run on top of F5’s Traffic Management Operation System® (TMOS), designed specifically to inspect network and application traffic and make real-time decisions based on the configurations given. BIG-IP Configuration Utility is a Web GUI for F5 users to set up the BIG-IP product and to make additional changes.
Vulnerability | CVE-2021-22986
BIG-IP iControl is a REST API for BIG-IP, which is accessible over HTTPS on port 443/TCP via the following URL:
https://<host>/mgmt/tm/
BIG-IP iControl REST interface has an unauthenticated remote command execution vulnerability. This vulnerability allows for unauthenticated attackers with network access to the iControl REST interface, through the BIG-IP management interface and self IP addresses, to execute arbitrary system commands, create or delete files, and disable services. This vulnerability can only be exploited through the control pane. Exploitation can lead to complete system compromise. An unauthenticated, remote attacker could exploit this vulnerability by sending a specially crafted request to the vulnerable REST interface. Due to insufficient validation in login requests to the REST API the attacker is able to successfully bypass authentication .

After bypassing the authentication, a remote attacker can use multiple vectors to execute commands on the target
server as shown below:
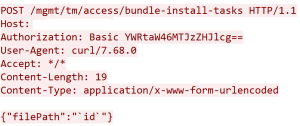
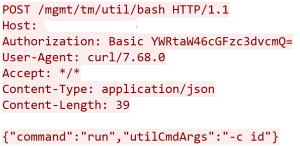
The following JSON payload would execute the “id” command on the underlying operating system:
The following versions are vulnerable :
-
- versions 16.0.x before 16.0.1.1
- 15.1.x before 15.1.2.1
- 14.1.x before 14.1.4
- 13.1.x before 13.1.3.6
- 12.1.x before 12.1.5.3
- BIG-IQ 7.1.0.x before 7.1.0.3 and 7.0.0.x before 7.0.0.2
This vulnerability is patched . The vendor advisory is here
SonicWall Capture Labs provides protection against this threat via following signatures:
-
- IPS 15471:F5 BIG-IP iControl REST Remote Command Execution 1
- IPS 15472:F5 BIG-IP iControl REST Remote Command Execution 2
- IPS 15473:F5 BIG-IP iControl REST Remote Command Execution 3
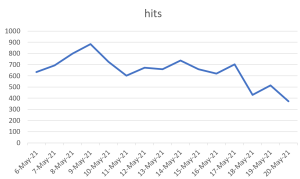
Threat Graph